Full-custom AES SubByte circuit resisting differential power analysis attack
A differential power consumption analysis and fully customized technology, applied in logic circuits, encryption devices with shift registers/memory, electrical components, etc., can solve problems such as lack of security of SubByte
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
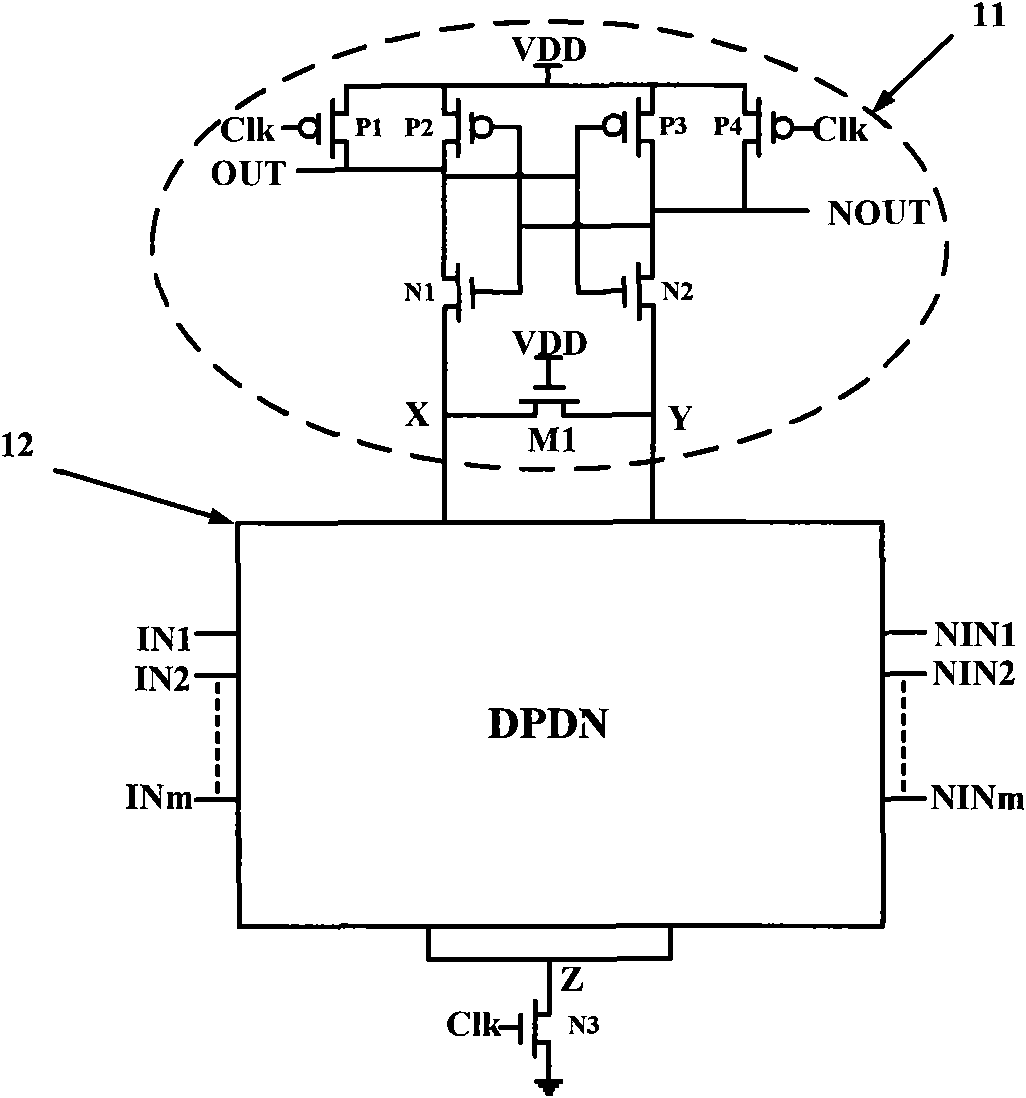
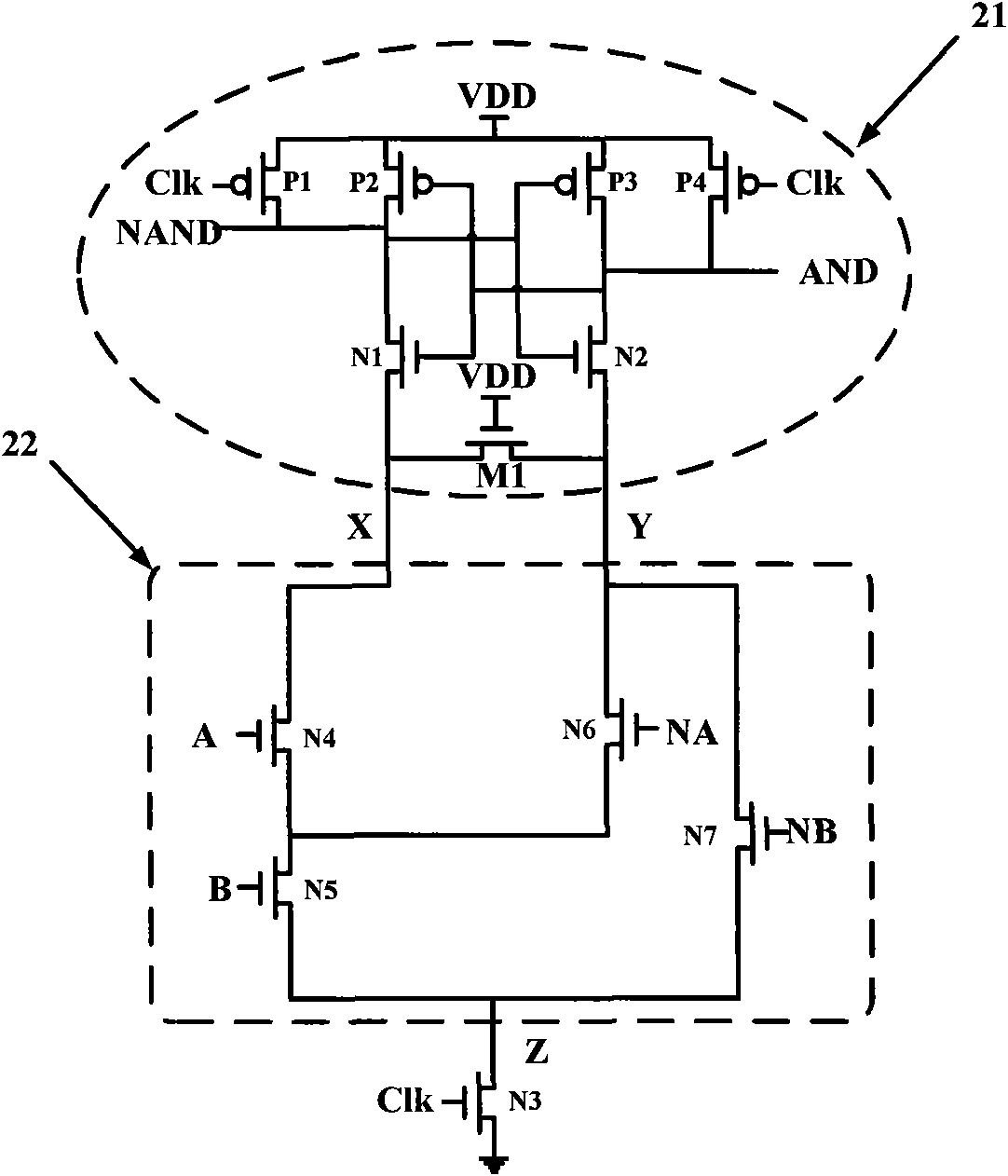
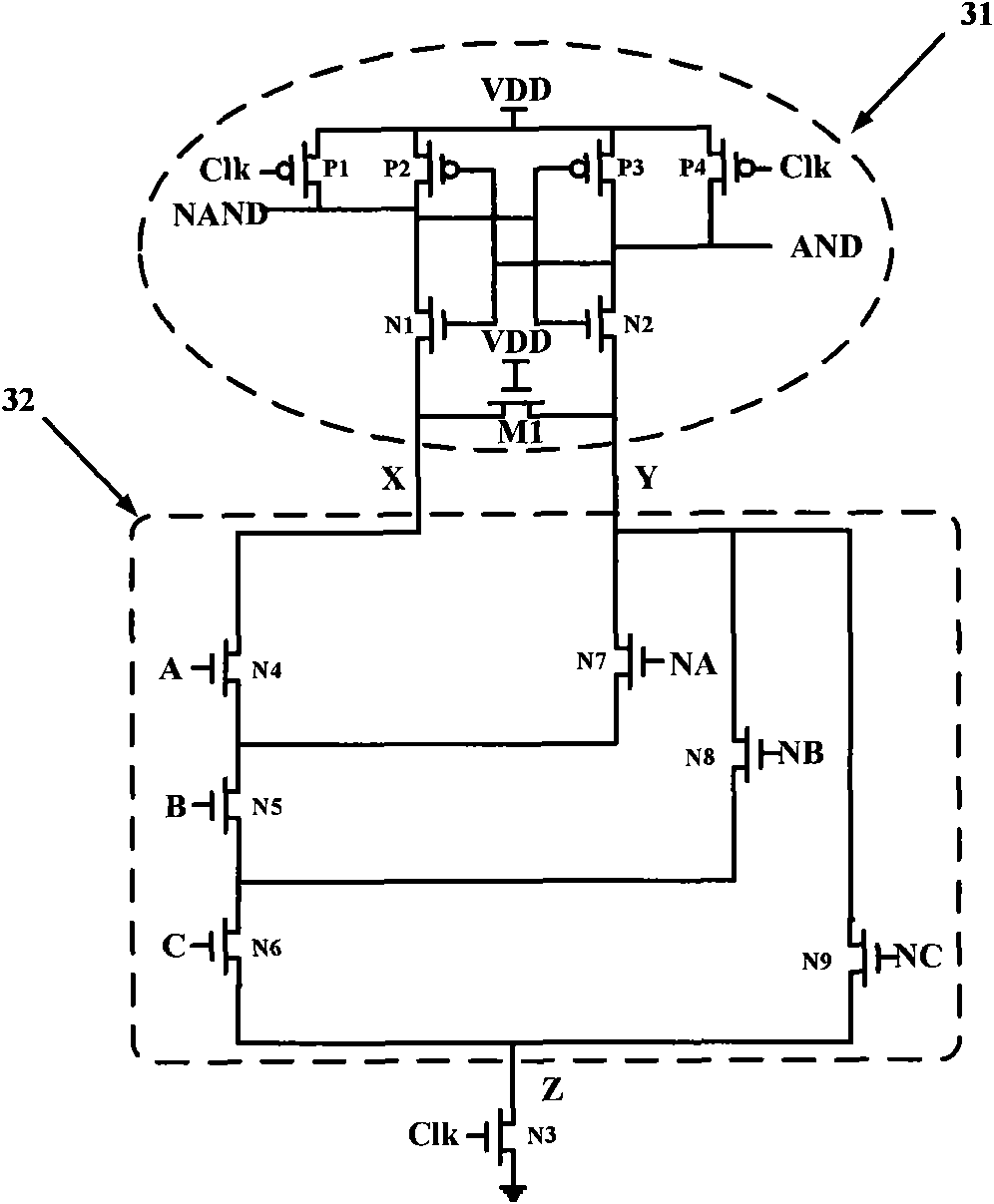
[0024] The purpose of the present invention is to propose a fully customized AES SubByte circuit that is resistant to differential power analysis attacks, so that the AESS SubByte module structure is resistant to differential power analysis attacks, embedded in AES, and can make the entire AES structure resistant to differential power analysis.
[0025] The SubByte structure is the most complicated part of the AES algorithm. It contains non-linear operations and has different affine transformations for encryption and decryption. There are two implementation methods of the SubByte module, one is a lookup table, and the other is a finite field operation. In order to reduce the hardware area, the present invention adopts the method of finite field calculation to realize the SubByte module. About to be originally in GF(2 8 ) domain inverse calculation, converted to GF(2 4 ) domain implementation. Since GF(2 4 ) field is relatively simple, and can quickly and effectively perfo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com