Safety protection method of network feedback host computer
A security protection and network technology, applied in the field of network information security, can solve problems such as ineffective detection of viruses and ineffective monitoring of host firewalls, achieving efficient and flexible policy configuration and auditing, and ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] The content of the invention will now be further explained in conjunction with the description of the drawings.
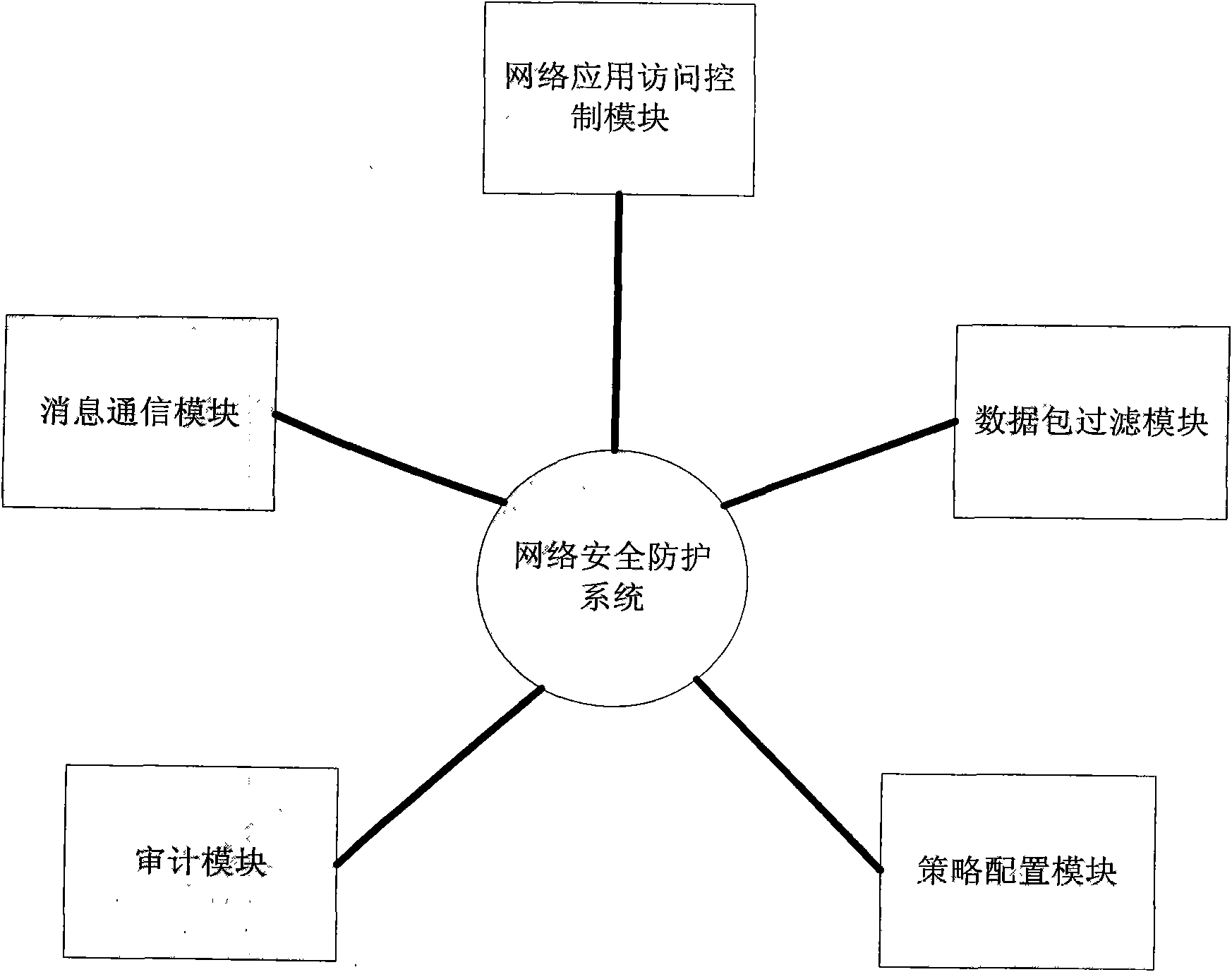
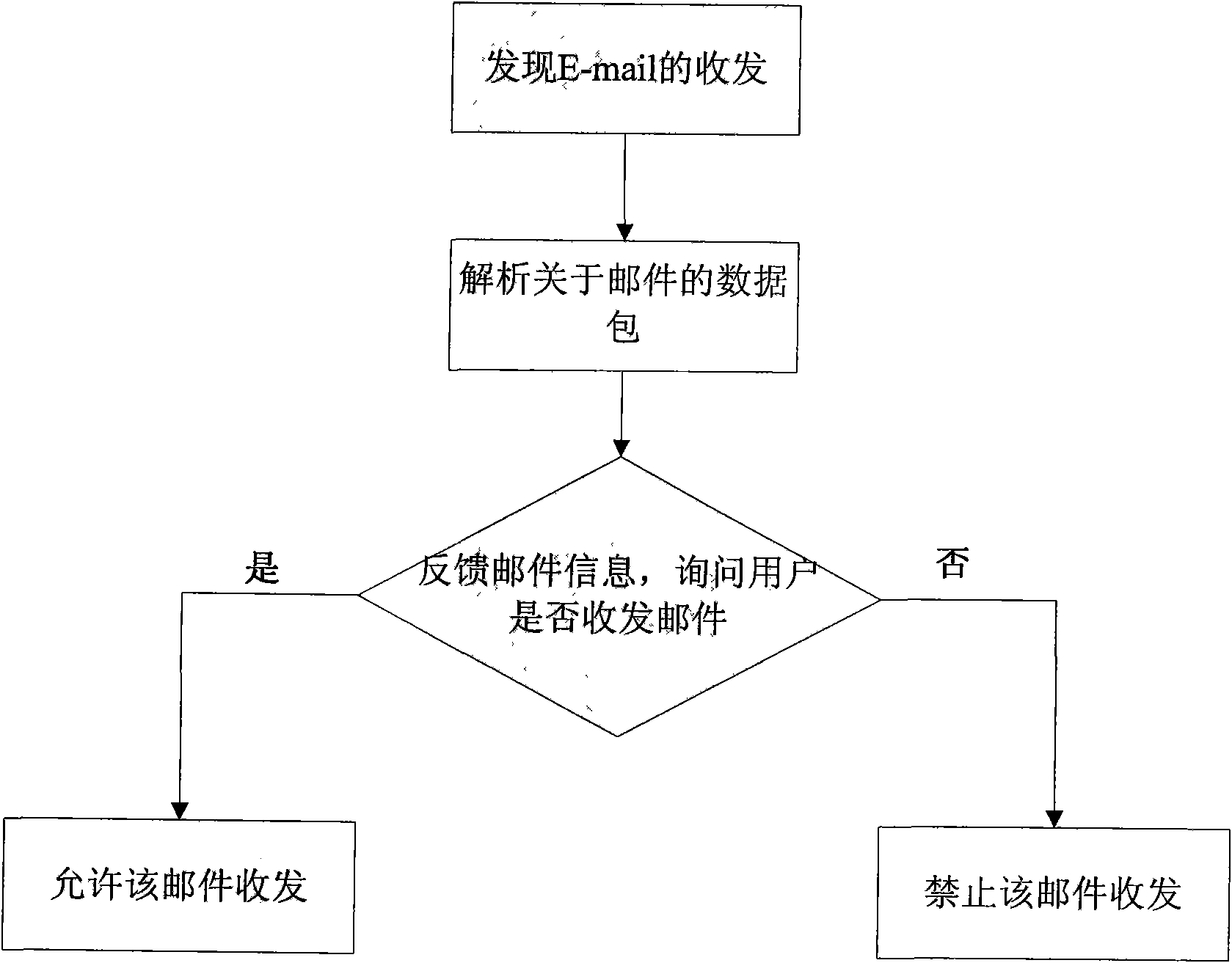
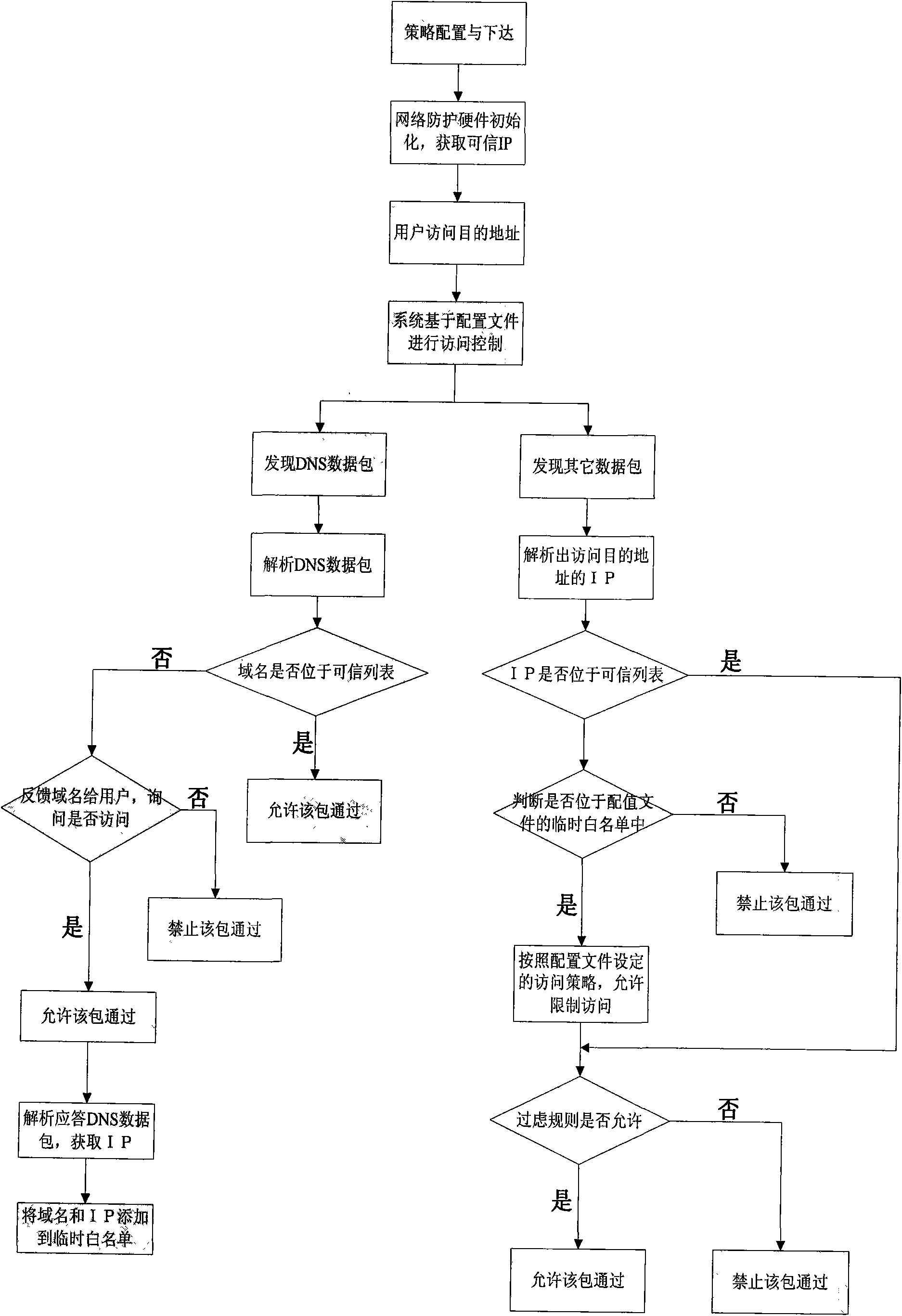
[0043] The system is composed of hardware equipment and PC terminal software, and can be applied in various network environments such as individuals or units. The main content is that the host monitoring software monitors various resources such as system processes, files, application software, and network connections, and the network hardware equipment detects and controls the connection between the internal and external networks. Effectively protect the security of information on computer terminals.
[0044] The overall structure of the computer network security protection system consists of three parts: network security protection hardware equipment, user PCs, management and audit servers. The network protection system is located between the PC and the Internet, isolates the internal and external networks, and realizes the access control of the network co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com