Trustworthy computing base cutting method used for virtual machine system
A trusted computing and virtual machine technology, applied in computing, computer security devices, instruments, etc., can solve problems affecting the implementation of trusted verification, unfavorable static trust chain construction, leakage threats, etc., to achieve enhanced security and startup speed, Effect of reducing the risk of leakage and preventing tampering or destruction
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
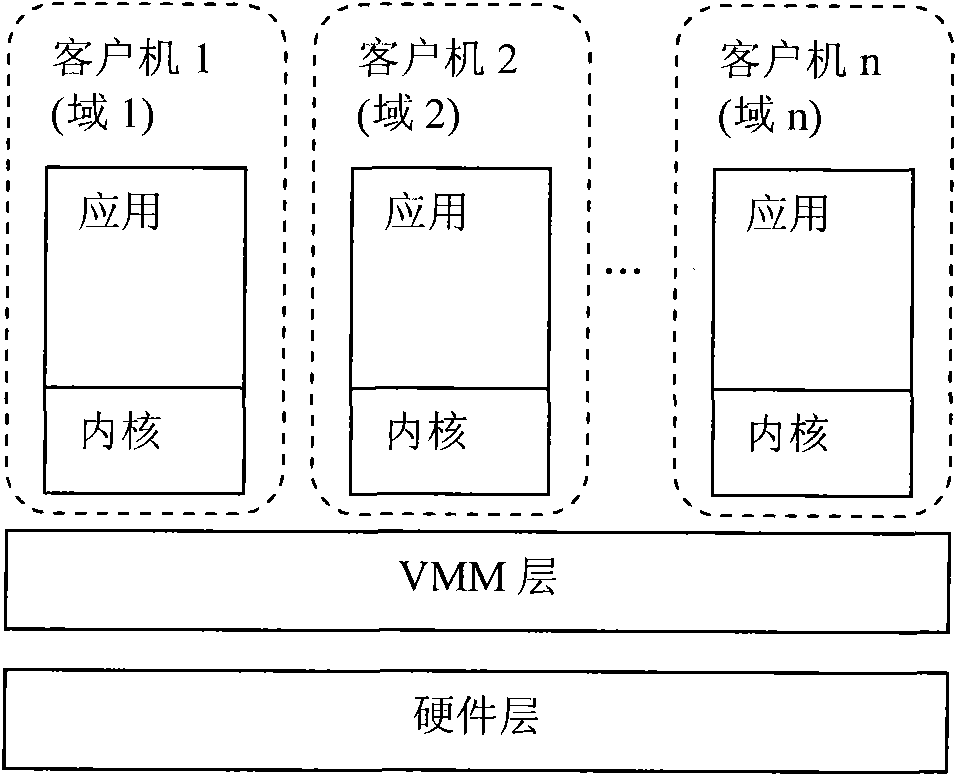
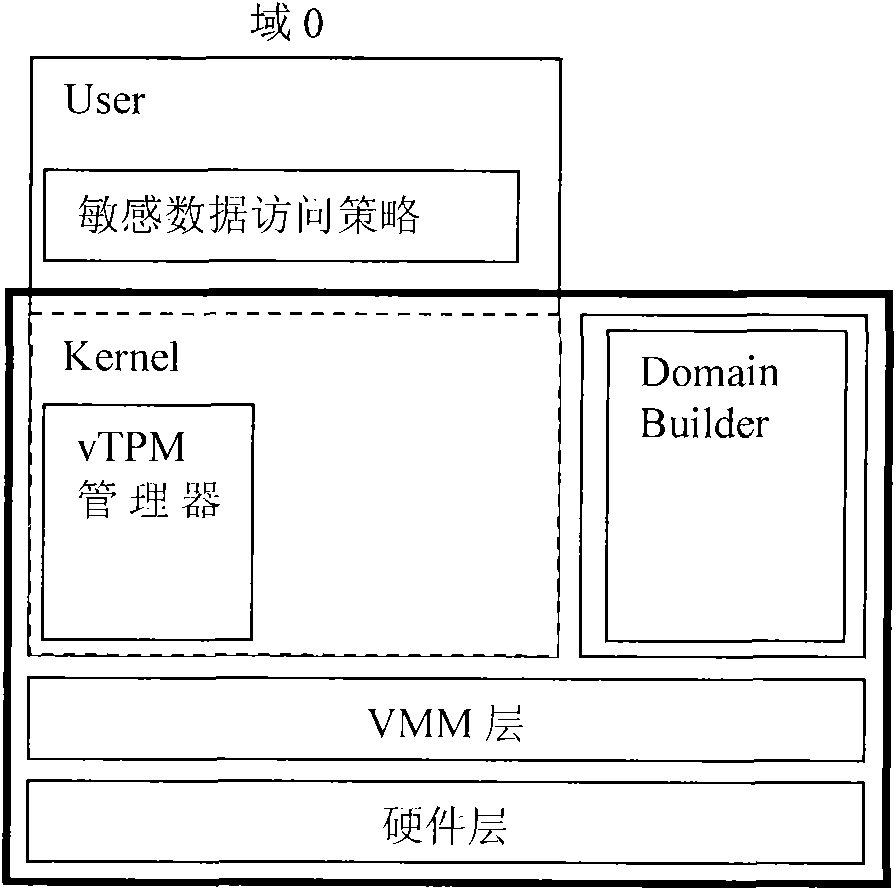
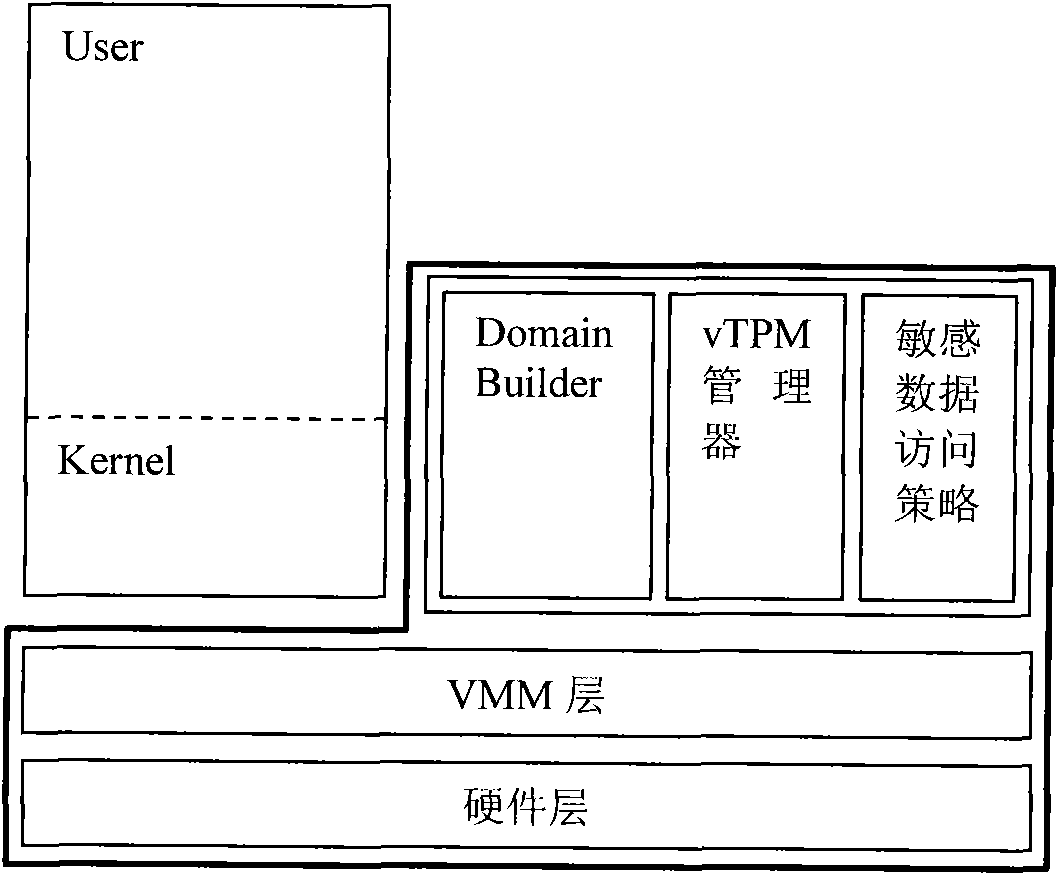
[0016] The invention proposes a trusted computing base cutting method for a virtual machine system. The trusted computing base in the prior art includes a hardware layer (including CPU, BIOS, etc.), a VMM layer, a vTPM manager, a Domain Builder, a kernel, and sensitive data access policies. The present invention places vTPM manager, DomainBuilder and sensitive data access policy in a domain isolated from domain 0. According to the virtual machine technology, domains other than the privileged domain belong to the user domain, but the domain established by the present invention is for the purpose of security and anti-leakage, so it is called a special user domain, which is recorded as domain B in the embodiment. In order to support the work of Domain Builder, it is necessary to realize the communication mechanism between domain B where Domain Builder is located and domain 0. see image 3 , under the tailoring scheme of the present invention, the trusted computing base includes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com