Method for protecting encrpytion software
An encryption software, encryption authentication technology, applied in the direction of program/content distribution protection, instruments, electrical digital data processing, etc., can solve the problems of slow access speed, affecting system performance, high risk of being cracked, to avoid performance loss, increase The effect of cracking the difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0020] Describe in detail below in conjunction with specific implementation plan:
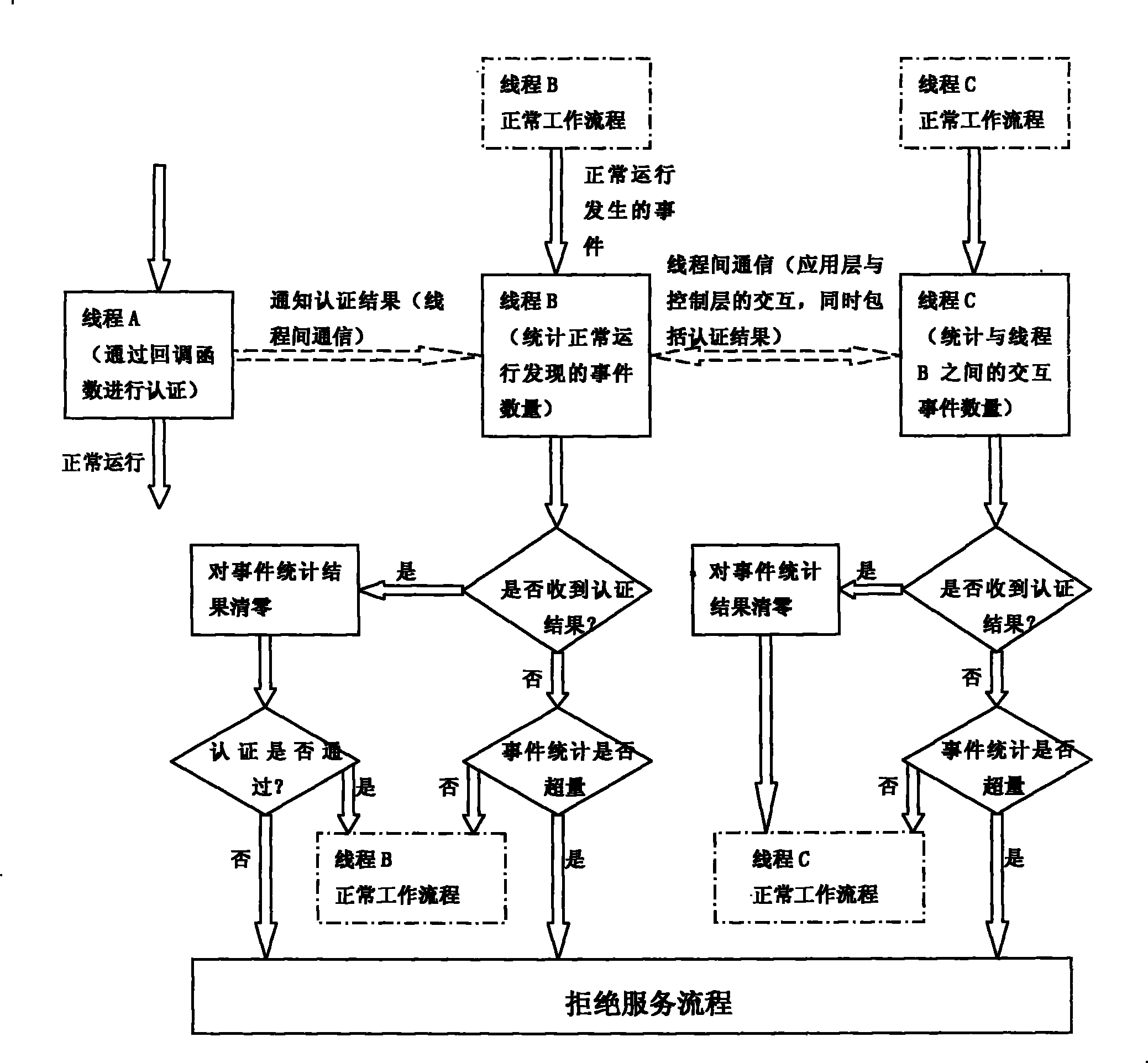
[0021] The key function thread that adopts in this specific embodiment only adopts one, namely key function thread C, but this does not affect the scope of protection of the present invention, because can add a plurality of key function threads as required, carry out multiple nesting authentication by inter-thread communication , in order to increase protection.
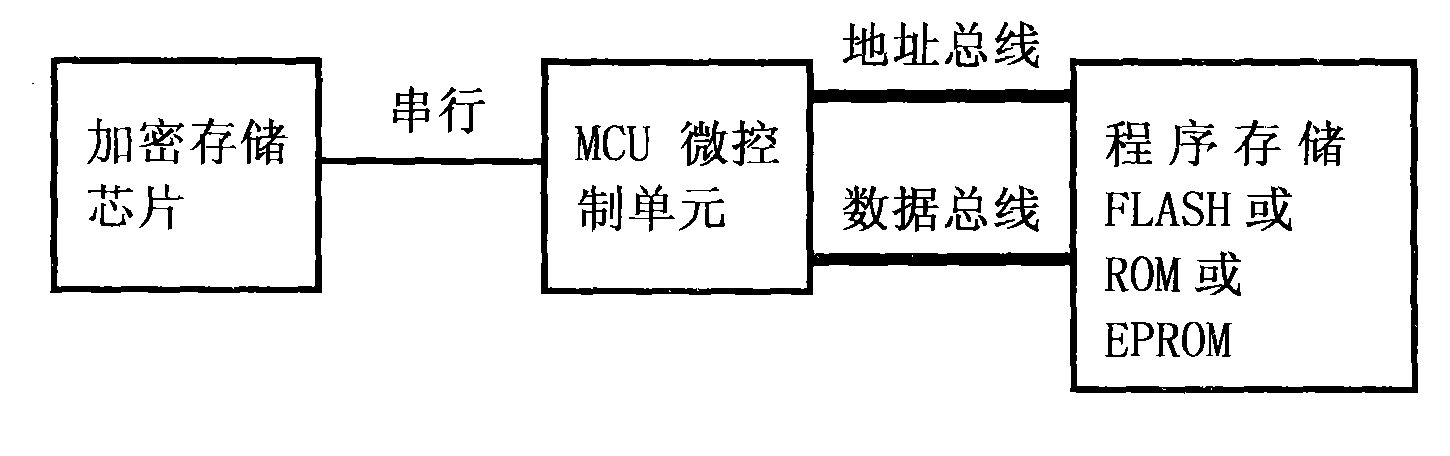
[0022] This method is used to perform multi-threaded hardware encryption authentication by adopting a general encryption chip, and has an encryption memory chip. Its hardware connection is as follows figure 1 shown. Since the MCU and the encryption memory chip use a serial interface for communication, such as SPI or I2C, the recommended encryption memory chip has only 8 pins and is packaged in SOIC, which occupies a relatively small space (7mm×5.5mm) and is low in cost. , it is easy to increase, and it is also very convenient to tr...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com