Method for distributing code stream encrypting and decrypting keys in SIP video monitoring system
A video monitoring system and key distribution technology, which is applied in key distribution, can solve problems such as inconvenient management and poor adaptability of cross-domain applications, and achieve the effects of eliminating security risks, resisting replay attacks, and improving safety factors
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
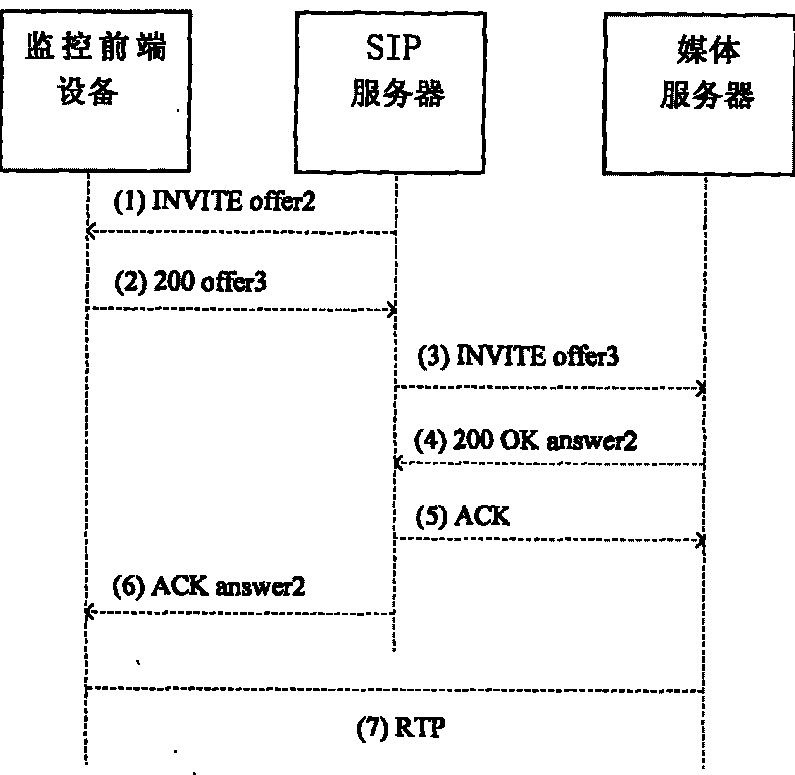
[0014] The present invention will be described in further detail below in conjunction with accompanying drawing and specific embodiment, as figure 1 , 2 Shown, the present invention comprises the following steps:
[0015] 1. The process of obtaining a shared key seed through two-way authentication of device registration based on digital certificates;
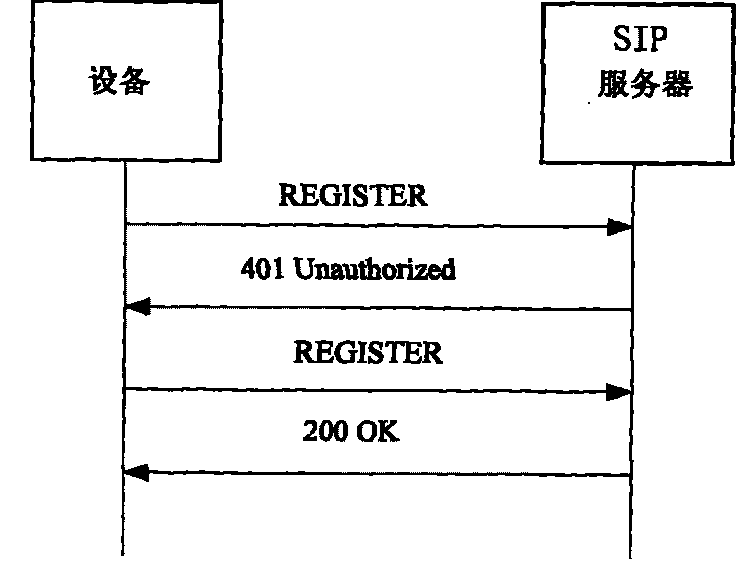
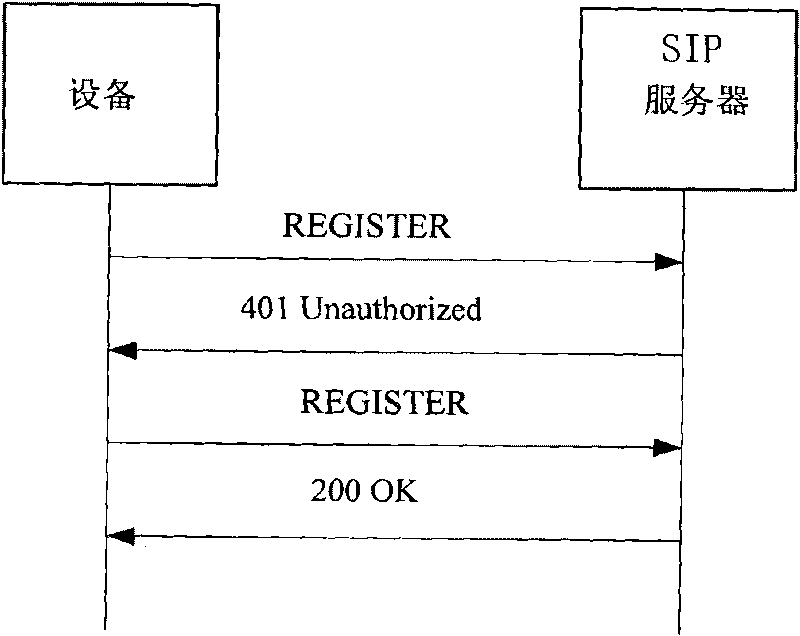
[0016] In the process of two-way authentication of device registration based on digital certificates to obtain a shared key, the REGISTER message defined in RFC3261 is used to authenticate the process based on challenges.
[0017] When the SIP server receives the REGISTER message sent by the device, the SIP server generates a random number SEED, calculates the nonce value, and sends the nonce value to the device through a 401 error message. nonce=A&B (& is the string connection separator), A=E[PRs, H(From+To+Call-ID+Contact+SEED)], where + is the string connection character; H is the Hash operation, B =E(PUd, SEED) (where, E ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com