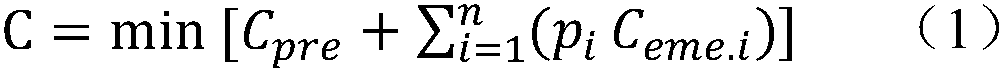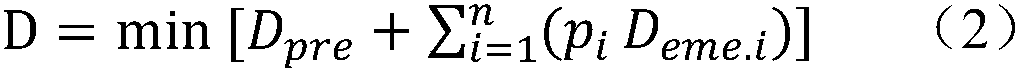Patents
Literature
273results about How to "Eliminate security risks" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
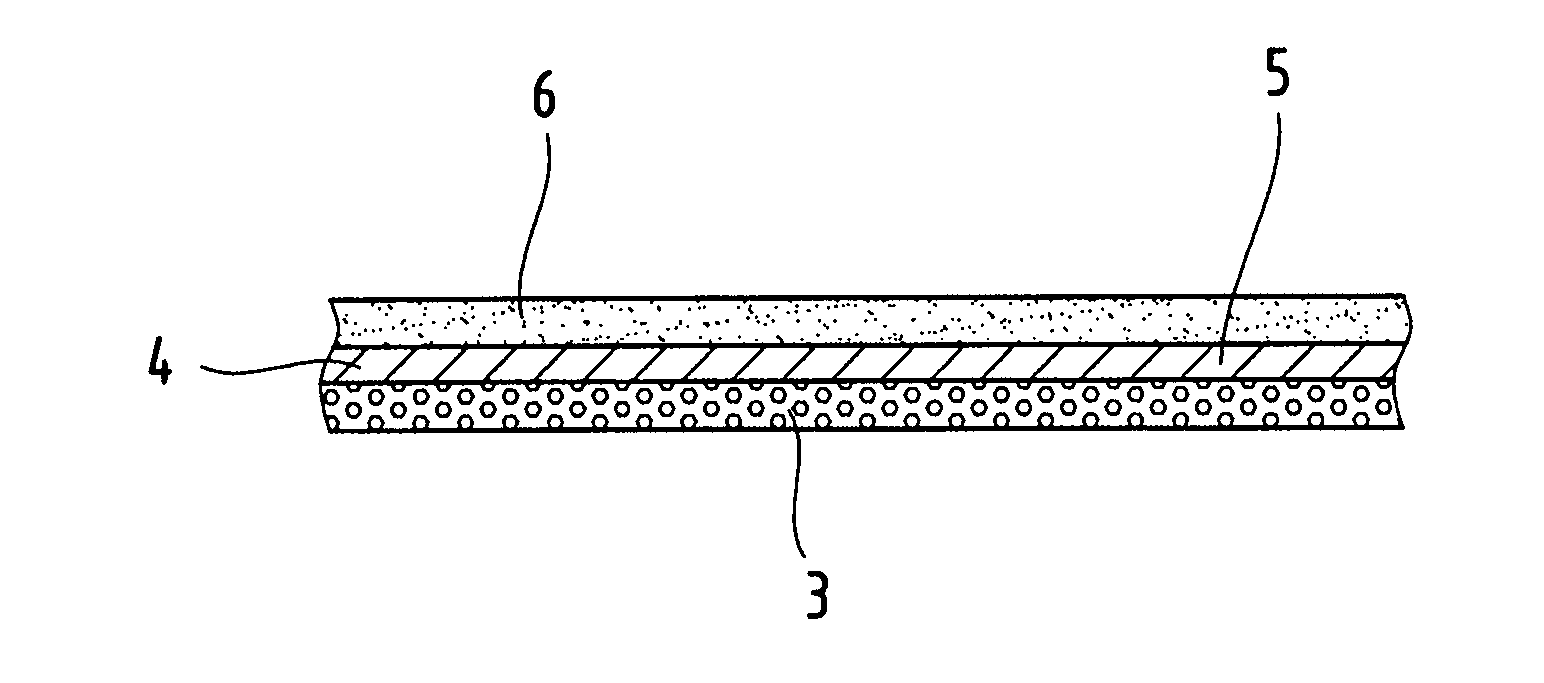
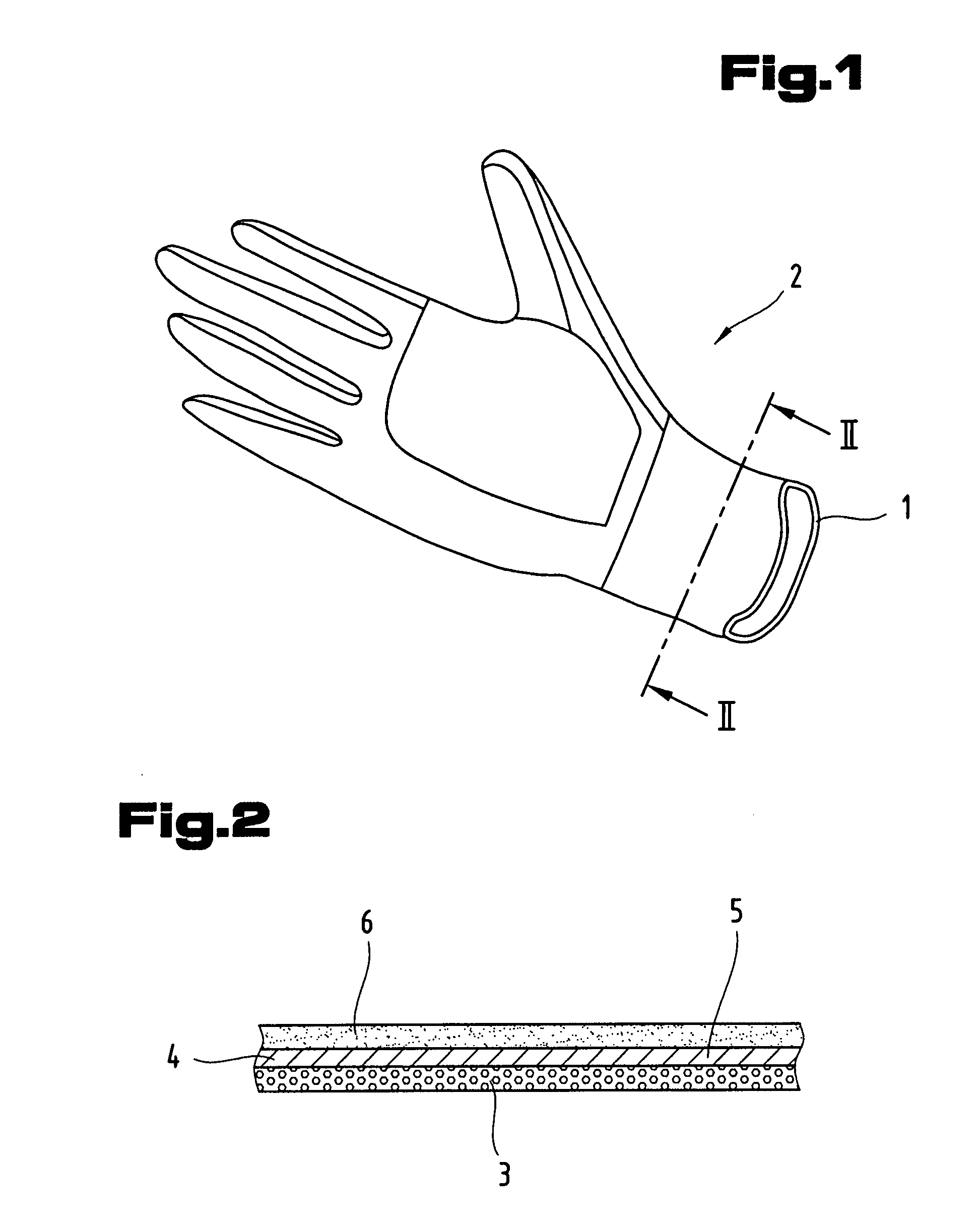
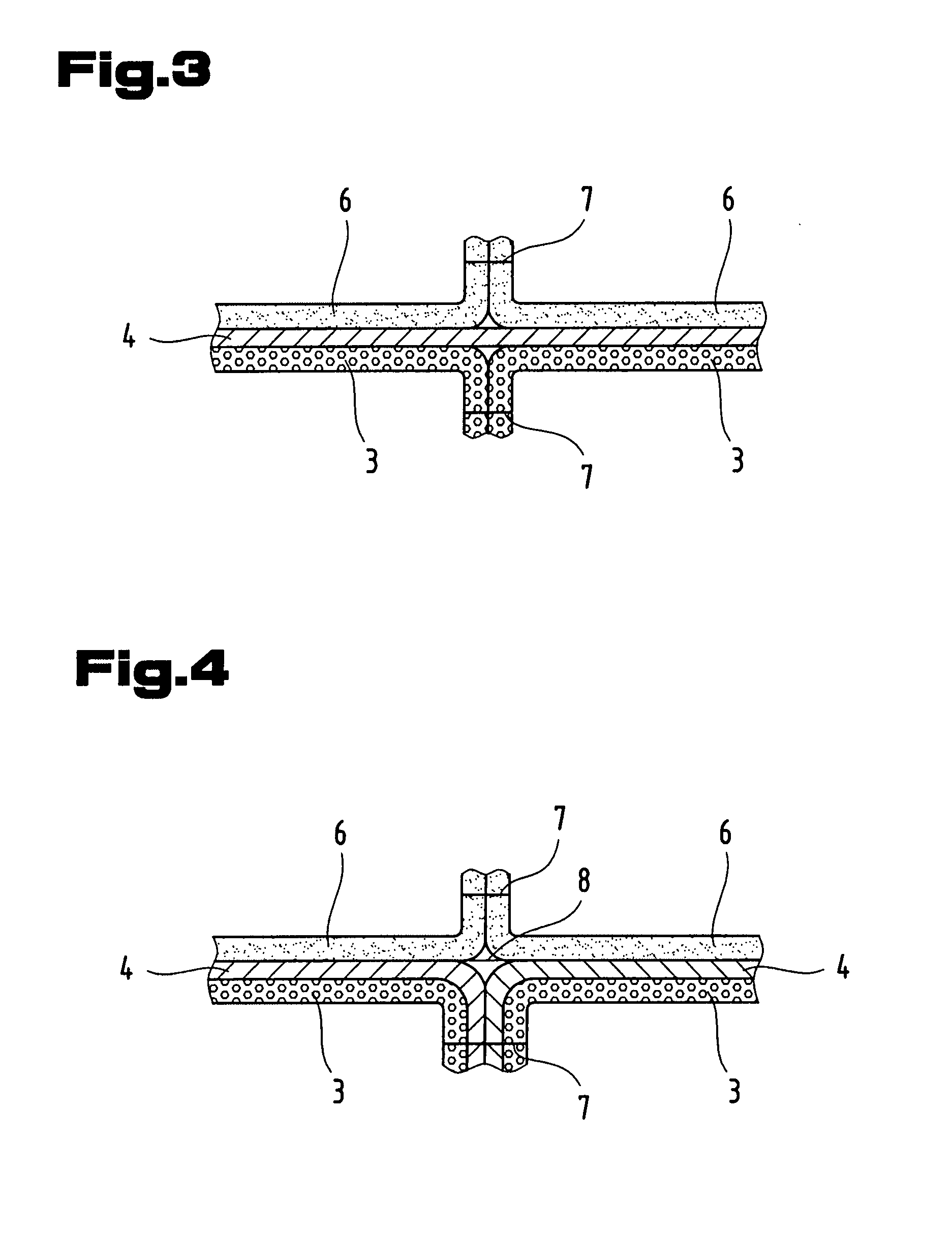
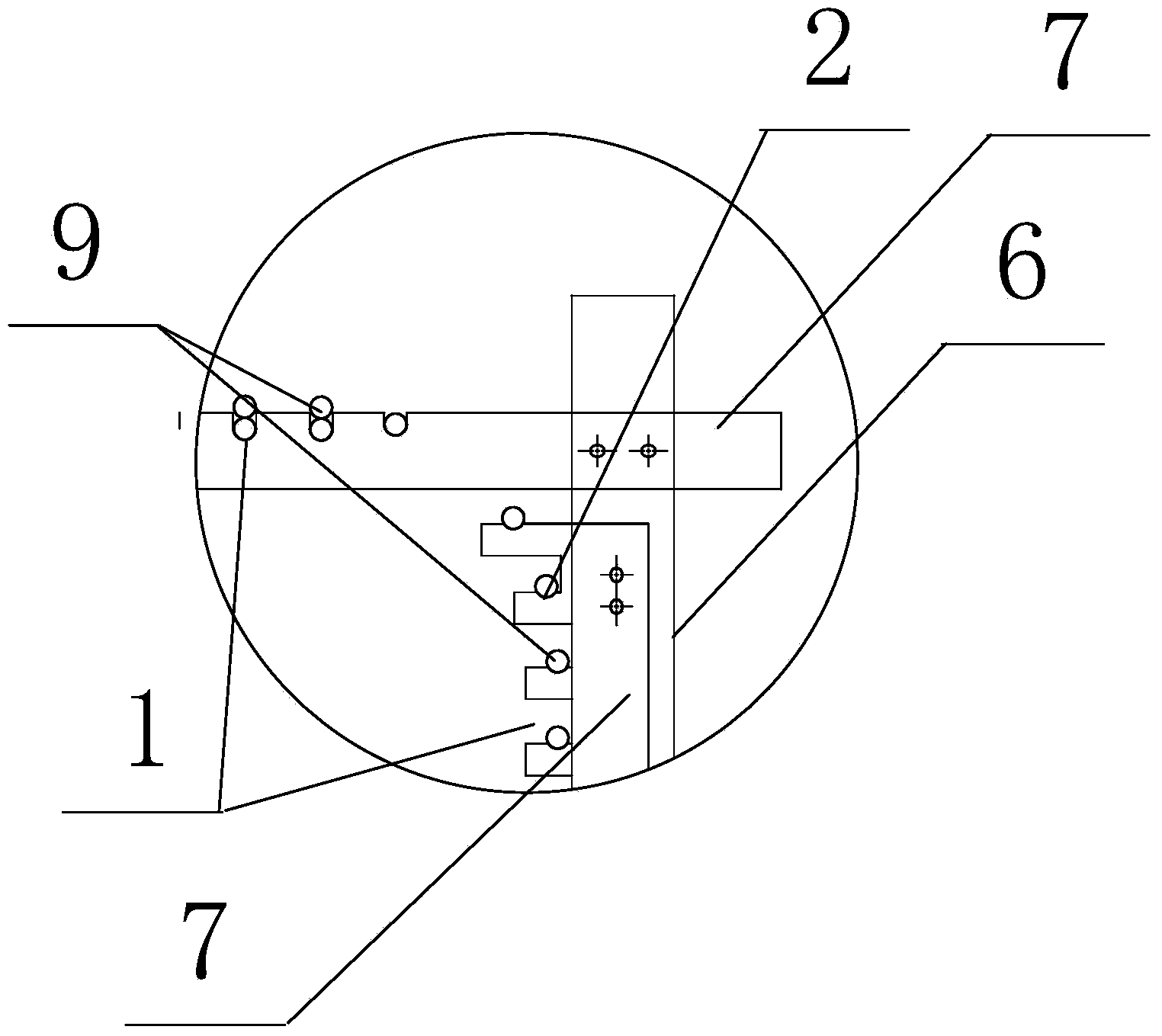
Internal Lining and Method for the Production Thereof
InactiveUS20090075019A1Eliminating environmentEliminate security risksGarment special featuresElectrotherapyYarnFiber
An internal lining of several layers having anti-microbial effect is described for an item of equipment suitable for at least temporarily covering body parts; in particular, the layers include at least one layer made from a woven fabric and / or knitted and / or non-woven fabric with an anti-microbial effect wherein the fabric contains a metal, which metal is integrated in a filament, a fiber and / or a spunbonded fiber or spunbonded yarn; and at least one other layer of a semi-permeable membrane made from polytetrafluoroethylene (PTFE), and / or a polymeric laminate. The method of production of the multiple layered internal lining with an antimicrobial effect is also disclosed.
Owner:ESKA LEDERHANDSCHUHFAB & CO
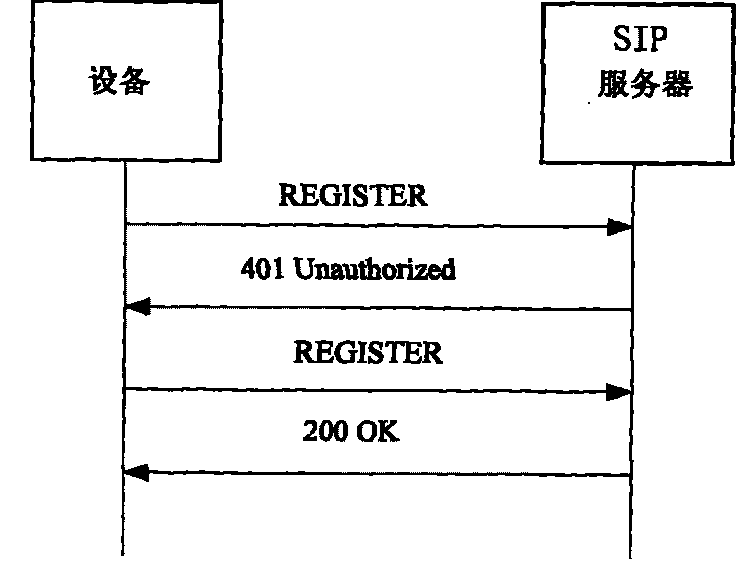
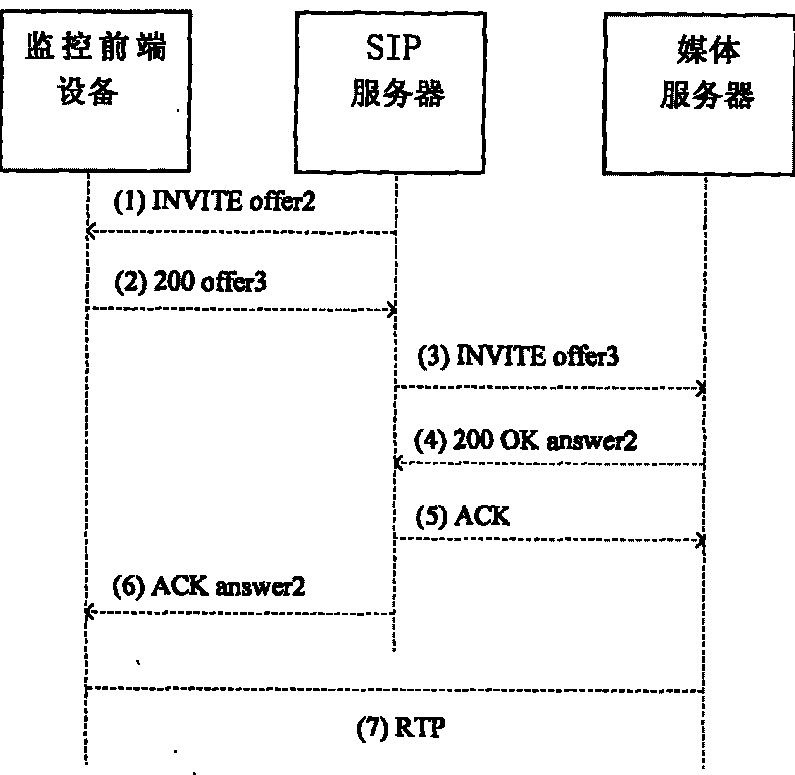
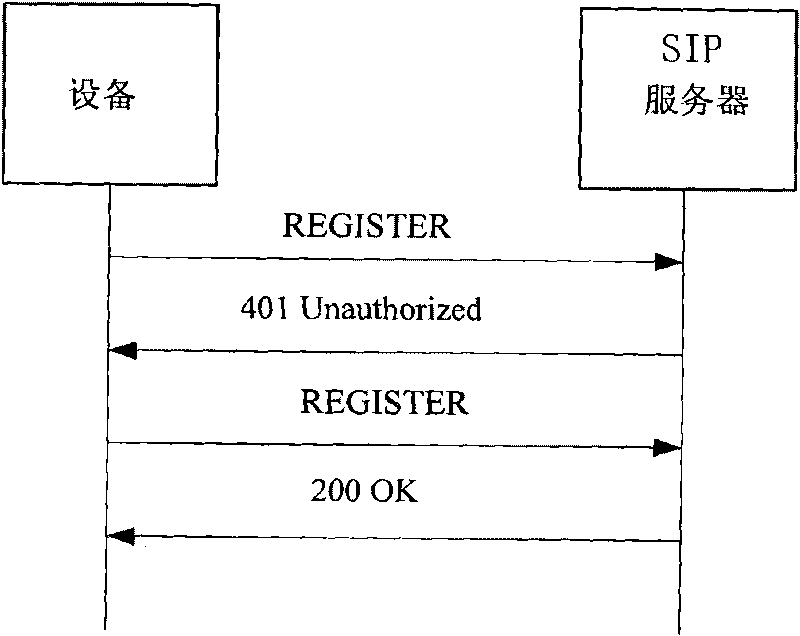
Method for distributing code stream encrypting and decrypting keys in SIP video monitoring system
ActiveCN101729854AEliminate security risksImprove securityKey distribution for secure communicationUser identity/authority verificationVideo monitoringMedia server
The invention discloses a method for distributing code stream encrypting and decrypting keys in an SIP video monitoring system. In the method, in a process for calling a 3 pcc between code stream encrypting monitoring front end equipment and code stream decrypting customer premise equipment, or a process of calling a 3 pcc between the code stream encrypting monitoring front end equipment and a media server and a 3 pcc between code stream decrypting customer premise equipment and the media server, seeda, seedb and seedc, which are obtained by the monitoring front end equipment, the media server and the customer premise equipment in an identity authentication process during registration, are used as keys shared with an SIP server and identifiers, the content of an SIP signaling message bodySDP is expanded to carry the encrypting and decrypting keys, and a symmetric algorithm or asymmetric algorithm is used to guarantee the safety of the transmission of the encrypting and decrypting keys. The method has the advantages of generating different keys at each time of broadcasting, greatly improving safety coefficient, resisting replay attack and eliminating the safety hazards of the storage of the keys at multiple places.
Owner:THE FIRST RES INST OF MIN OF PUBLIC SECURITY +1
Direct forced draft fluid cooler/cooling tower and liquid collector therefor
InactiveUS20110315350A1Reduced initial construction costHeight of structurePipe supportsServomotor componentsCooling towerClosed loop
Direct forced draft fluid cooler / closed loop cooling towers and cooling towers are provided with fans at the bottom of the unit, and a plurality of layers of water collection troughs or channels above the fans to capture water droplets sprayed downwardly from the top of the device through a heat exchanger or fill media above the collection troughs. In one embodiment the collection troughs supply the collected water to one or more gutters inside the housing which lead the water to an external collection tank from which the water is recirculated through the system.
Owner:CURTIS HAROLD +1
Heat pump air conditioning system, electric vehicle and control method thereof
ActiveCN108068577AAffect the mileage and other issuesRealize electric frequency conversion controlAir-treating devicesVehicle heating/cooling devicesEngineeringAir conditioning
The invention discloses a heat pump air conditioning system, an electric vehicle and a control method thereof. The heat pump air conditioning system comprises an enthalpy compressor (11), a first indoor heat exchanger (32), a flash evaporator (12) and an outdoor heat exchanger (31); an exhaust end of the enthalpy compressor (11) communicates with a refrigerant inlet of the first indoor heat exchanger (32); a refrigerant outlet of the first indoor heat exchanger (32) communicates with a first inlet and outlet end of the flash evaporator (12); a second inlet and outlet end of the flash evaporator (12) communicates with a first refrigerant inlet and outlet of the outdoor heat exchanger (31); a second refrigerant inlet and outlet of the outdoor heat exchanger (31) communicates with a suction end of the enthalpy compressor (11); and an air supply end of the flash evaporator (12) communicates with an air supply opening of the booster compressor (11). According to the scheme, the defects of large energy consumption, inconvenient operation and poor user experience in the prior art can be overcome, and the beneficial effects of small energy consumption, convenient operation and good user experience are achieved.
Owner:GREE ELECTRIC APPLIANCES INC
System and method for preventing misoperation in electric power system by using two-dimension codes
InactiveCN104036349AEasy to operatePrevent misuse functionCo-operative working arrangementsResourcesElectric power systemTerminal equipment
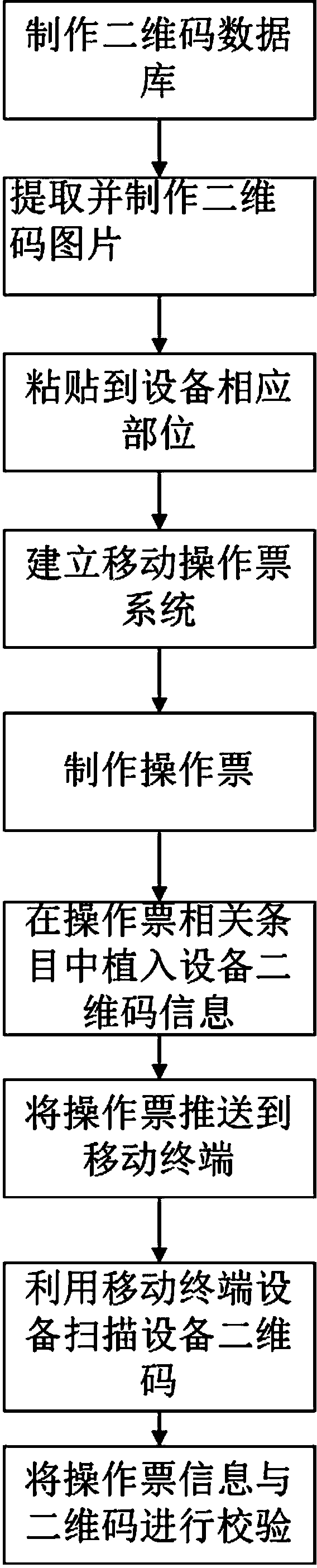
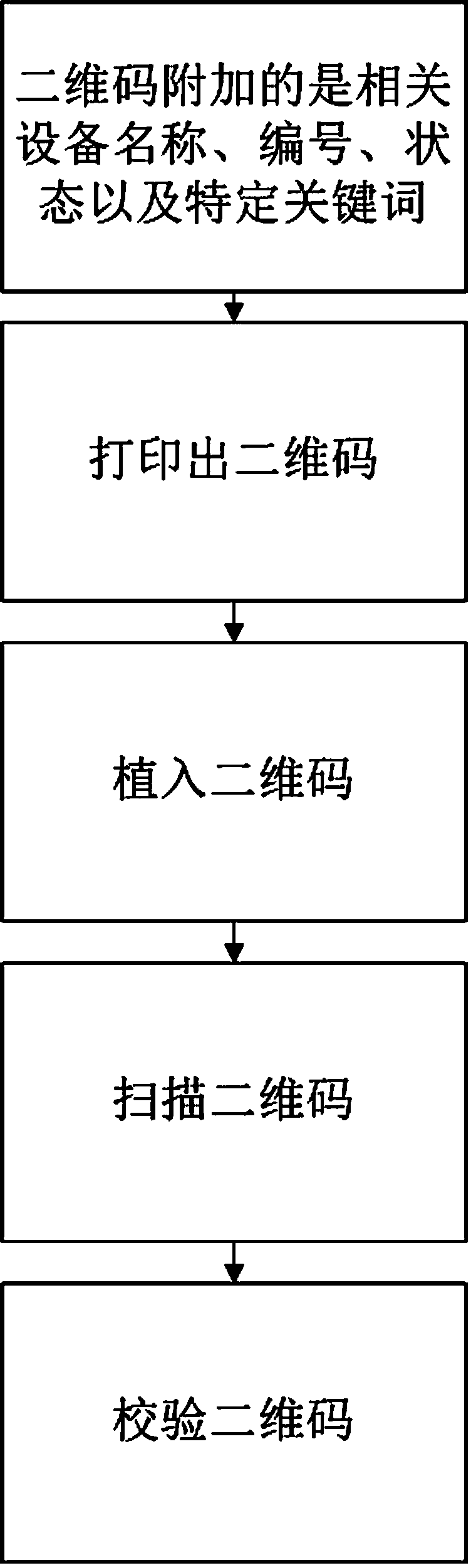
The invention relates to the field of a two-dimension code application system, in particular to a system and a method for preventing misoperation in an electric power system by using two-dimension codes. The method for preventing the misoperation in the electric power system by using the two-dimension codes sequentially comprises the following steps that: (1) a two-dimension code database is manufactured; (2) two-dimension code pictures are extracted and manufactured; (3) the two-dimension code pictures are pasted to corresponding positions of equipment; (4) a mobile operation order system is built; (5) an operation order is manufactured; (6) two-dimension code information of the equipment is implanted into relevant items of the operation order; (7) the operation order is pushed to a mobile terminal; and (8) mobile terminal equipment is used for scanning the two-dimension codes of the equipment. The system and the method provided by the invention have the advantages that the functionality is high; the operation by operators is convenient; great importance is realized on safety risk elimination, personal injury and equipment damage avoidance and safe operation guarantee; and the system and the method are suitable to be widely popularized and applied.
Owner:段君寨 +2
High-content sodium alginate nanofiber membrane and electrostatic spinning manufacturing method thereof
InactiveCN105586716AHigh porosityFine fiber diameterFilament/thread formingNon-woven fabricsPorosityFiber
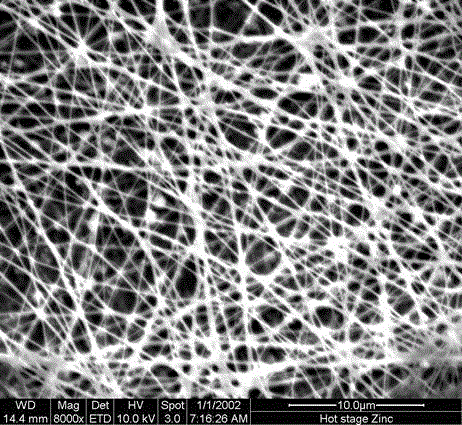
The invention provides a high-content sodium alginate nanofiber membrane and an electrostatic spinning manufacturing method thereof. The material is formed by sodium alginate or sodium alginate and polyvinyl alcohol, wherein the absolute content of the sodium alginate is 42.5 wt% to 100 wt%, and average diameter of the fiber is 100 nm to 150 nm. A solvent used in a preparation process of an electrostatic spinning solution is deionized water, and a surfactant is TX-100 which is certificated by US Food and Drug Administration. The manufacturing method is simple and feasible, and the high-content sodium alginate nanofiber membrane is not added with any hazardous substance. The manufactured sodium alginate nanofiber membrane is characterized by high content of sodium alginate, thin average diameter, and high porosity. The sodium alginate nanofiber membrane can be applied in the fields of wound dressing and tissue engineering (for example, a support material), etc.
Owner:TIANJIN TEDA JINSHAN PACKING MFR
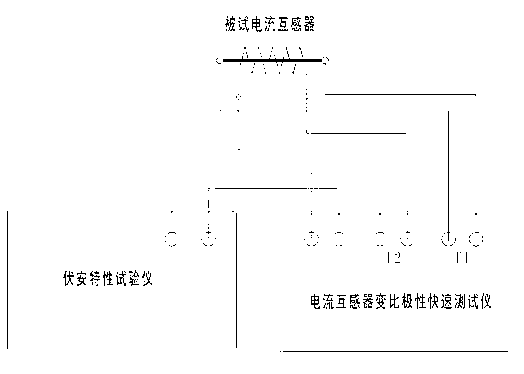
Fast testing instrument of variable ratio and polarity of current transformer and testing method thereof
InactiveCN103278790AEnsure personal safetyAccurate measurementElectrical testingSquare waveformHemt circuits
The invention relates to a fast testing instrument of the variable ratio and the polarity of a current transformer and a testing method thereof. According to the invention, not only can the time for testing the variable ratio and the polarity of the current transformer be shortened from about 50min to about 25min, but also the invention has the advantages of small size, convenience in carrying, high in measuring accuracy, safety and reliability. The testing method comprises the following steps: the voltage outputted by a volt-ampere tester is inputted to a volt-ampere voltage input end of the tester, an exciting voltage U2 is outputted to a secondary coil of the current transformer by S1 and S2; a primary side of the current transformer is inputted to the input end of a primary voltage U1 of the testing instrument; volt and ampere are inputted to the output end of the exciting voltage U2, and then a small current transformer is connected in series and is used for monitoring volt-ampere current I; U2, I and U1 are respectively sampled by a corresponding range switching circuit, a corresponding buffering and amplifying circuit and an corresponding AD, and are transmitted to a CPU (Central Processing Unit) by optoelectronic isolation; the CPU measures amplitudes of three paths of signals; and the U2 and the U1 are also changed into square waves through a waveform converting circuit, the square waves are transmitted to the CPU through the opoelectronic isolation to be used for measuring the phase difference of the U2 and the U1, so as to judge the polarity of the current transformer.
Owner:HANGZHOU KAIDA ELECTRIC POWER CONSTR
Coating device for spraying for petroleum casing pipe
InactiveCN106890749AAvoid doping with impuritiesEliminate security risksSpraying apparatusSpray nozzleEngineering
The invention discloses a coating device for spraying oil casing pipes, comprising nozzle I, nozzle II and a conveying pipeline, a spray ring is arranged between the nozzle I and the conveying pipeline, the spray ring is hollow, and spray holes are arranged on its outer surface Ⅰ, nozzle Ⅰ is connected with spray hole Ⅰ; there is a paint inlet hole Ⅰ on the inner surface of the spray ring, and the delivery pipe is connected with the paint inlet Ⅰ; a fixed ring is arranged between the nozzle Ⅱ and the delivery pipeline, and the fixed ring is hollow. The inner surface is provided with spray hole II, and the nozzle II is connected with the spray hole II; the outer surface of the fixed ring is provided with a paint inlet hole II, and the delivery pipe is connected with the paint inlet hole II. Nozzle I sprays paint on the inner wall of the casing, and nozzle II sprays paint on the outer wall of the casing. This spraying device does not need to build a paint pool, so it avoids the situation that the paint is exposed to the air for a long time and is mixed with impurities, improves the quality of the casing coating layer, and reduces the cost.
Owner:CHENGDU DAMO PETROLEUM TECH CO LTD
Universal spiral compaction type grounding wire operating rod
PendingCN107275906ASolve the problem of difficult installation of ground wires at different anglesSolve installation difficultiesClip conductor connectionWire wrapping connectorsUniversal jointEngineering
The invention discloses a universal spiral compaction type grounding wire operating rod. The universal spiral compaction type grounding wire operating rod is characterized by comprising a lead clamp assembly, an adjusting assembly, an operating rod assembly and a transmission handle assembly which are sequentially connected, and further comprising an insertion type connector used for connecting an insulation operating rod and a limit stop nail, wherein lead clamps are provided with screws and spiral compaction bolts connected with universal joints and clamp heads connected with a steel wire transmission soft shaft, the adjusting assembly comprises supporting pipes used for fixing the universal joints and the steel wire transmission soft shaft, the operating rod assembly comprises the insulation operating rods and insulation transmission rods which are arranged in the insulation operating rods and are connected with the steel wire transmission soft shaft and a transmission handle clamp head, and the transmission handle assembly is provided with a thread type connection head used for connecting the operating rods. The universal spiral compaction type grounding wire operating rod is advantaged in that leads are made to be clamped in any adjustment angle of the horizontal direction 360 DEG and the vertical direction about 120 DEG, the quantity of the operating rods is reduced through employing an assembly connection mode, exchange of the lead clamps in different modes is facilitated, and cost is reduced.
Owner:谭加新
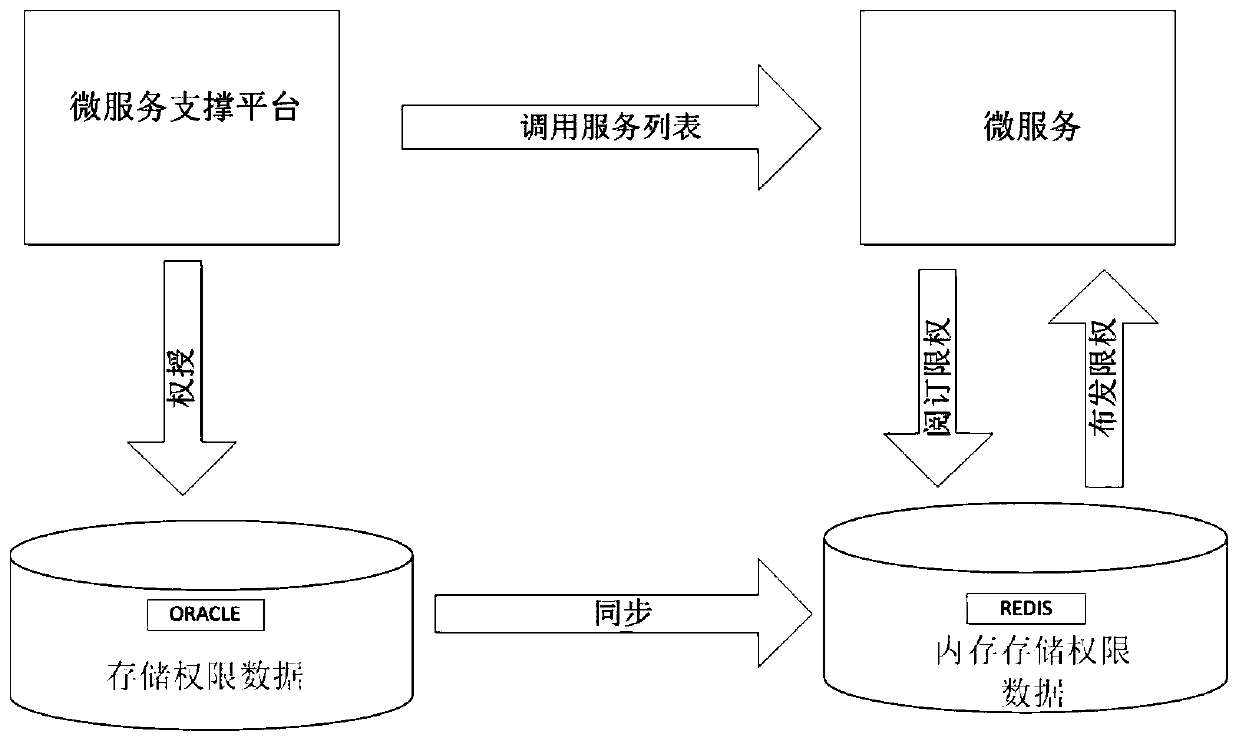
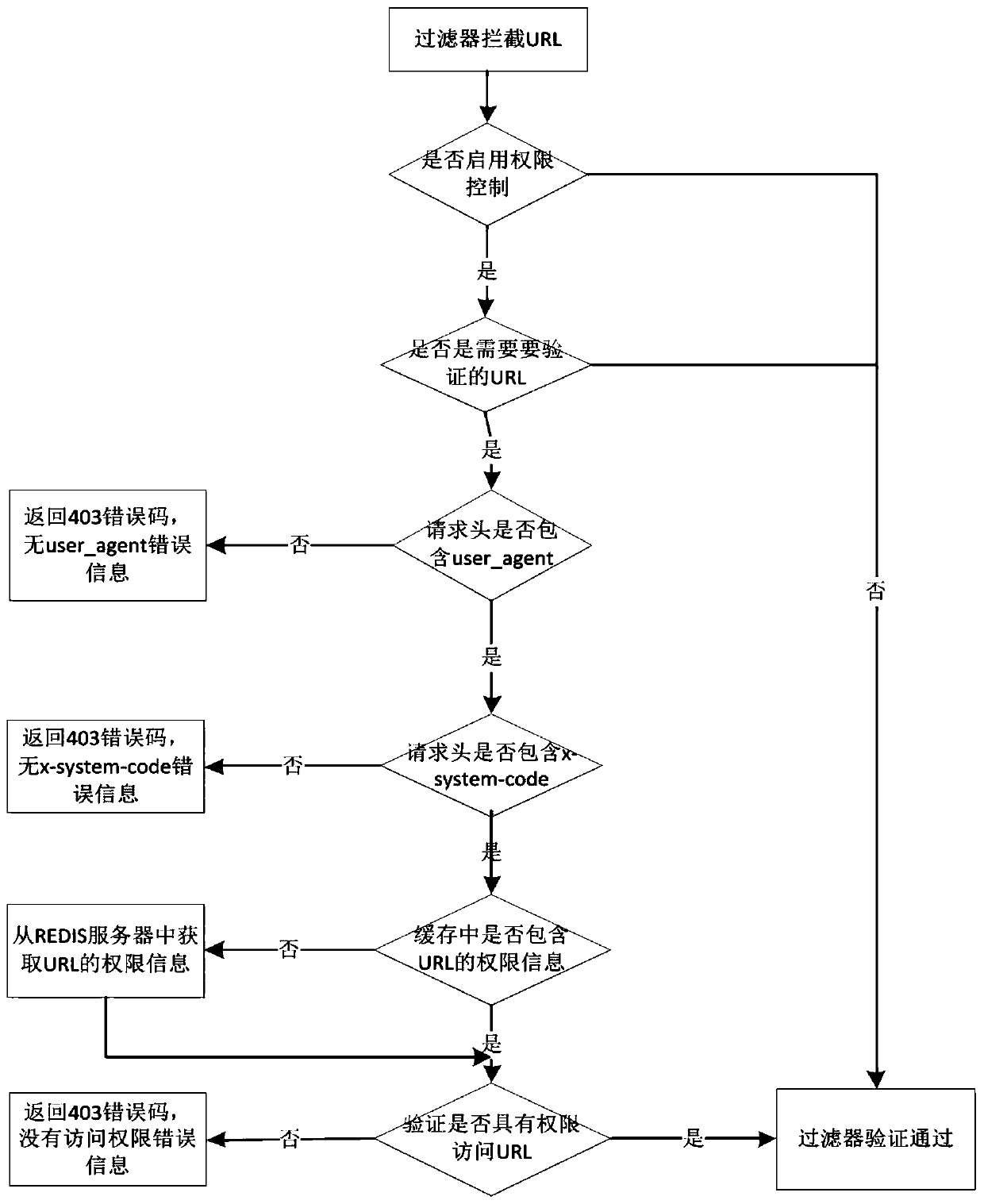
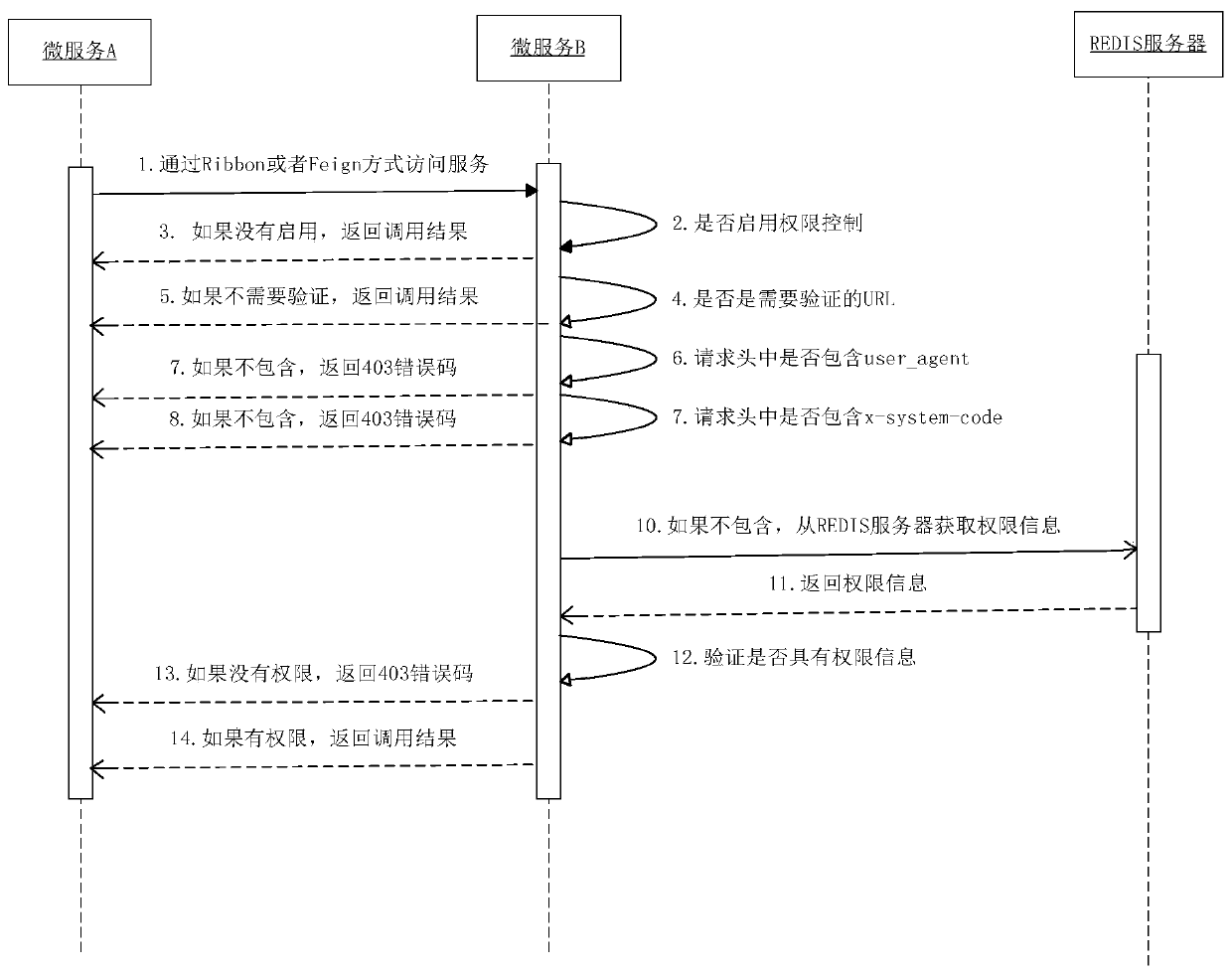
A service calling permission control method based on a micro-service architecture
PendingCN109948356APrevent illegal service callsEliminate security risksDigital data protectionTransmissionAuthority controlAuthorization
The invention discloses a service calling permission control method based on a micro-service architecture. The method is used for service authorization and service calling permission control of a micro-service registered based on a registration center. The micro-service support platform provides a micro-service authorization operation function, and authorities are stored in the Oracle and the Redis; pushing the authority to an authorization micro-server through a subscription release mechanism provided by the Redis, and carrying out authority verification control; the method comprises the steps of micro-service authorization operation, authority storage and release, authority control and authority control client jar package use. According to the invention, authority control is carried outon the micro-service registered based on the registration center through authorization, illegal service calling is prevented, and the interface calling security risk is completely eradicated.
Owner:JIANGSU ELECTRIC POWER INFORMATION TECH
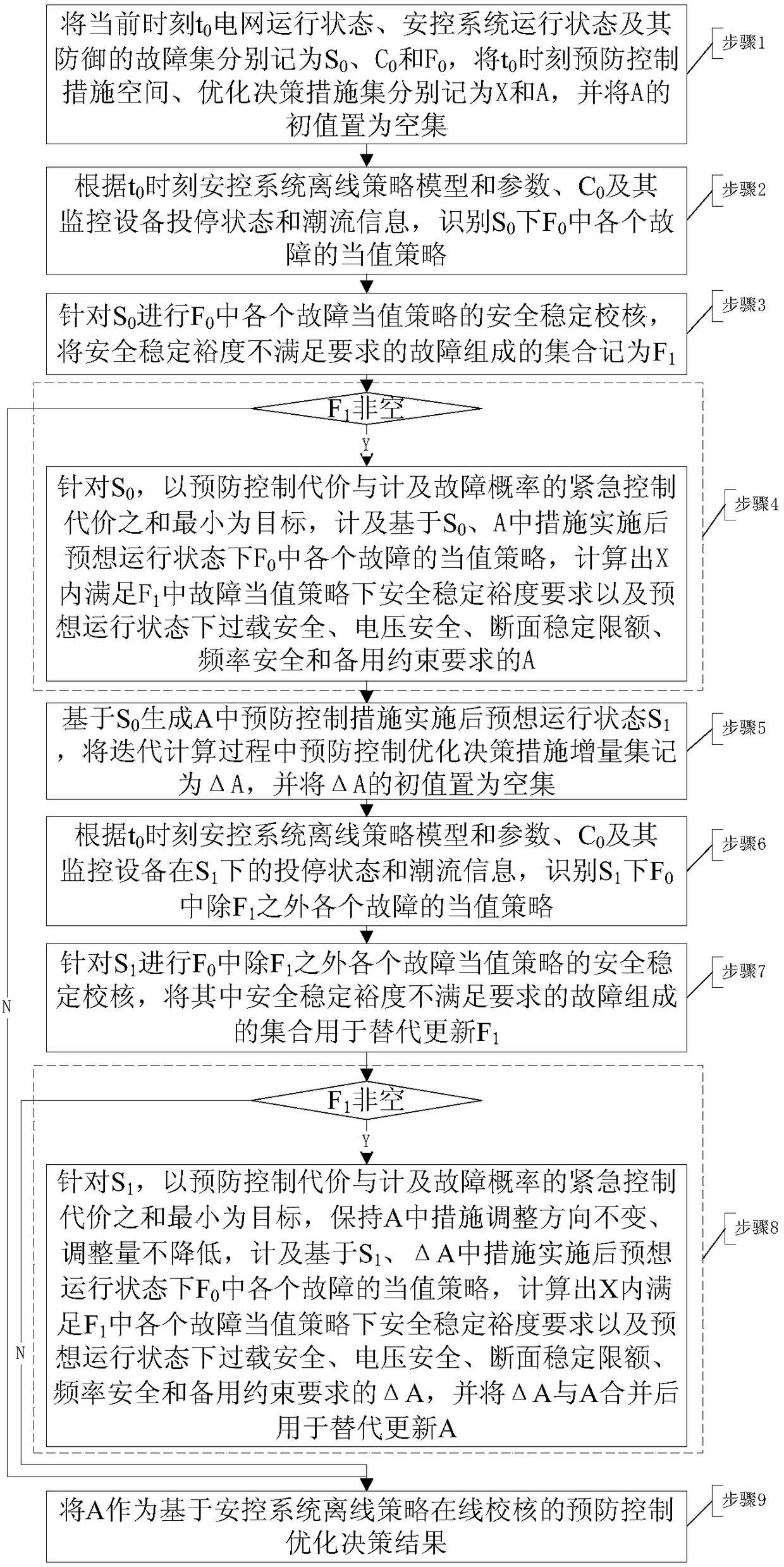
Prevention and control optimization decision method based on offline strategy online check of security control system
ActiveCN108847660AEliminate security risksAvoid security risksAc network circuit arrangementsPower gridModel parameters
The invention discloses a prevention and control optimization decision method based on offline strategy online check of a security control system. Firstly, according to the real-time status of the security control system and the offline policy model parameters, the on-duty strategy of each defended fault is identified; and then, aimed at the real-time status of the grid, security check is carriedout on each fault on-duty strategy, and the fault with transient or dynamic or static security and stability margin is used as a risk fault; after that, aimed at the real-time status of the grid, theminimum of the sum of the prevention and control cost and the emergency control cost of fault probability is taken as an objective function to calculate a prevention and control optimization decisionthat satisfies the security and stability requirements of the grid under all risk faults; the security check of other faults defended by the security control system is carried out for the prevention and control optimization decision, until, through iteration, all the faults defended by the security control system under the prevention and control optimization strategy meet the requirements of secure and stable operation of the grid after the faults, thereby avoiding the grid security risk of insufficient offline strategy control quantity or mismatch.
Owner:NARI TECH CO LTD +2
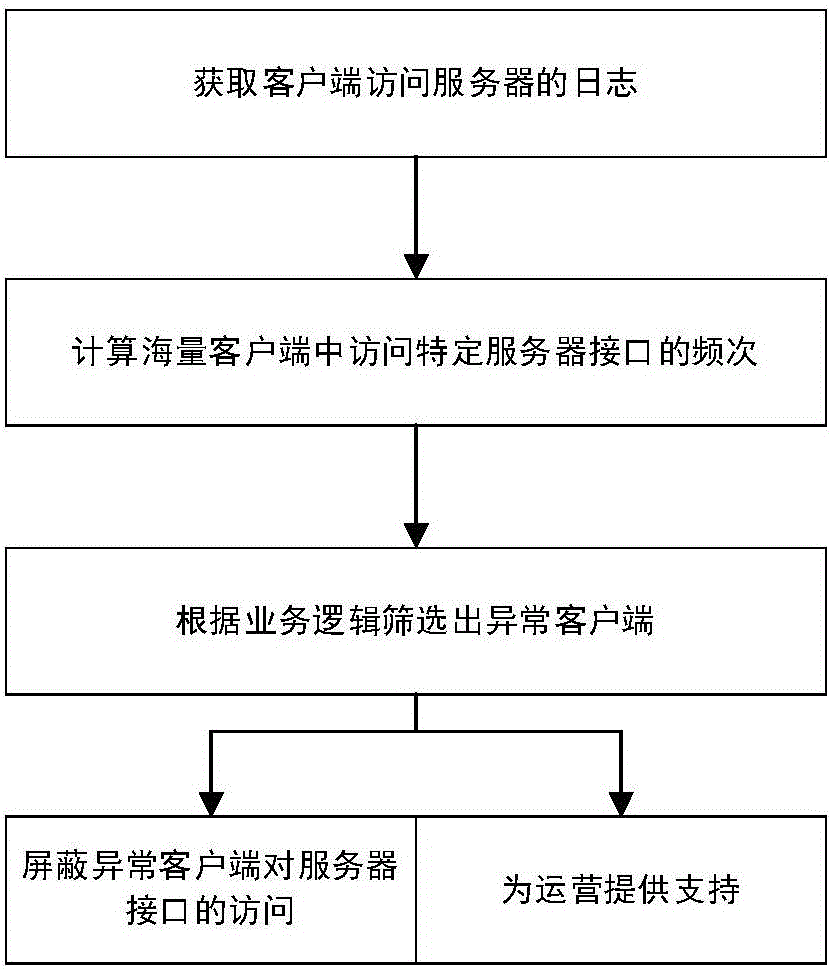
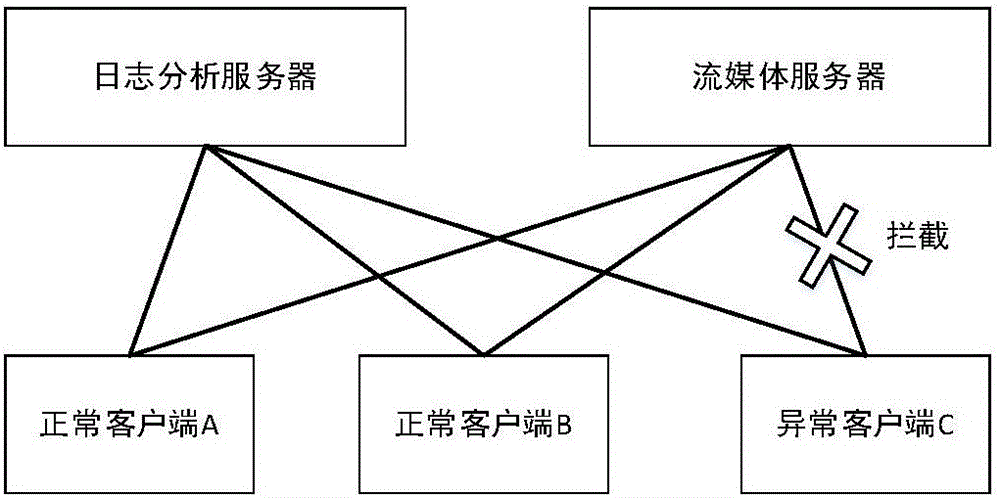
Statistics-based abnormal interface access recognition method
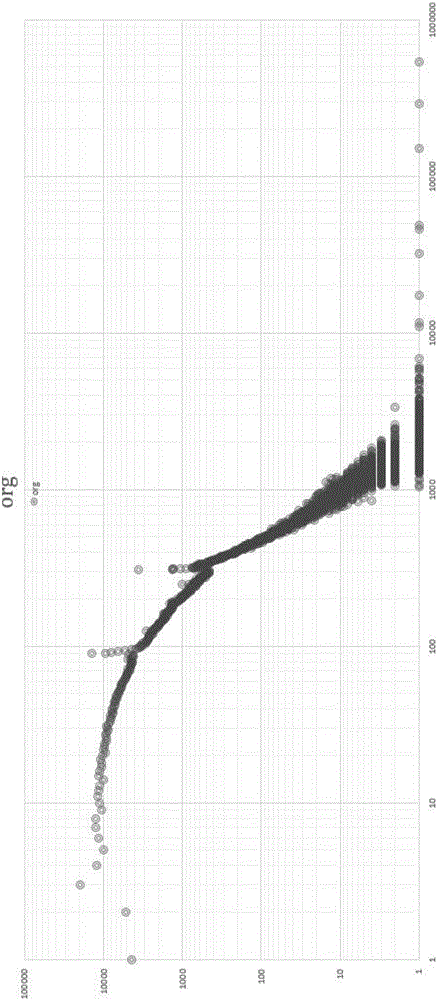
ActiveCN106209781AEffectively identify abnormal usage behaviorAbnormal usage behavior shieldingTransmissionRelation graphAccess frequency
The invention relates to a statistics-based abnormal interface access recognition method, comprising the following steps: step 1, acquiring, by a server, a log that a client accesses the server to form a historical record; step 2, analyzing, by the server, the log that the client accesses the server to obtain a relation graph of access frequencies and the number of users of each interface; step 3, acquiring a relation between access frequencies and the number of the users of a specific interface; step 4, analyzing an abnormal value in the relation between access frequencies and the number of the users; step 5, automatically judging the abnormal access type according to the abnormal value; and step 6, correspondingly processing the abnormal access type. According to the method, statistical analysis is performed on massive client logs, so that user's abnormal use behaviors of illegally accessing the server through the client can be effectively recognized, and an operation support can be provided for operators, wherein the operation support provides a basis for improving products according to the recognized user's abnormal use behaviors in order to eliminate the security risk and shield the user's abnormal use behaviors.
Owner:北京航天云路有限公司
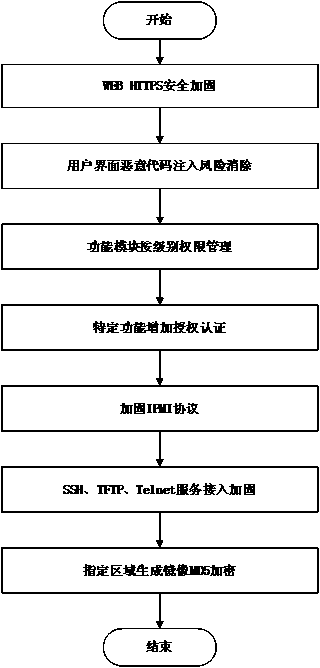
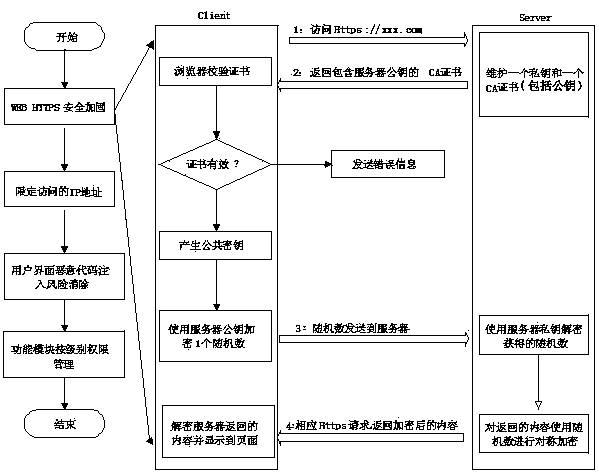
Server-oriented safe firmware designing method
ActiveCN103944913AImprove securityImprove effectivenessInternal/peripheral component protectionTransmissionThird partyUser Privilege
The invention provides a server-oriented safe firmware designing method. The safety of firmware used for a server is guaranteed through various measures, and the remote WEB access safety of the server is mainly guaranteed through an Https-access mode. Access safety of users of different authority levels is controlled by managing the user authority of a function module, and malicious code injection points in an access interface are blocked. User names and passwords in firmware compiling and mirror image generating processes are subjected to an MD5 encryption algorithm, so that user information safety is improved. Safety protecting is carried out in the mode that authority is added to a module with a specific function and License is given to the module with the specific function. Third-party IPMI access safety is enhanced by shutting down the functions related to user authority adding, modifying and default in an IPMI protocol. External access safety of server firmware is enhanced by shutting down an access service program in a system.
Owner:LANGCHAO ELECTRONIC INFORMATION IND CO LTD
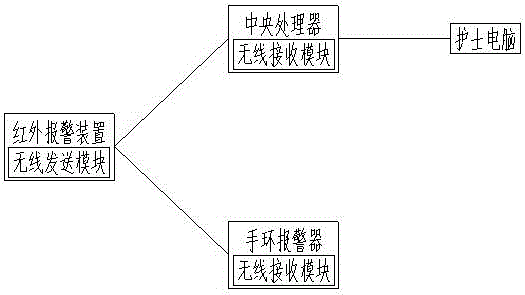
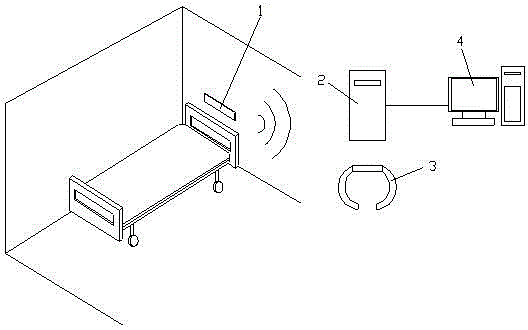
Intelligent anti-fall off-bed alarm system
InactiveCN106652348AEliminate security risksAccurate receptionAlarmsTelecommunicationsIntelligent agent
The invention discloses an intelligent anti-fall off-bed alarm system comprising an infrared alarm device, wherein the infrared alarm device is fixedly installed on a wall right above a bedside or on the bedside, a wireless sending module is built in the infrared alarm device, the infrared alarm device is separately connected with a central processor and a bracelet alarm through a wireless network, wireless receiving modules are built in both of the central processor and the bracelet alarm, and the central processor is connected with a nurse computer through the network. The intelligent anti-fall off-bed alarm system disclosed by the invention has the advantages of being convenient to use and able to effectively monitor off-bed of a monitoring object and notify medical care personnel on duty or chaperonage personnel in time so as to take subsequent service measures, the safety risk caused by failure of timely handling after the off-bed of the monitoring object is eliminated, the alarm mode is adjusted to a vibration mode during chaperonage at night, and the chaperonage personnel are reminded in a point-to-point mode, therefore the alarm information can be received more accurately, and the influence to the normal rest of the personnel on the surrounding during the alarm is avoided.
Owner:AFFILIATED HOSPITAL OF NANTONG UNIV
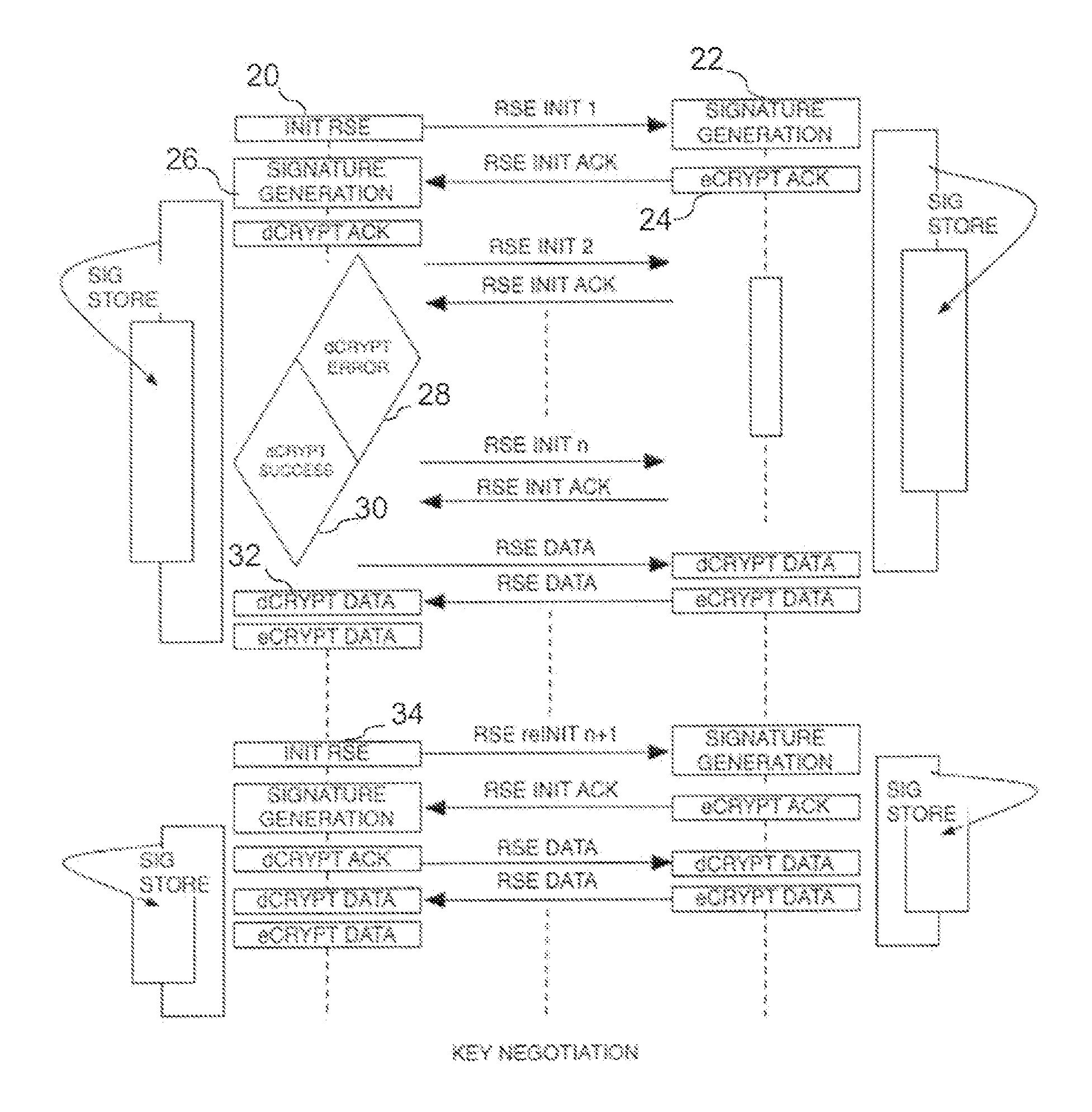
Radio scene encryption and authentication process
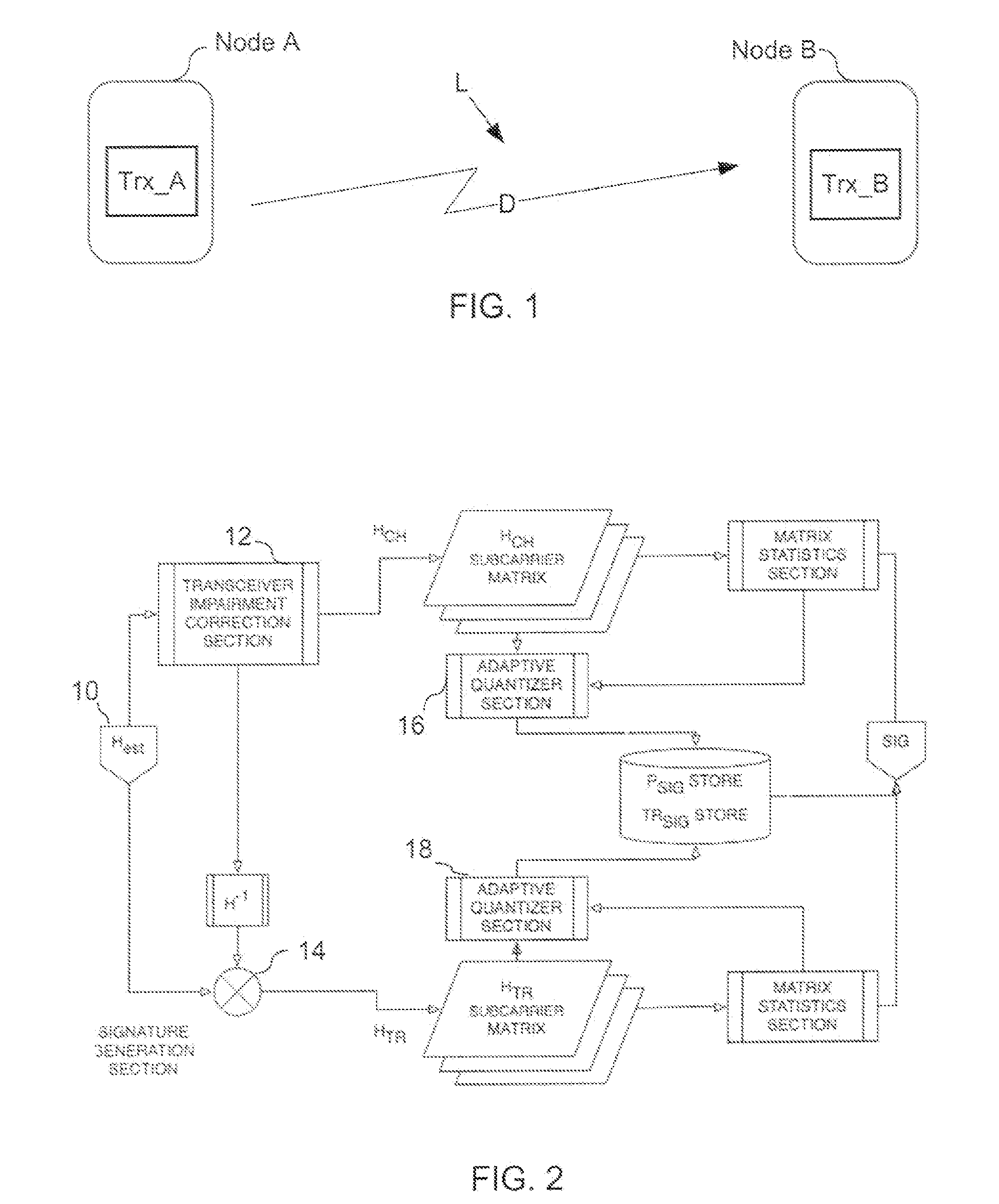
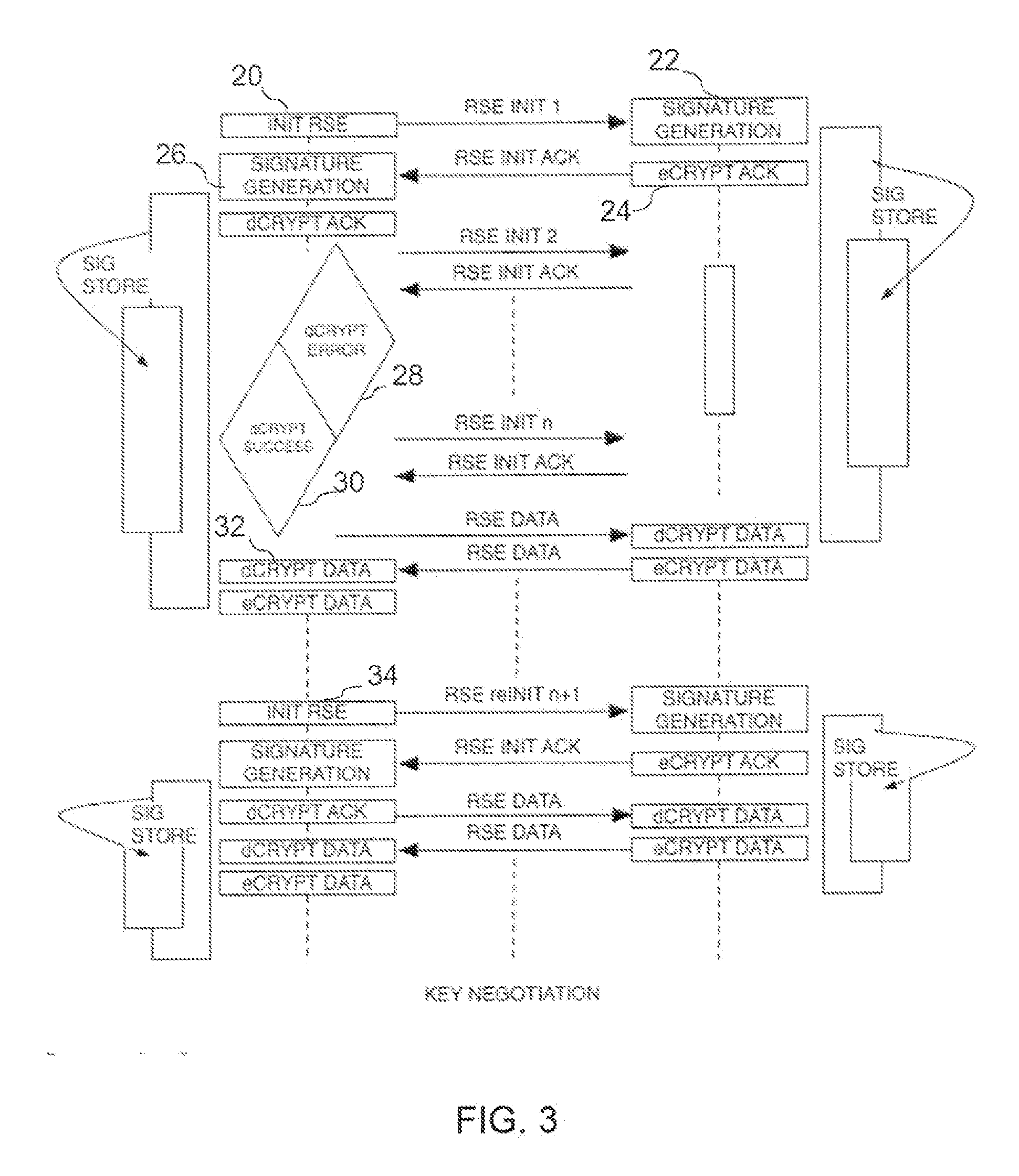
InactiveUS20100146289A1Reduce overheadReduce riskUser identity/authority verificationSecret communicationTelecommunications linkCommunications system
A method is provided for encryption / decryption for secure the privacy of the information flow between two communicating nodes, and authentication to establish the identity of the communicating nodes in digital communications systems. A common secret or encryption key is generated at the two nodal ends of the communication link without prior dissemination. The authenticity of the communicating entities are maintained over time based on unique non-idealities of the communicating nodes in conjunction with the propagation characteristics of a link between them.
Owner:STEVENS INSTITUTE OF TECHNOLOGY
External slanted type steel box arch installing method
ActiveCN104652281AEliminate security risksReduce quality control riskBridge erection/assemblyArch-type bridgeJackscrewArchitectural engineering
The invention discloses an external slanted type steel box arch installing method, which belongs to the technical field of the bridge construction. The external slanted type steel box arch installing method includes the following steps: an arch rib and an arch section are operated to complete turning to the side and turning over on the ground; after the arch section is lifted on a bracket at the top of a support, the fine adjustment of the accurate positioning of the arch section is performed through a trim holder arranged at the top of the support, a support top bracket and a jack; after the position of the arch section is adjusted in place, the temporary welding positioning measure is performed, and the arch section positioning and installing are completed. The optimized less support method according to the invention has the advantages that the posture adjusting process is performed on the ground, meanwhile, the arch section is accurately positioned though the trim holder, the support top bracket and the jack, the high altitude construction safety risk is eliminated, the quality control risk is lowered, the construction operation is convenient, the construction speed is fast, and the construction period can be saved about 30 days compared with the traditional less support method.
Owner:CHINA RAILWAY NO 2 ENG GRP CO LTD +1
Self-service double-gate customs clearance security inspection device and customs clearance security inspection method therefor
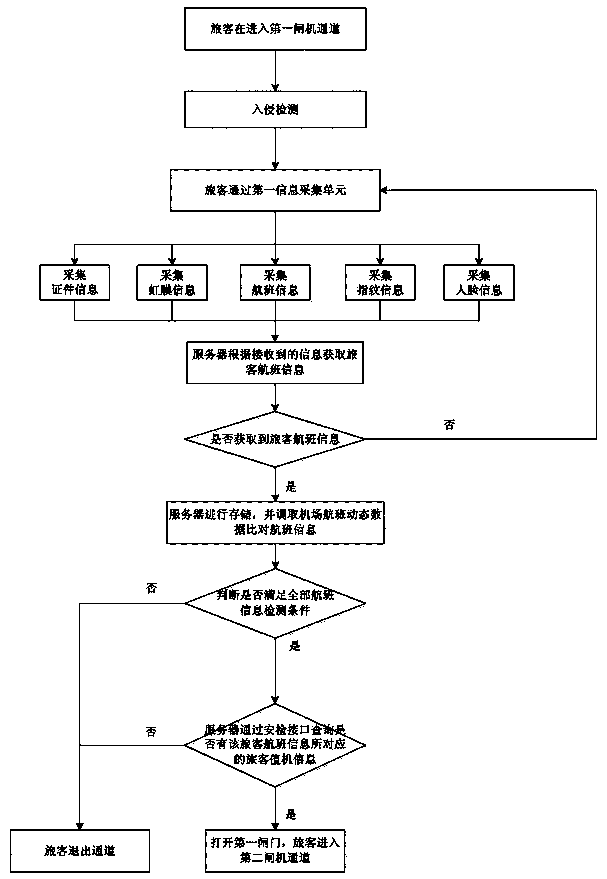
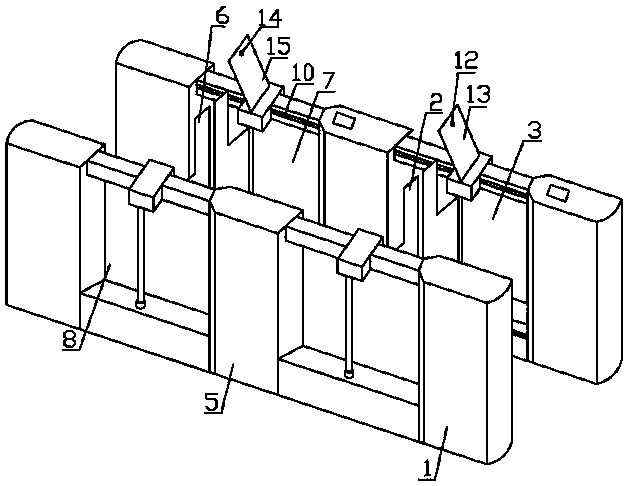
PendingCN109300204ASimple structureSimple methodIndividual entry/exit registersSelf-serviceDouble gate
The invention relates to the technical field of customs clearance security inspection, and is a self-service double-gate customs clearance security inspection device and a customs clearance security inspection method therefor. The former comprises a control unit, a first gate machine, and a second gate machine. The first gate comprises a first gate machine portion and a first gate located behind the first gate machine portion, wherein a first protective baffle is disposed between the first gate machine portion and the first gate, and a forward intrusion detection unit is mounted on the inner side wall of the first protective baffle. The second gate machine comprises a second gate machine portion and a second gate, wherein second protective baffles are disposed between the second gate machine portion and the first gate, and between the second gate machine portion and the second gate, and a second information collecting unit is mounted on the gate machine portion, and a trailing detecting unit is mounted on the inner side wall of the second protective baffles. According to the self-service double-gate customs clearance security inspection device and the customs clearance security inspection method therefor, the problems of low efficiency and easy to cause false detection in the existing manual security inspection mode can be solved, which can effectively identify passengers and baggage, effectively reduce the false detection rate of the trailing detection, improve the efficiency of passing, identify the control personnel at the same time , and help eliminate security risks.
Owner:新疆民航凯亚信息网络有限责任公司
Paper money, coin and cash service device and method of internet payment (financial) account
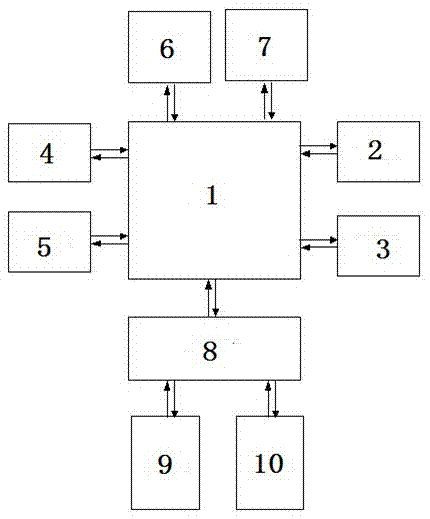
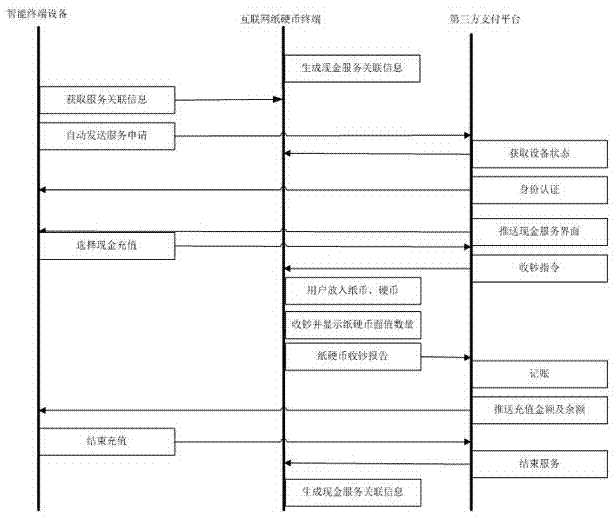
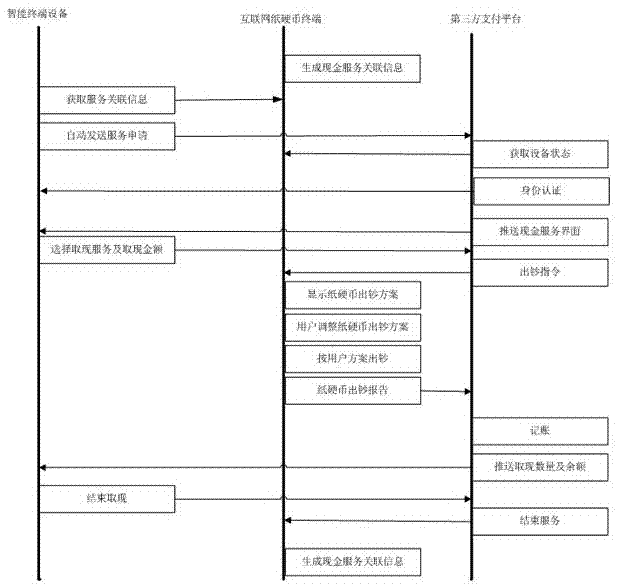
InactiveCN105447685ASpeed up circulationRich payment needsComplete banking machinesPayment protocolsPrivate networkComputer module
The invention discloses a paper money, coin and cash service device of an Internet payment (financial) account; an instruction controller is respectively in two-way linkage with a WIFI module, a communication module, a Bluetooth module, an NFC module, a touch screen, a display and a cash box controller; the cash box controller is connected to a paper money module and a coin module; the device automatically generates cash service associated information; the cash service associated information is obtained by a hand-held terminal; a third party payment platform is logged in; identity authentication is carried out; a service interface is logged in; service is selected; after the device receives the selection instruction of the user by a private network, the display displays prompt information, the user operates according to the prompt; the third party payment platform keeps accounts and pushes operation amount of money and account balance, the user sends an ending request to the third party payment platform; the third party payment platform sends an ending instruction to the device; after finishing the service, the device generates new cash service associated information; convenient, high efficient and safe cash service is provided for various internet financial accounts.
Owner:王义海 +3
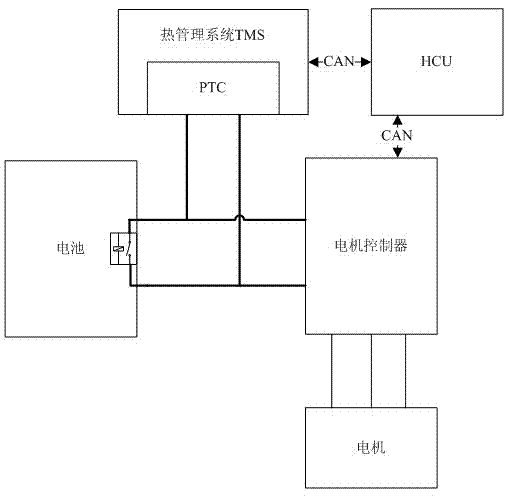
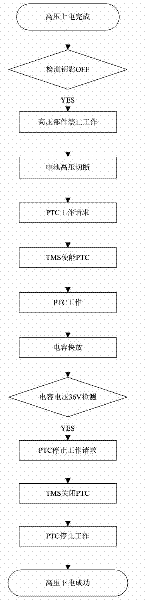
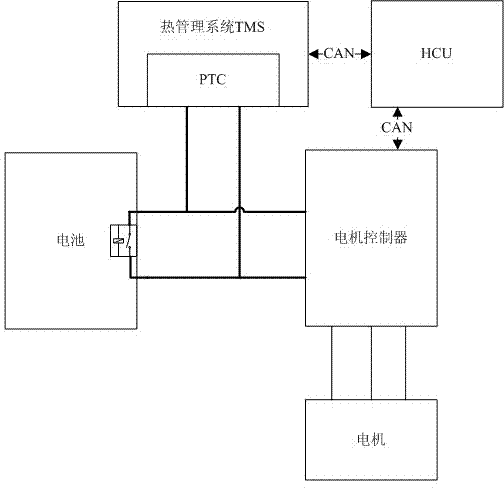
Series connection stroke increment type electric automobile high-voltage electricity quick-discharge control method
The invention discloses a plug-in automobile high-voltage electricity quick-discharge control method. The main scheme adopted in the method is as follows: in the electricity discharge process of a finished automobile, the work of a pitch trim compensator (PTC) arranged in a thermal management system is controlled by the harmonious work of a hybrid control unit (HCU) and the thermal management system, and the high-voltage electricity in the capacitor of a motor can be rapidly discharged to be safe voltage. In the method, the normal operation of all critical components in the high-voltage electricity discharge process of the finished automobile is not influenced; and the method is rapid in response and simple in control of the whole quick-discharge process, and is capable of rapidly discharging the high-voltage electricity in high-voltage parts to be safe voltage in the electricity discharge process of the finished automobile so as to eliminate high-voltage security risks.
Owner:CHONGQING CHANGAN AUTOMOBILE CO LTD +1
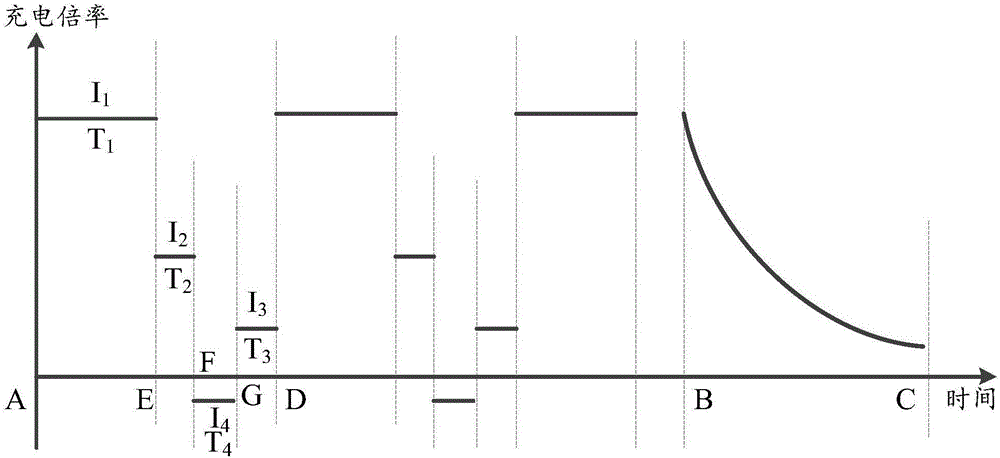
Charging method and device
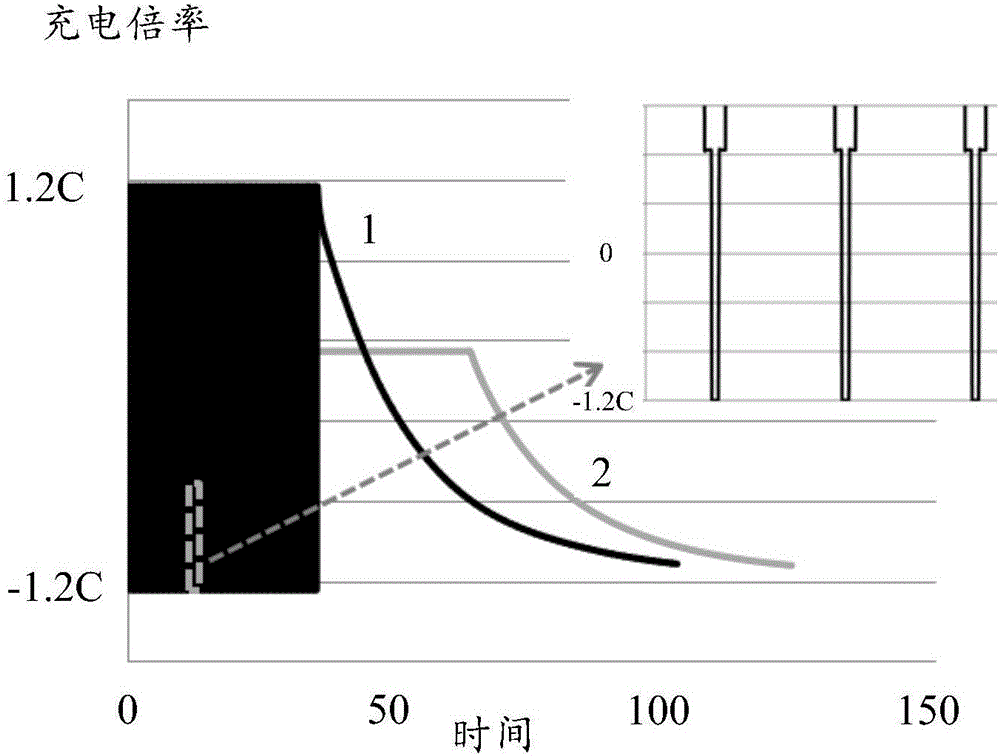
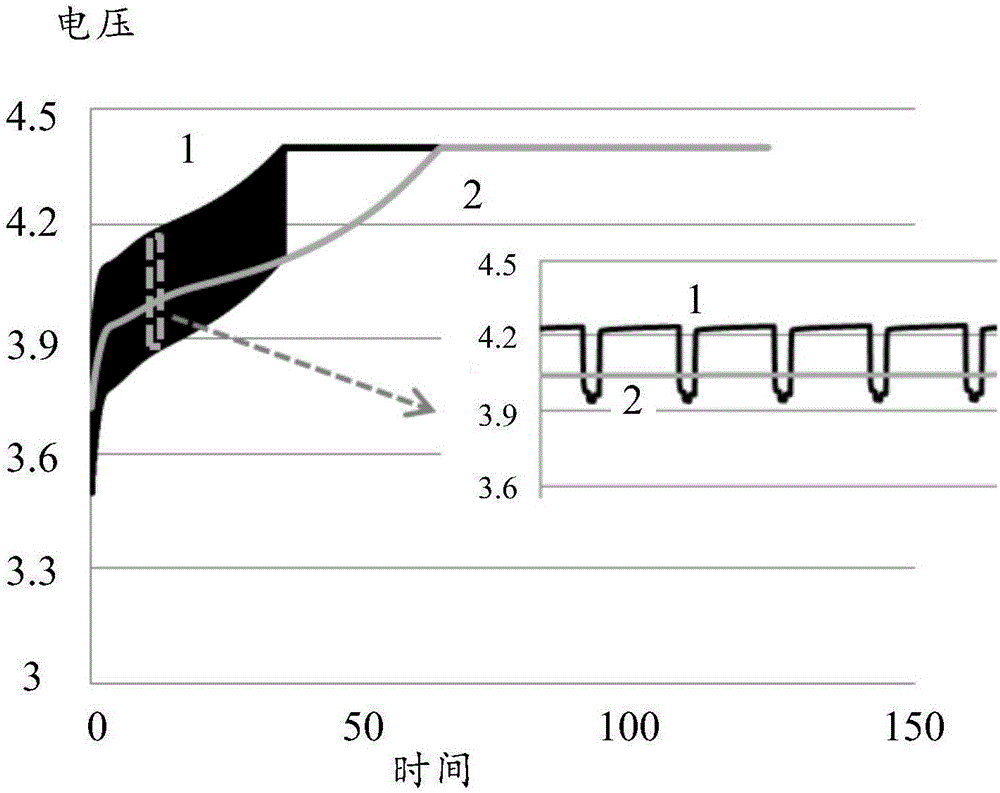
InactiveCN106785144AReduce polarizationDepolarizationSecondary cells charging/dischargingElectronConstant current
The embodiment of the invention provides a charging method and device. The charging method is characterized in that the charging for a battery includes a first charging stage and a second charging state, wherein the first charging state comprises at least two charging sub-steps; the battery is sequentially subjected to first constant-current charging, second constant-current charging, constant-current discharging and third constant-current discharging in each charging sub-step; the battery is subjected to constant-voltage charging in the second charging state. According to the technical scheme provided by the embodiment of the invention, the charging method and device can solve the problem of high safety risk, caused by the increase of the charging speed, of the battery in an existing charging method, can be solved.
Owner:NINGDE AMPEREX TECH
Forming method of 3D curved glass, forming system and 3D curved glass
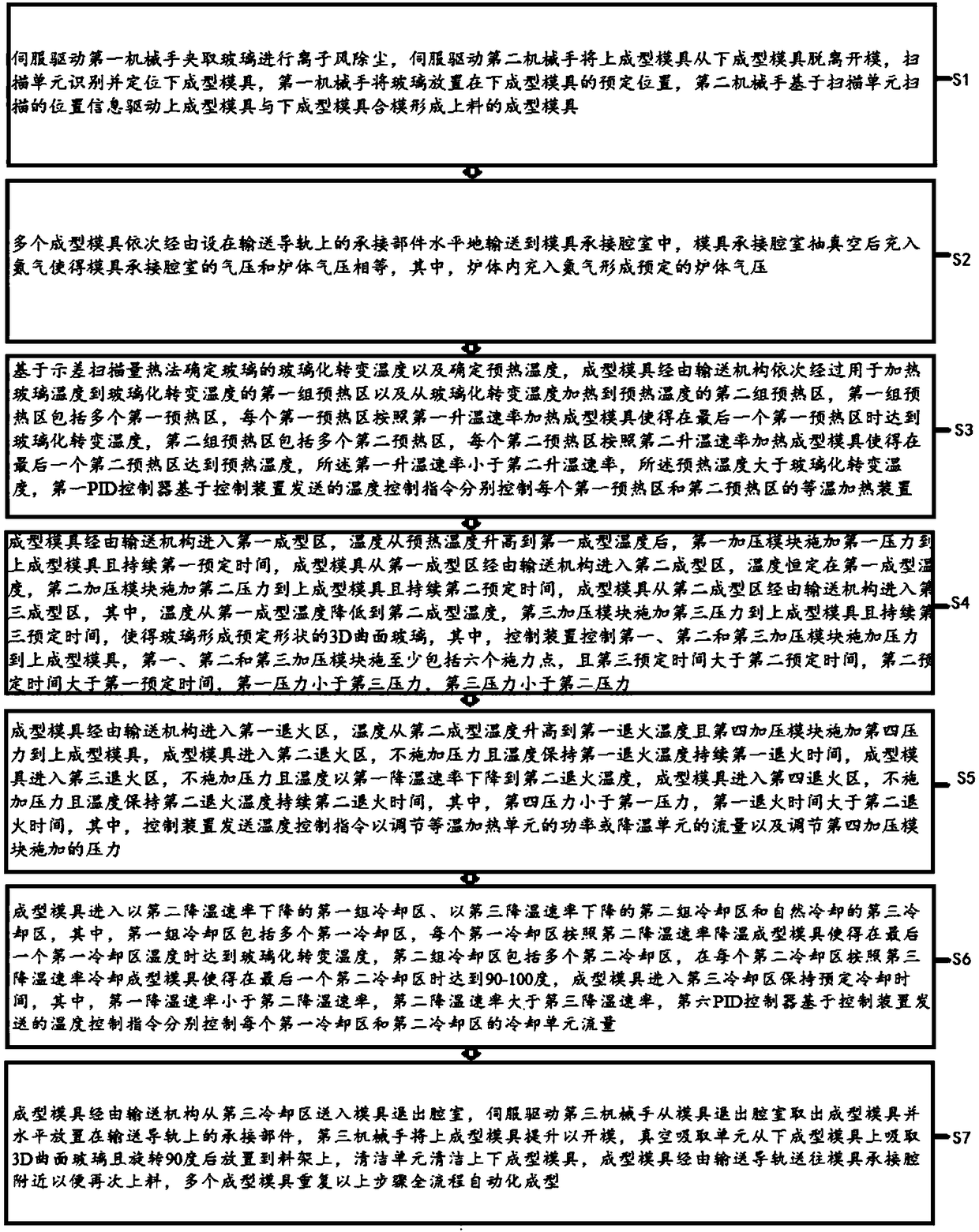
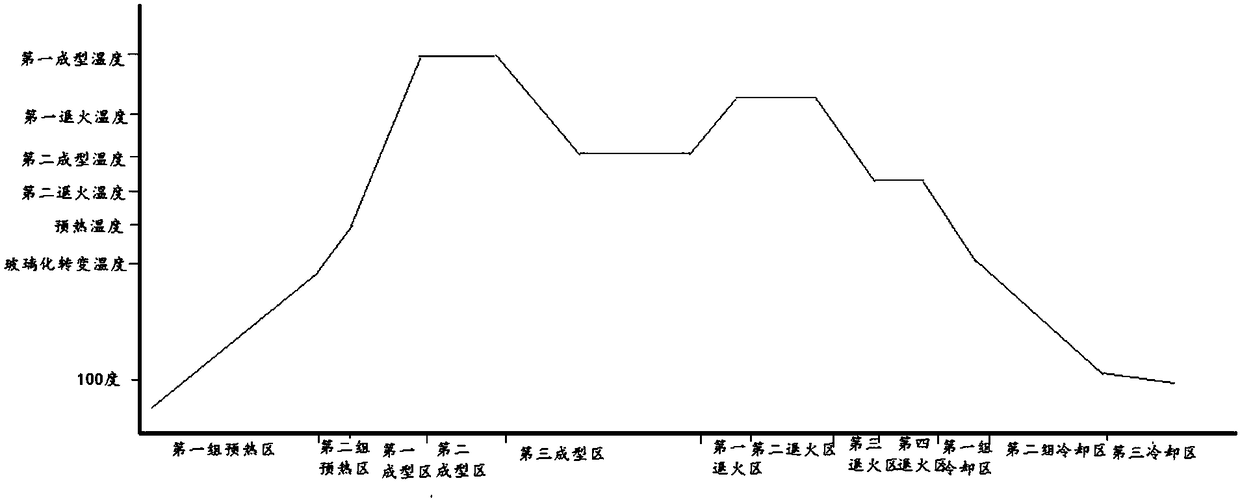
InactiveCN108585452AAvoid the risk of splinteringSoften evenly and fullyGlass reforming apparatusNitrogenEngineering
The invention discloses a forming method of 3D curved glass, a forming system and the 3D curved glass. The forming method of the 3D curved glass comprises the following steps: a second manipulator (2)performs die assembling on the basis of position information scanned by a scanning unit (5) to form forming dies (6) for loading materials; the multiple forming dies (6) are horizontally conveyed into a die carrying cavity (8) in sequence; after being vacuumized, the die carrying cavity (8) is filled with nitrogen to enable gas pressure in the die carrying cavity (8) to be equal to that of a furnace body (9); the forming dies (6) pass through a first group of preheating regions (10) for heating glass from a temperature to a glass transition temperature and a second group of preheating regions(11) for heating the glass from the glass transition temperature to a preheating temperature in sequence through a conveying mechanism; after being formed, annealed and cooled, the forming dies (6) are conveyed to a position near to the die carrying die (8) through a conveying guide rail (7) for material reloading; the multiple forming dies (6) are repeatedly subjected to the processes to realizeautomatic forming in the whole procedure.
Owner:深圳市太平洋自动化设备有限公司
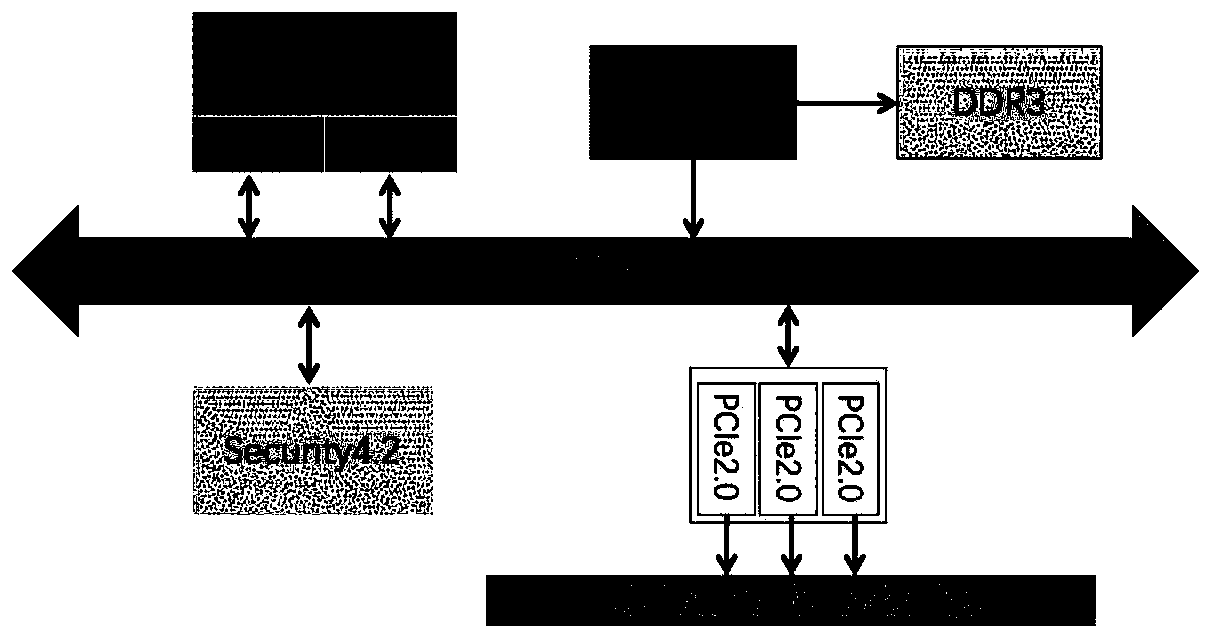
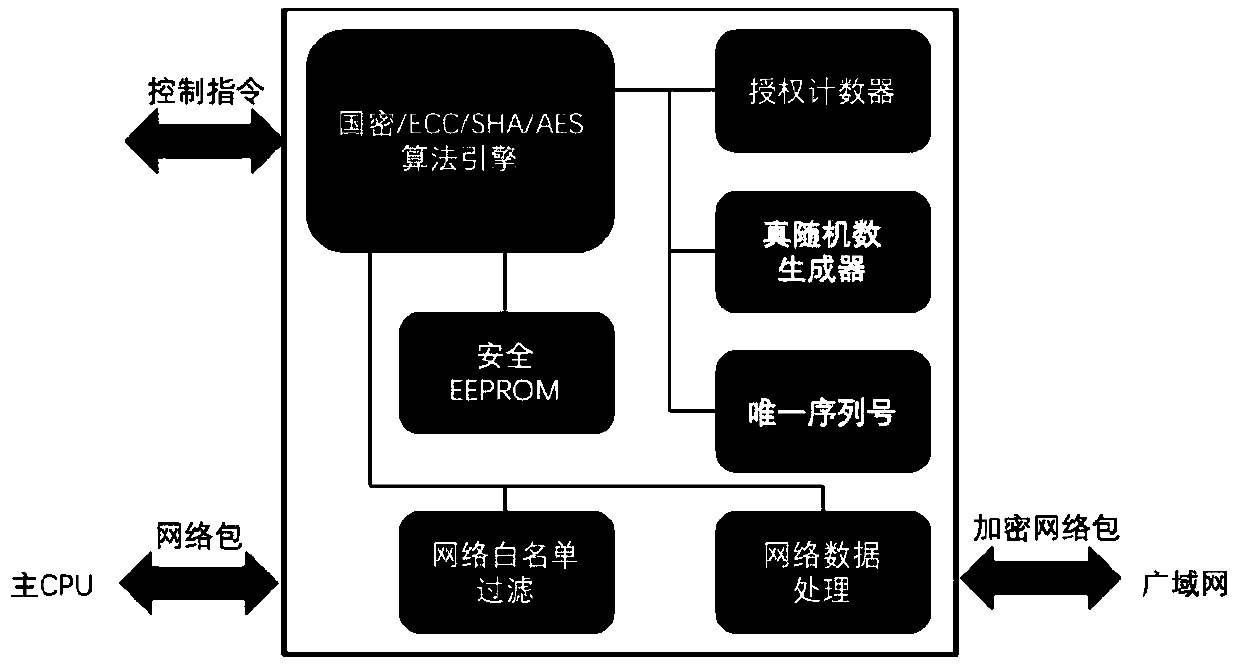
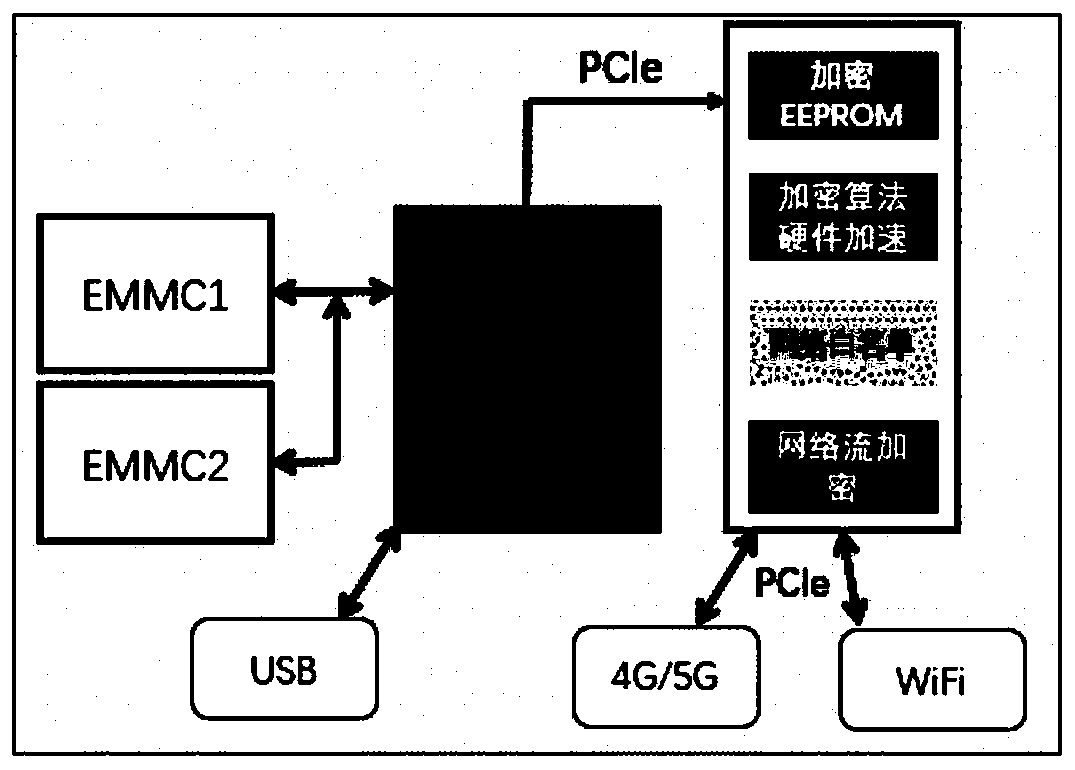
Security chip for protecting network security system and network security system using same
InactiveCN110430178AHigh speed encryptionHigh speed recoveryKey distribution for secure communicationUser identity/authority verificationCommunications securityData stream
A security chip for protecting a network security system comprises a data security part for providing a secure encryption and decryption algorithm and an interaction protocol, wherein the data security part mainly comprises an encryption and decryption algorithm control engine, an authorization counter, a true random number generator, a unique serial number and a secure EEPROM; and a network security part composed of a network white list filtering module and a network data processing module. The encryption and decryption algorithm control engine comprises private key security storage for supporting private key ECDH operation and ECDSA signature authentication. The mainstream national password and commercial password encryption and decryption algorithms perform high-speed encryption and reduction on the data stream so as to adapt to the security requirements of different scenes. The chip safety management supplies power, manages the read-write ROM on the chip, allows special equipment to write, and allows remote erasure but does not allow reading. The invention also provides a network security system using the security chip. The sensitive data communication security can be protectedfrom the hardware level, and the efficiency can be greatly improved while the system security is improved.
Owner:XI AN JIAOTONG UNIV
Desulfurizing system and method for biogas containing high-concentration hydrogen sulfide
ActiveCN108579373ASatisfy the utilizationReduce the concentration of hydrogen sulfideGas treatmentDispersed particle separationHigh concentrationGas detector
The invention relates to a desulfurizing system for biogas containing high-concentration hydrogen sulfide. The desulfurizing system comprises a biogas inlet, a biogas flowmeter, a biogas cabinet, a wet-process desulfurizing tower, a gas-water separator, a plurality of dry-process desulfurizing towers in serial connection or parallel connection, an outlet gas detector, a biogas fan and a biogas utilization pipeline which are sequentially communicated through biogas, and both spraying liquid after being treated by the wet-process desulfurizing tower and liquid of the gas-water separator enter adesulfurizing liquid regeneration and treatment device. The desulfurizing system combines wet-process desulfurizing with dry-process desulfurizing, and concentration of hydrogen sulfide can be loweredfrom higher than 20000ppm to below 100ppm to meet biogas energy utilization needs. the desulfurizing system is low in running cost, economic benefit can be generated utilizing biogas after being treated by the system, and generated byproducts can be sold as goods, so that many things are achieved at one stroke.
Owner:华夏碧水环保科技股份有限公司
Asymmetric FHE (Fully Homomorphic Encryption) method and secret key substitution and cipher text delivery methods thereof
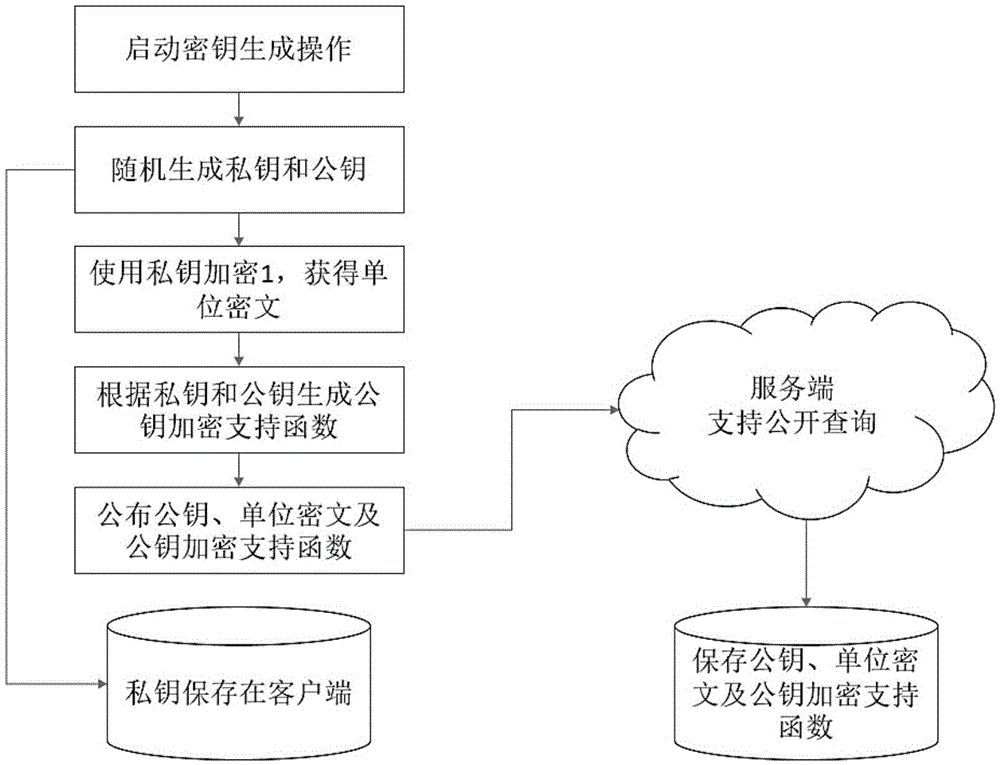
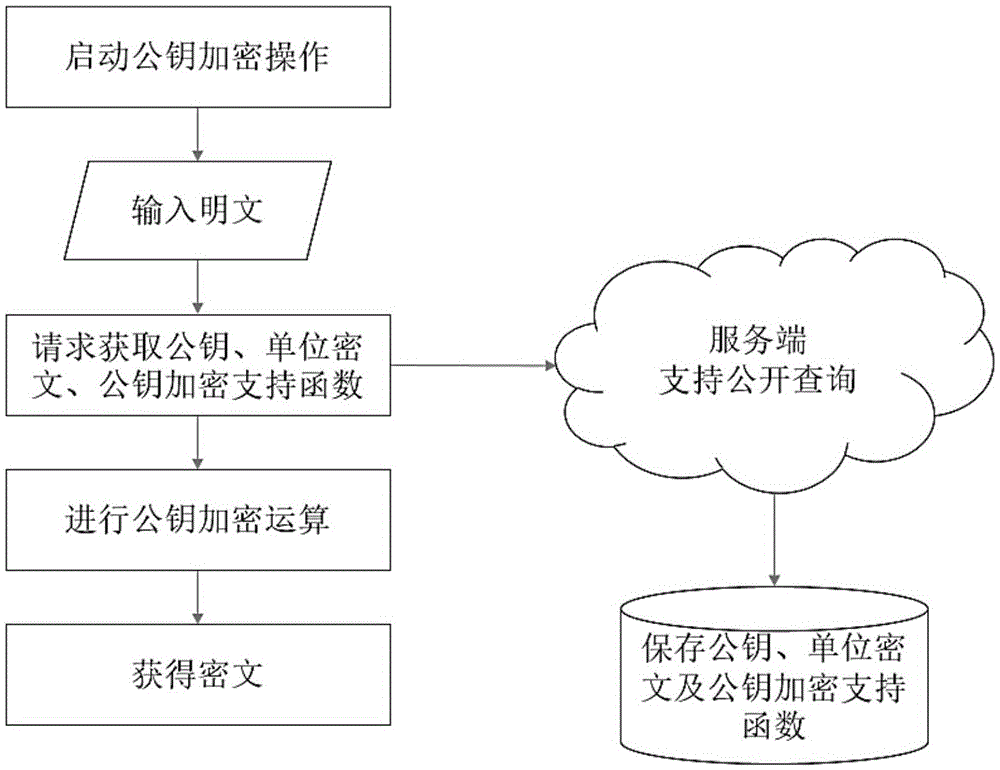
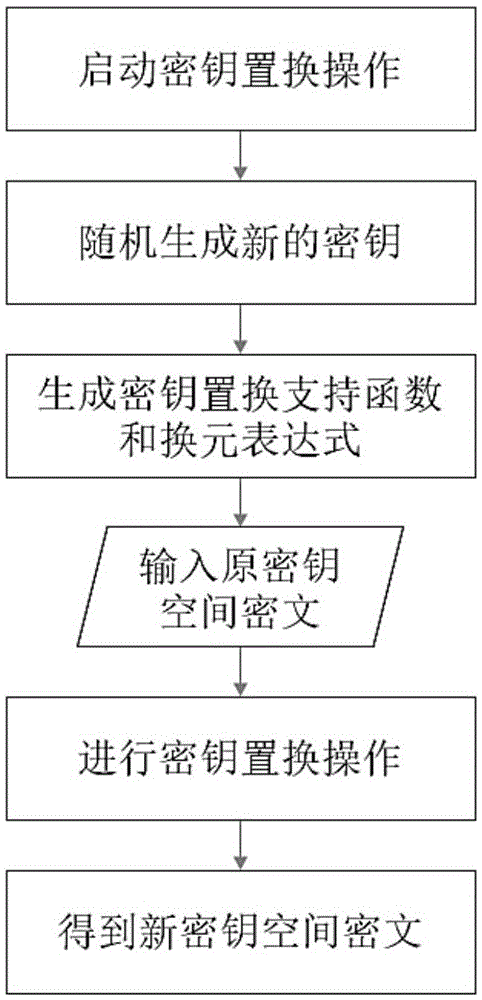
ActiveCN107181584AOverall small sizeLow speedKey distribution for secure communicationCommunication with homomorphic encryptionPlaintextNon symmetric
The invention relates to an asymmetric FHE method and secret key substitution and cipher text delivery methods thereof. A private key and a public key are generated randomly, and the secret key is used to generate an operation support function, a unit cipher text of secret key encryption and a public key encryption operation support function; a plaintext is encrypted to generate a cipher text, namely, the secret key is used for encryption directly to obtain a direct cipher text, or the public key corresponding to the secret key is used to carry out encryption operation to obtain a compatible cipher text in the same secret key space; and when the cipher text needs to be delivered to the receiving end safely, the sending, receiving and server ends or the sending and receiving ends complete delivery of the cipher text. Operation of the cipher text is carried out directly without leakage of the plaintext, a safe data storage and operation environment is provided, the computing speed is improved substantially compared with the prior art, the required cipher text volume and expansion speed are lower, the methods can be realized in different manners, and a data owner can use different cloud computing services needless of worrying about leakage of sensitive and secrete data.
Owner:上海麟羿信息科技有限公司
Steel reinforcement cage overall precast scaffold for wide pier body of cross-sea bridge
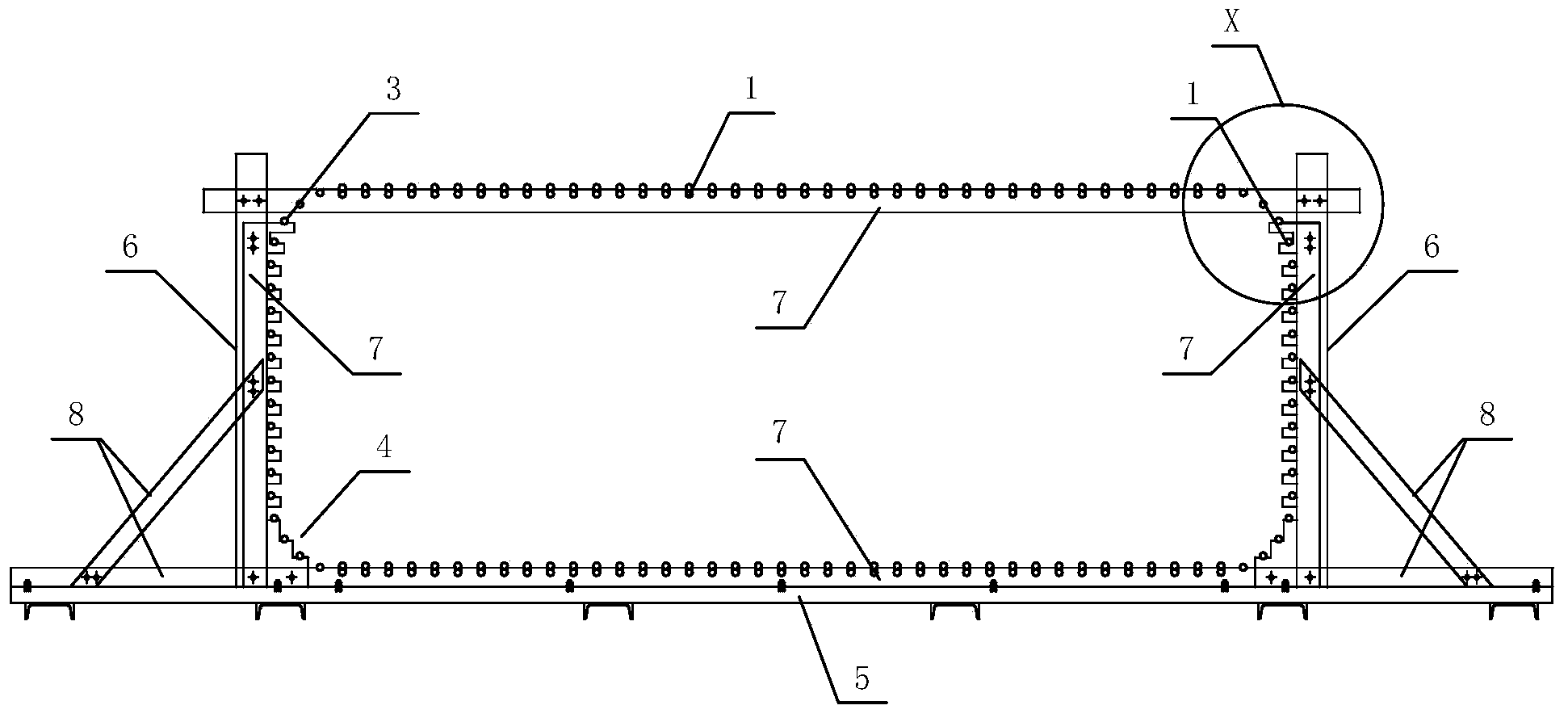
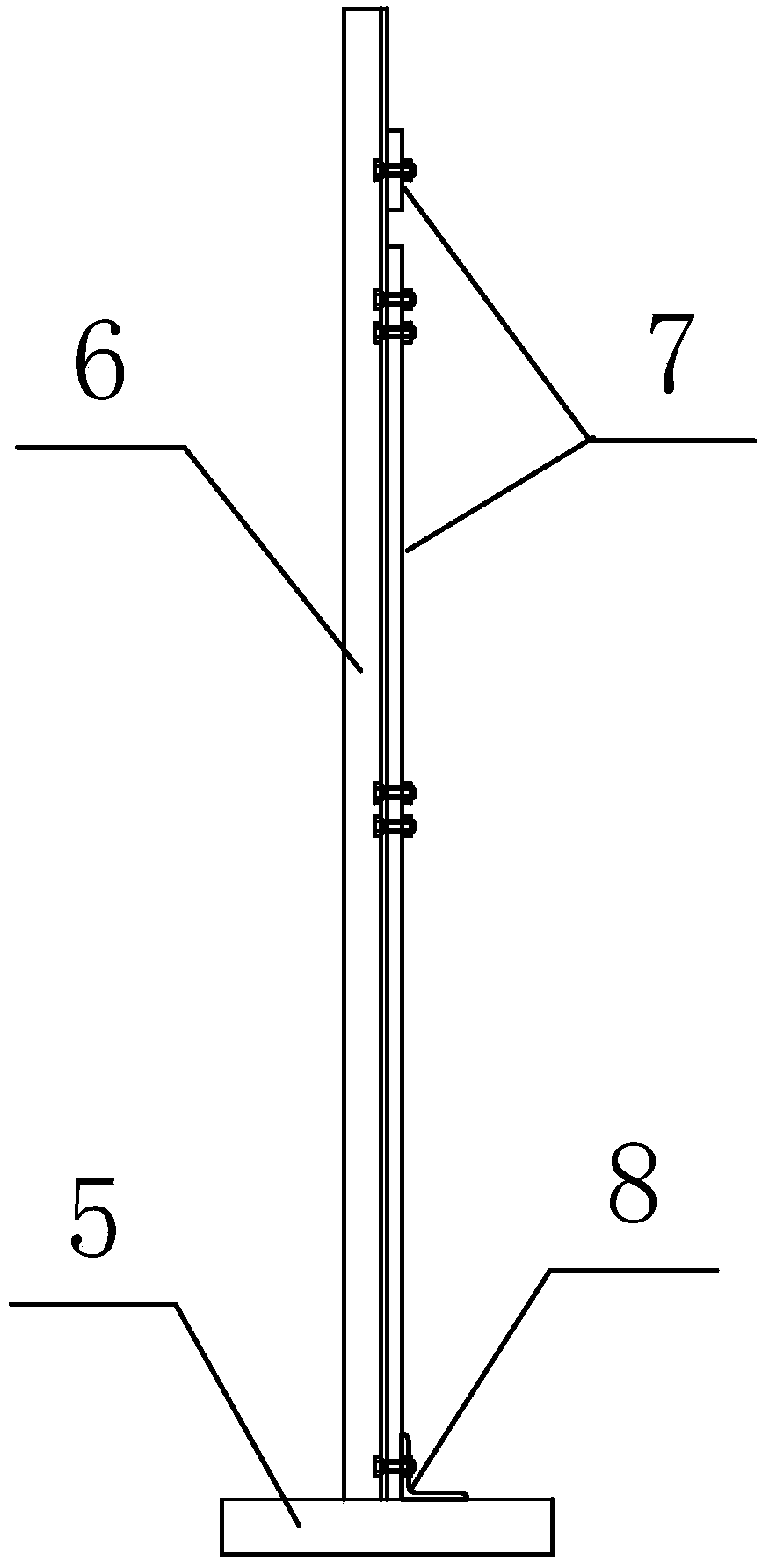
ActiveCN103924526AImprove working environmentQuality is easy to controlBridge erection/assemblyRebarBuilding construction
The invention discloses a steel reinforcement cage overall precast scaffold for a wide pier body of a cross-sea bridge, and belongs to the field of under bridge component construction tools. The steel reinforcement cage overall precast scaffold for the wide pier body of the cross-sea bridge comprises a frame component with all edges detachable, a plurality of grooves are formed in the upper surface of the top edge and the upper surface of the bottom edge of the frame assembly in the length direction, and a plurality of grooves are also formed in the inner surface of the left side edge and the inner surface of the right side edge of the frame assembly in the length direction. The steel reinforcement cage overall precast scaffold for the wide pier body of the cross-sea bridge is high in construction efficiency, high in quality, safe, reliable, and particularly suitable for construction of wide pier body reinforcing bar engineering under severe marine environments.
Owner:CCCC SHEC FOURTH ENG +1
High safety polyene phosphatidyl choline for injection and preparation method thereof
InactiveCN101940586ASolve the Stability ConundrumReduce dosageOrganic active ingredientsPowder deliveryPolyene phosphatidylcholineMedicine
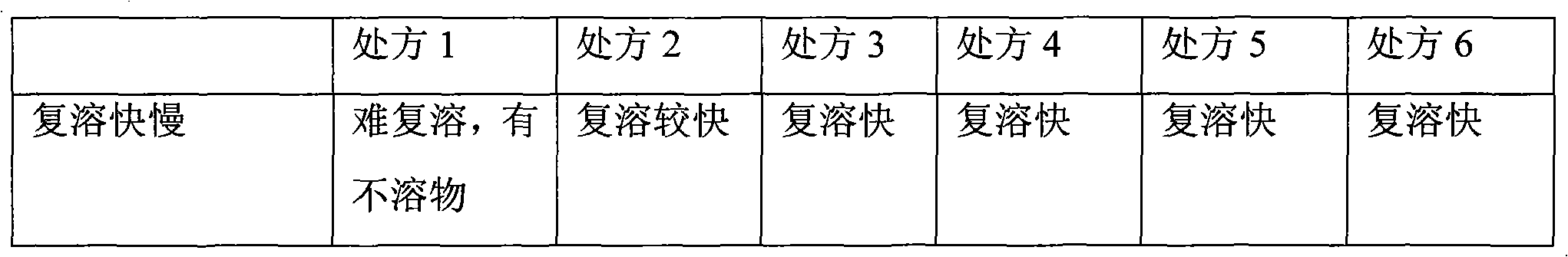
The invention provides high safety polyene phosphatidyl choline for injection and a preparation method thereof. Each injection contains the polyene phosphatidyl choline, vitamin B6, vitamin B12, nicotinamide, sodium pantothenate, a solubilizer and cryoprotectant. The injection is characterized in that the weight ratio of the solubilizer to the polyene phosphatidyl choline is 0.4-0.6:1, and is 0.5:1 preferably. The dosage of the solubilizer is reduced, the potential safety problem is reduced, the problem of re-dissolution is solved by optimizing the formula and the process, and the excellent re-dissolution is maintained on the premise of reducing the dosage of the solubilizer.
Owner:北京中海康医药科技发展有限公司
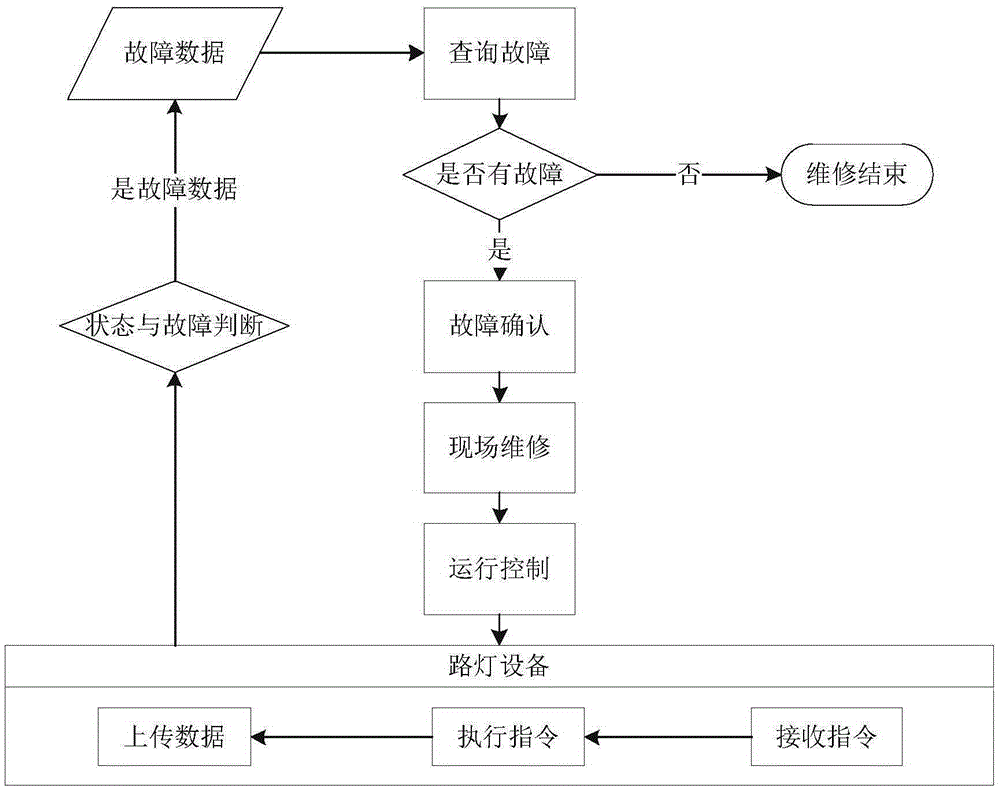
Field debugging and maintenance method of street lamp on the basis of mobile terminal
ActiveCN105282943AGuaranteed accuracyEnsure safetyElectric light circuit arrangementEnergy saving control techniquesElectricityGeolocation
The present invention discloses a field debugging and maintenance method of a street lamp on the basis of a mobile terminal. The mobile terminal is employed to query whether there is provided failure data of operation of city street lamp facilities or not, and the failure data is determined; the mobile terminal is employed to perform positioning of geographic locations of determined faulted city street lamp facilities, through adoption of the mobile terminal, the electricity in the control cabinets including the faulted city street lamp facilities is turned off and instruction issue is locked and the electricity in the control cabinets including the faulted city street lamp facilities is turned on and the instruction issue is unlocked after finishing changing or maintenance, and turning on the electricity is successful and the lock is unlocked according to the instruction feedback result; the street lamp facilities receive control instructions of normal operation, and the execution result data is uploaded to a monitoring center sever side; determination of states and faults is performed, and failure data is determined and screened out for query of the mobile terminal or pushing to the mobile terminal; and the steps above are repeated until there is no failure data. According to the invention, a safe, independent and quick debugging on site may be realized when street lamp facilities are operated and maintained.
Owner:TAIHUA WISDOM IND GRP CO LTD
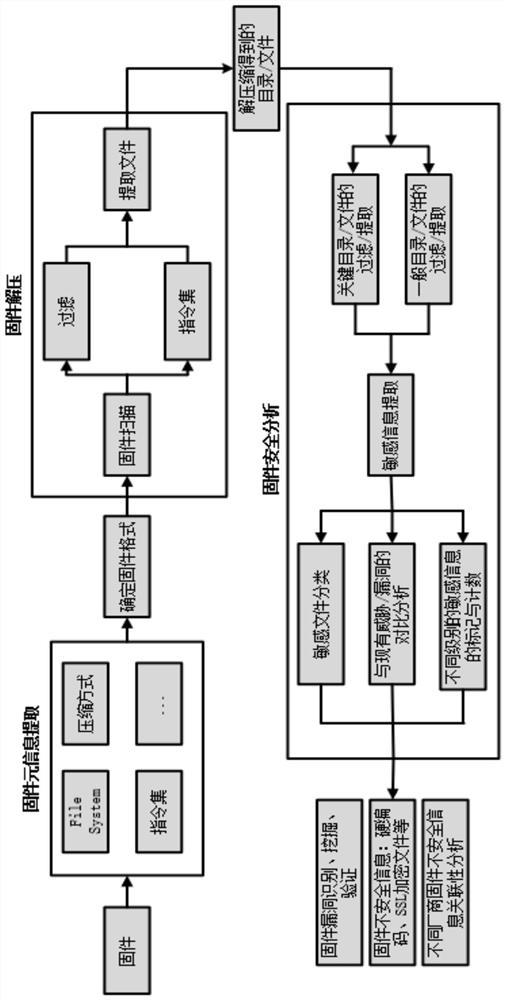
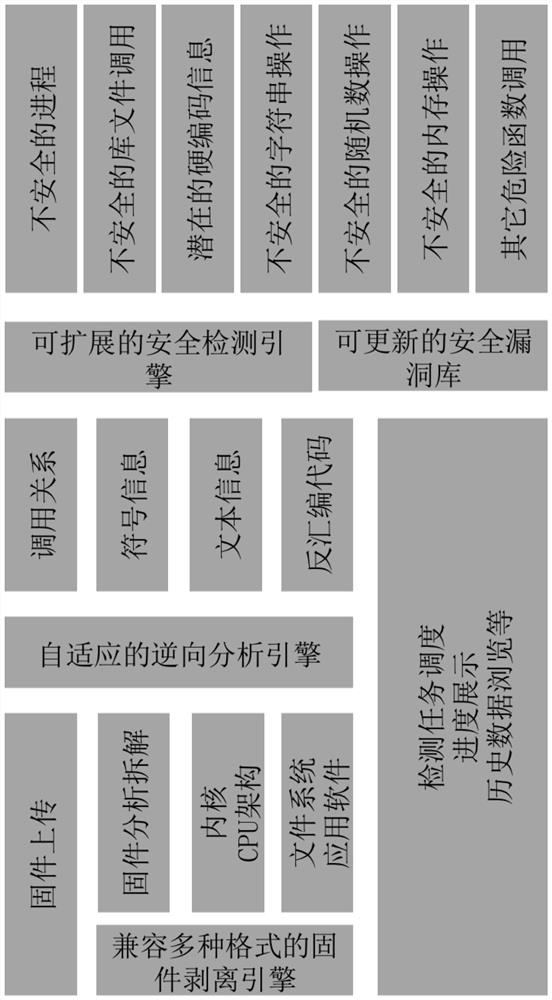
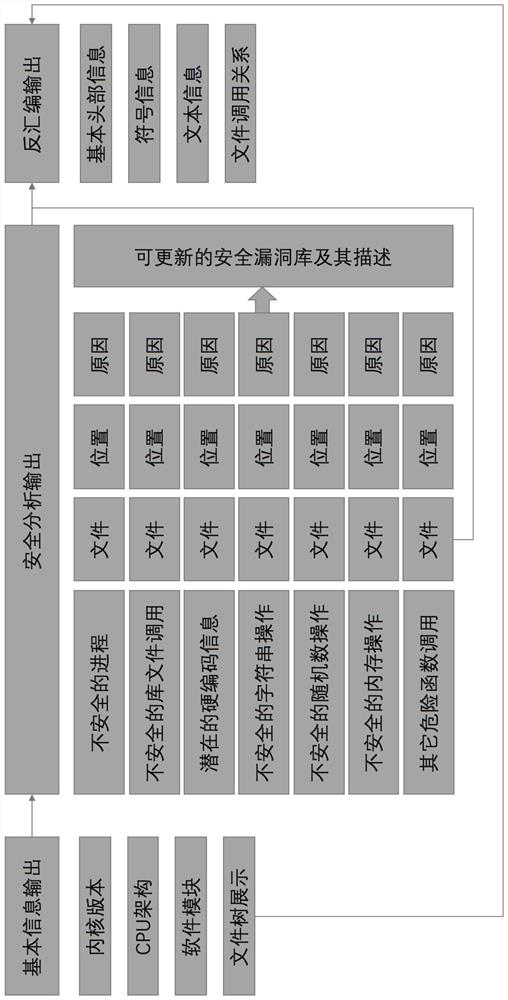
Method for constructing firmware security detection of Internet of Things terminal equipment
InactiveCN111680295AHigh unpacking rateEliminate security risksPlatform integrity maintainanceTransmissionSoftware engineeringThe Internet
The invention relates to the field of firmware package detection of internet-of-things terminal equipment, and provides a method for constructing firmware security detection of the internet-of-thingsterminal equipment in oder to overcome the defects of an existing security detection mode for a firmware package of the internet-of-things terminal equipment. The method comprises the following steps:step 1, collecting metadata of the internet-of-things terminal, and establishing a firmware list according to the metadata; establishing a firmware unpacking engine library, and establishing a mapping relationship between the firmware list and the firmware unpacking engine library; 2, obtaining a firmware package to be tested, extracting metadata, matching a corresponding firmware unpacking engine, and converting the firmware package to be tested into a machine language code; 3, converting the machine language code of the firmware package to be tested into an assembly language code; 4, scanning and detecting the assembly language code; 5, generating a detection report, wherein the metadata is multi-dimensional data. According to the invention, a basis is provided for reasonable planning of an Internet of Things operation and maintenance scheme, and possibility is provided for reducing the security risk of Internet of Things terminal equipment.
Owner:ELECTRIC POWER RES INST OF STATE GRID ZHEJIANG ELECTRIC POWER COMAPNY
Method for clearing material lumps on cylinder wall of cylinder warehouse
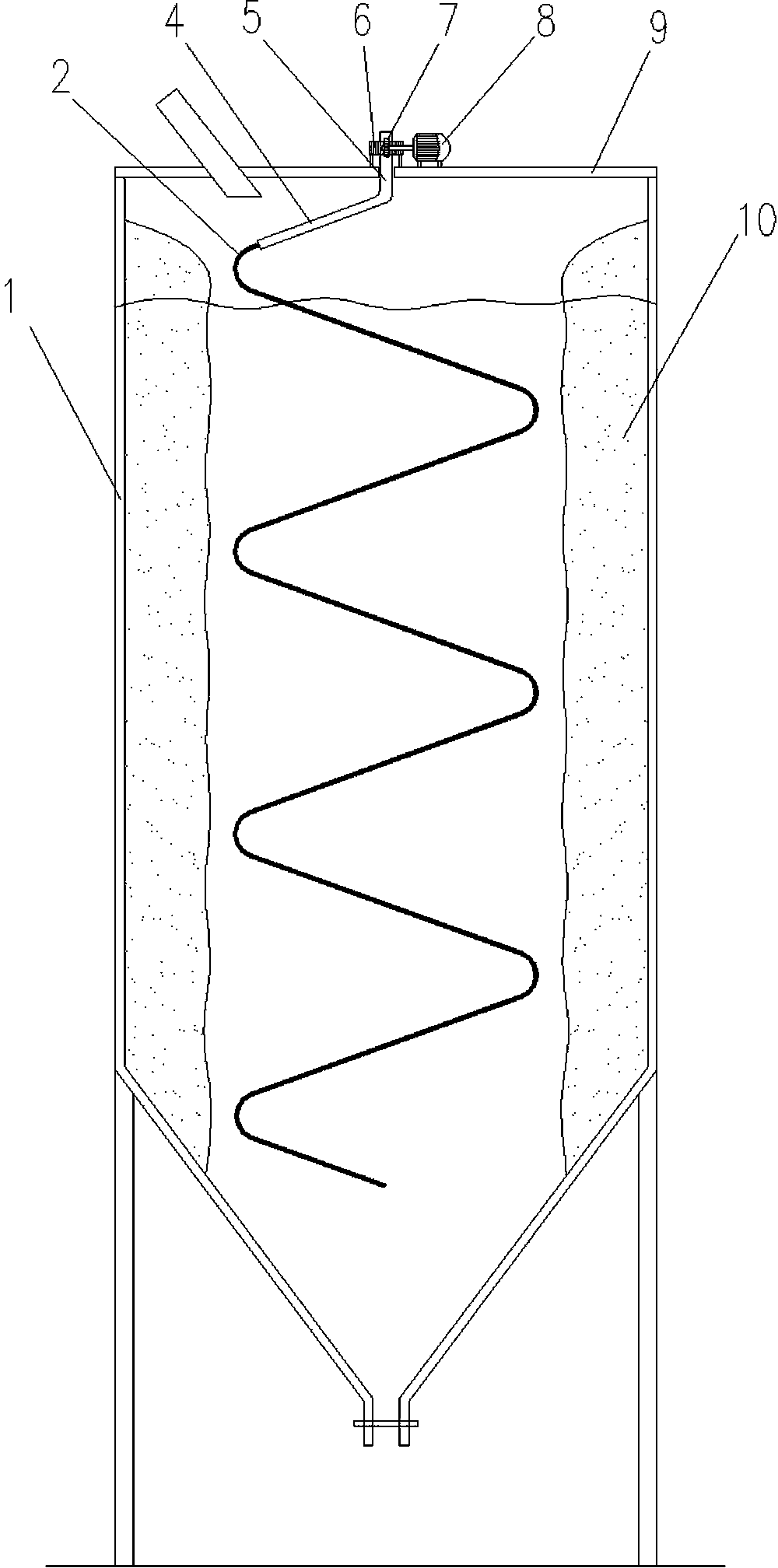
InactiveCN103394479AEliminate security risksImprove the efficiency of warehouse clearing operationsCleaning using toolsEngineeringWire rope
The invention relates to a method for clearing material lumps on the cylinder wall of a cylinder warehouse. The method is characterized by comprising the following steps: a rotating arm (4) is arranged at the top (9) of the cylinder warehouse (1); the rotating arm stretches into the end part in the cylinder warehouse and is connected with a steel wire rope (2); the rotating arm is driven by a transmission to rotate to enable the rotating arm to drive the steel wire rope to rotate in a spiral manner; the spirally turning force of the steel wire rope is utilized to strike the lumps adhering to the cylinder wall. The revolving speed and camber of the rotating arm are adjusted to regulate the striking radius and striking dynamics of the steel wire rope. The method has the following advantages: the safety risk of warehouse clearing operation can be completely eliminated; the efficiency of warehouse clearing operation can be greatly improved; the production cost can be decreased; the use cost is very low; private facilities can be directly built on the cylinder warehouse.
Owner:(CNBM) BENGBU DESIGN & RES INST FOR GLASS IND CO LTD +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com