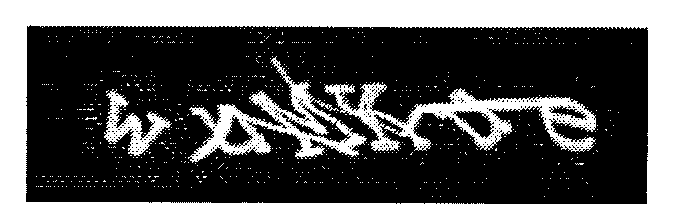Method and device for generating three-dimensional dynamic verification code
A three-dimensional dynamic and verification code technology, applied in computer security devices, digital data authentication, instruments, etc., can solve problems such as difficult to identify symbols, interference pictures, and normal users are difficult to identify, so as to improve the ability to resist attacks and make identification simple and easy Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0025] The generation method of the three-dimensional dynamic verification code provided by the present invention, the generation process is as follows:
[0026] a. Randomly generate verification code information, and set the position where the verification code information is displayed on the screen of the three-dimensional video;
[0027] b. Establish a three-dimensional space of a certain size, and generate a three-dimensional geometric primitive in the three-dimensional space; said generating a three-dimensional geometric primitive includes setting the position attribute, geometric attribute and motion track of the three-dimensional geometric primitive, and the position attribute includes a three-dimensional geometric primitive The three-dimensional coordinates of , the geometric attributes include the brightness, shape, size and color attributes of the three-dimensional geometric primitives;
[0028] c. Judging whether the three-dimensional geometric primitive is located ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com