Method for obtaining software security defects based on vertical search and semantic annotation
A vertical search and semantic annotation technology, applied in special data processing applications, instruments, electrical and digital data processing, etc., can solve the problems of expensive software maintenance and fault recovery, computer loss, heavy and other problems
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
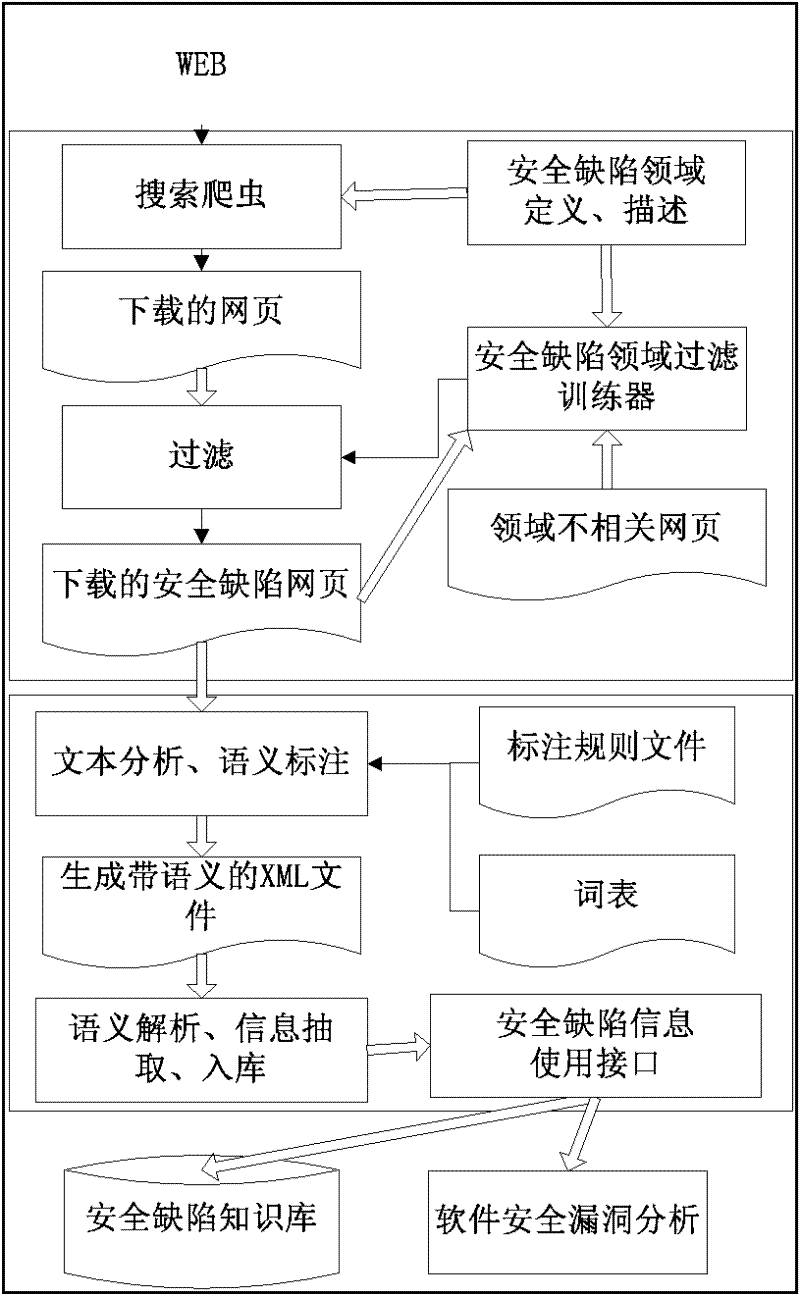
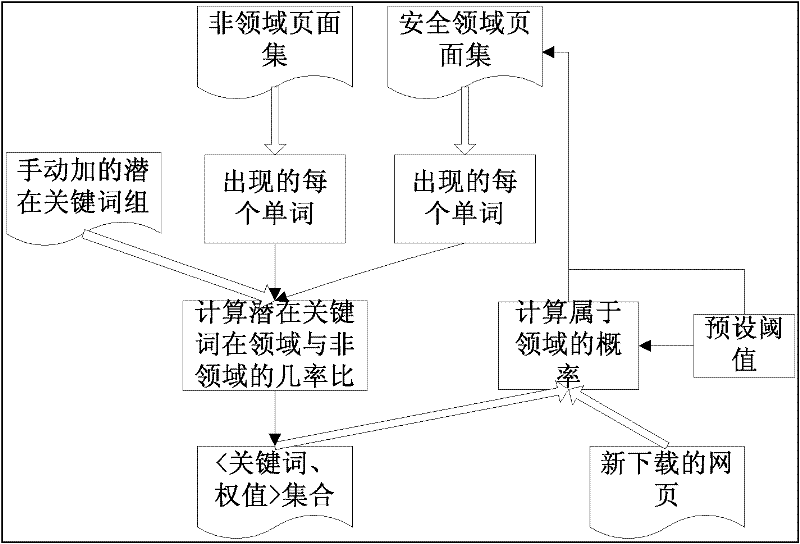
[0026] Such as figure 1 As shown, the overall technical solution process of the present invention is as follows: firstly, the domain search crawler is used to crawl the published security defect information web pages on the World Wide Web, and the security defect domain filter trainer provides powerful filtering support for the search crawler to complete the task; These downloaded webpages are semantically annotated to make the webpages carry semantic information and make the machine understandable; then an annotation analysis tool is designed to extract further information from the annotated information; finally the information is provided for the software security defect knowledge base and software security vulnerability analysis Interface to provide data support for them. The present invention will be described in detail below.
[0027] 1. Vertical search
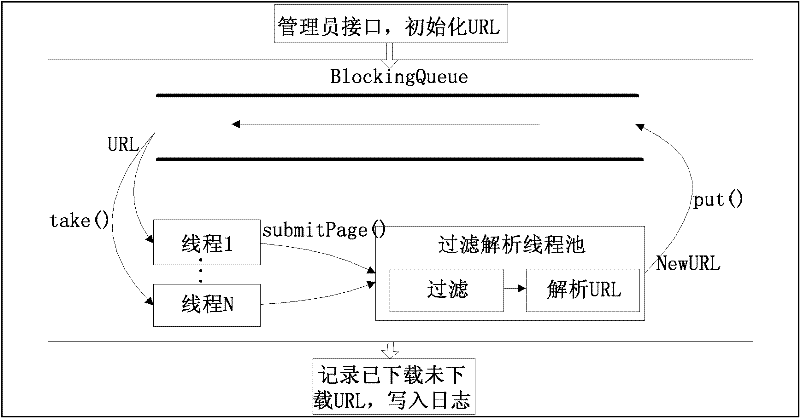
[0028] Such as figure 2 The vertical search crawler download schematic diagram shown. Vertical search is a professional...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com