Method and network device for detecting malicious network software agents
A technology of network equipment and automatic software agent, applied in the field of computer network, which can solve the problem of inability to detect or respond to software agent
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
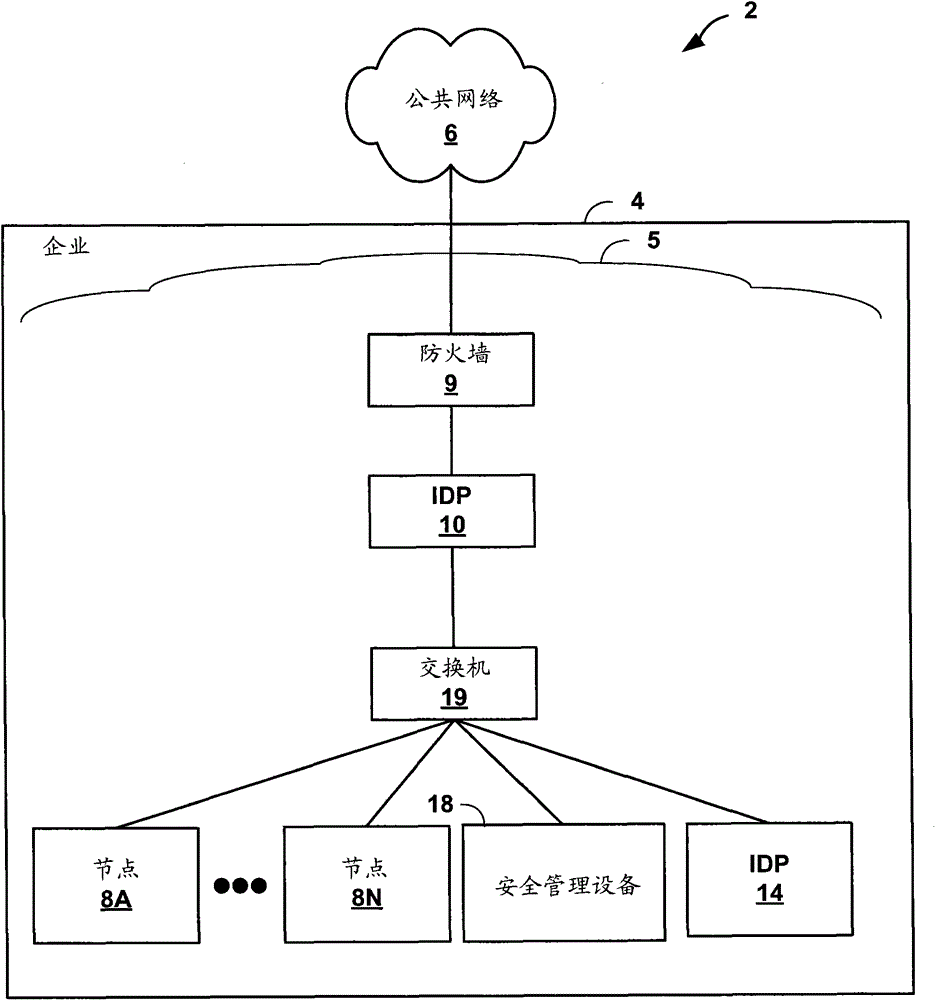
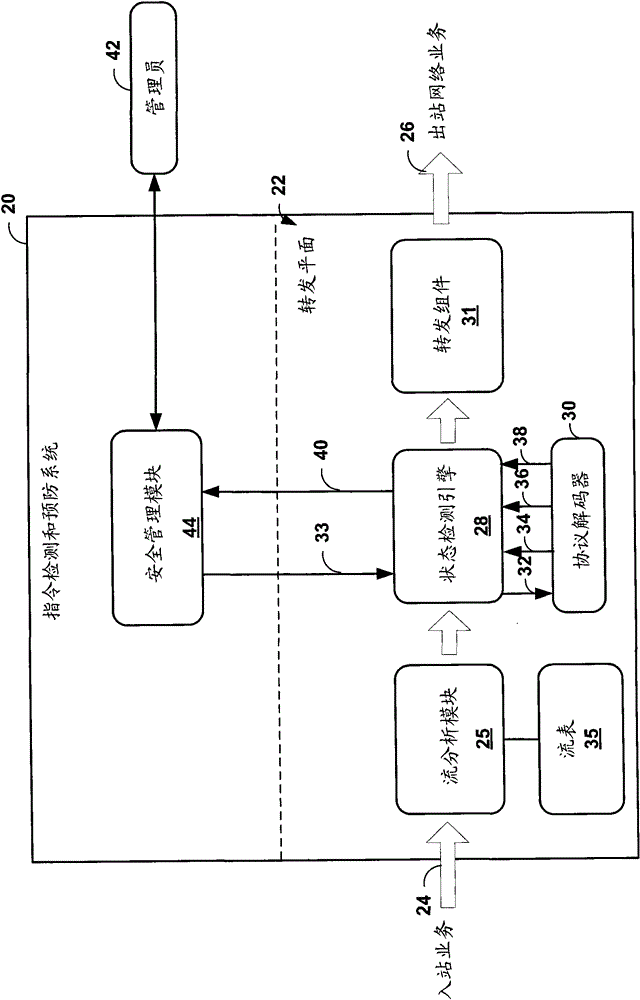
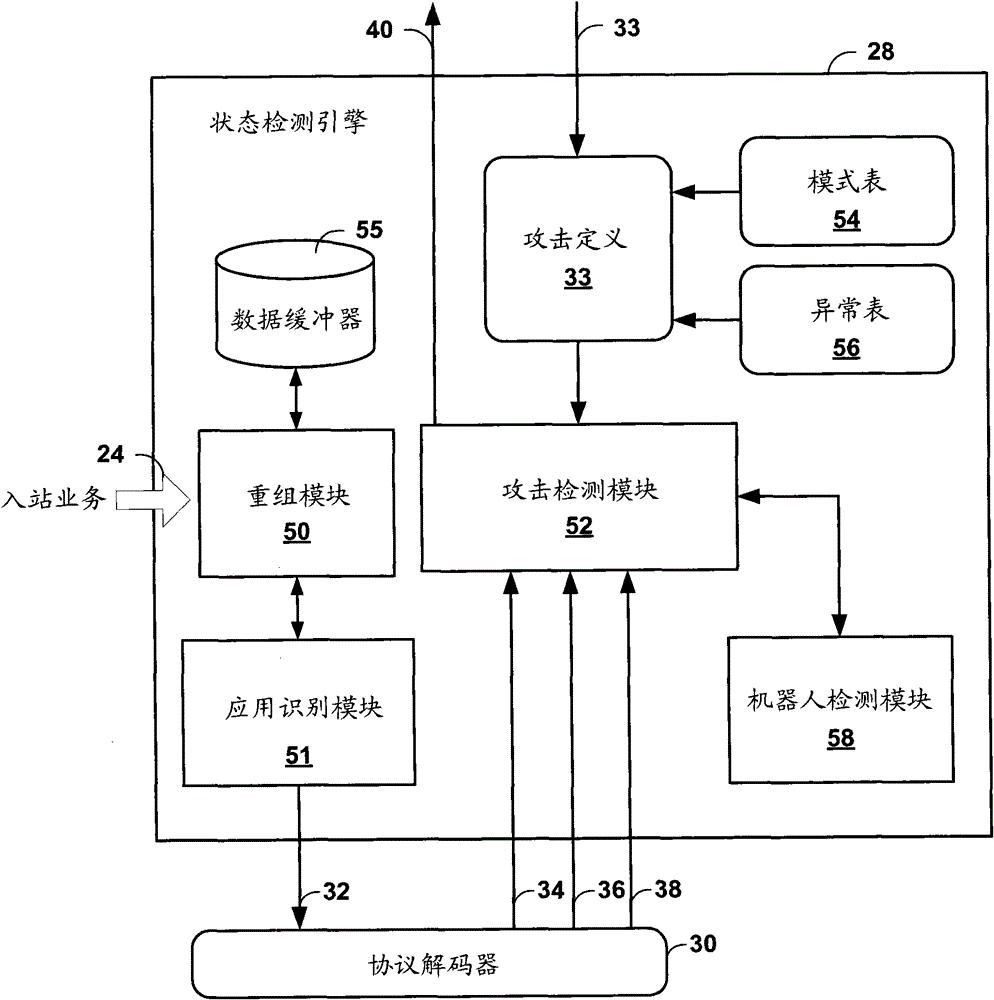
[0021] figure 1 is a block diagram illustrating an exemplary enterprise computer network 4 in which an intrusion detection and prevention (IDP) device 10 may attempt to detect an Malicious web sessions. References to "bots" in this disclosure should generally be understood to refer to automated software agents that may perform malicious or otherwise undesirable actions. Although the present disclosure primarily relates to an IDP device, an Intrusion Detection System (IDS) or Intrusion Prevention System (IPS) may employ similar techniques. exist figure 1 In the example, IDP10 is a single network device. For example, firewall 9, switch 19, security management device 18, IDP 14 or any one of nodes 8A-8N, or other devices such as routers, virtual private network (VPN) devices or gateways, can realize the Described function.
[0022] Network 4 includes a private enterprise computing network 5 coupled to a public network 6, such as the Internet. Public network 6 may include, f...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com