Dot product protocol-based protocol security quantizing method and system
A technology of protocol security and quantification method, which is applied in the field of protocol security quantification method and system based on the dot product protocol, can solve the problems that the absolute security of zero leakage cannot be realized, and the calculation method cannot be applied, so as to improve the use efficiency Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
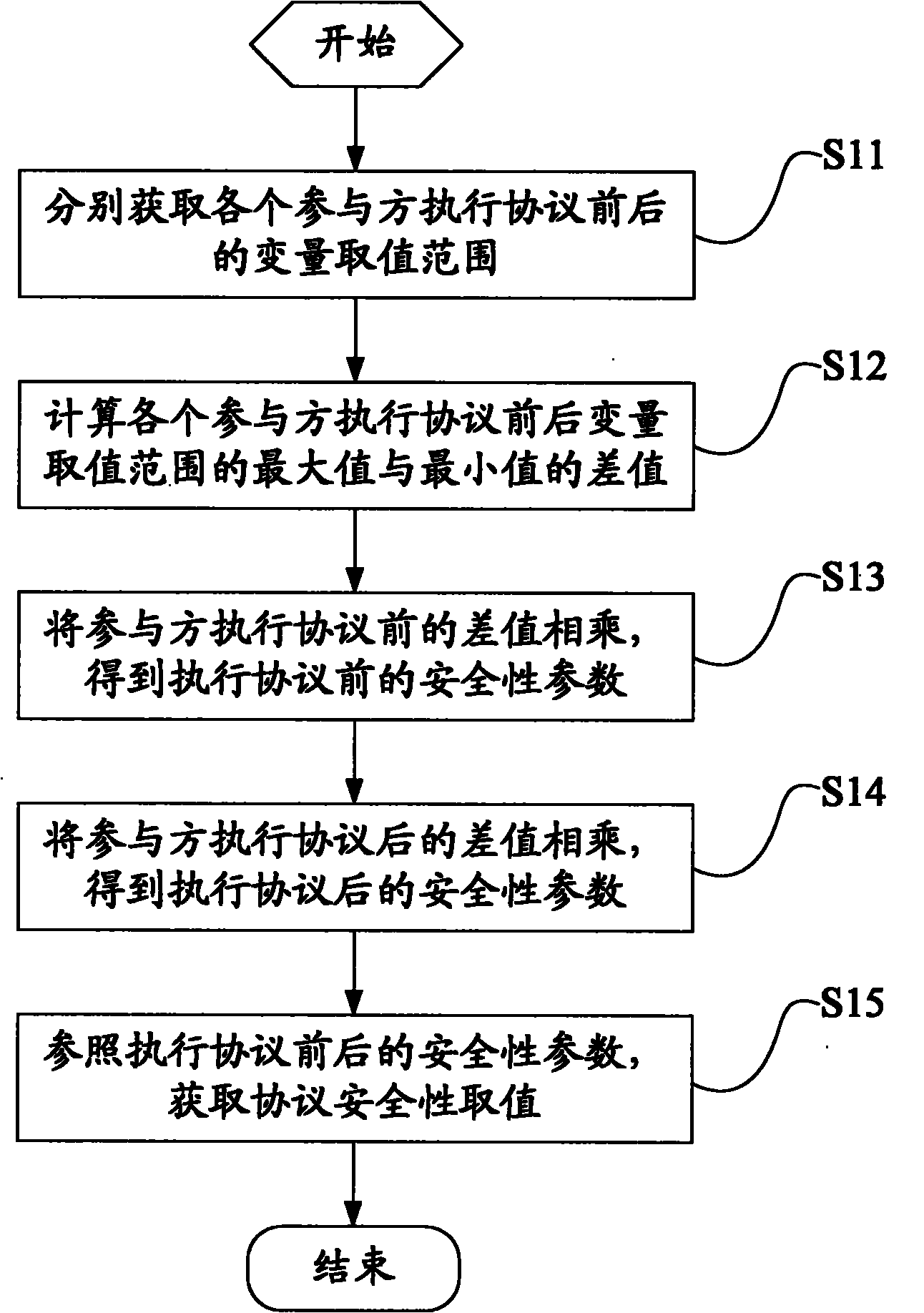
[0054] The flow of the protocol security quantification method based on the dot product protocol disclosed in Embodiment 1 of the present invention is as follows: figure 1 shown, including:
[0055] Step S11, obtaining the value ranges of variables before and after each participant executes the agreement respectively;
[0056] Step S12, respectively calculating the difference between the maximum value and the minimum value of the variable value range before and after each participant executes the agreement;
[0057] Step S13. Multiply the difference between each participant before executing the agreement to obtain the security parameter before executing the agreement;
[0058] Step S14. Multiply the difference between each participant after executing the agreement to obtain the security parameter after executing the agreement;
[0059] Step S15 , referring to the security parameters before and after the execution of the protocol, to acquire the security value of the protocol...
Embodiment 2
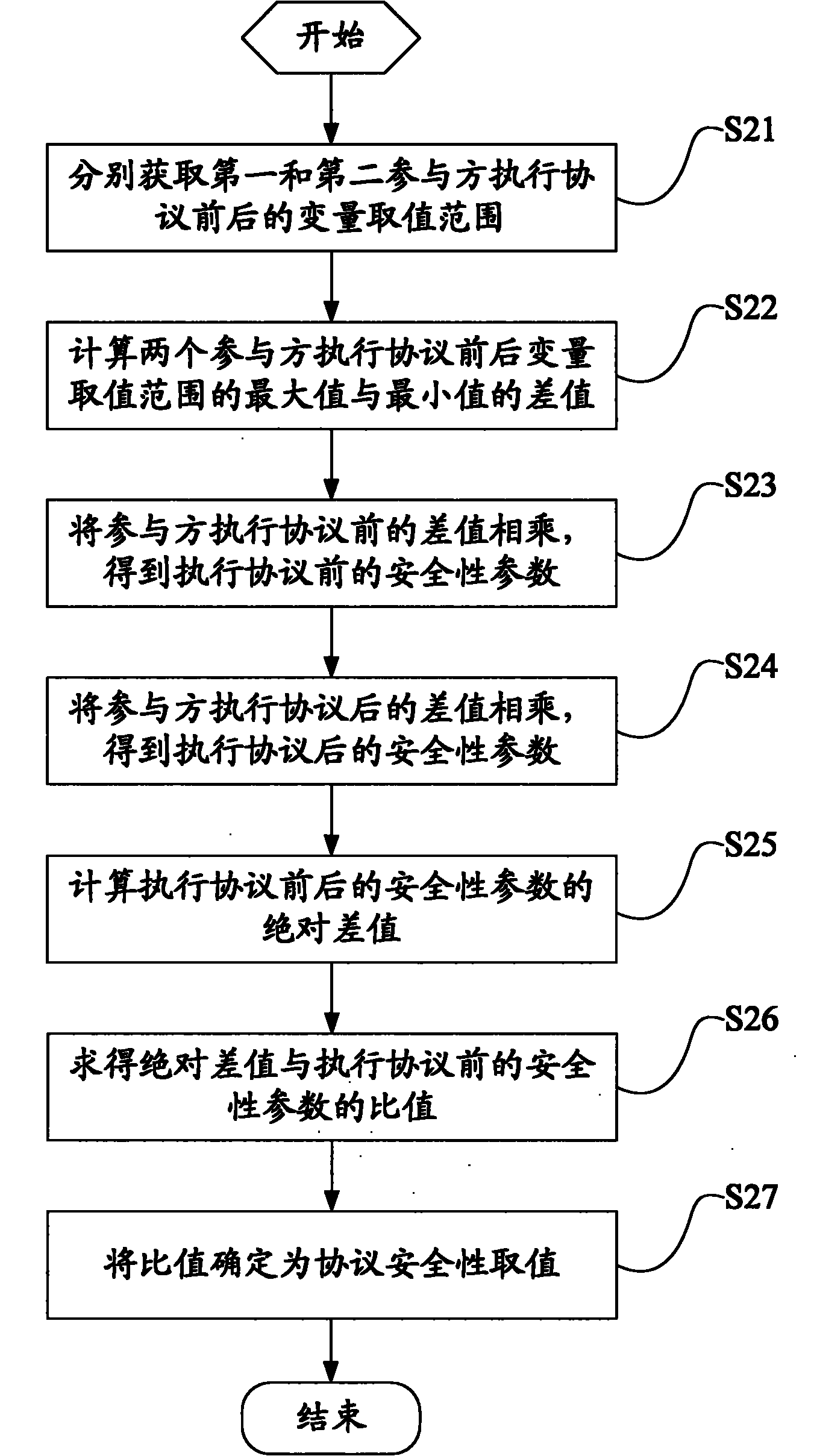
[0062] This embodiment discloses a protocol security quantification method based on the dot product protocol when the number of participants is two, and the process is as follows figure 2 shown, including:
[0063] Step S21, obtaining the value ranges of variables before and after the execution of the agreement by the first and second participants respectively;
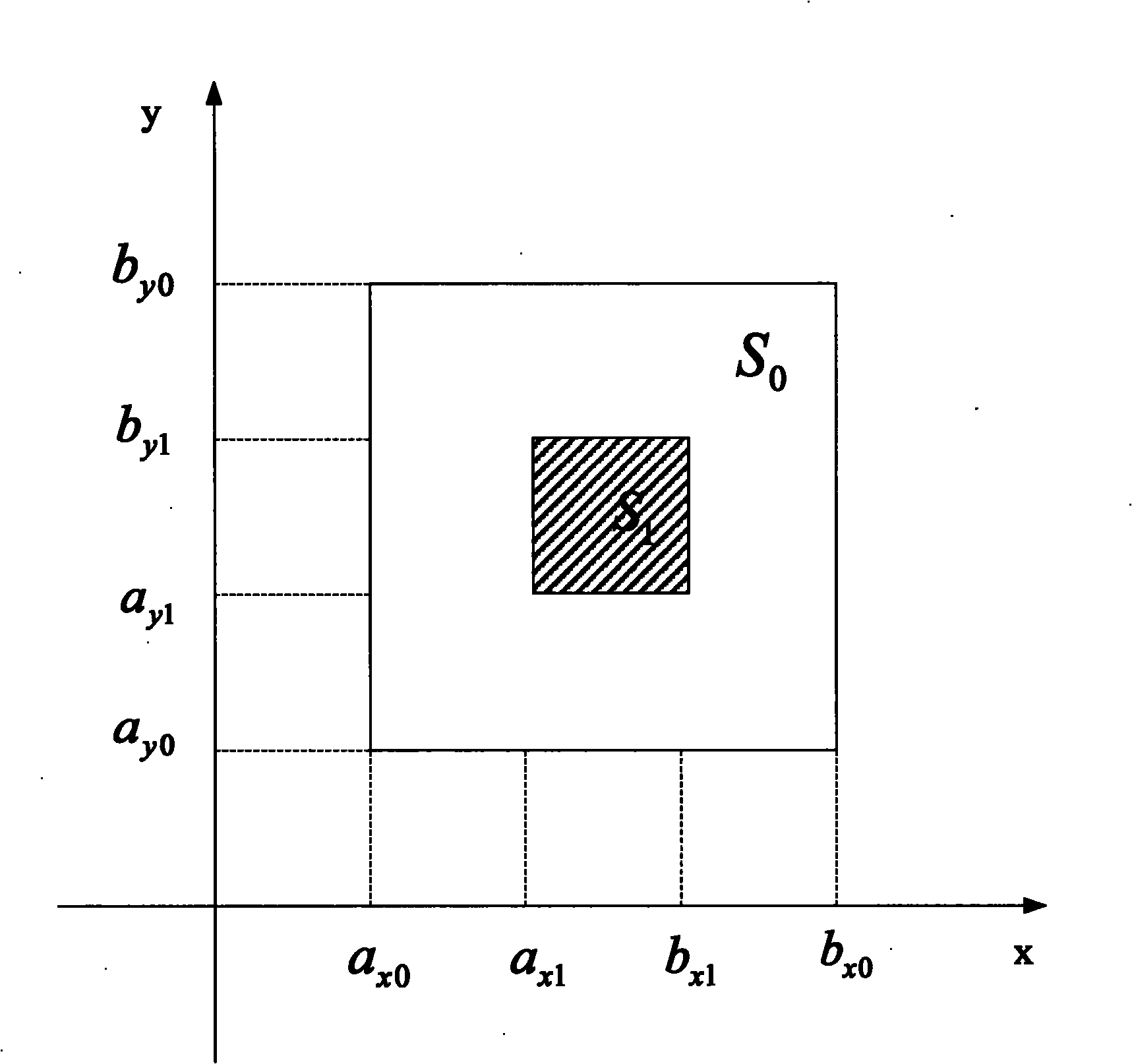
[0064] For an agreement with only two parties, it is necessary to obtain the variable value range X of the first party before the agreement is executed 0 =[a x0 , b x0 ] and the variable value range X of the first party after the agreement is executed 1 =[a x1 , b x1 ], the second party’s variable value range Y before the agreement is executed 0 =[a y0 , b y0 ], and the variable value range Y of the second party after the protocol is executed 1 =[a y1 , b y1 ].
[0065] Step S22, respectively calculating the difference between the maximum value and the minimum value of the variable value range before and ...
Embodiment 3
[0080] For the dot product protocol involving a third party, since the private data of the third party is also concealed, and some information may be leaked before and after the execution of the protocol, when quantifying the security of the protocol, the security of the third party should also be consider. This embodiment discloses a protocol security quantification method based on the dot product protocol when the number of participants is three, and the process is as follows Figure 4 shown, including:
[0081] Step S41, obtaining respectively the value ranges of the variables before and after the execution of the agreement by the first, second and third parties;
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com