Patents
Literature
136 results about "Acquisition Protocol" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
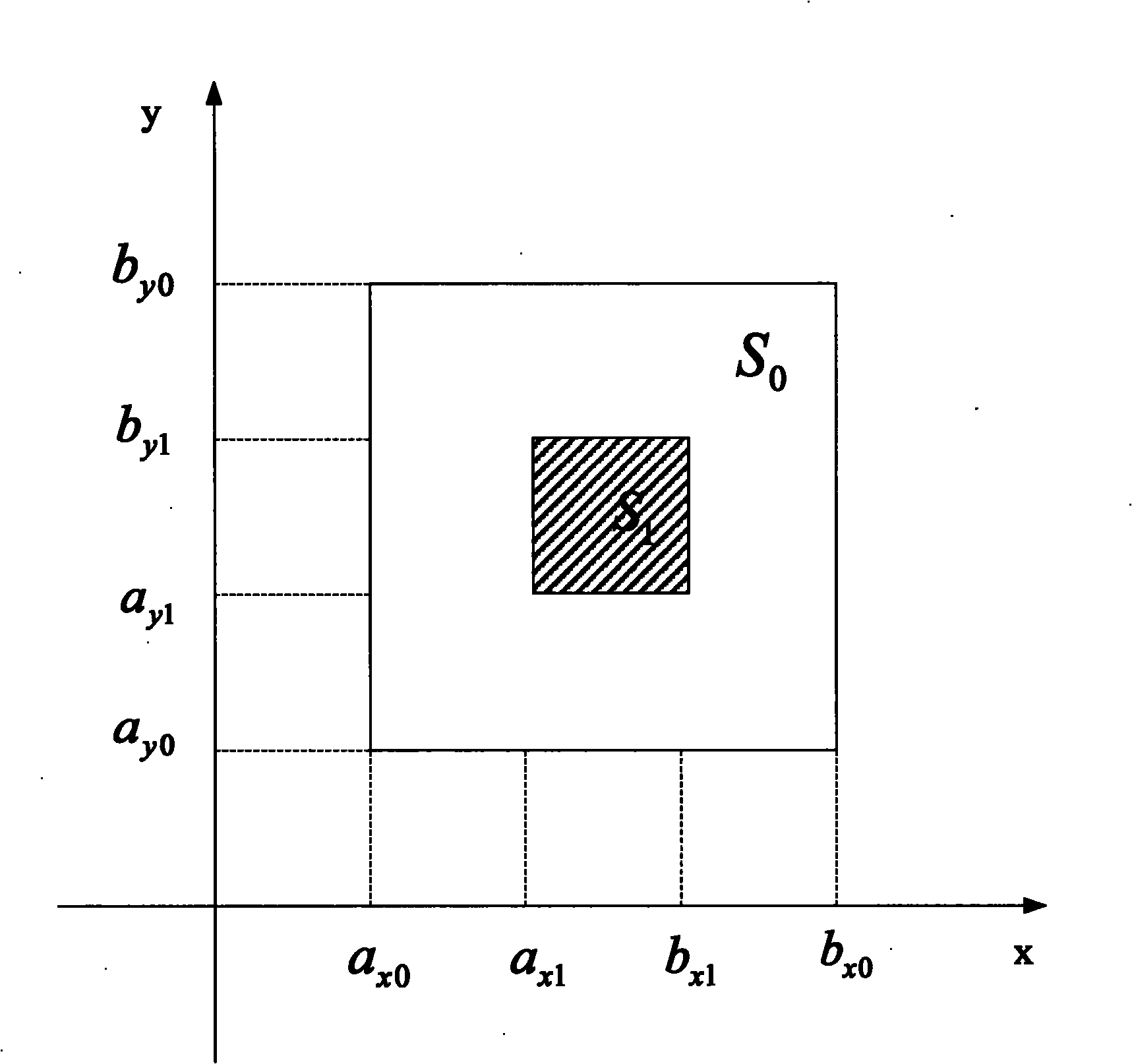
Rights Object Acquisition Protocol is a suite of XML-based Digital Rights Management (DRM) security protocols which enables Open Mobile Alliance-conformant user devices to request and acquire viewing and/or editing rights, permissions, privileges and other attributes from a Rights Issuer.
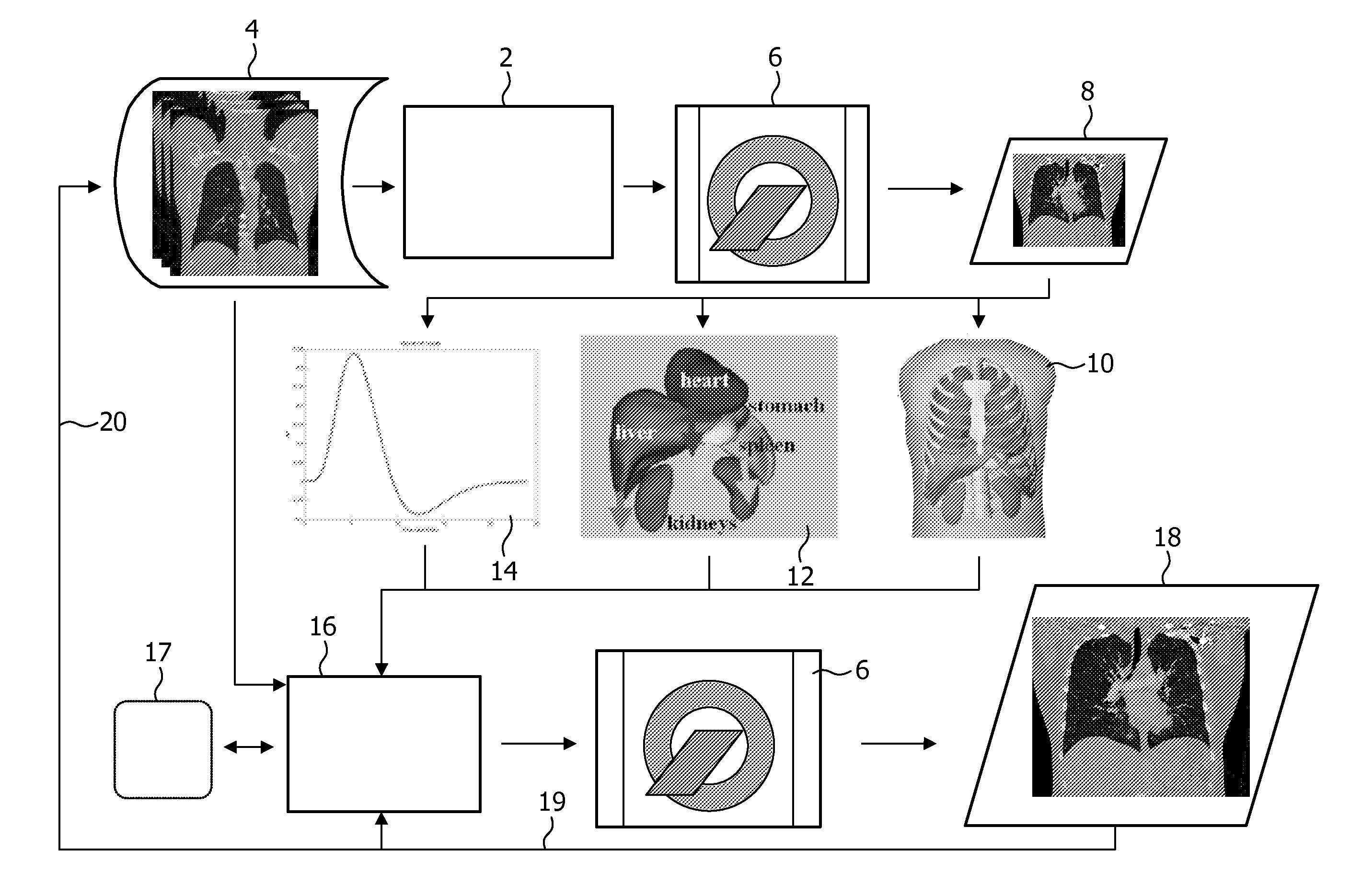
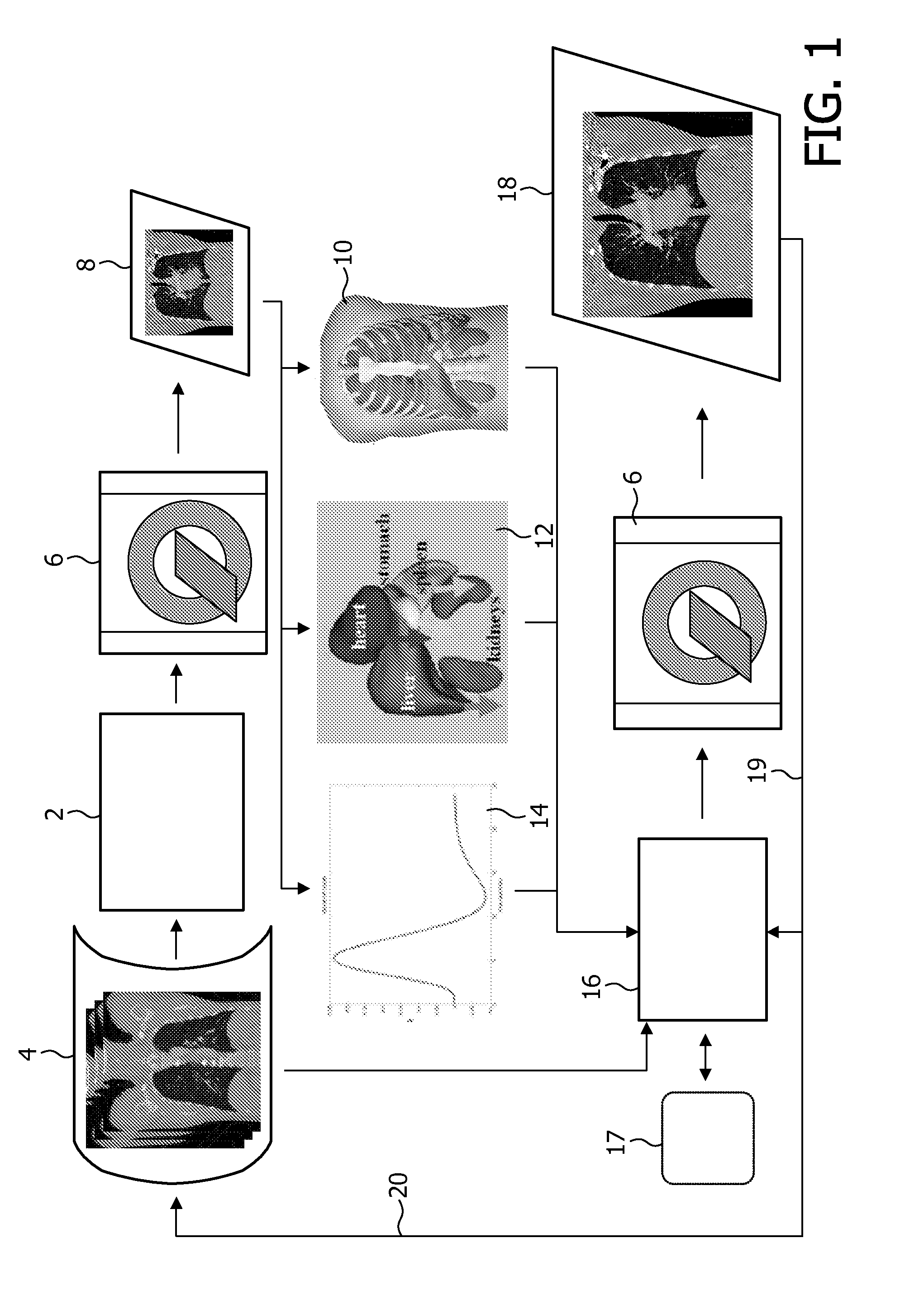
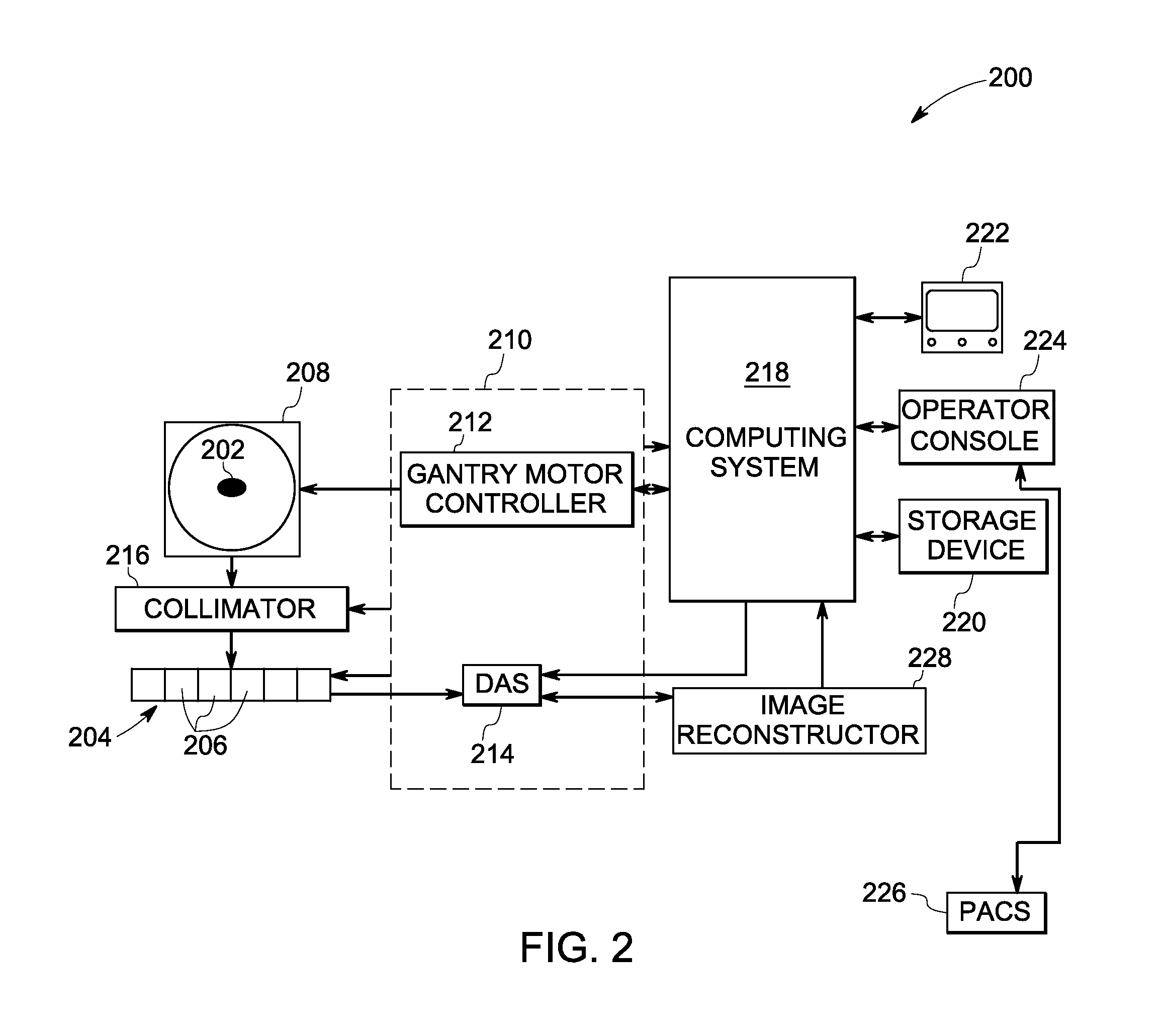
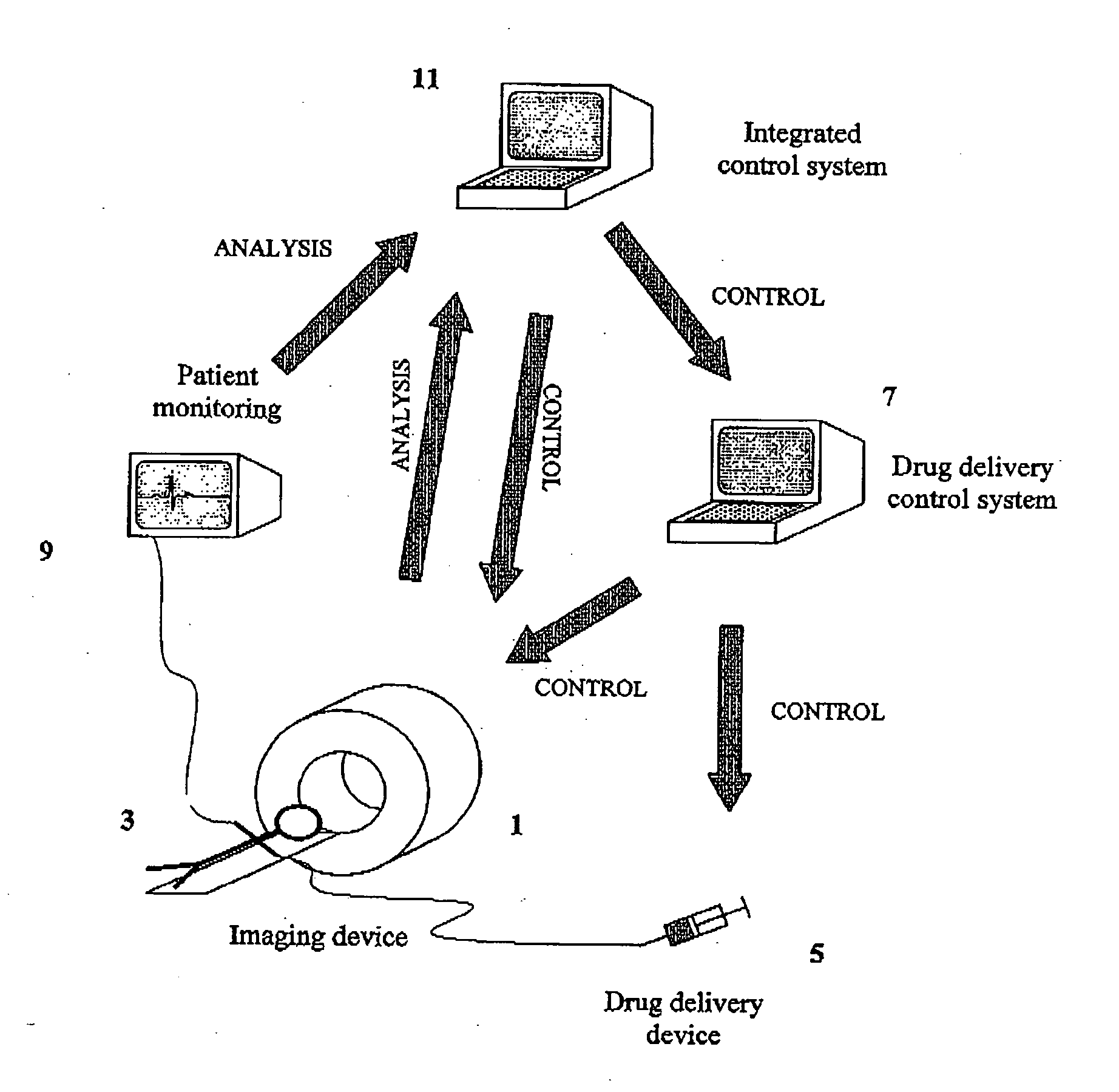
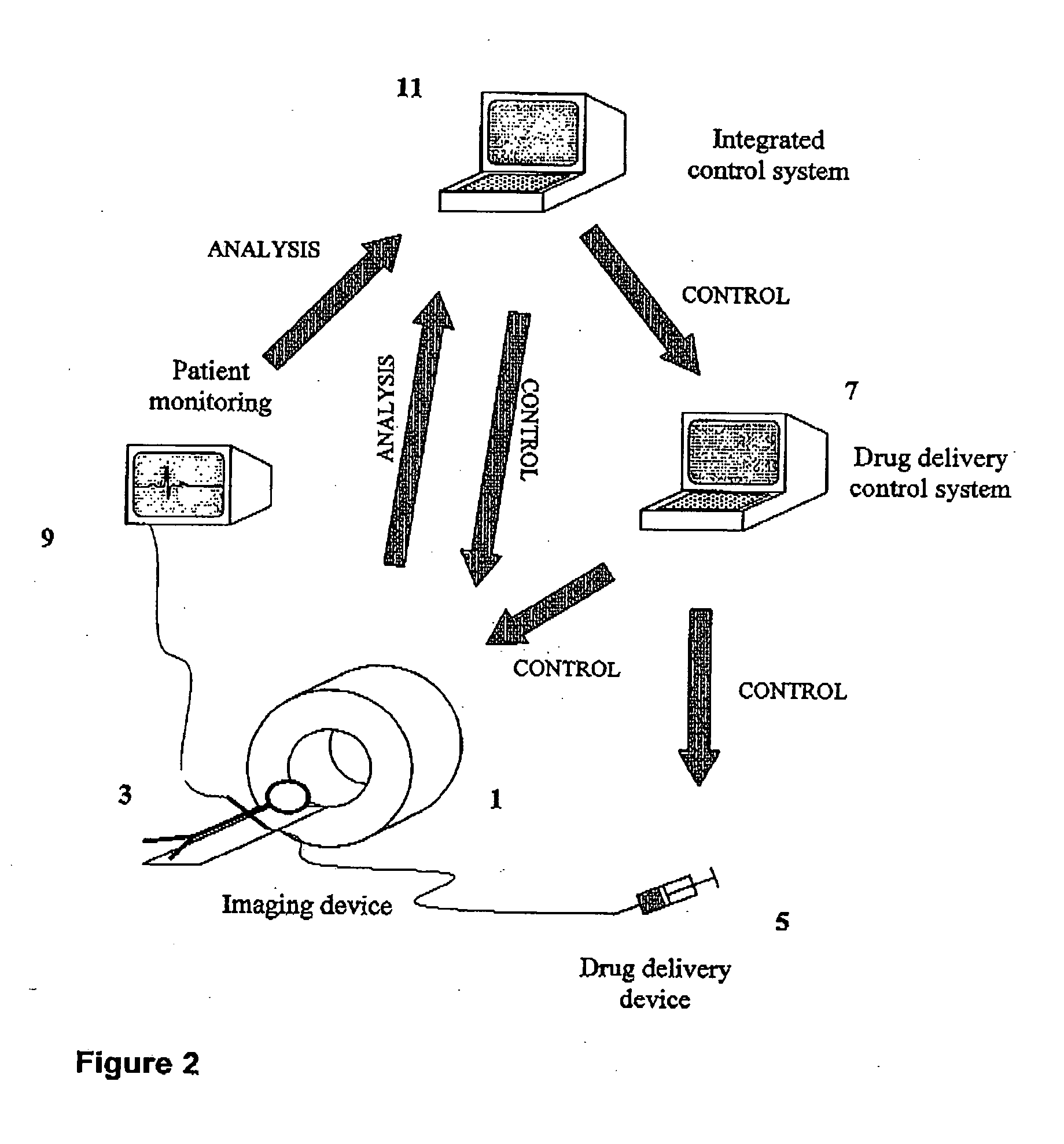
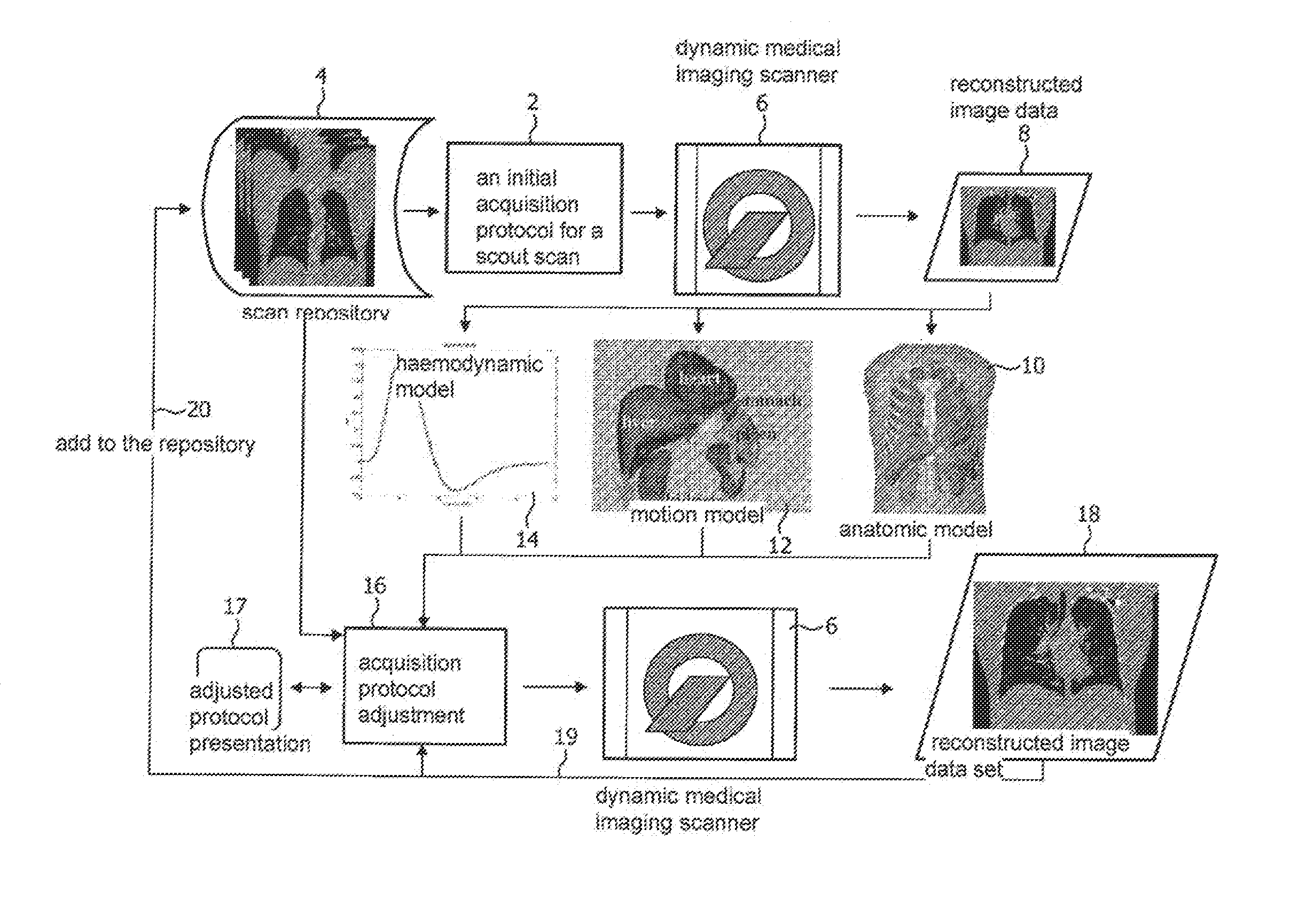
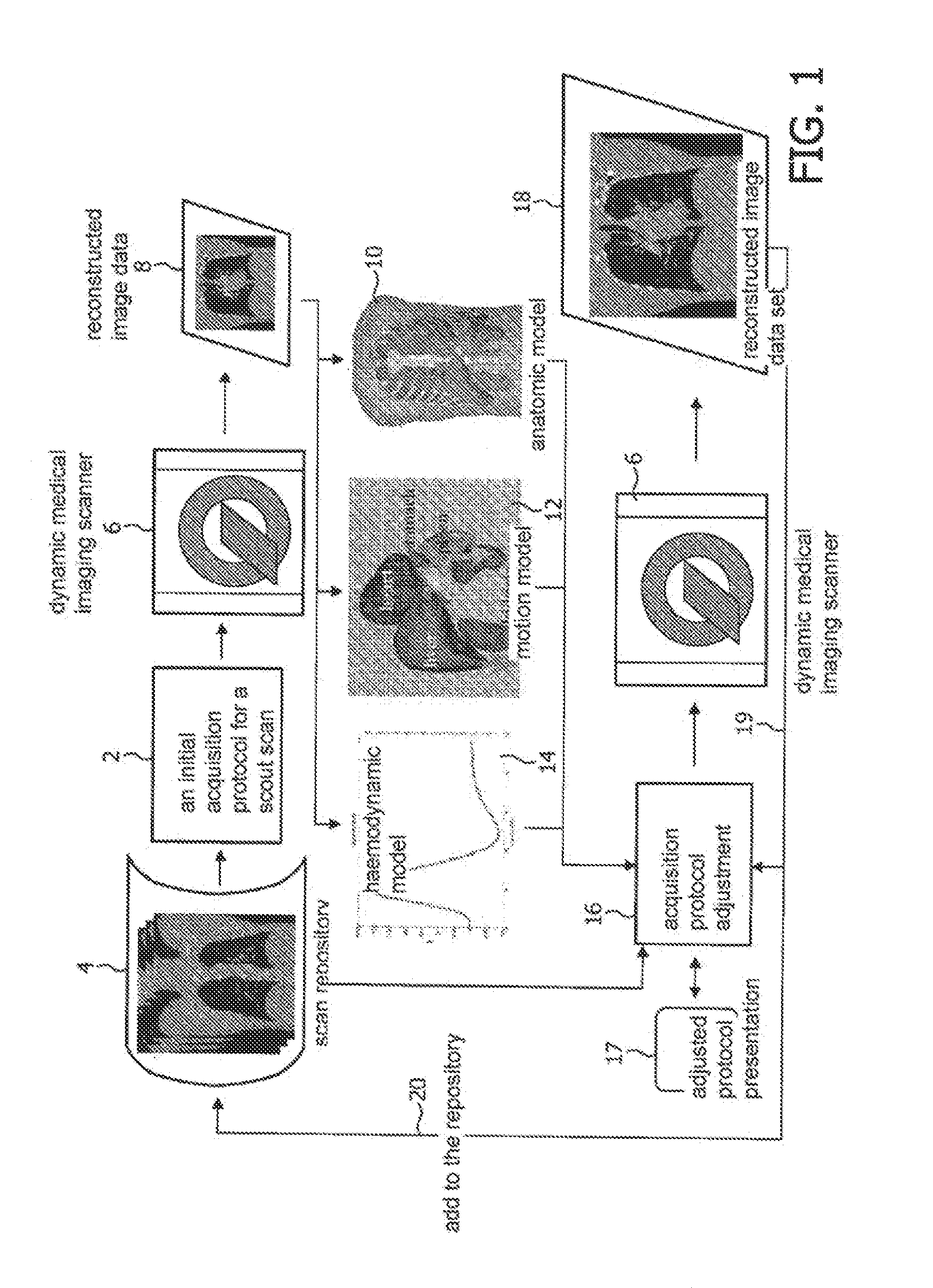
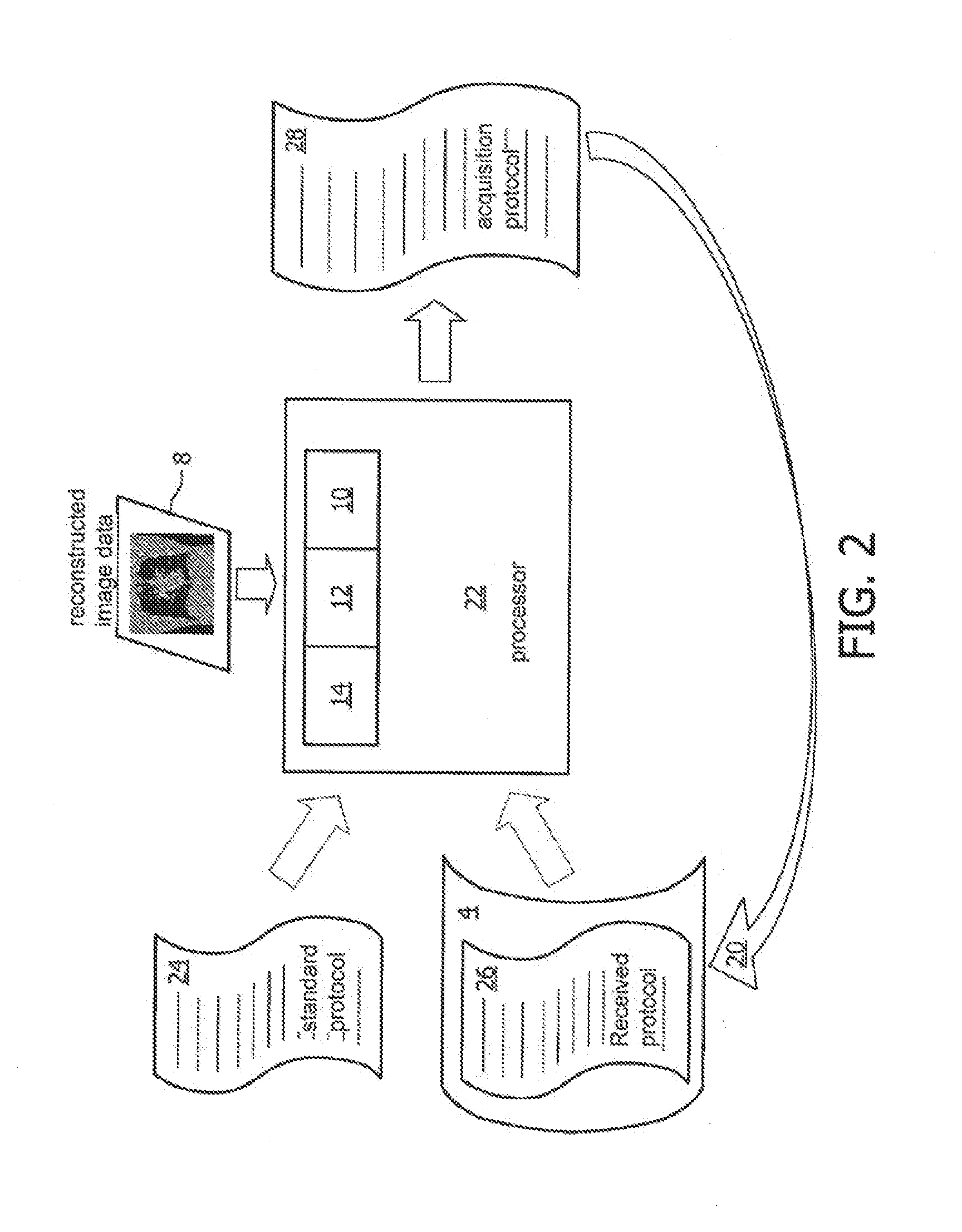
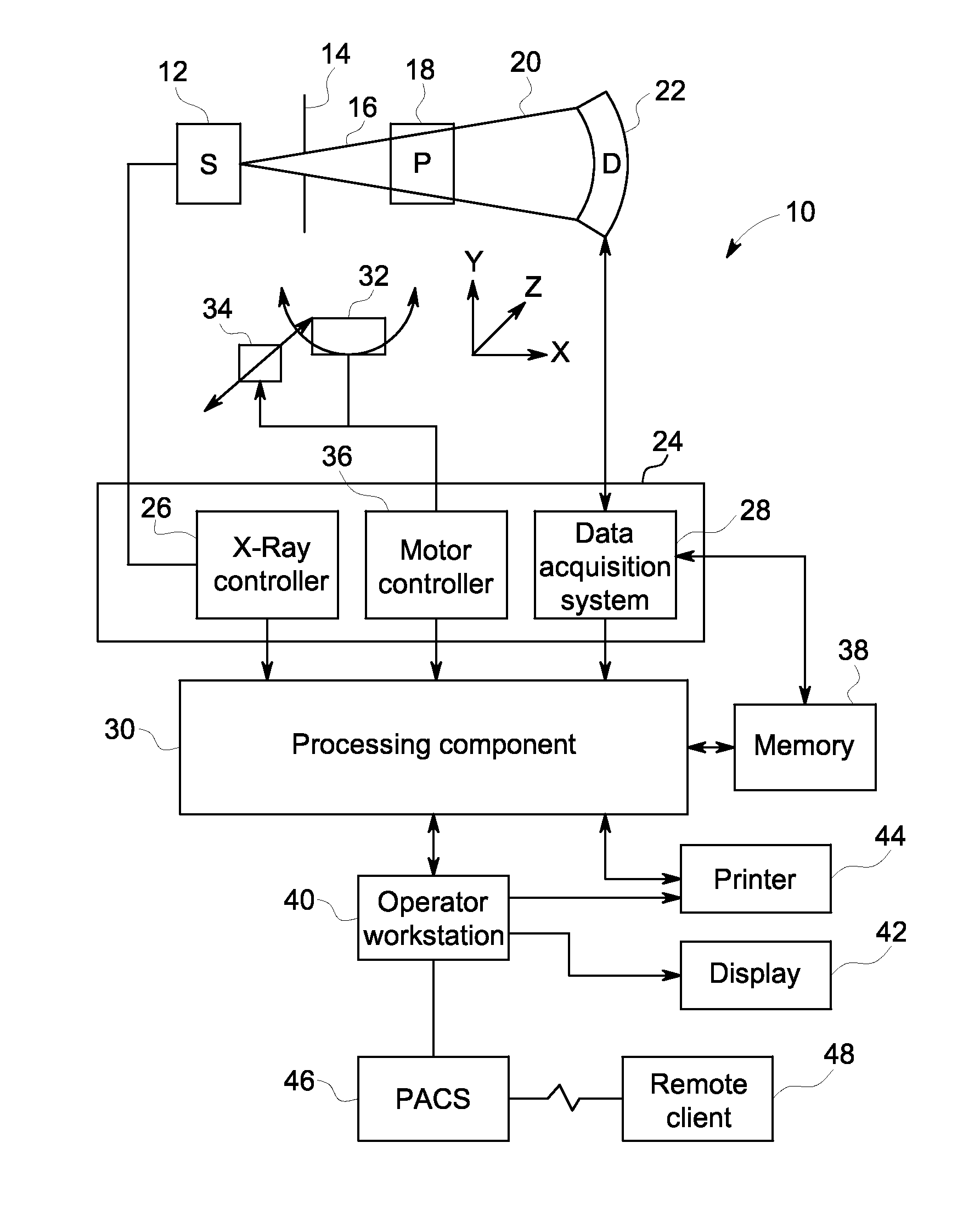
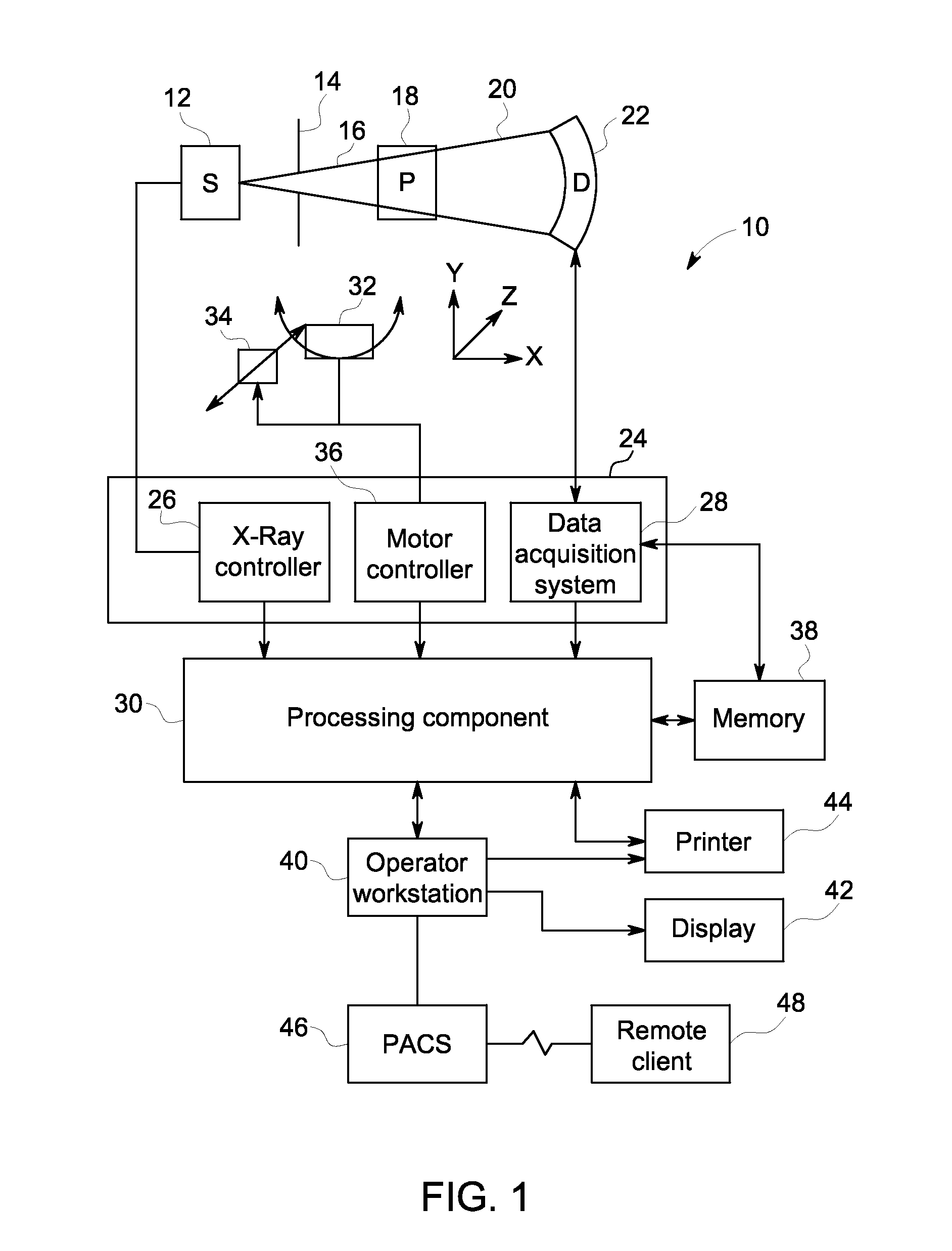
Adjusting acquisition protocols for dynamic medical imaging using dynamic models
ActiveUS20100183206A1More standardizedBetter quantifiableImage enhancementImage analysisDynamic modelsHemodynamics
The invention relates to automatically adjusting an acquisition protocol for dynamic medical imaging, such as dynamic CT, MRI or PET imaging. The protocols are adjusted based on anatomic and dynamic models (10, 12, 14) which are individualized or fitted to each patient based on a scout scan (6, 8). The adjustment can compensate for changes in the patient due to patient motion (e.g. breathing or heartbeat) or flow of contrast or tracing agent during the sequence. This ensures that changes in the reconstructed images are indicative of pathological changes in the patient and not caused by patient motion or changes in scanning parameters or timing. The dynamic model can be a motion model (12) used to predict the motion of anatomic / physiologic features, typically organs, during scanning, or a haemodynamic model (14) used to predict flow of the contrast agent allowing for precise timing of the scanning sequence.
Owner:KONINKLIJKE PHILIPS ELECTRONICS NV
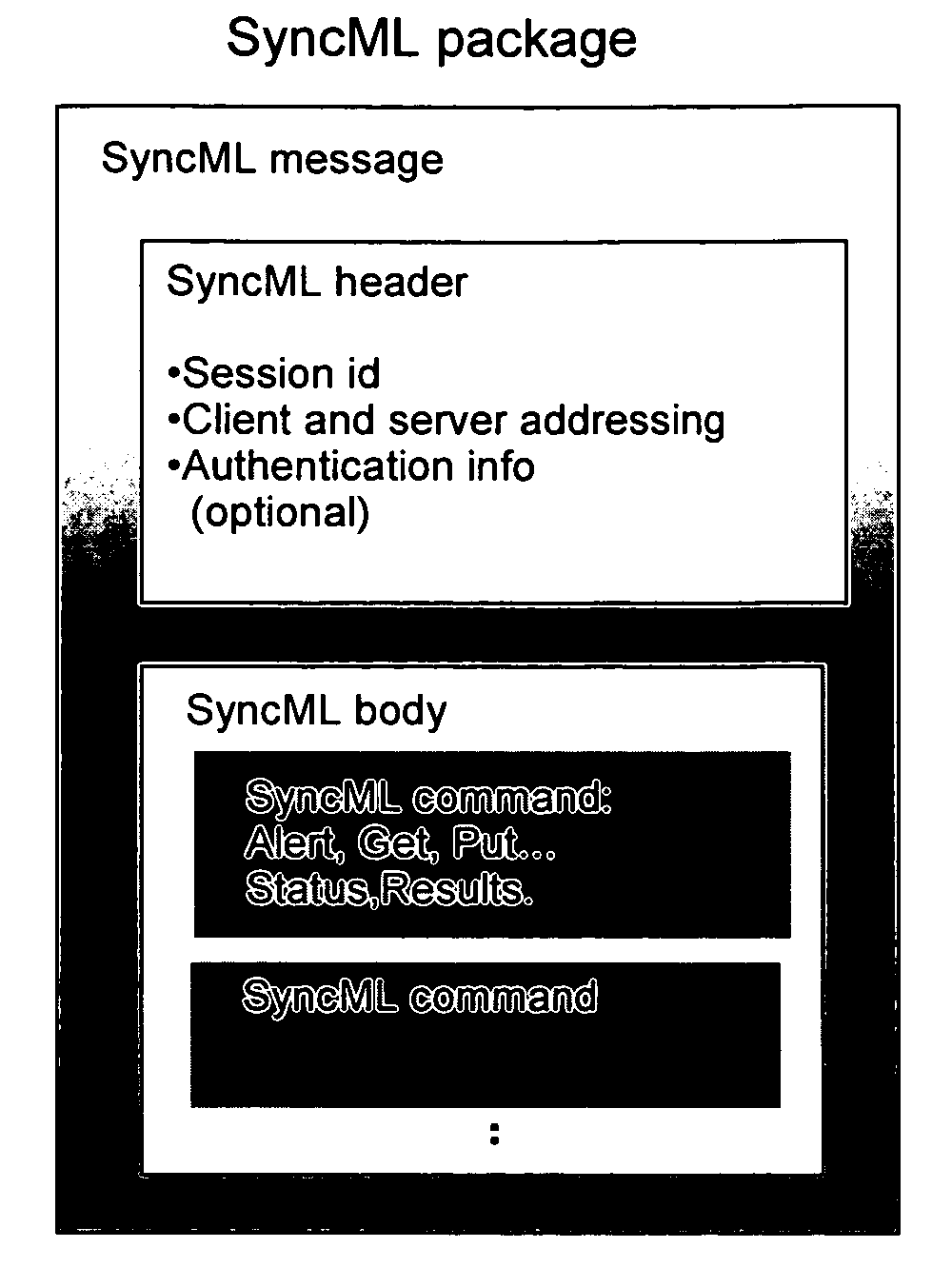
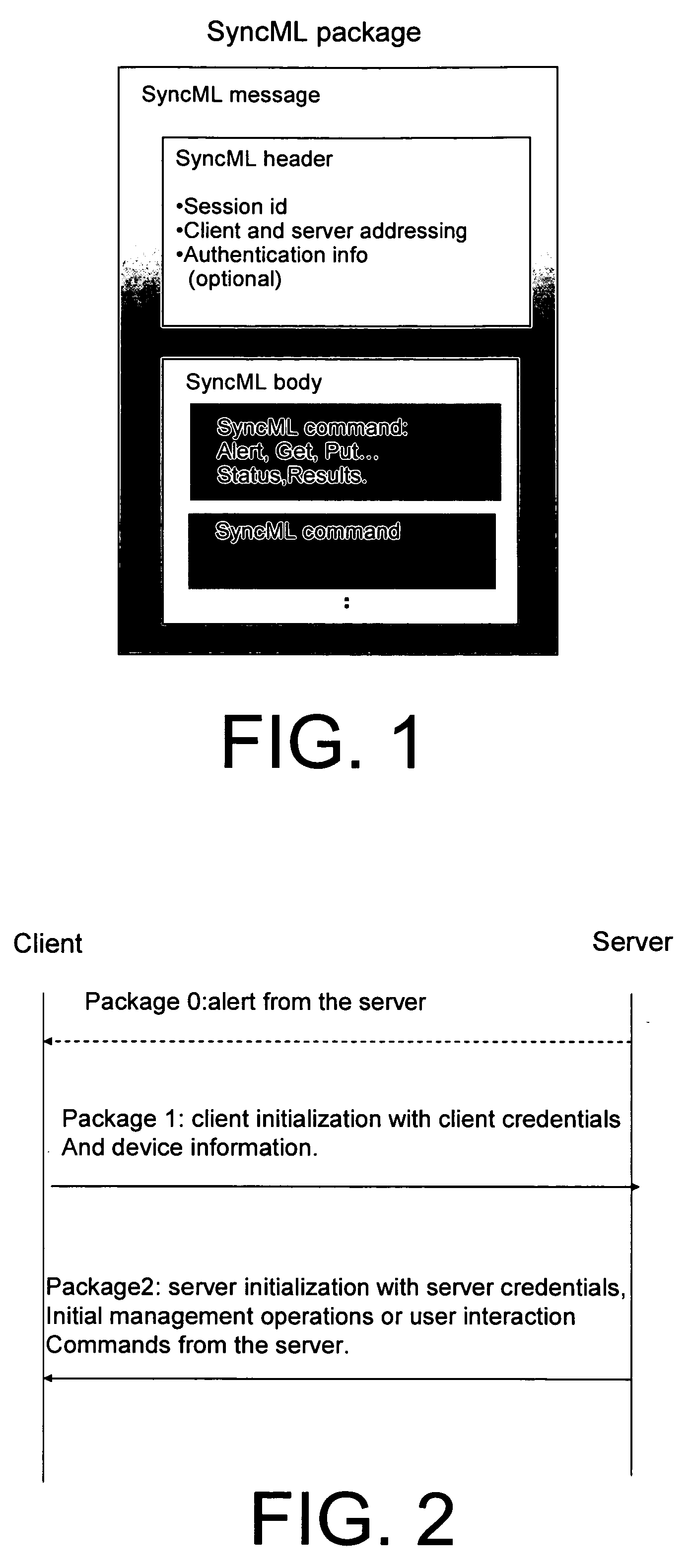
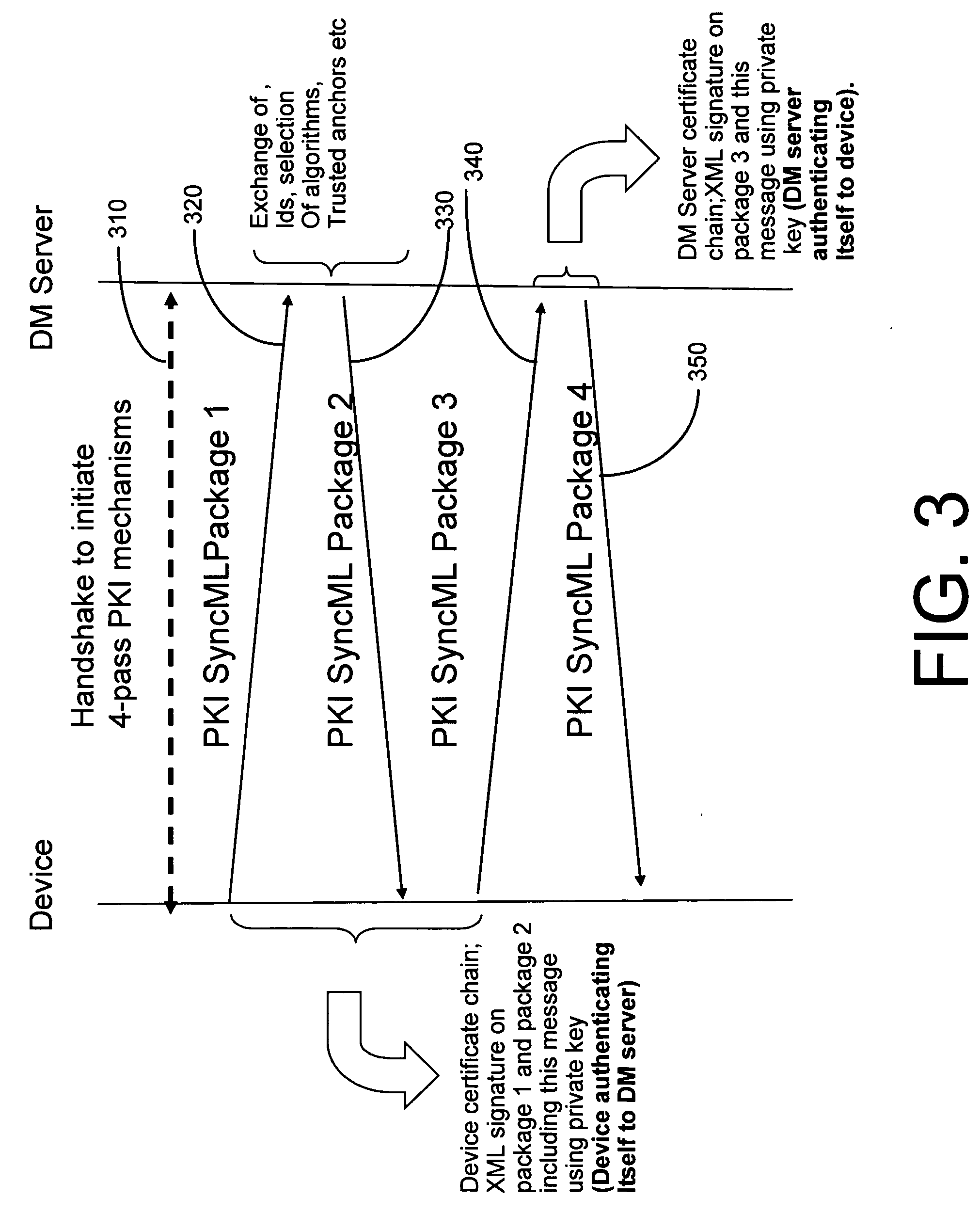
System and method for integrating PKI and XML-based security mechanisms in SyncML
Additions of extensions to SyncML protocol to incorporate PKI-based and XML-based security mechanisms. The present invention involves the partial incorporation of the PKI based mechanisms present in the Rights Object Acquisition Protocol (ROAP) suite of OMA DRMv2 model into the SyncML protocol, resulting in security enhancements for SyncML.
Owner:NOKIA CORP
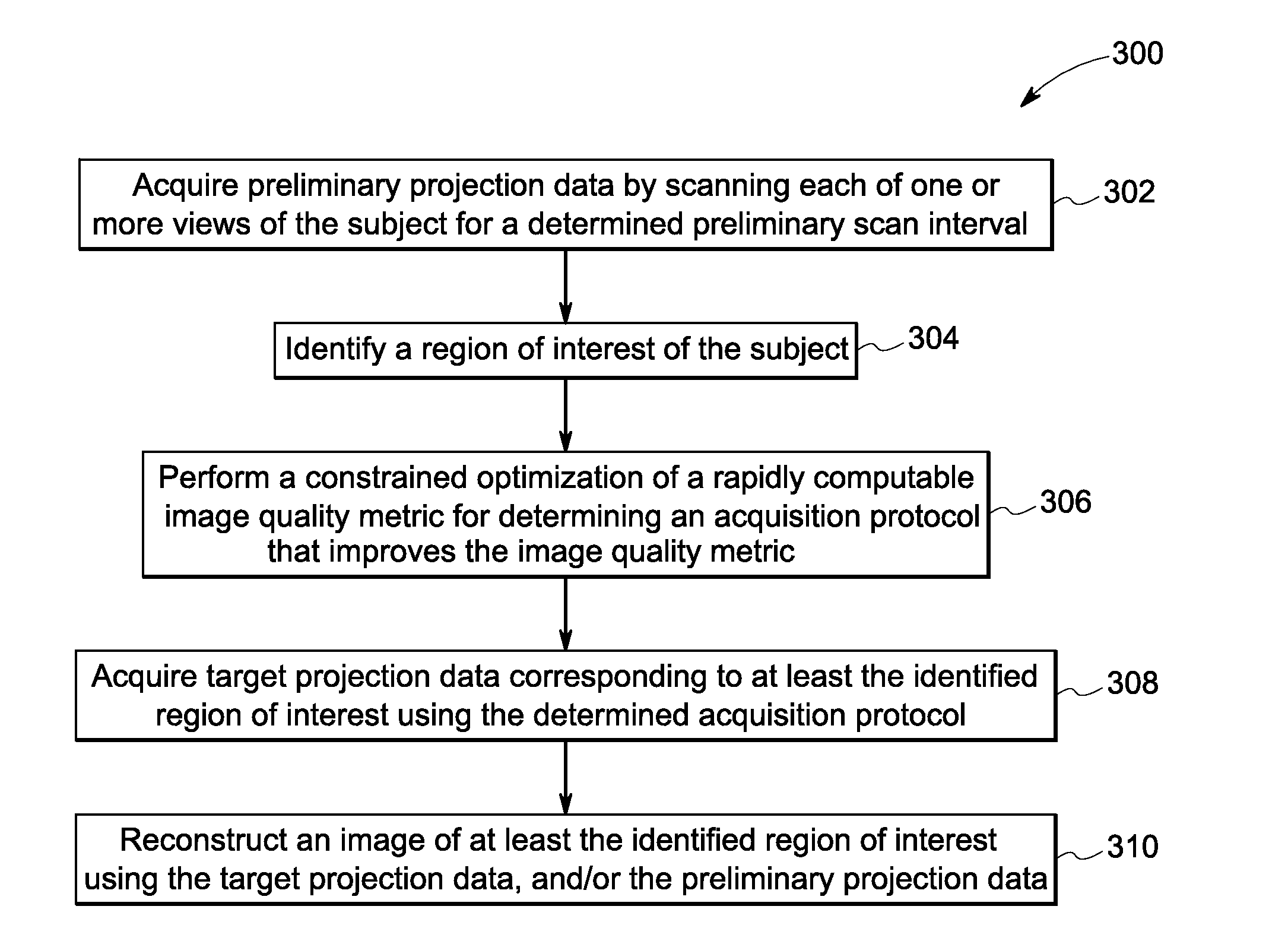
Methods and systems for adaptive tomographic imaging
ActiveUS20130105699A1Improves image quality metricMaterial analysis by optical meansCharacter and pattern recognitionPresent methodAdaptive imaging
Nuclear imaging systems, non-transitory computer readable media and methods for adaptive imaging are presented. Particularly, the present method includes acquiring preliminary projection data by scanning each of one or more views of a subject for a determined preliminary scan interval. Further, a region of interest of the subject is identified. The preliminary projection data is then used to perform a constrained optimization of a rapidly computable image quality metric for determining an acquisition protocol that improves the image quality metric at the identified region of interest. Particularly, the determined acquisition protocol is used to acquire target projection data corresponding to at least the identified region of interest. Further, an image of at least the identified region of interest is reconstructed using the target projection data, the preliminary projection data, or a combination thereof.
Owner:GENERAL ELECTRIC CO
Method for three dimensional multi-phase quantitative tissue evaluation
InactiveUS20070127789A1Ultrasonic/sonic/infrasonic diagnosticsHealth-index calculationComputed tomographyData source
A method of evaluating tissue of an organ includes accessing image data and processing the image data to quantify at least one feature of interest in the tissue. The image data is derived from a computed tomography acquisition system and includes multiple phases of acquired whole organ data. Each phase is acquired within five gantry rotations of the acquisition system using an acquisition protocol.
Owner:GENERAL ELECTRIC CO
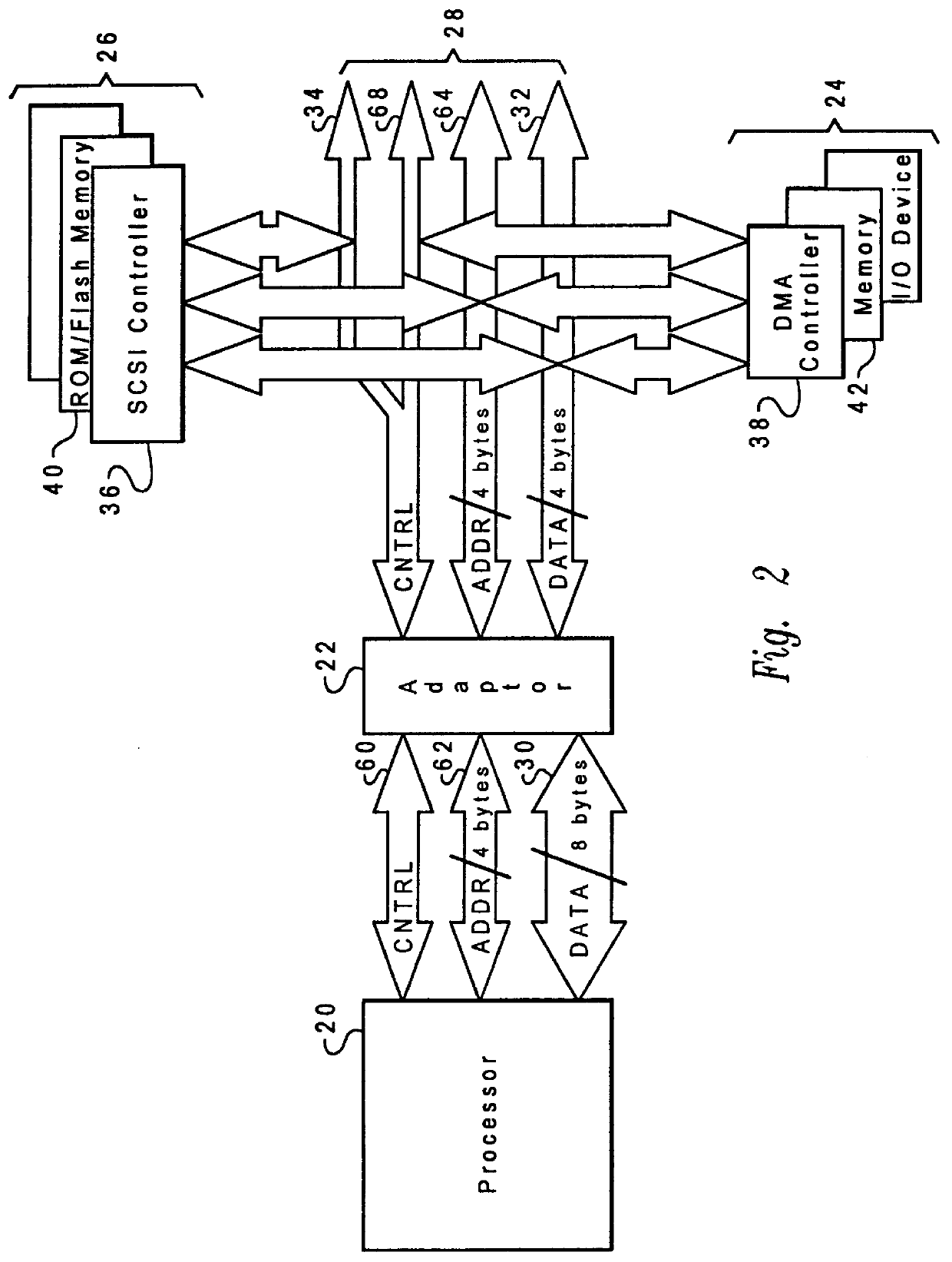
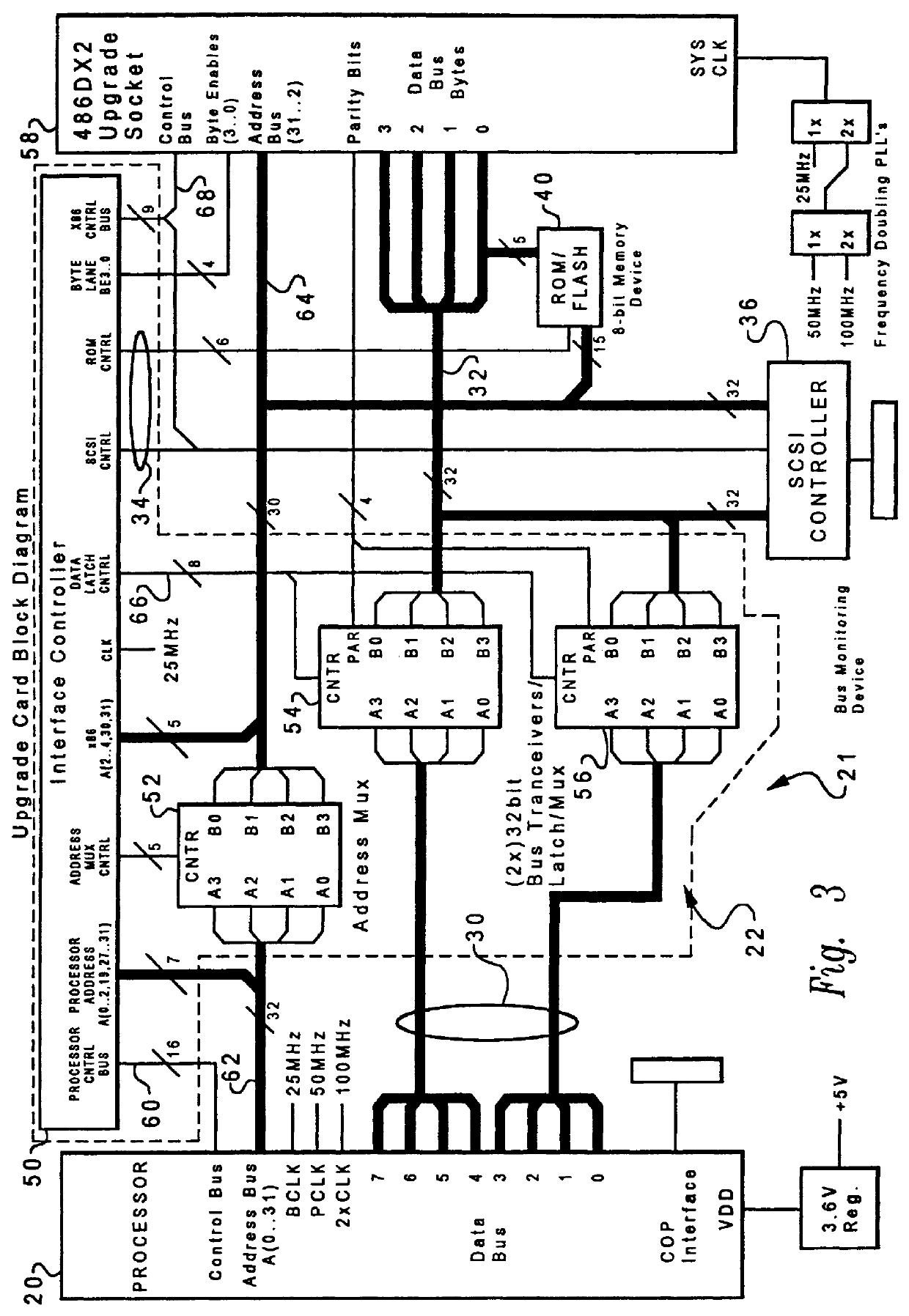
Method and system for arbitrating between bus masters having diverse bus acquisition protocols
A data processing system is disclosed which includes a first processor having an m-byte data width, an n-byte data bus, where n is less than m, and a second processor electrically coupled to the bus which performs bus transactions utilizing n-byte packets of data. An adaptor is electrically coupled between the first processor and the bus which converts n-byte packets of data input from the bus to m-byte packets of data, and converts m-byte packets of data input from the first processor to n-byte packets of data, thereby enabling the first processor to transmit data to and receive data from the bus utilizing m-byte packets of data. In a second aspect of the present invention, a method and system are provided for arbitrating between two bus masters having disparate bus acquisition protocols. In response to a second bus master asserting a bus request when a first bus master controls the bus, control of the bus is removed from the first bus master. Thereafter, in response to a signal transmitted from an arbitration control unit to the first bus master instructing the first bus master to terminate its bus transactions, control of the bus is granted to the second bus master. In response to the second bus master terminating its bus request, control of the bus is granted to the first bus master and a signal is transmitted from the arbitration control unit to the first bus master acknowledging the grant of control.
Owner:IBM CORP
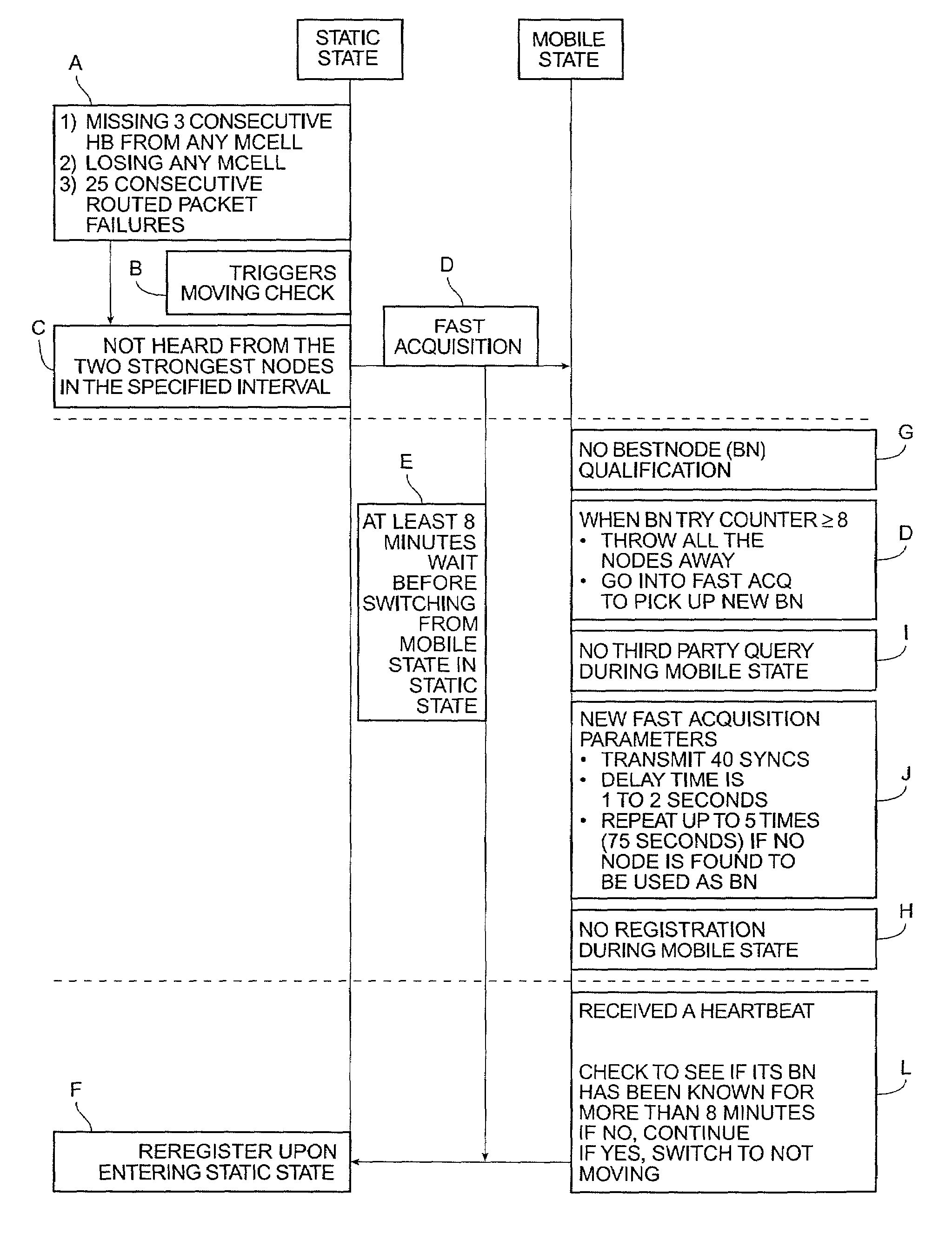
Method for enhancing mobility in a wireless mesh network
Owner:GOOGLE LLC
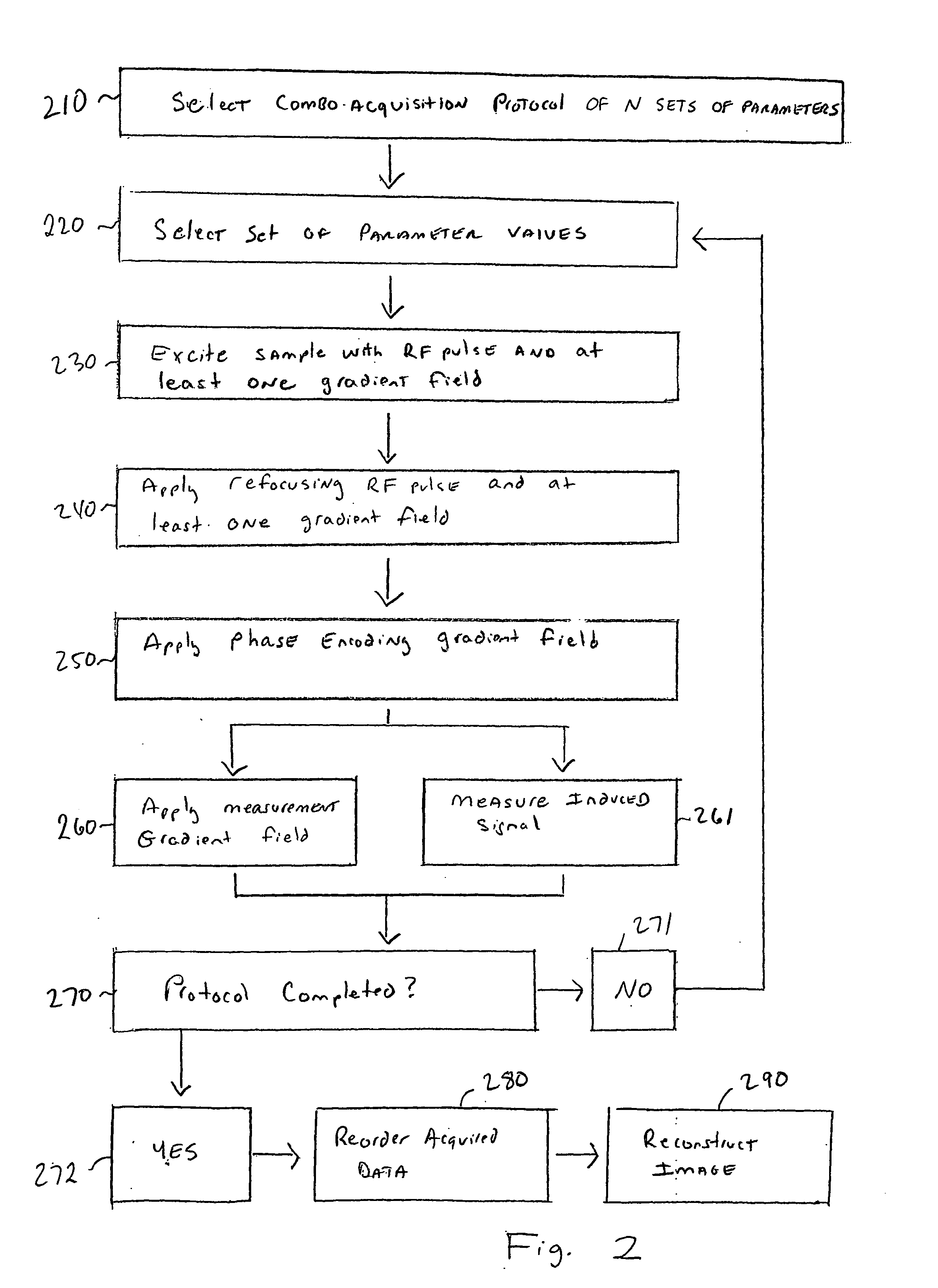
Combined magnetic resonance data acquisition of multi-contrast images using variable acquisition parameters and k-space data sharing
InactiveUS20050033151A1Reduce scan timeDiagnostic recording/measuringMeasurements using NMR imaging systemsResonanceData acquisition
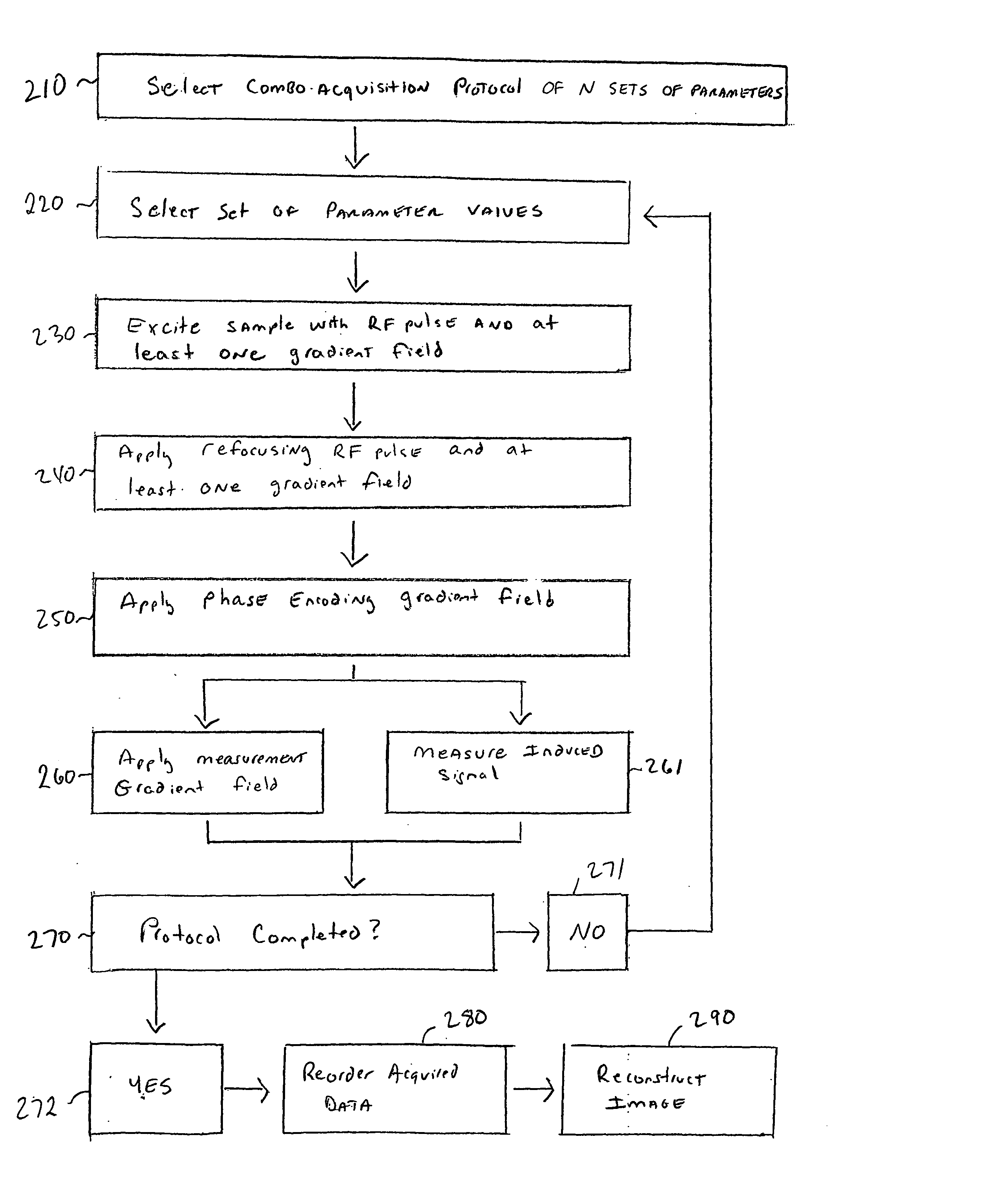
Techniques for reducing the scan time required for the acquisition of two or more magnetic resonance imaging images of a subject having differing contrasts. In one arrangement, a combo acquisition protocol of N sets of parameters is selected prior to imaging. In order to image a subject, a first set of parameter values is selected from the protocol, a first RF pulse and at least one gradient field are used to excite the subject, a refocusing RF pulse and at least one gradient field is applied to the subject, a phase encoding gradient field is applied to the subject, and then a measurement gradient field is applied to the subject simultaneously while an induced signal is measured. The process is repeated to obtain N measurements, which are then processed into two or more reconstructed images of differing contrast, and where some of the measurements are used during the reconstruction of two or more of the images.
Owner:WU ED X +2
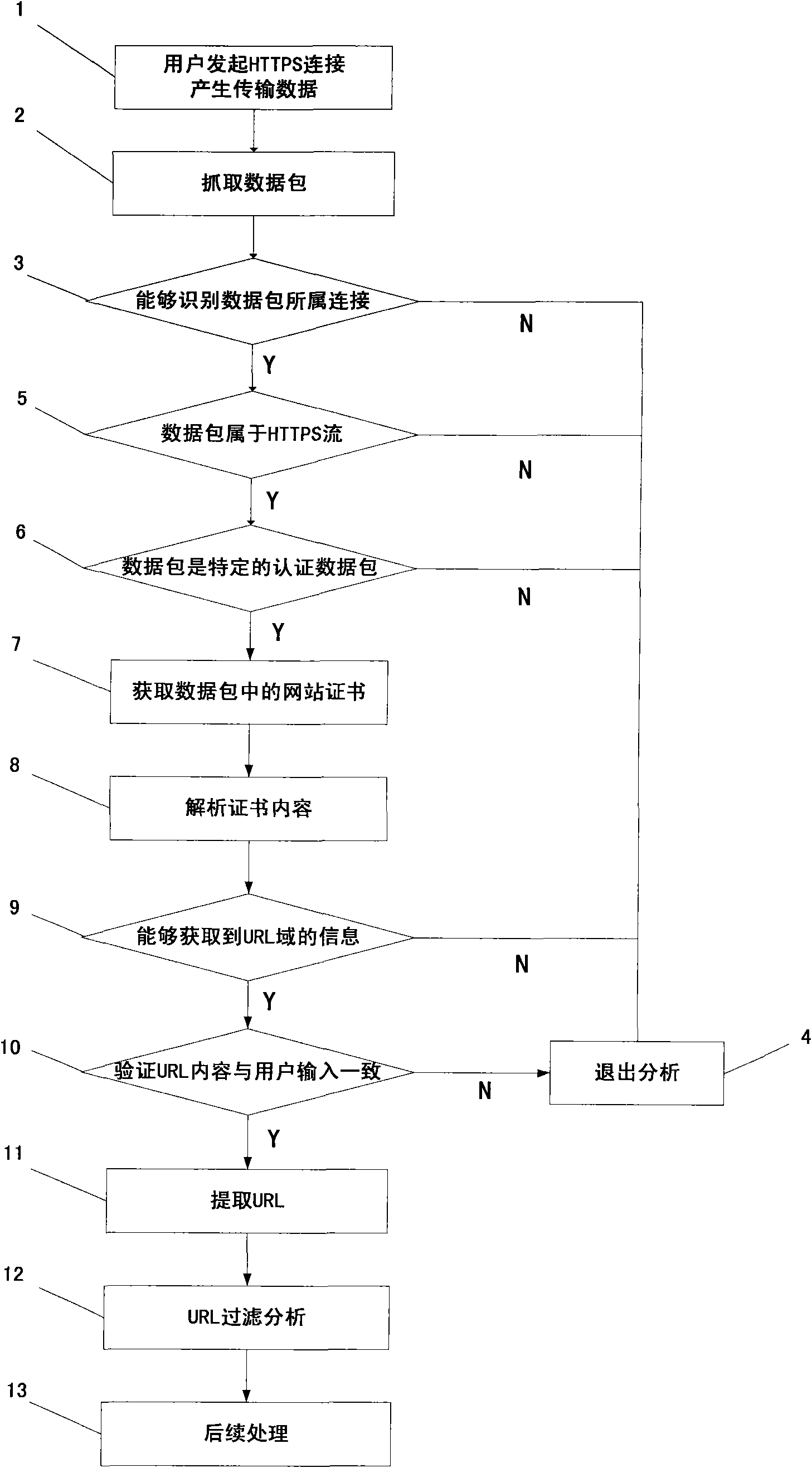
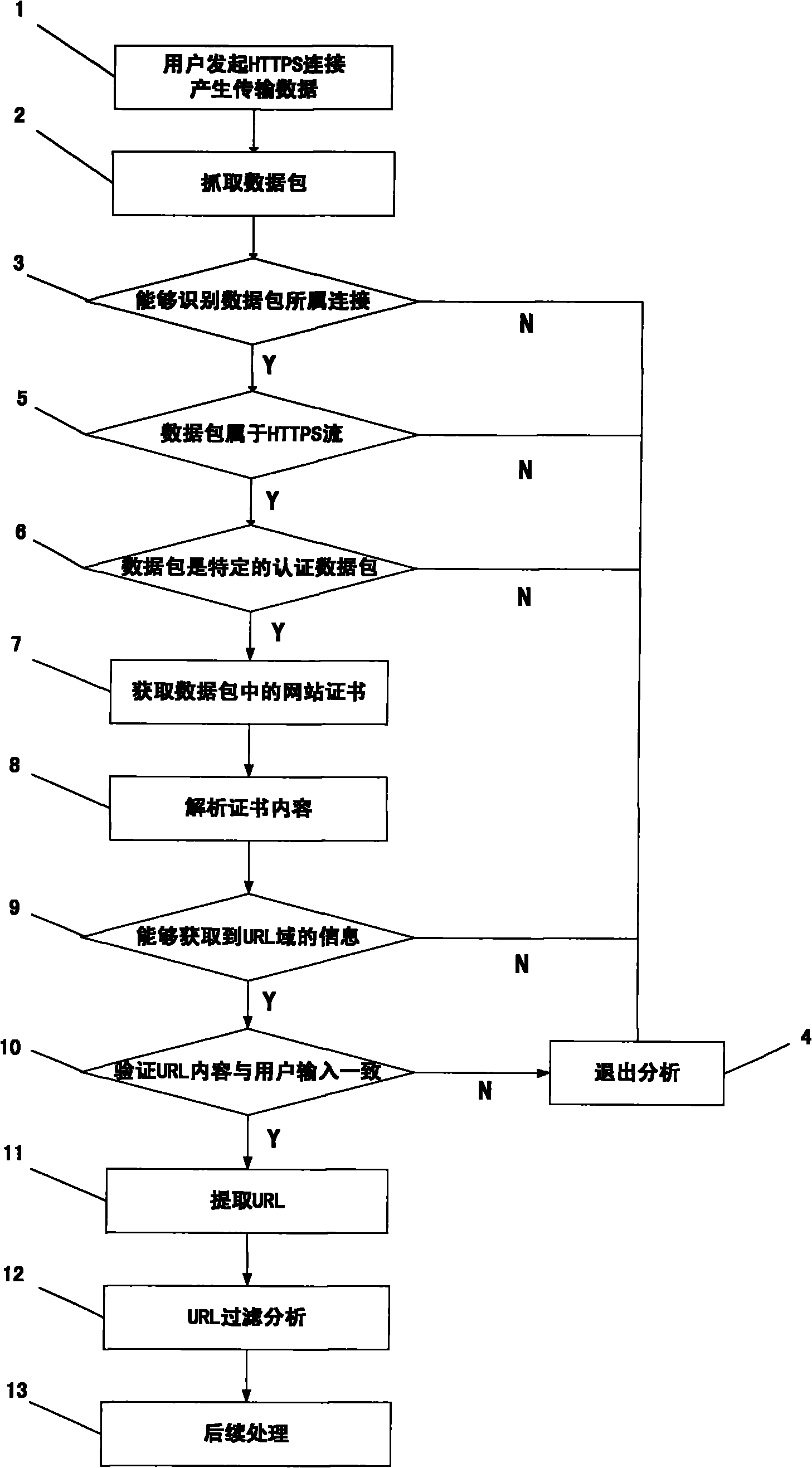
URL (Uniform Resource Locator) filtering method aiming at HTTPS (Hypertext Transport Protocol Server) encrypted website access
The invention discloses a URL (Uniform Resource Locator) filtering method aiming at HTTPS (Hypertext Transport Protocol Server) encrypted website access. The HTTPS is a secure access protocol based on identity authentication. The method comprises the following steps of: firstly, recognizing an HTTPS protocol stream and acquiring an authentification message in the protocol stream trough an analysis method through capturing data packets; then, analyzing a website certificate in the authentification message and extracting URL information, i.e. a webpage address; and finally, identifying the URL accessed by a user, matching to obtain an URL attribute class through a special URL library and filtering and blocking URLs beyond the permitted range of an access rule. The technical scheme of the invention is adopted to provide a security protection mechanism for network application, solves the problem of difficulty in URL acquisition because of encrypted HTTPS transmission and can fully filter HTTPS websites accessed by the user.
Owner:BEIJING VRV SOFTWARE CO LTD
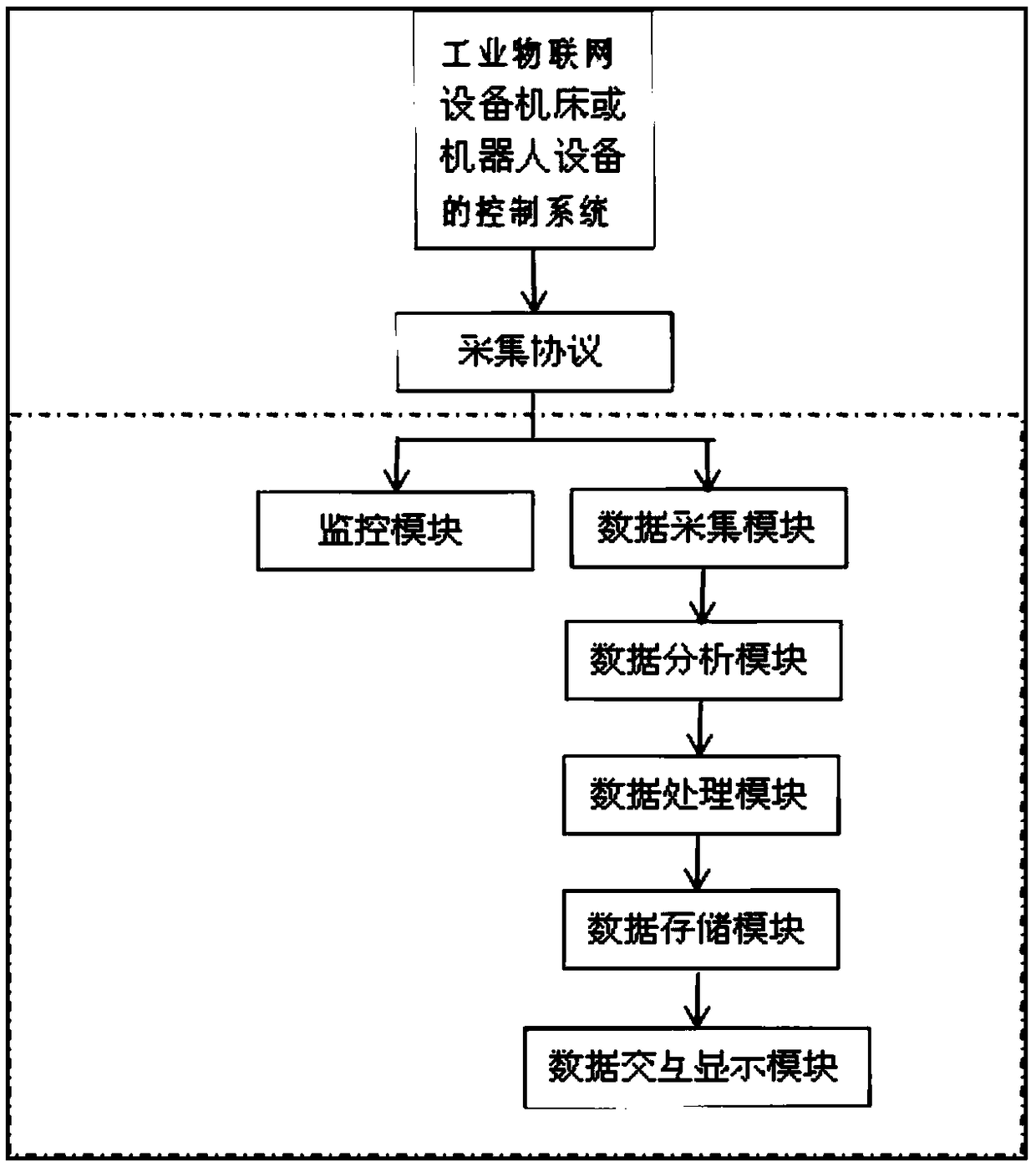
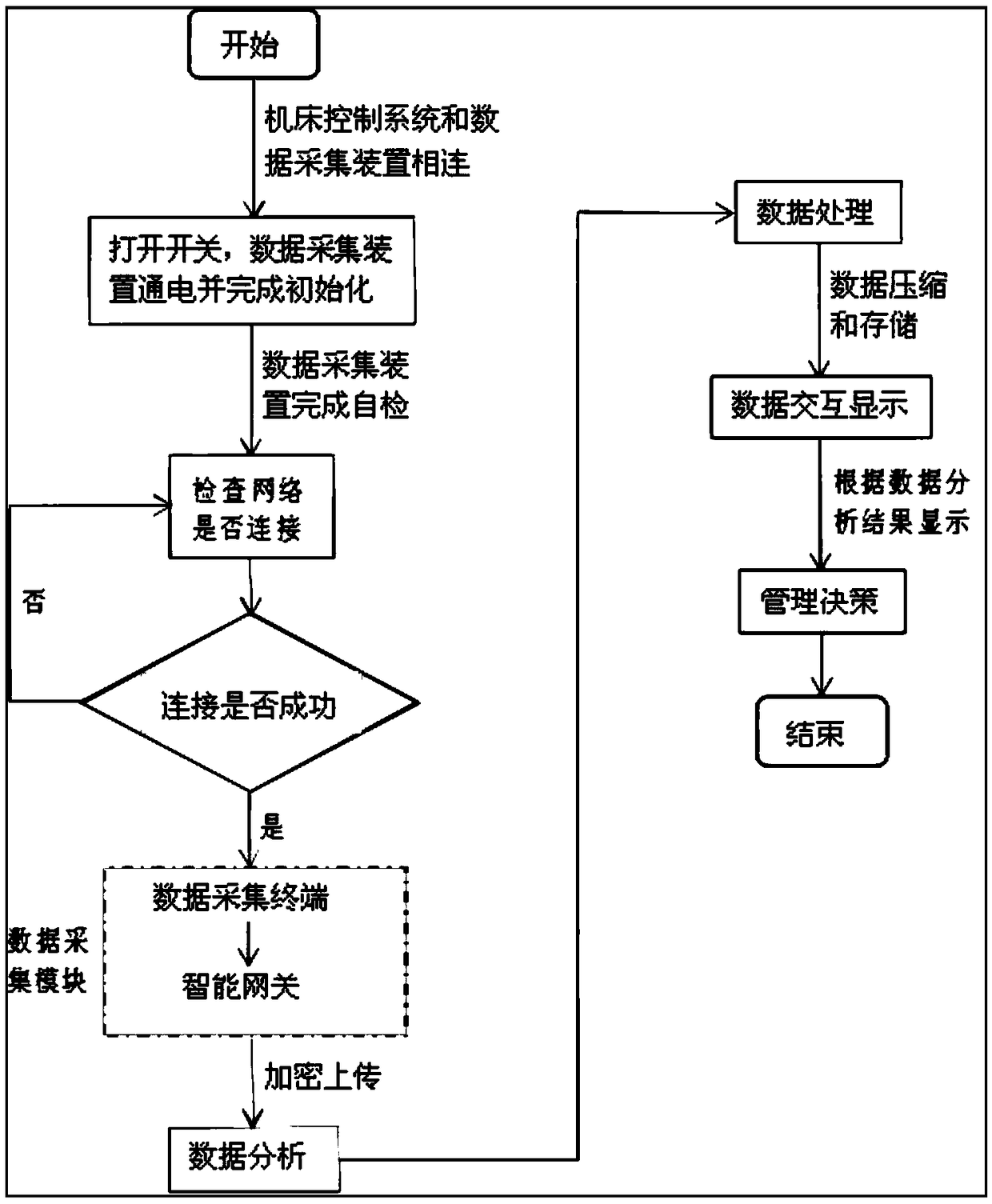
Industrial intelligent manufacturing data acquisition apparatus and method based on Internet of Things
PendingCN108762210AEasy to exportRefined production managementTotal factory controlProgramme total factory controlIndustrial equipmentThe Internet
The invention discloses an industrial intelligent manufacturing data acquisition apparatus and method based on the Internet of Things. The apparatus comprises a data acquisition module, a data transmission module, a data analysis module, a data processing module, a data storage module, a data interaction display module and a monitoring module, the data acquisition module is connected with a control system of an industrial Internet of Things equipment machine tool through an acquisition protocol, the data acquisition module, the data transmission module, the data analysis module, the data processing module, the data storage module and the data interaction display module are connected in sequence, and the monitoring module is connected with the control system of the industrial Internet of Things equipment machine tool through the acquisition protocol. According to the method and apparatus, data acquisition, analysis, transmission, storage and monitoring are performed for industrial Internet of Things factory equipment machine tools and robot equipment etc., the work efficiency is improved, the production cost is reduced, the information interaction between industrial equipment and production management personnel is enhanced, the efficiency of the equipment is improved, and intelligent and datamation management of factory processing equipment can be realized.
Owner:银川华信智信息技术有限公司
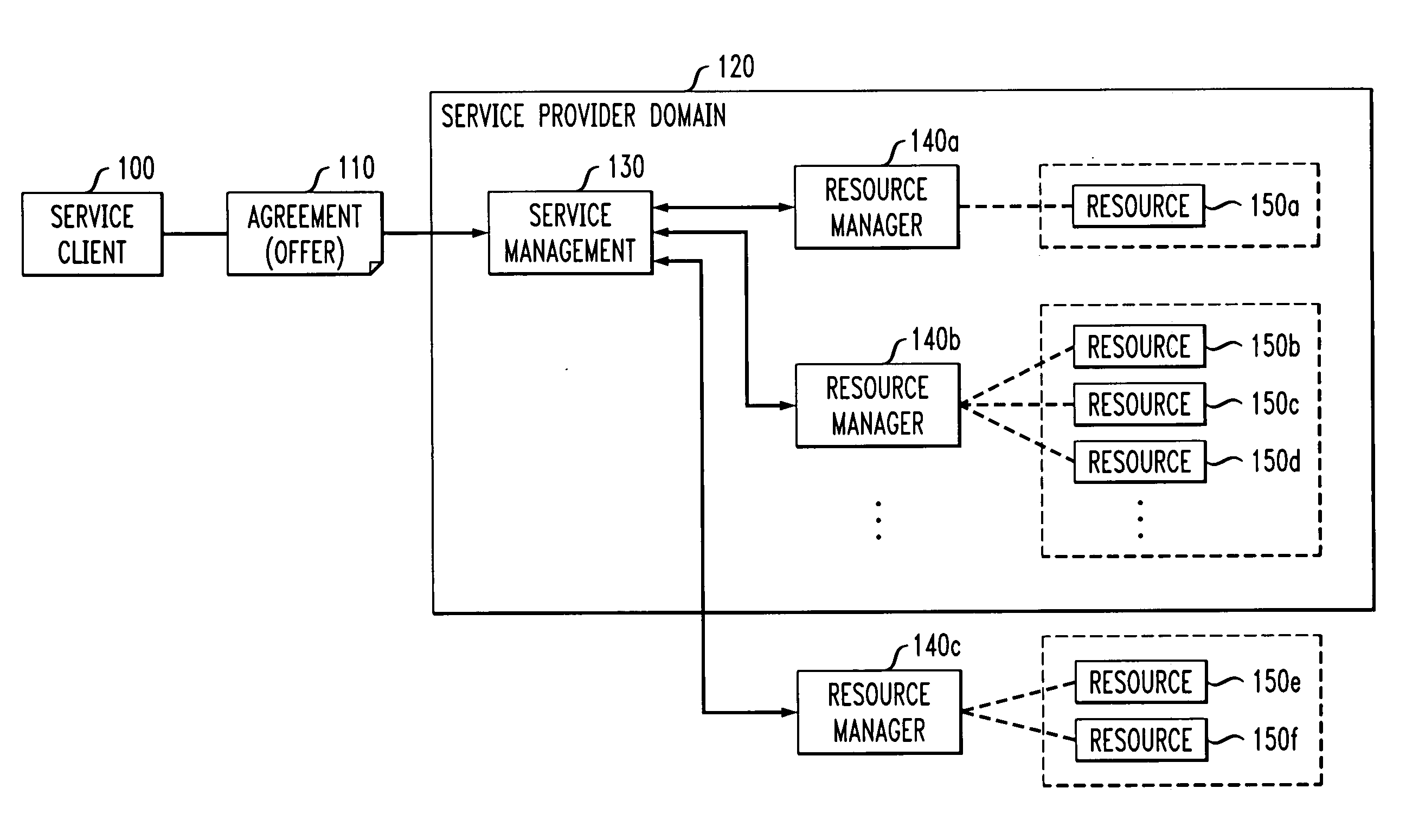
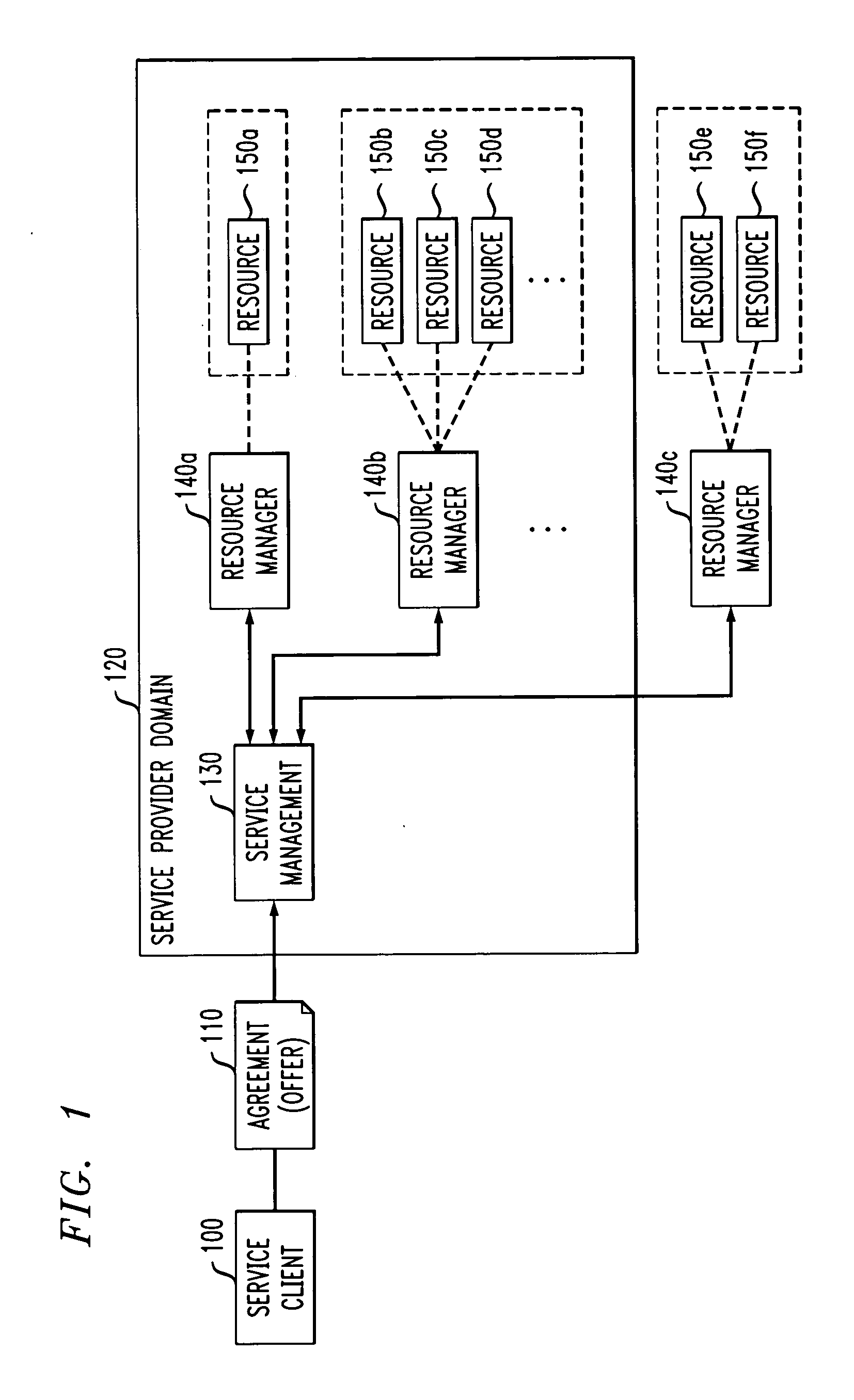
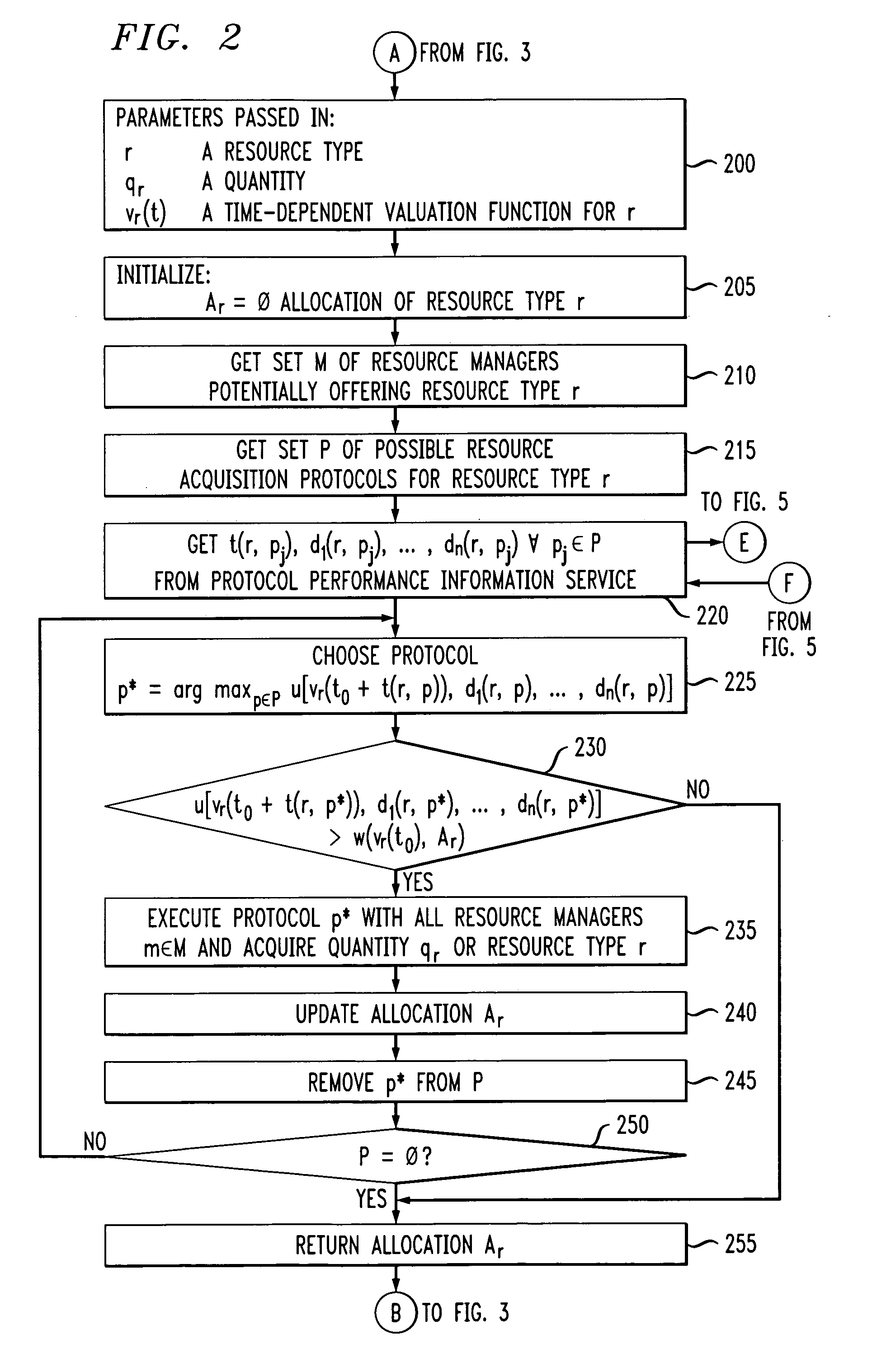
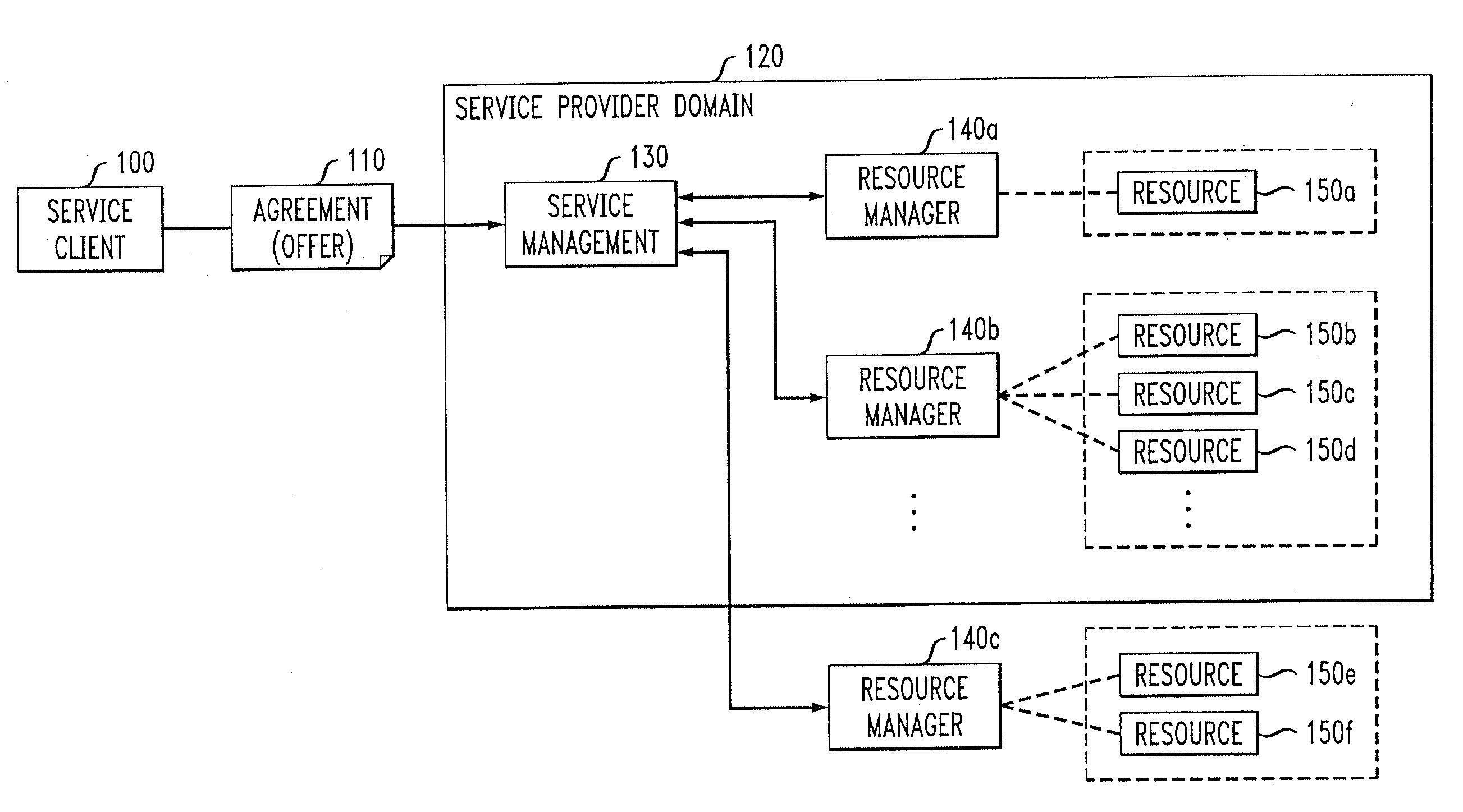
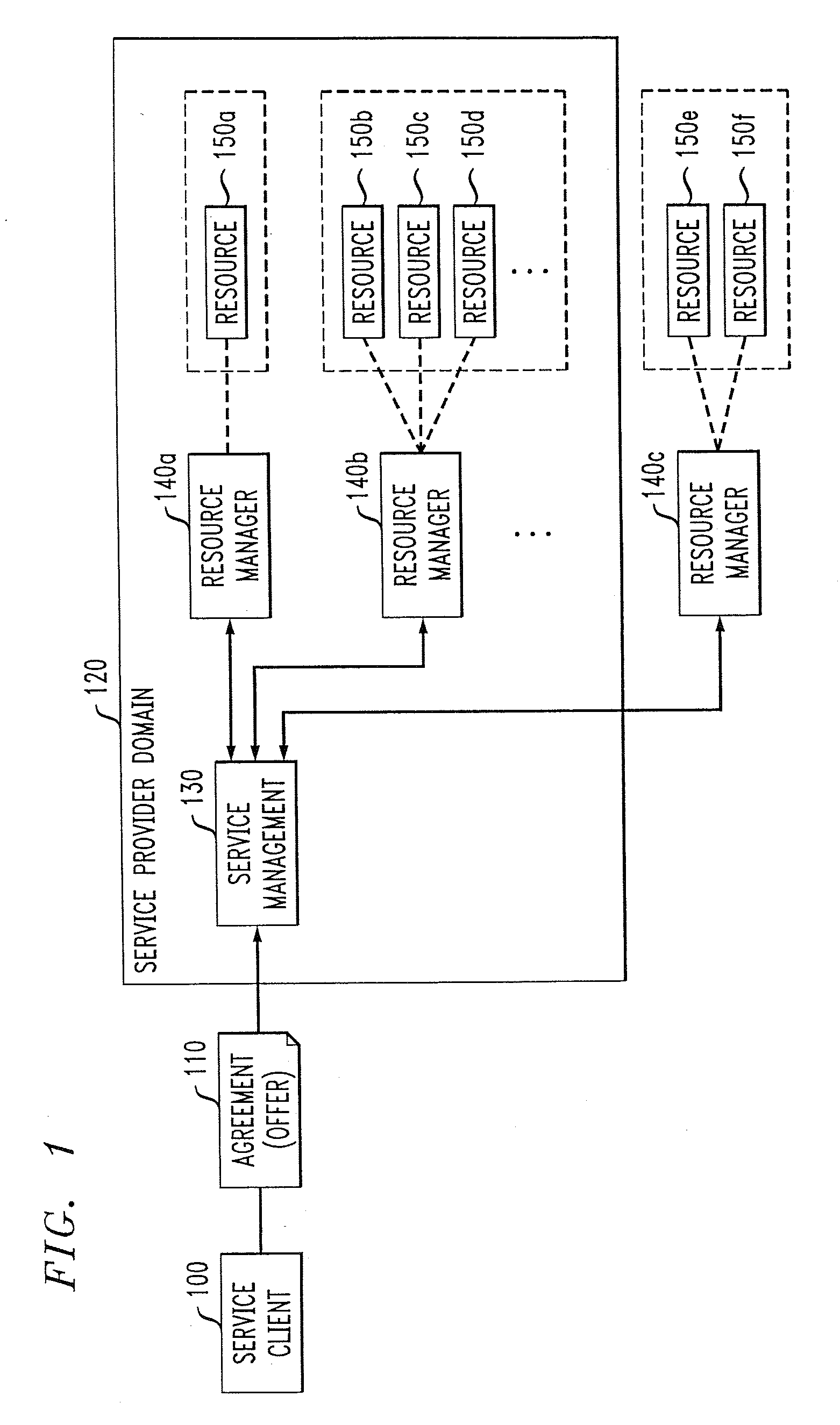
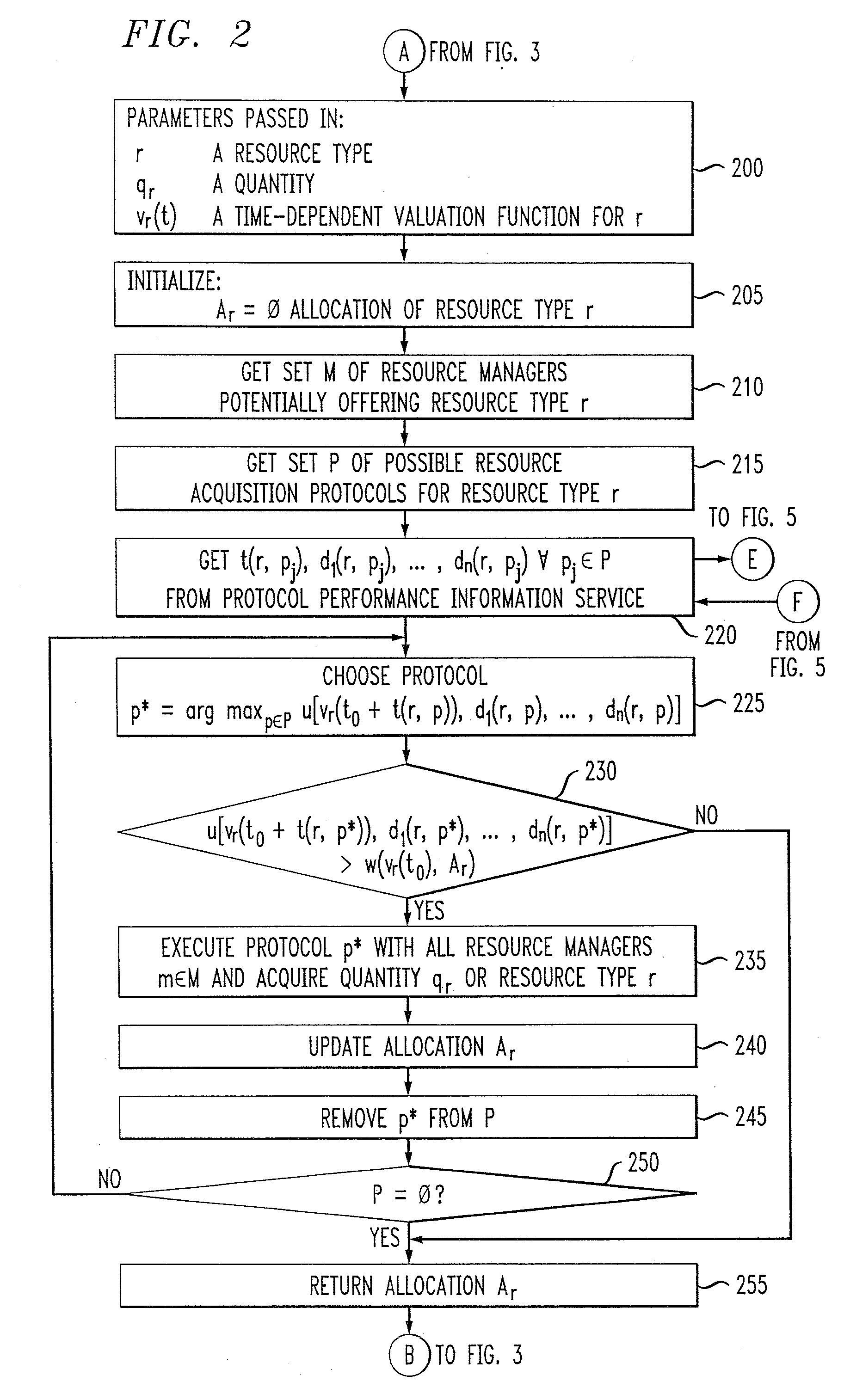
Methods and apparatus for coordinating and selecting protocols for resources acquisition from multiple resource managers
Techniques are disclosed for allocation of resources under the control of resource managers and the choice and coordination of resource acquisition protocols to communicate with these resource managers. The resource managers may be distributed and heterogeneous. For example, a technique for use by a service provider for allocating one or more resources from multiple resources associated with multiple resource managers based on at least one service agreement offer from a service client comprises the following steps / operations. At least one service agreement offer is obtained. A resource allocation is automatically determined based on the obtained service agreement offer. The automated step / operation of determining the resource allocation comprises: (i) coordinating selection of a resource acquisition protocol from among multiple resource acquisition protocols for use in communicating with the multiple resource managers to acquire one or more resources associated therewith; and (ii) evaluating a performance associated with one or more of the multiple resource acquisition protocols.
Owner:IBM CORP
Method for enhancing mobility in a wireless mesh network
InactiveUS7050806B2Radio/inductive link selection arrangementsRadio transmissionCommunications systemWireless mesh network
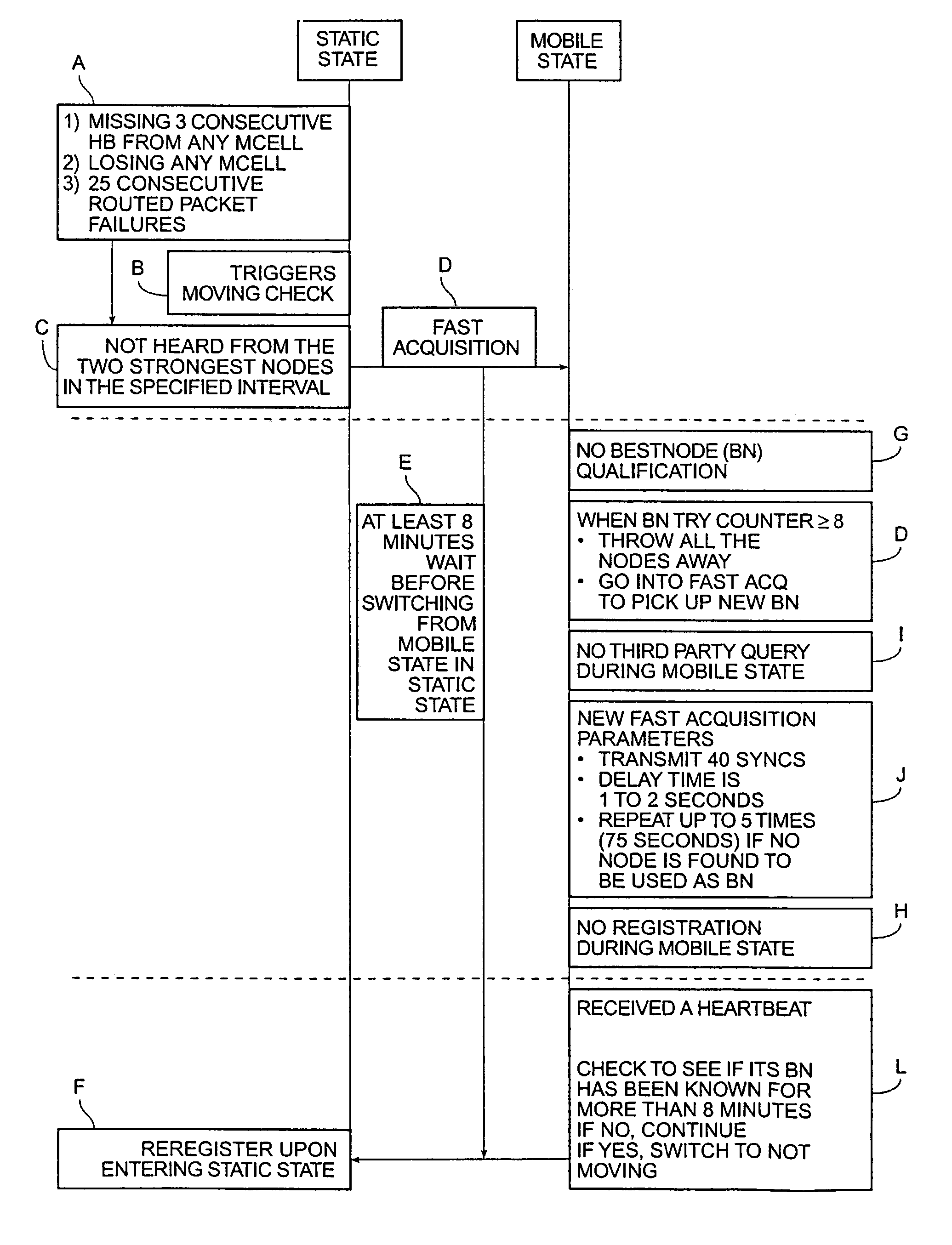
In a wireless communication system having sometimes mobile subscriber units and a plurality of fixed network devices located at cell sites, a multimode acquisition protocol is provided at each subscriber unit which first senses whether the subscriber unit is static or mobile from the nature and quality of the communication links with nearby network devices and then enables an acquisition protocol suited to either static mode or mobile mode. In a specific embodiment, the protocol initiates procedures to change acquisition mode from static to mobile upon failure of the subscriber unit to sense three consecutive scheduled polling packets sent by a linked network device or upon loss of communication with any locally-known network device or upon failure to transmit 25 consecutive data packets. In such case, the procedure is initiated to determine whether it is appropriate to switch to a mobile mode for purposes of acquisition.
Owner:GOOGLE LLC +1
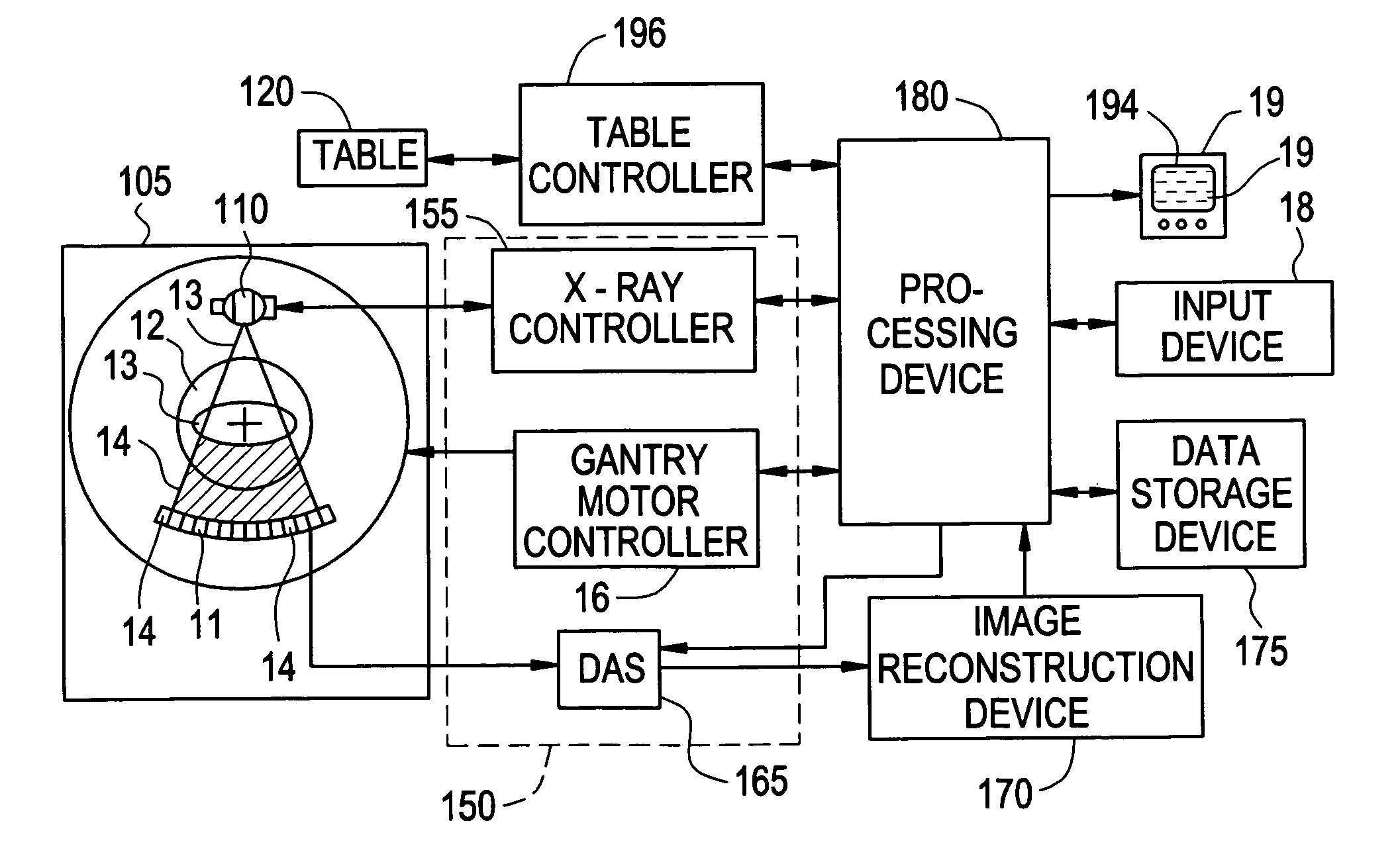
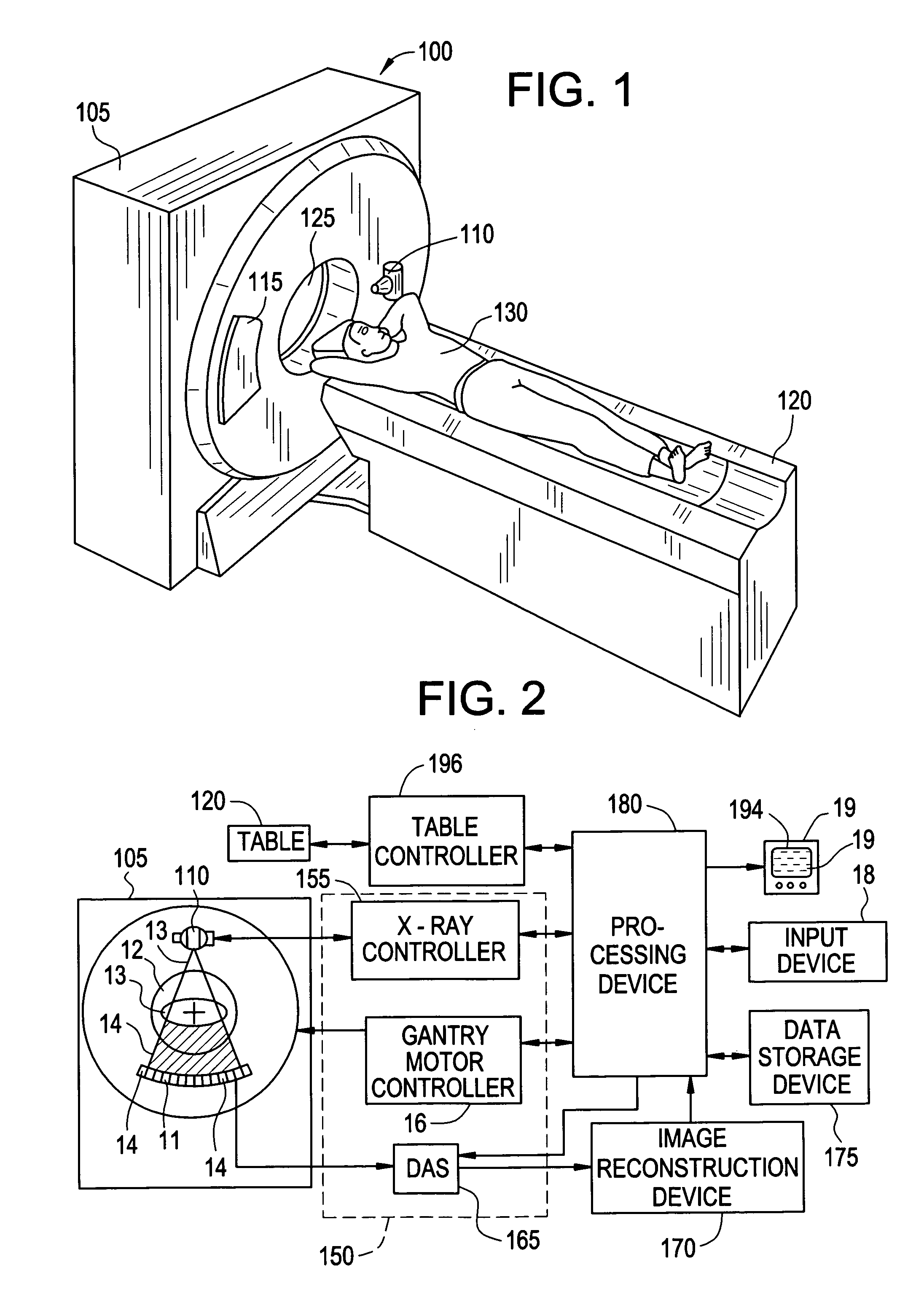
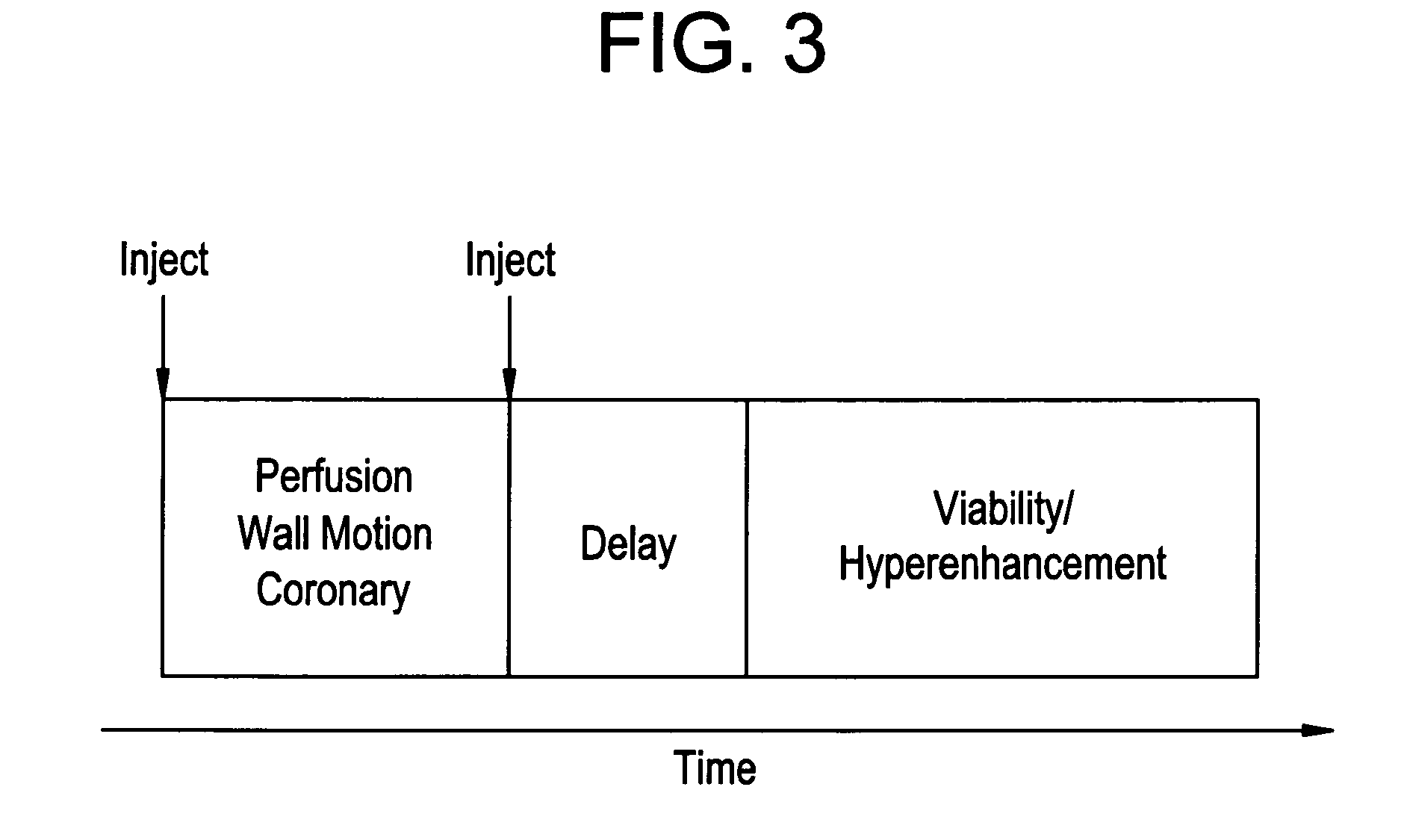
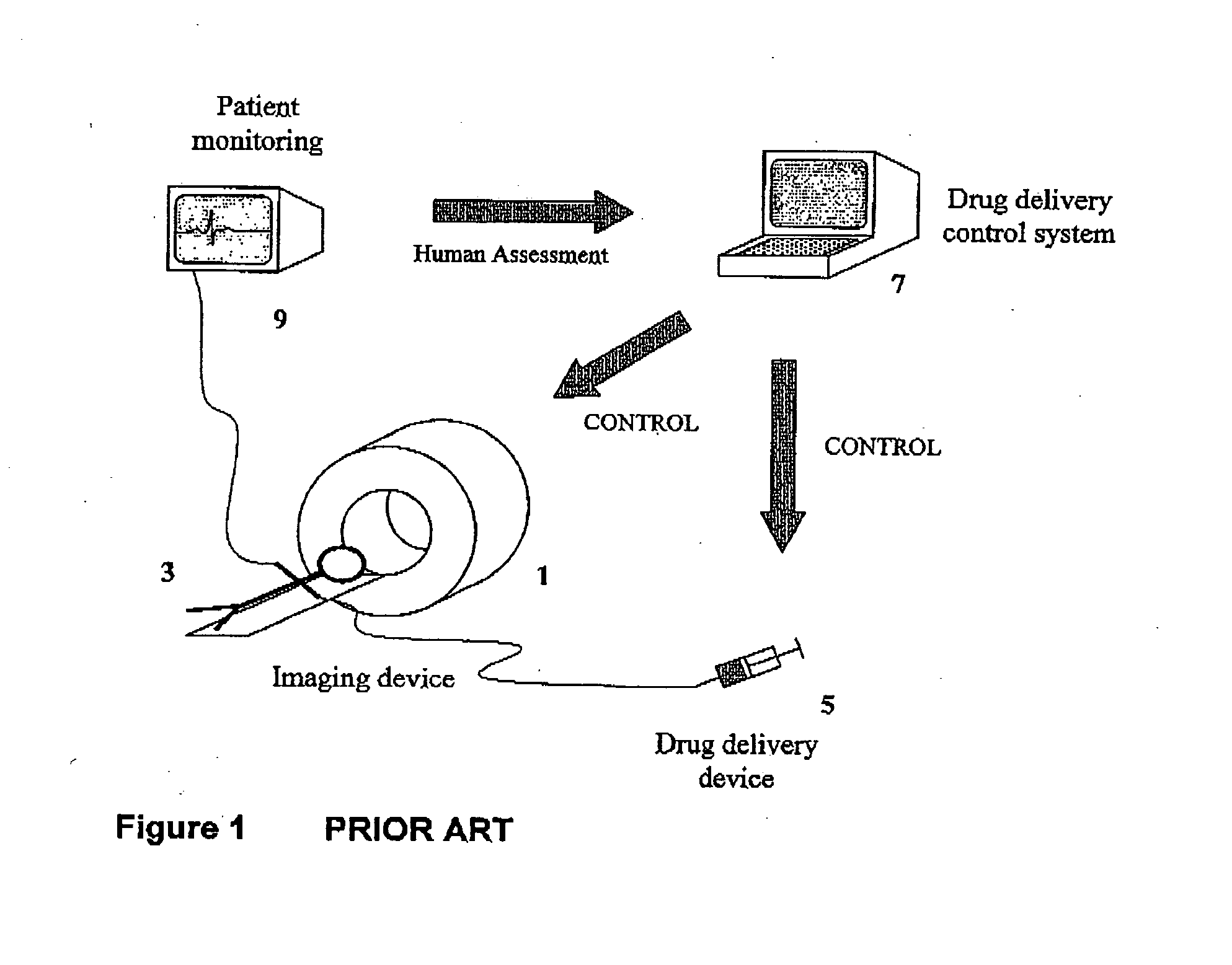
System for controlling medical data acquisition processes
InactiveUS20040172303A1Closer controlSimple wayMedical simulationData processing applicationsData controlAcquisition apparatus
A system for controlling medical data acquisition, such as imaging, comprises a supervisory protocol controller which controls in real time a data acquisition device, such as an imaging apparatus, and an agent administration controller, such as a drug delivery device for delivering contrast agent. The supervisory protocol controller receives data from the acquisition apparatus and controls the acquisition apparatus and the administration controller based on that acquired data. Thus the acquisition protocol can be controlled and changed in response to the actual acquisition circumstances.
Owner:SIEMENS MEDICAL SOLUTIONS USA INC
Adjusting acquisition protocols for dynamic medical imaging using dynamic models
ActiveUS8705819B2Efficient and/or reliable way of adjusting an acquisition protocolImprove image qualityImage enhancementImage analysisDynamic modelsHemodynamics
Owner:KONINK PHILIPS ELECTRONICS NV
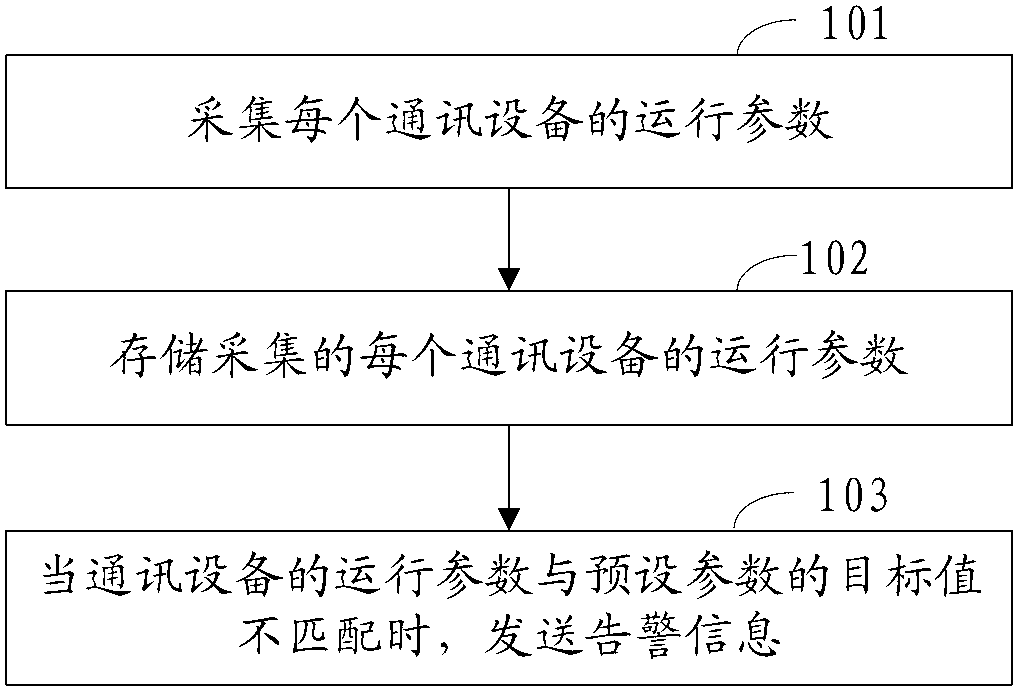
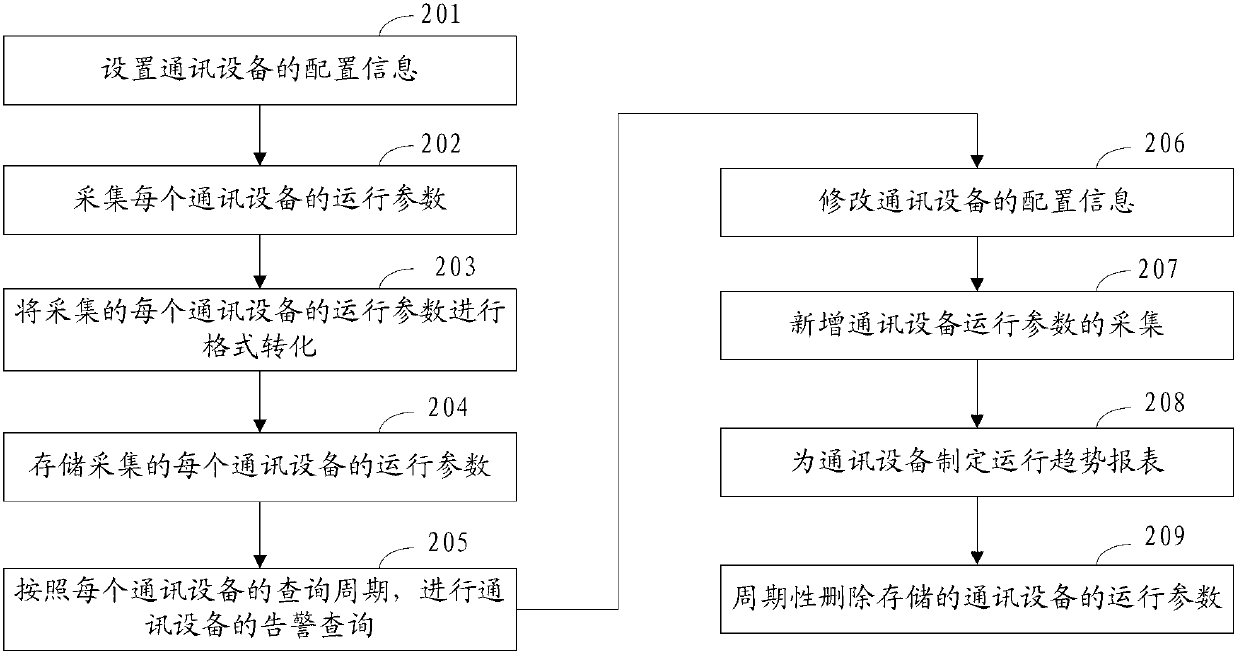
Call center monitoring method, device and system
InactiveCN103281461AImprove maintenance efficiencyRealize centralized monitoringSupervisory/monitoring/testing arrangementsState parameterMonitoring system
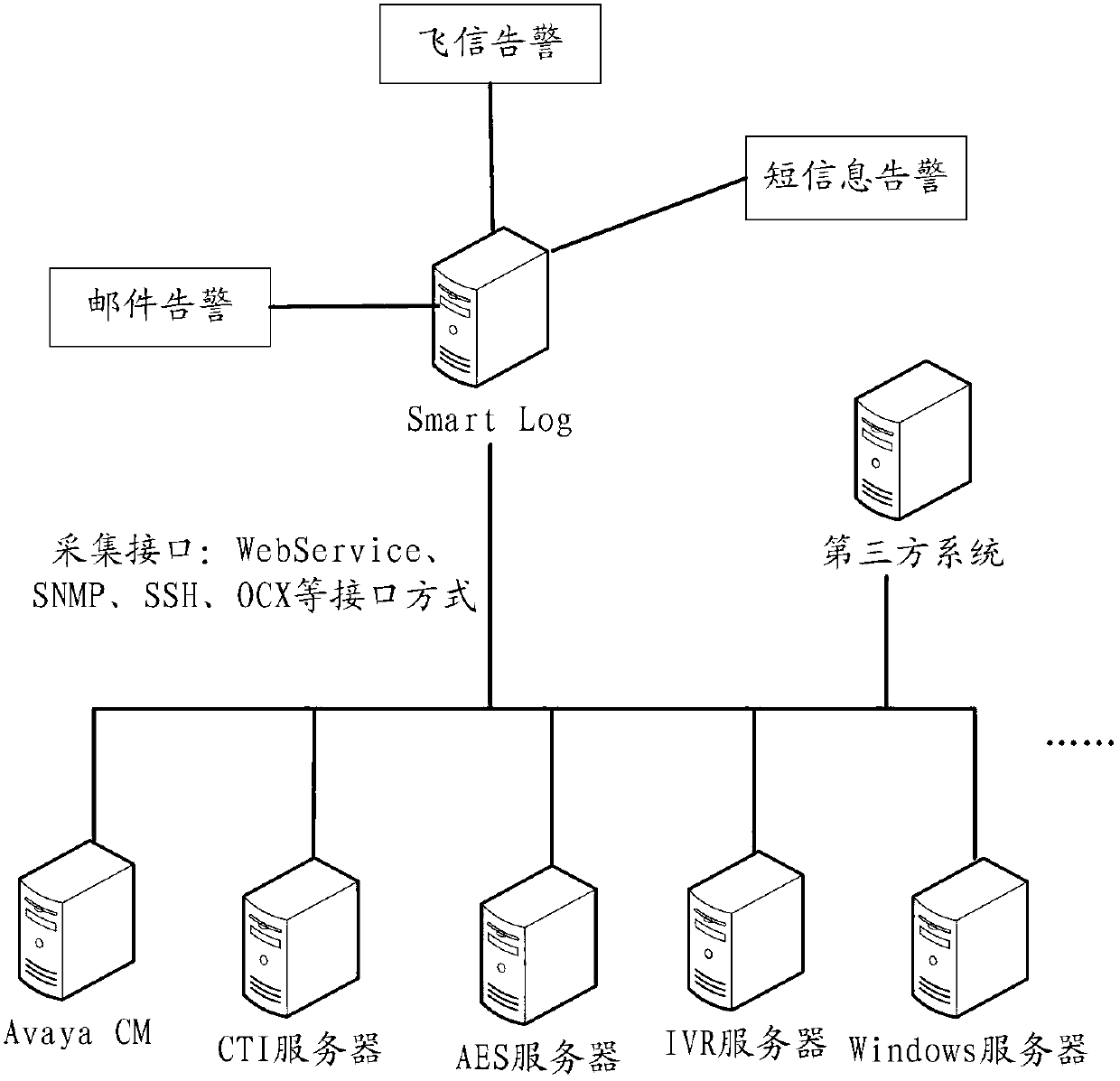
The invention discloses a call center monitoring method, a call center monitoring device and a call center monitoring system, wherein the method comprises the steps that the operating parameters of each piece of communication equipment are collected according to the acquisition protocol of each piece of communication equipment, and the operating parameters include the state parameter and the performance parameter; the collected operating parameters of each piece of communication equipment are stored; alarm inquiries of different communication equipment are carried out according to the stored operating parameters of different communication equipment; the alarm inquiry comprises: whether the stored operating parameters of the communication equipment are matched with the preset parameter target values or not are judged, and alarm information is sent when mismatching occurs. According to the method, the device and the system, one monitoring platform is adopted to monitor a call center as one integral monitoring object, and the invention avoids the situation in the prior art that multiple monitoring platforms are used, each monitoring platform corresponds to one type of communication equipment, and communication equipment in the call center is monitored in a centralized manner. When communication equipment is in fault, alarm information can be sent automatically, monitoring staff do not need to query and find out the fault actively, and the maintenance efficiency of the call center is improved.
Owner:SHANGHAI EAST CHINA COMPUTER CO LTD
Methods and Apparatus for Coordinating and Selecting Protocols for Resources Acquisition from Multiple Resource Managers
Techniques are disclosed for allocation of resources under the control of resource managers and the choice and coordination of resource acquisition protocols to communicate with these resource managers. The resource managers may be distributed and heterogeneous. For example, a technique for use by a service provider for allocating one or more resources from multiple resources associated with multiple resource managers based on at least one service agreement offer from a service client comprises the following steps / operations. At least one service agreement offer is obtained. A resource allocation is automatically determined based on the obtained service agreement offer. The automated step / operation of determining the resource allocation comprises: (i) coordinating selection of a resource acquisition protocol from among multiple resource acquisition protocols for use in communicating with the multiple resource managers to acquire one or more resources associated therewith; and (ii) evaluating a performance associated with one or more of the multiple resource acquisition protocols.
Owner:INT BUSINESS MASCH CORP
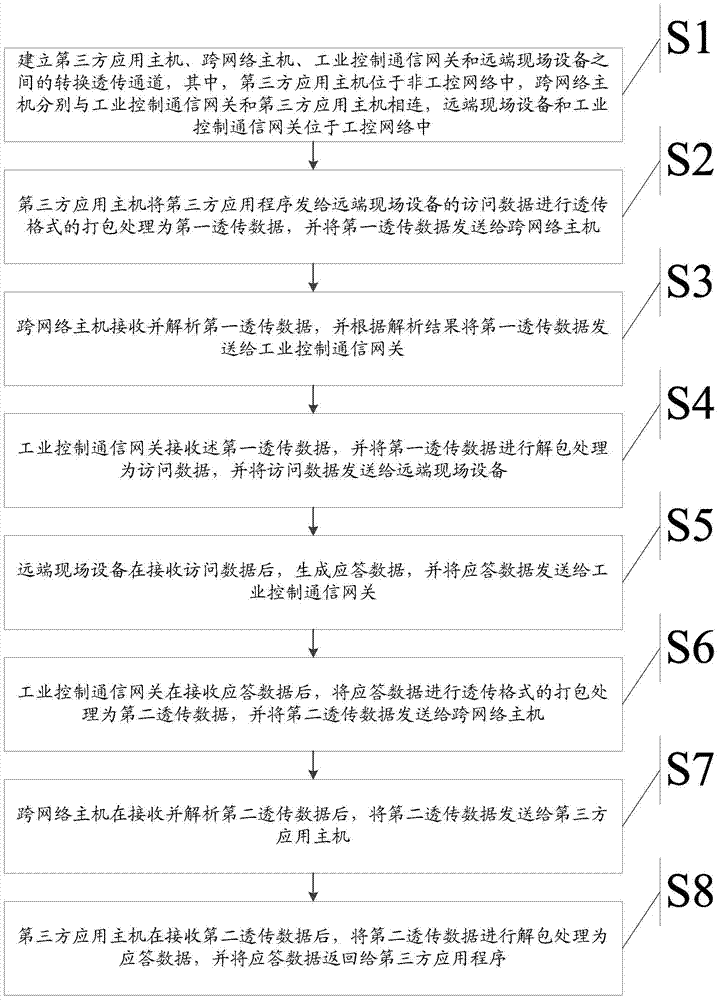
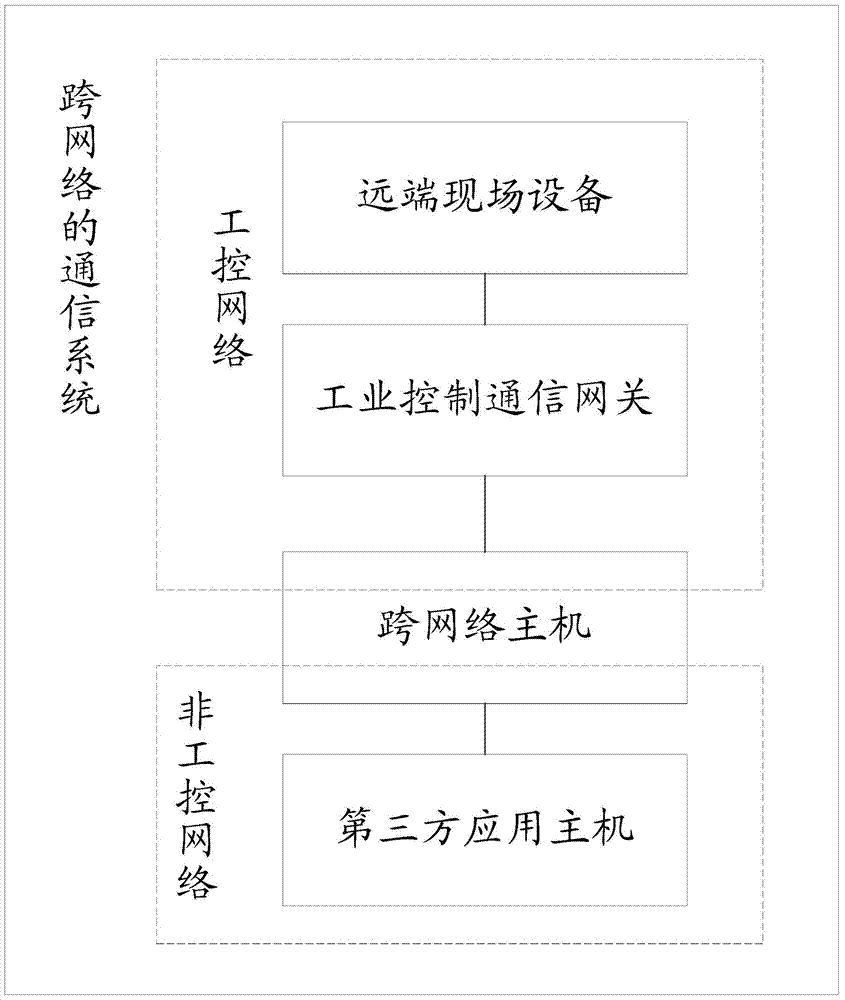
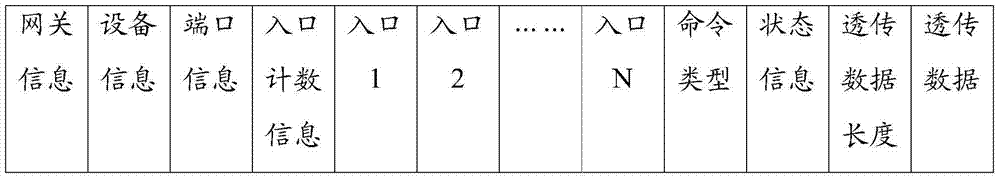
Cross-network communication method and communication system
ActiveCN104754027AAchieve maintenanceLow costData switching networksTransmission protocolNetwork conditions
The invention discloses a cross-network communication method and a communication system. Data transmission process between a far-end field device and a third-party application program running on a third-party application mainframe is achieved, only a conversion unvarnished transmission channel is needed to be established between the third-party application program and the far-end field device, unvarnished transmission type transmitted-data packing and unpacking processing is performed according to an unvarnished transmission protocol, matched specific software or a matched acquisition protocol under specific network development condition is not needed, and if the network environment where the far-end field device is located changes, only the unvarnished transmission channel is needed to be established between the far-end field device and the cross-network mainframe. A large amount of time and cost is saved, so that the technical problem that the mode that the far-end field device exists in a maintenance industrial control network in the prior art causes high development cost and long development period is solved, the industrial field device networking process of various special protocols is simplified, and a solution is also provided for remote access of the industrial field device.
Owner:BC P INC CHINA NAT PETROLEUM CORP +2
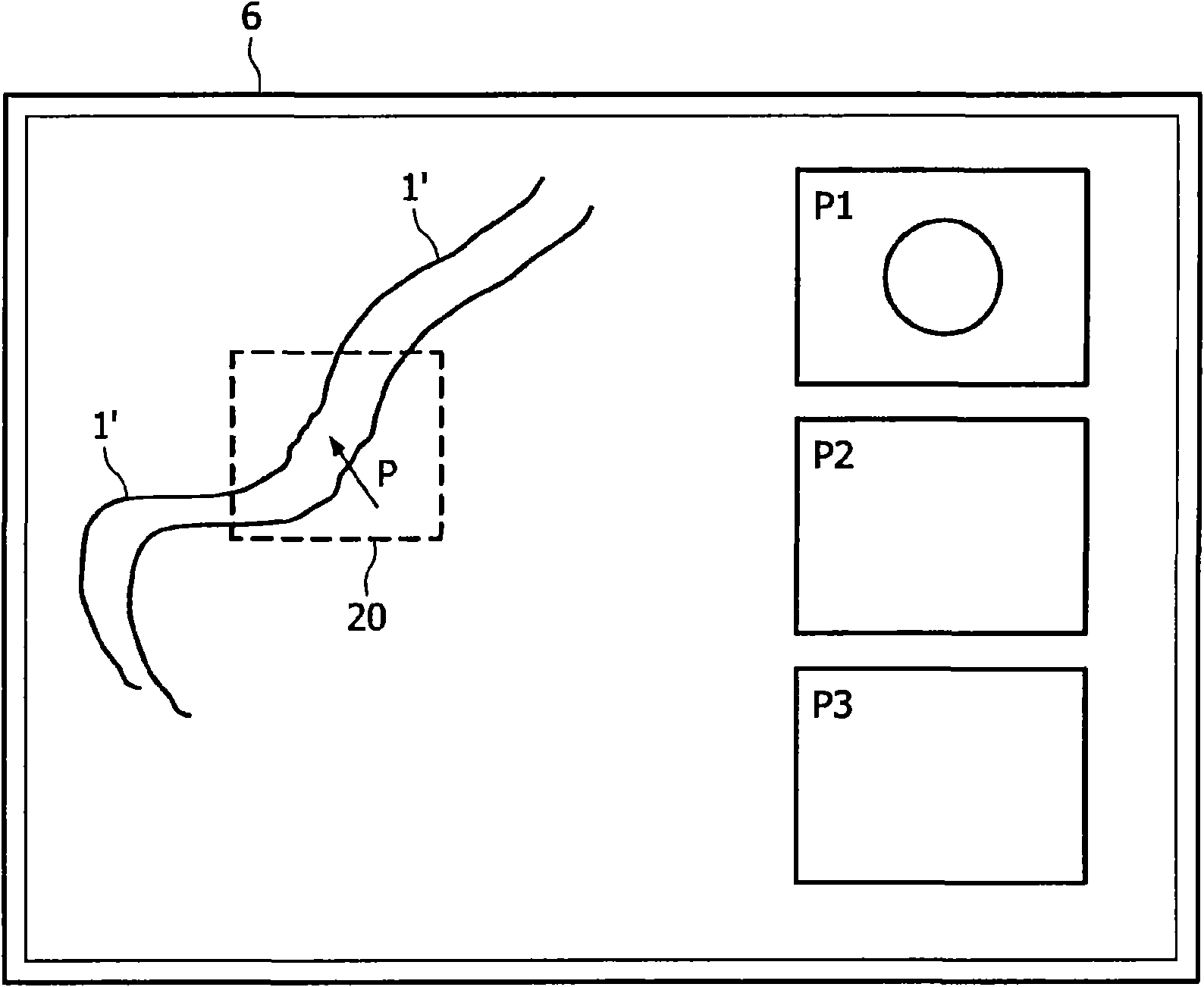
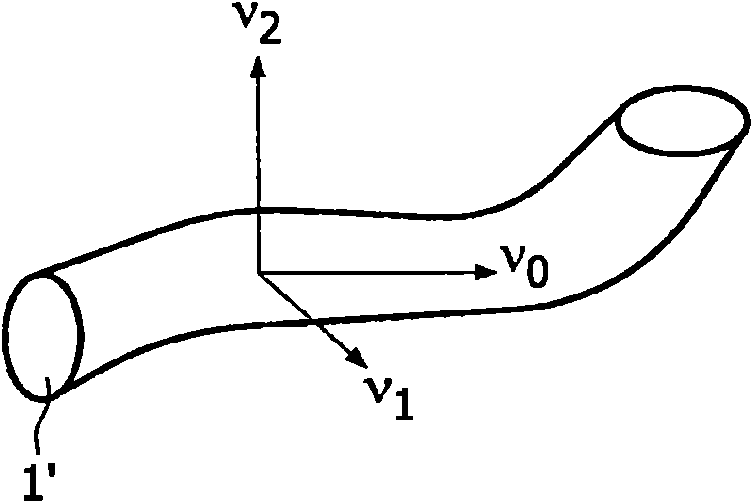
Inspection of tubular-shaped structures
The present invention discloses a method for inspecting tubular-shaped structures (1 ) within a three-dimensional (3D) image data set, e.g. a vessel in a medical image. Initially, there is provided animage data set and performed a visualization of the image data set. Then, an inspection of the image data set is performed. During the inspection the user moves a pointer (P), e.g. via a computer mouse, and a processor performs a local segmentation around the pointer so as to determine a possible shape of a tubular shaped segmented object (1 ), e.g. a vessel, and the processor also makes a localanalysis of the segmented object. Thereafter, a screen displays a view (P1) of the segmented object (1 ), where the orientation of the first view is derived from the local analysis; the first view canfor example be cross-sectional or longitudinal views. The invention may be used directly on the raw image data in a great diversity of visualizations. No advanced application knowledge such as anatomical models, advanced acquisition protocol settings or global segmentation is needed. It is therefore a robust method that can be used over a wide range of image modalities and anatomies, which is essential in a vascular quantification package.
Owner:KONINK PHILIPS ELECTRONICS NV
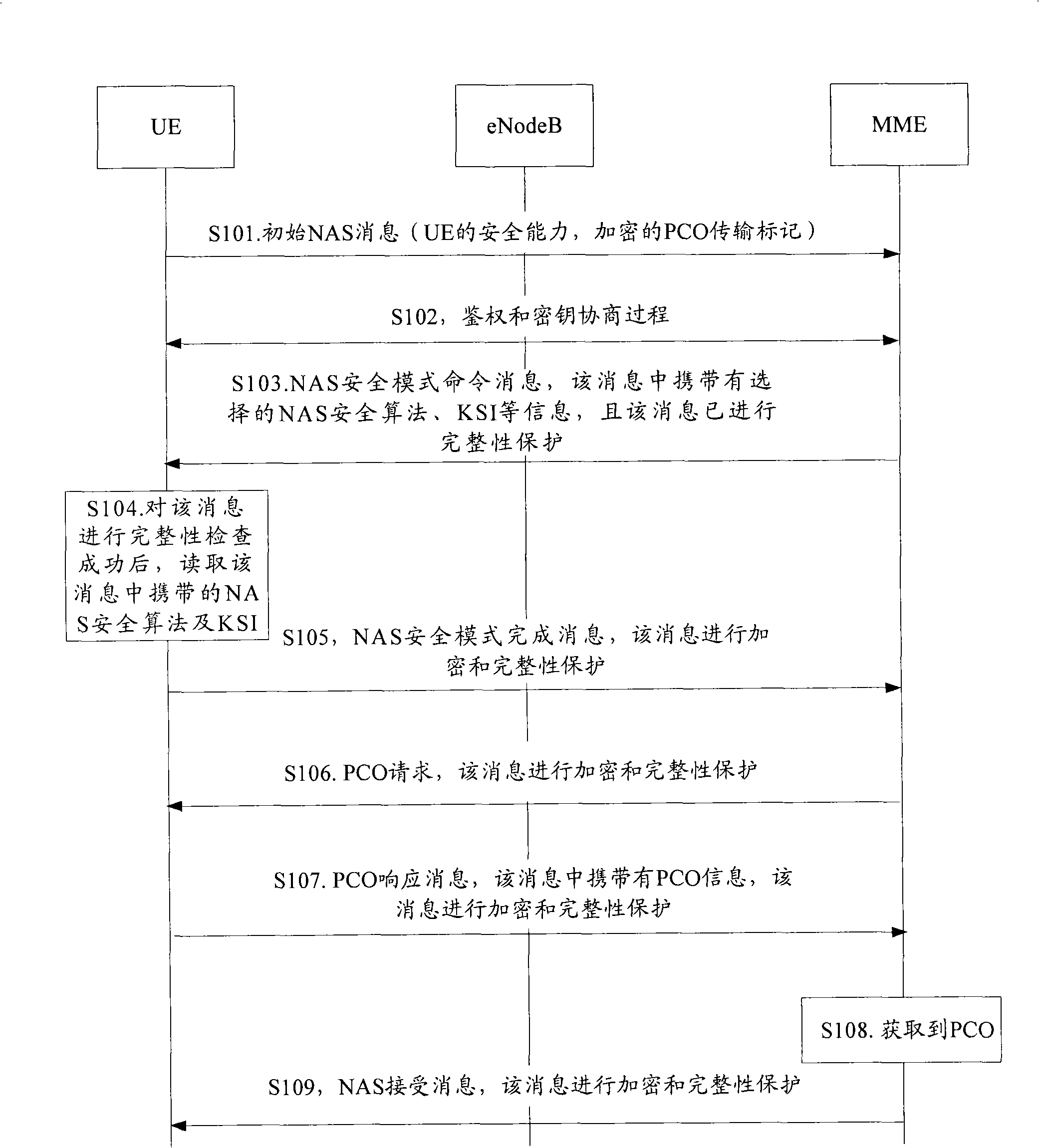
Protocol configuration option transmission method, system and user equipment
InactiveCN101336000AReduce signaling interactionReduce wasteRadio/inductive link selection arrangementsData switching networksNon-access stratumAcquisition Protocol
The invention provides a protocol arrangement option transmitting method, a system and a user terminal, wherein, after the user terminal receives non-access layer security mode command information transmitted by a mobile managing entity, the user terminal transmits non-access layer security mode completion information to the mobile managing entity. The non-access layer security mode completion information is carried with the protocol arrangement option. The mobile managing entity obtains the protocol arrangement option from the non-access layer security mode completion information. According to the technical scheme provided in the invention, signalling alternation between the user terminal and the mobile managing entity is reduced, and waste of network resource is reduced.
Owner:ZTE CORP
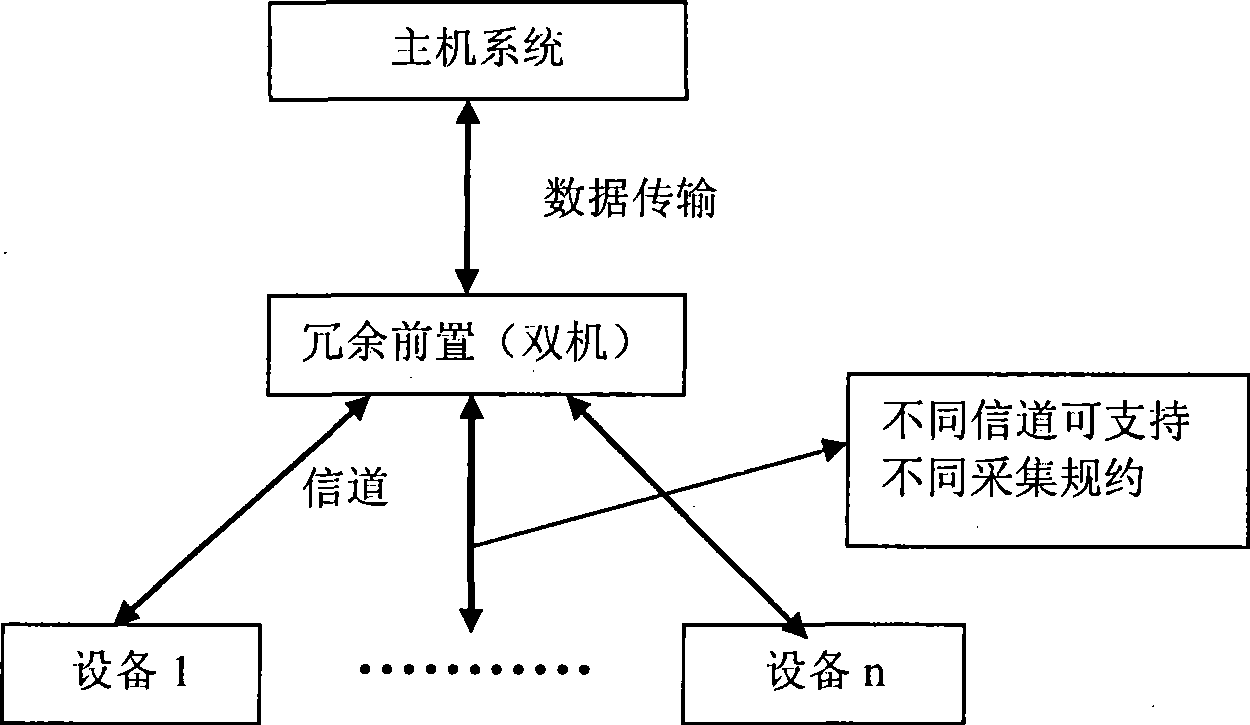
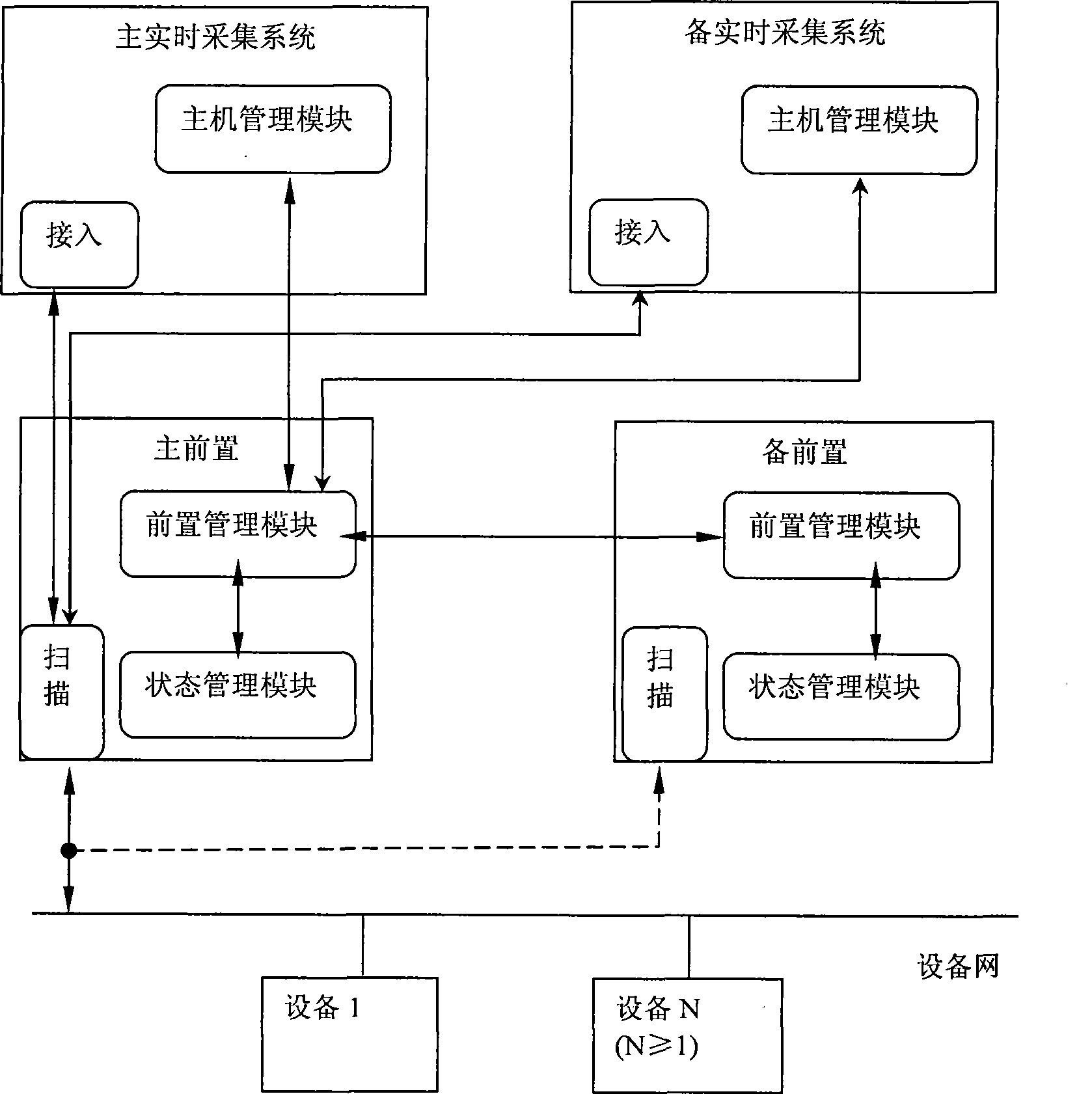
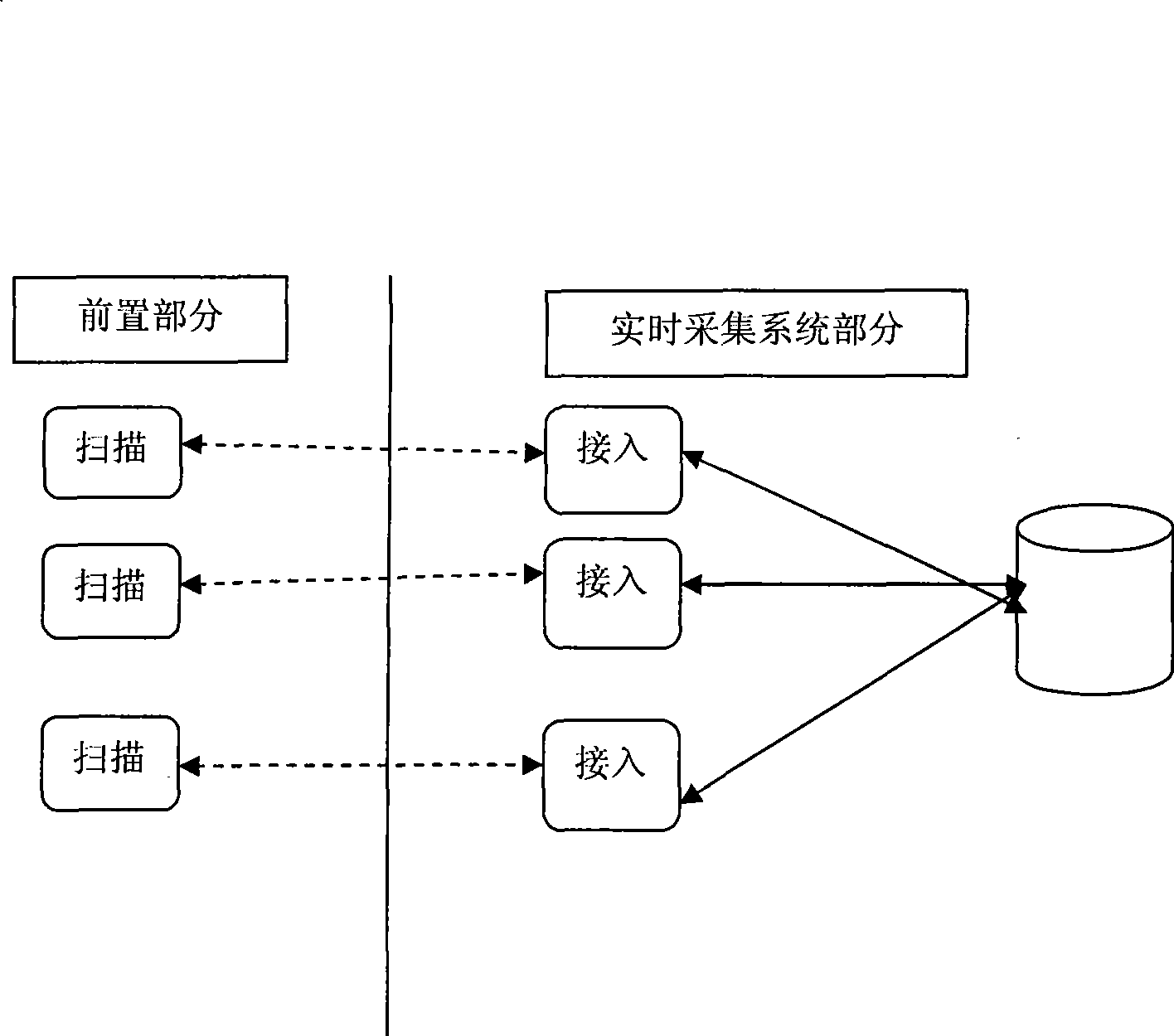
Preposed redundancy structure of collection system with convenient protocol extension, and method thereof
The invention discloses the prepositive redundant architecture of an acquisition system convenient for protocol extension, which is used for realizing the redundant function of a prepositive computer collecting data in a control system, and comprises a host management module, a prepositive management module, and a state management module. The invention also discloses a realizing method for the prepositive redundant architecture of the data acquisition system. The prepositive redundant architecture of the data acquisition system formed by adopting the technical proposal of the invention can lead the data acquisition system to be provided with good expansibility when different types of new acquisition devices are added to the data acquisition system. The system has clear structure, thus effectively realizing the exchange of main and standby route double prepositive computers, when an acquisition protocol is newly added, and independent development can be carried out without influencing the function of other modules and other acquisition protocols in the prepositive redundant architecture and the systematical normal use of data acquisition.
Owner:BEIJING CITY UNIVERSITY
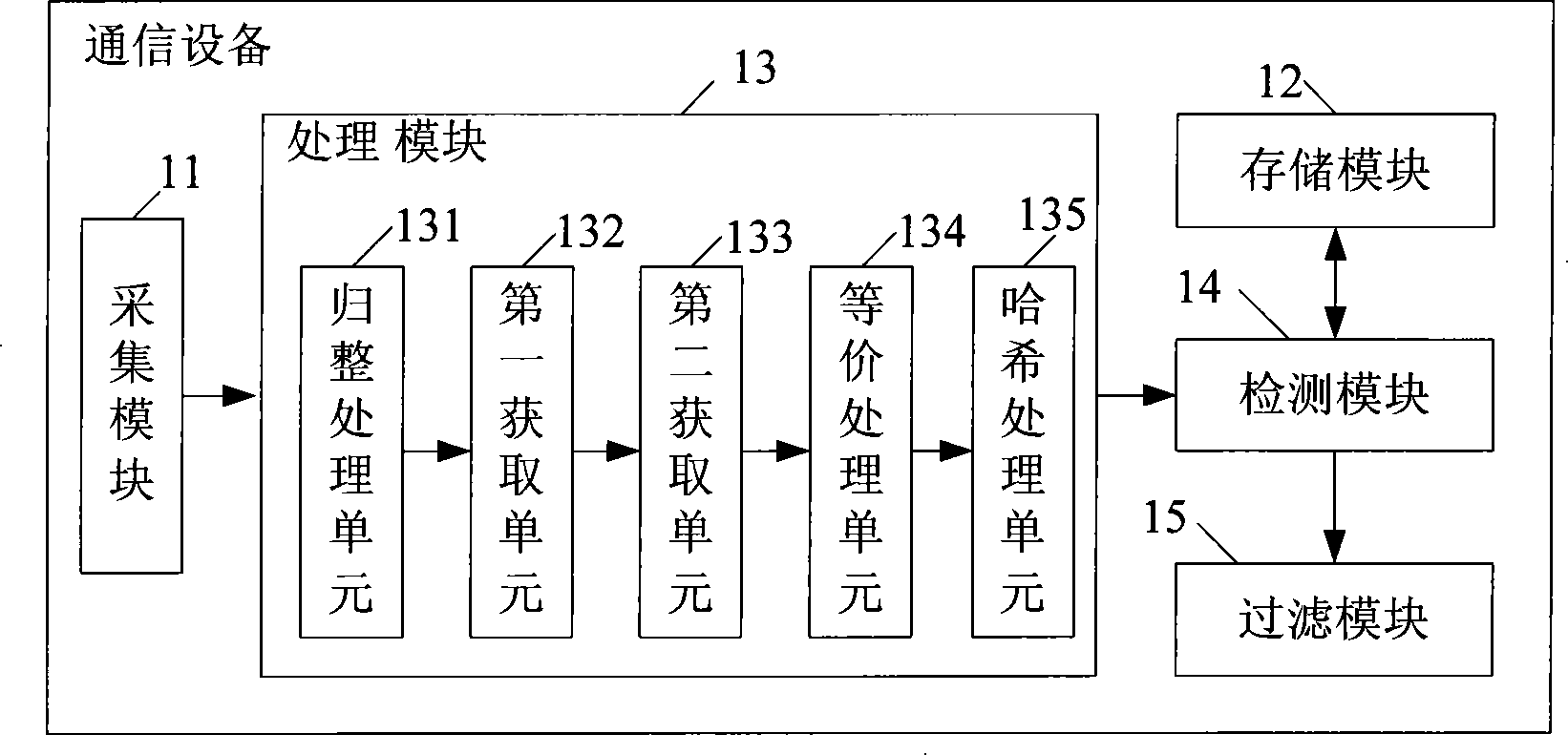
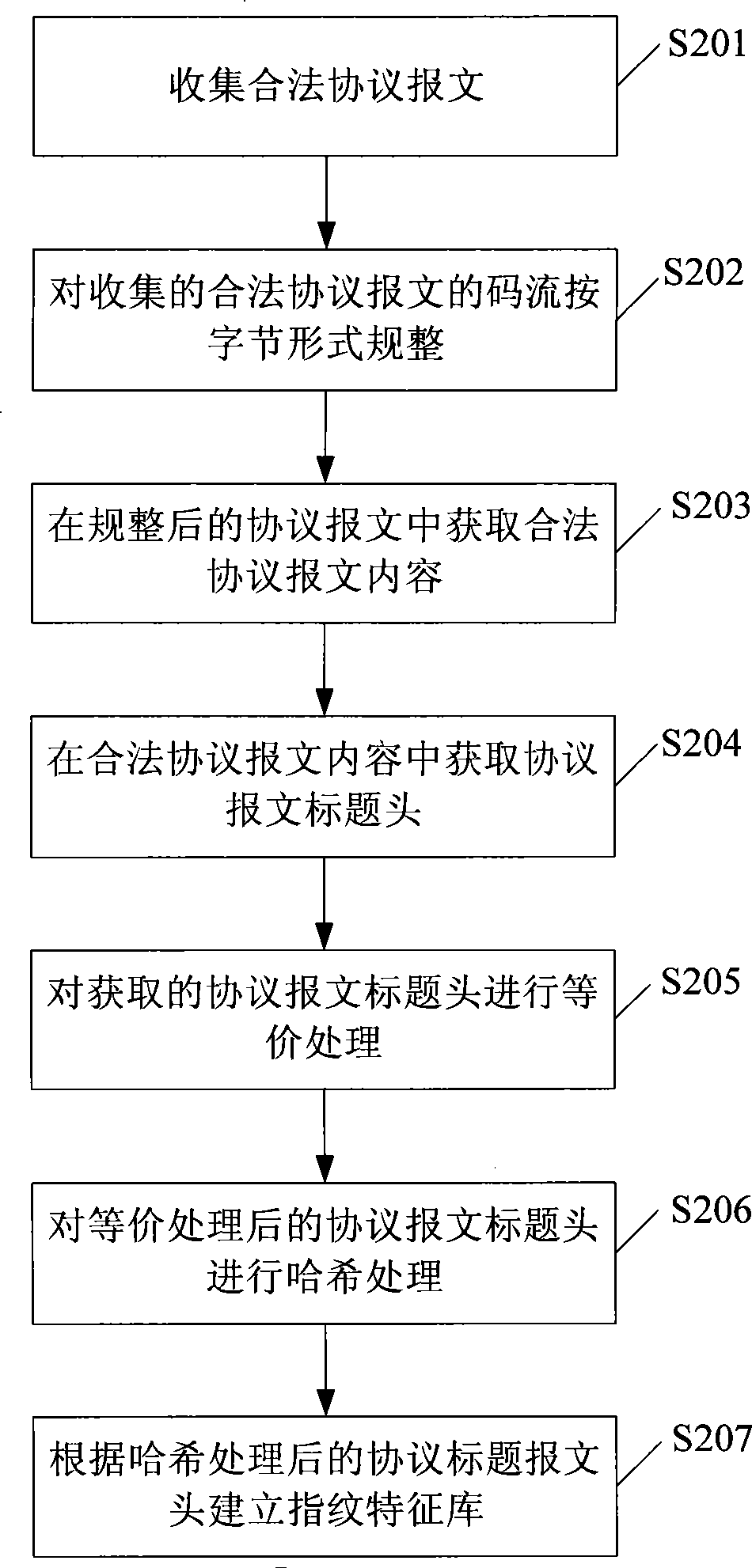
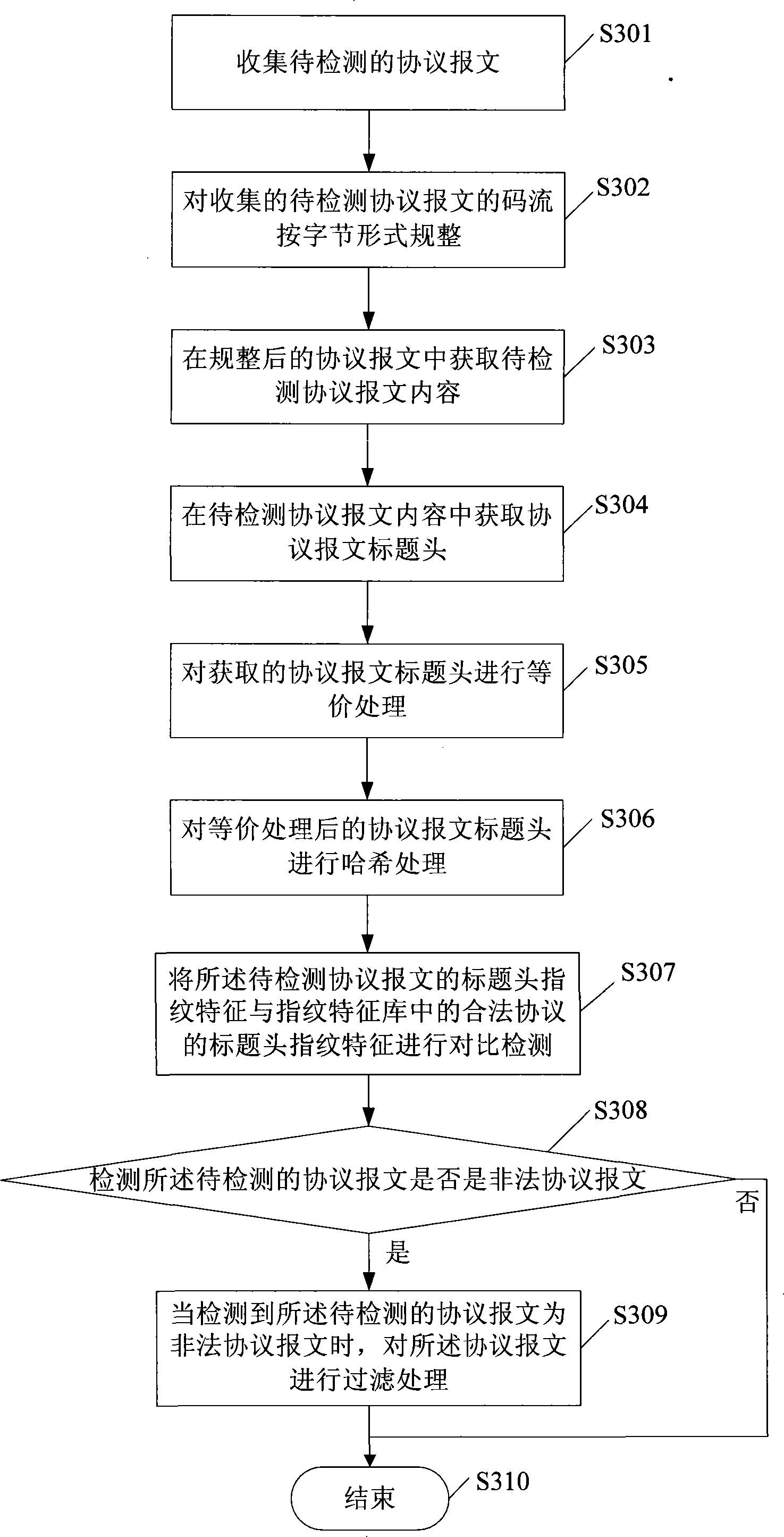
Protocol packet detecting method, system and equipment
InactiveCN101247281AImplement filteringAvoid attackData switching networksSpecial data processing applicationsComputer hardwareCommunication device
The embodiment of the invention discloses a detection method of protocol message, comprising the steps of: collecting the protocol message to be detected; obtaining title head fingerprint characteristic of the protocol message to be detected; comparing and detecting the title head fingerprint characteristic of the protocol message with that stored in a fingerprint library. The embodiment of the invention also discloses a communication equipment and system, by which the fingerprint library is built up for the legal or illegal title head fingerprint characteristic of protocol message, and after the protocol message to be detected is received, rapid comparision and detection can be realized by obtaining the title head fingerprint characteristic of the protocol message, thereby preventing the illegal protocol message which distorts the title head from attacking and cheating the VOIP system in order to filter the illegal message.
Owner:HUAWEI TECH CO LTD
Device and method for automatic data acquisition and/or detection
Methods and system for providing diabetes management including tomatic time acquisition protocol and expiration date detection are provided.
Owner:ABBOTT DIABETES CARE INC
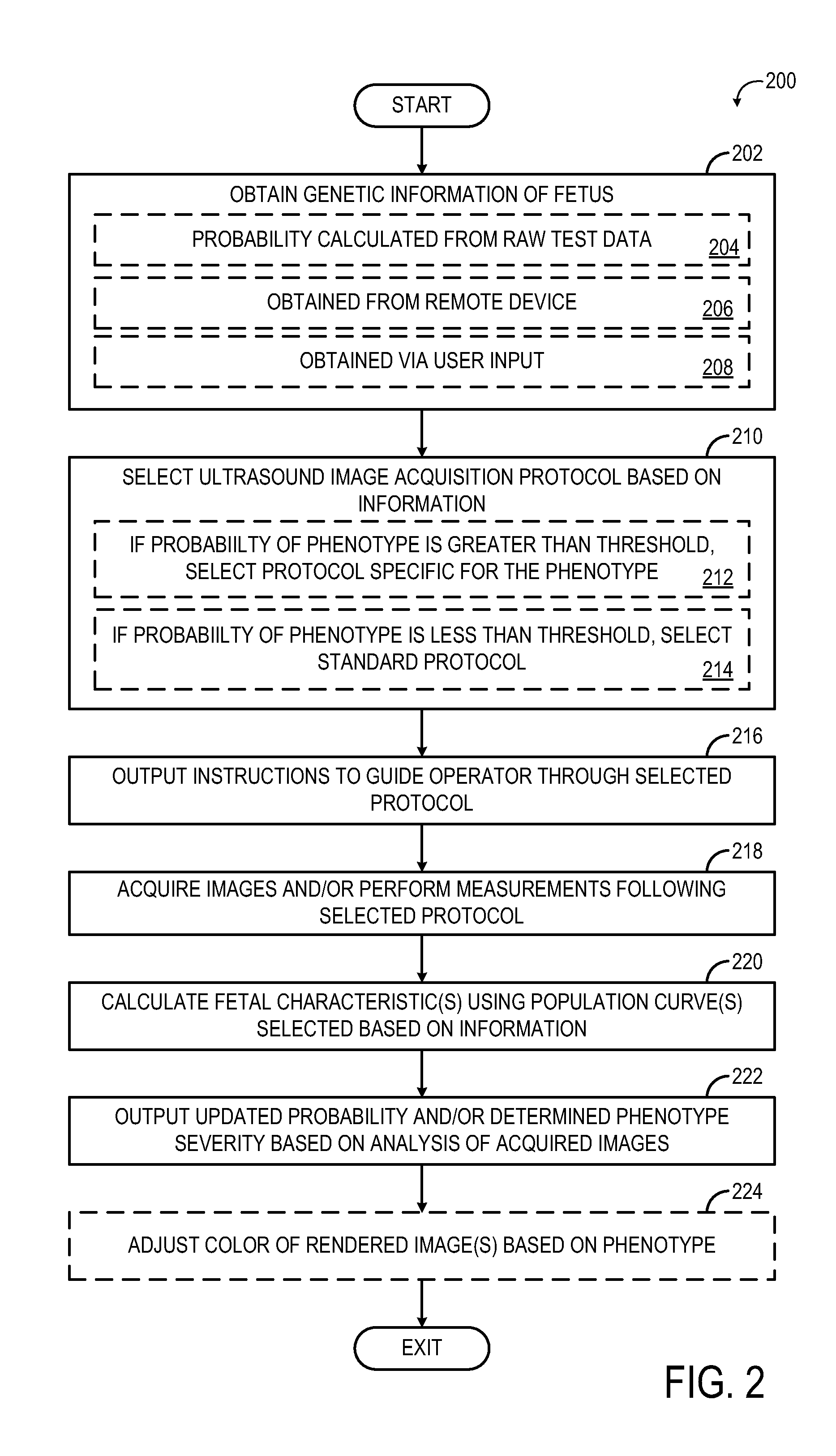
Method and systems for adjusting an imaging protocol
InactiveUS20160000401A1Health-index calculationOrgan movement/changes detectionComputer visionComputer science
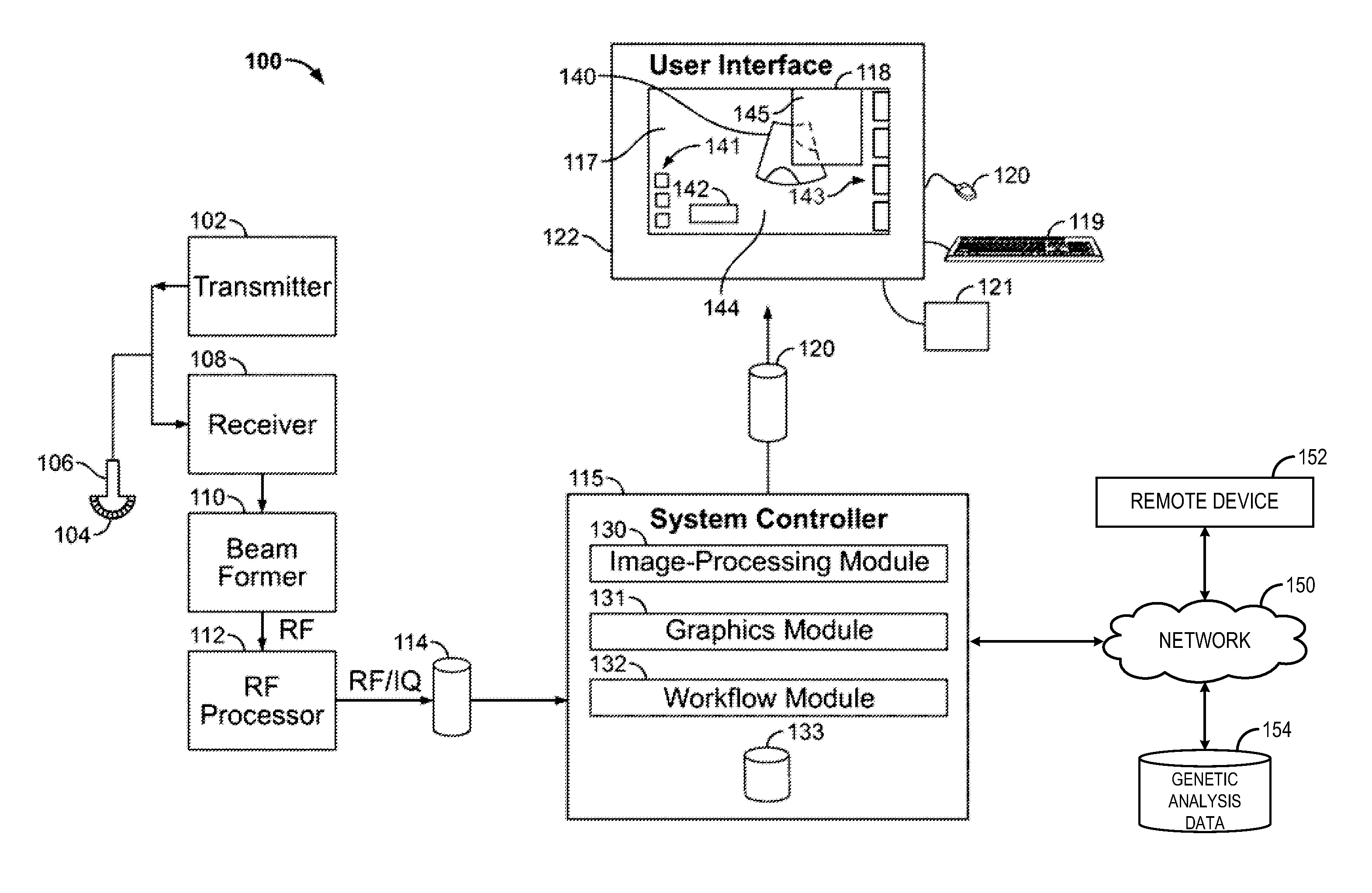
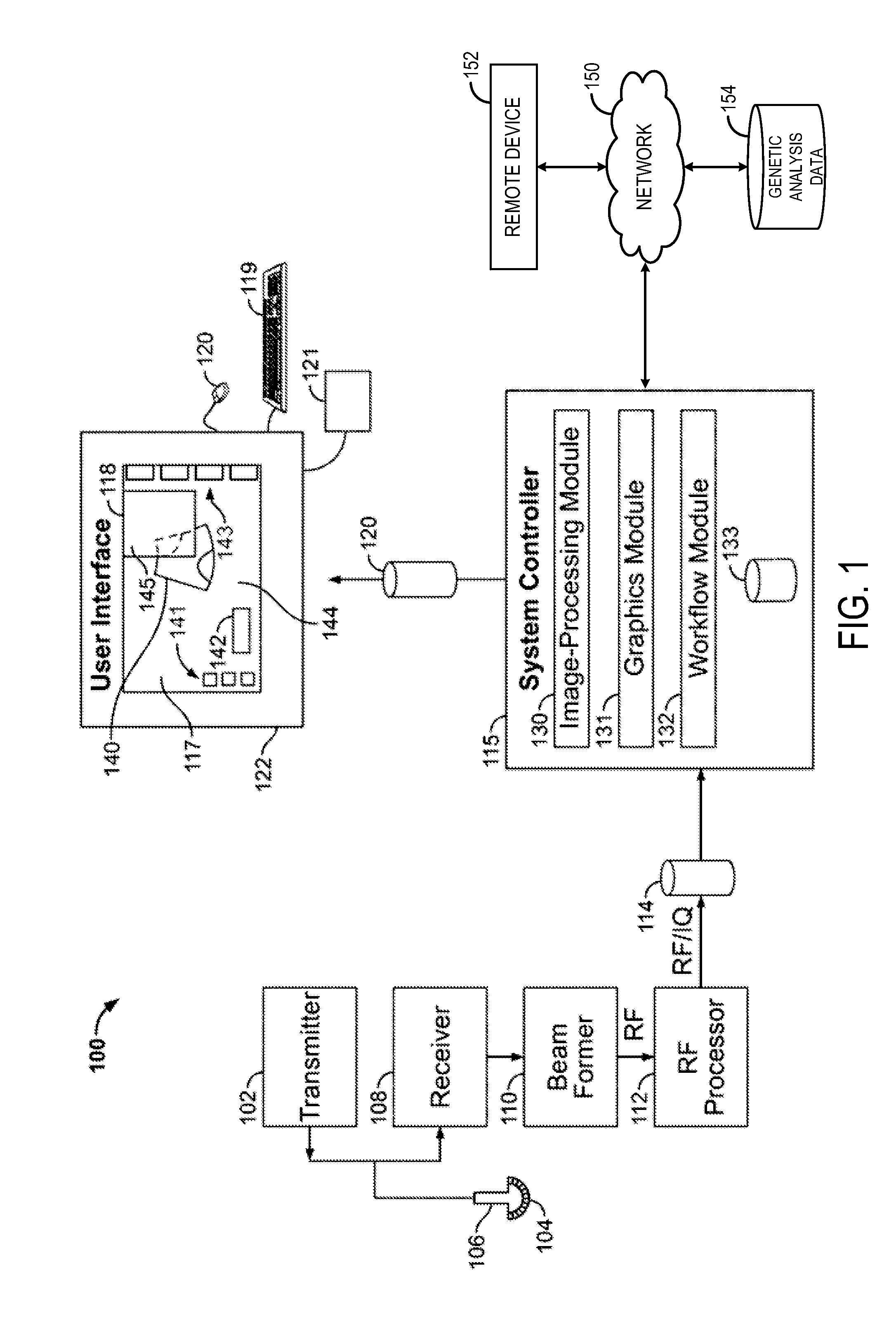
Various methods and systems are provided for imaging a fetus. One example method for imaging a fetus includes obtaining genetic analysis information of the fetus, and adjusting an ultrasound image acquisition protocol based on the information.
Owner:GENERAL ELECTRIC CO
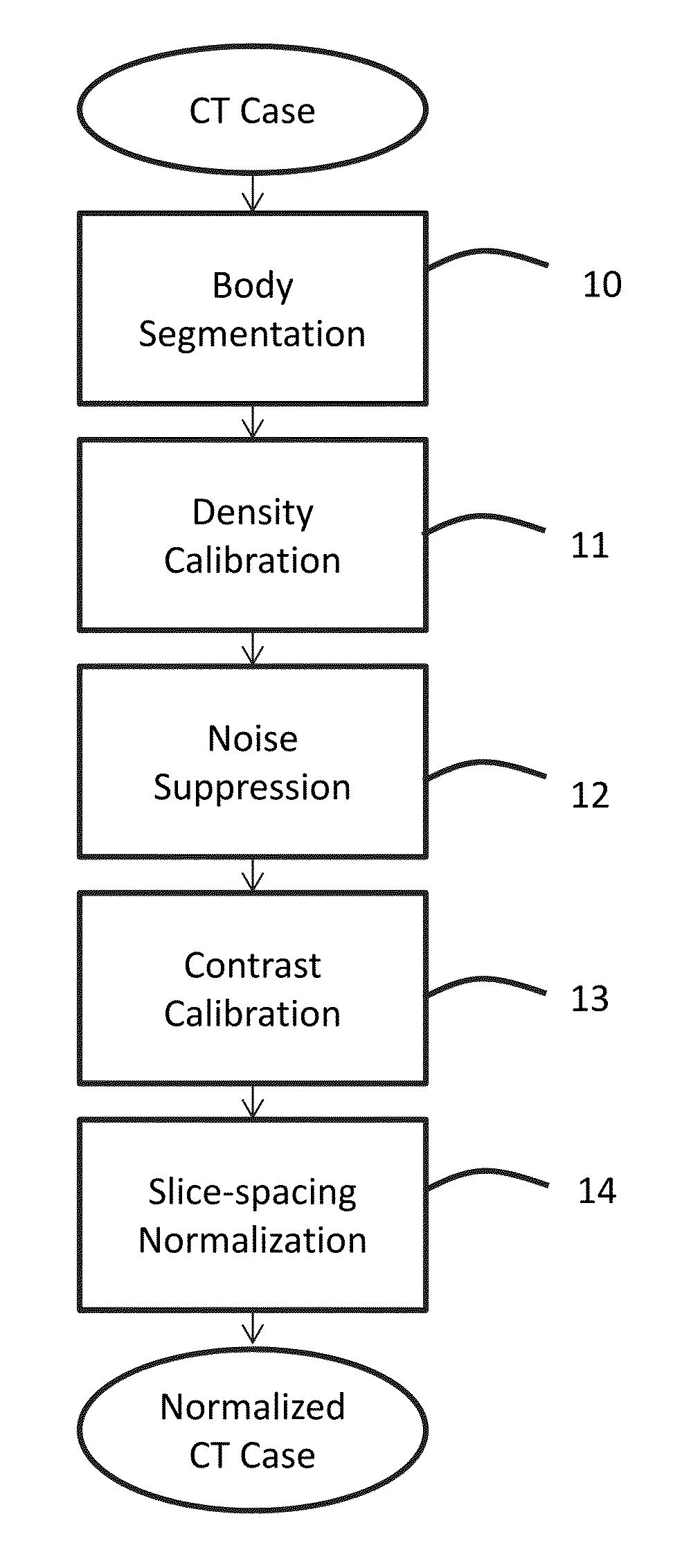
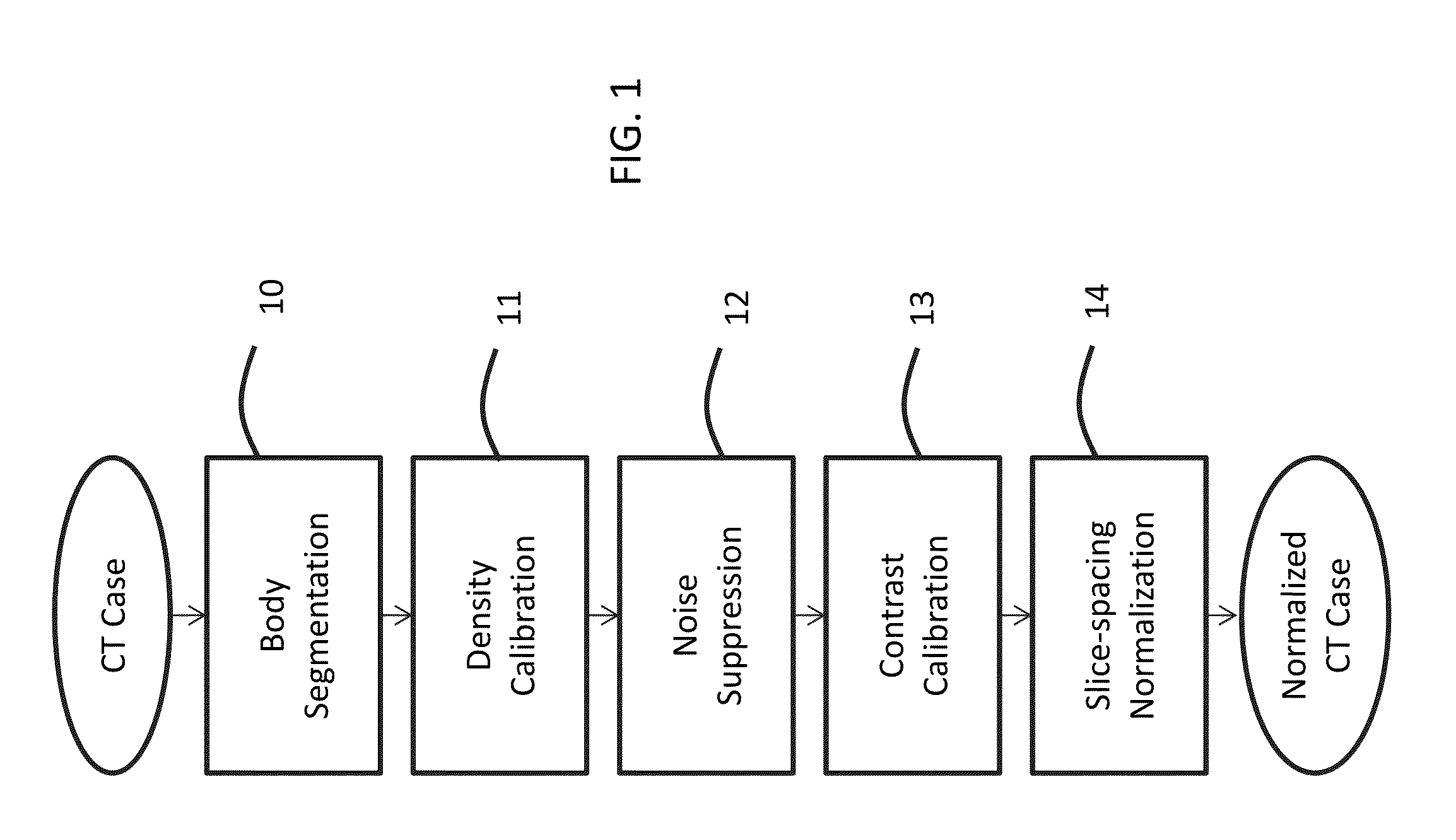
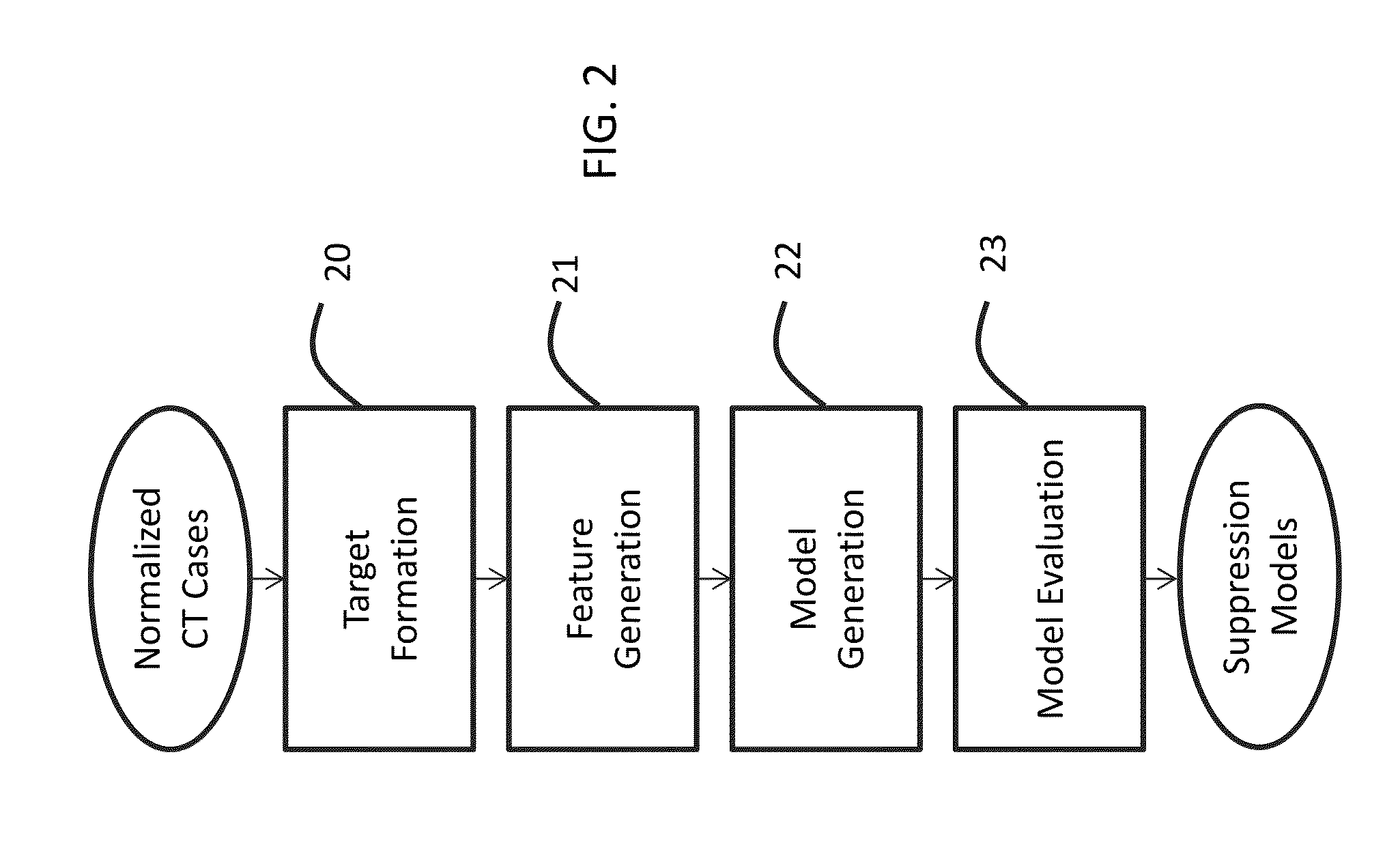
Suppression of vascular structures in images
ActiveUS20150279034A1Easy to detectSuppressing selected non-nodule structuresImage enhancementReconstruction from projectionAnatomical structuresVoxel
Image processing techniques may include a methodology for normalizing medical image and / or voxel data captured under different acquisition protocols and a methodology for suppressing selected anatomical structures from medical image and / or voxel data, which may result in improved detection and / or improved rendering of other anatomical structures. The technology presented here may be used, e.g., for improved nodule detection within computed tomography (CT) scans. While presented here in the context of nodules within the lungs, these techniques may be applicable in other contexts with little modification, for example, the detection of masses and / or microcalcifications in full field mammography or breast tomosynthesis based on the suppression of glandular structures, parenchymal and vascular structures in the breast.
Owner:RIVERAIN TECH
Computed tomography method and system
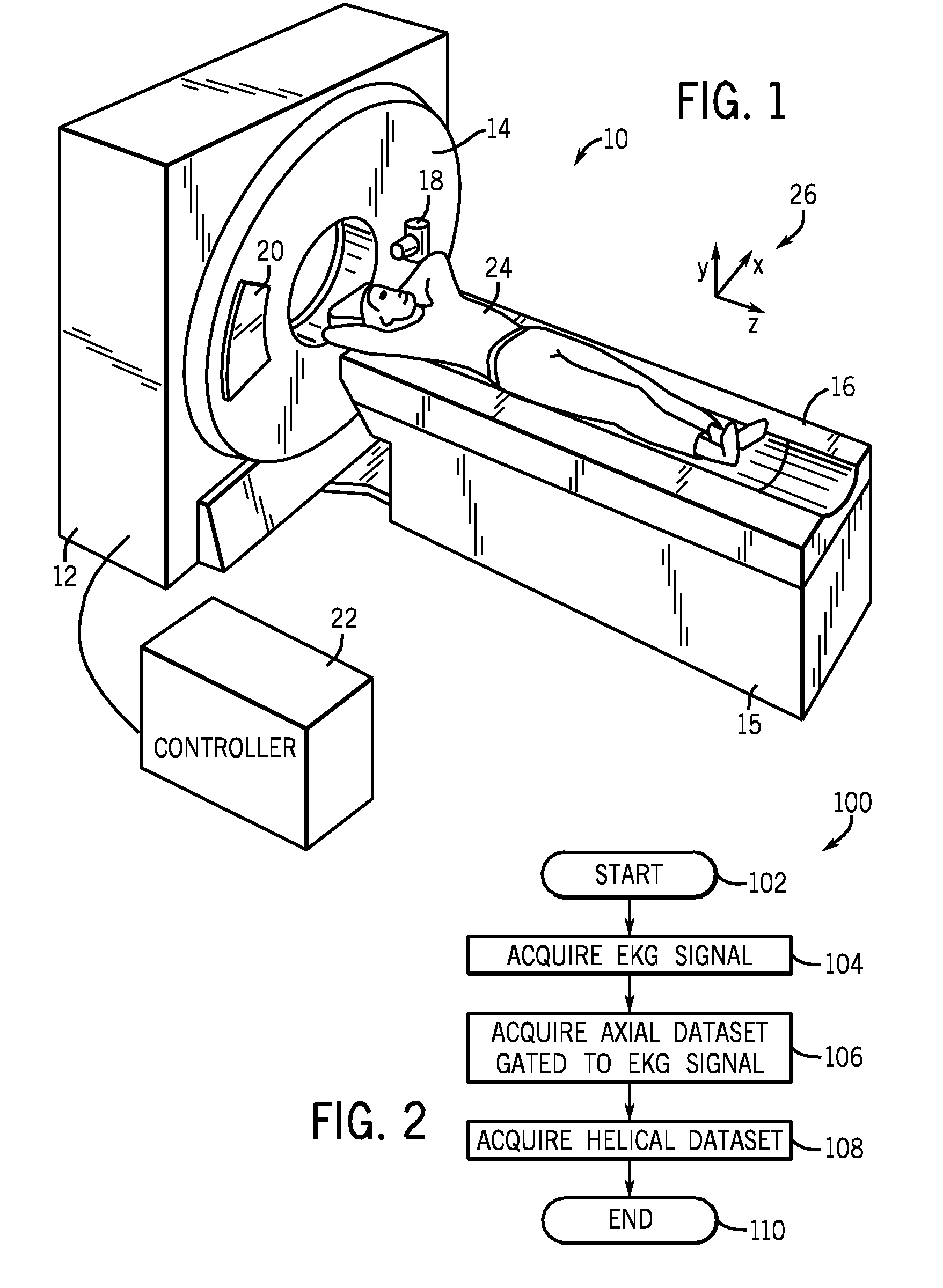
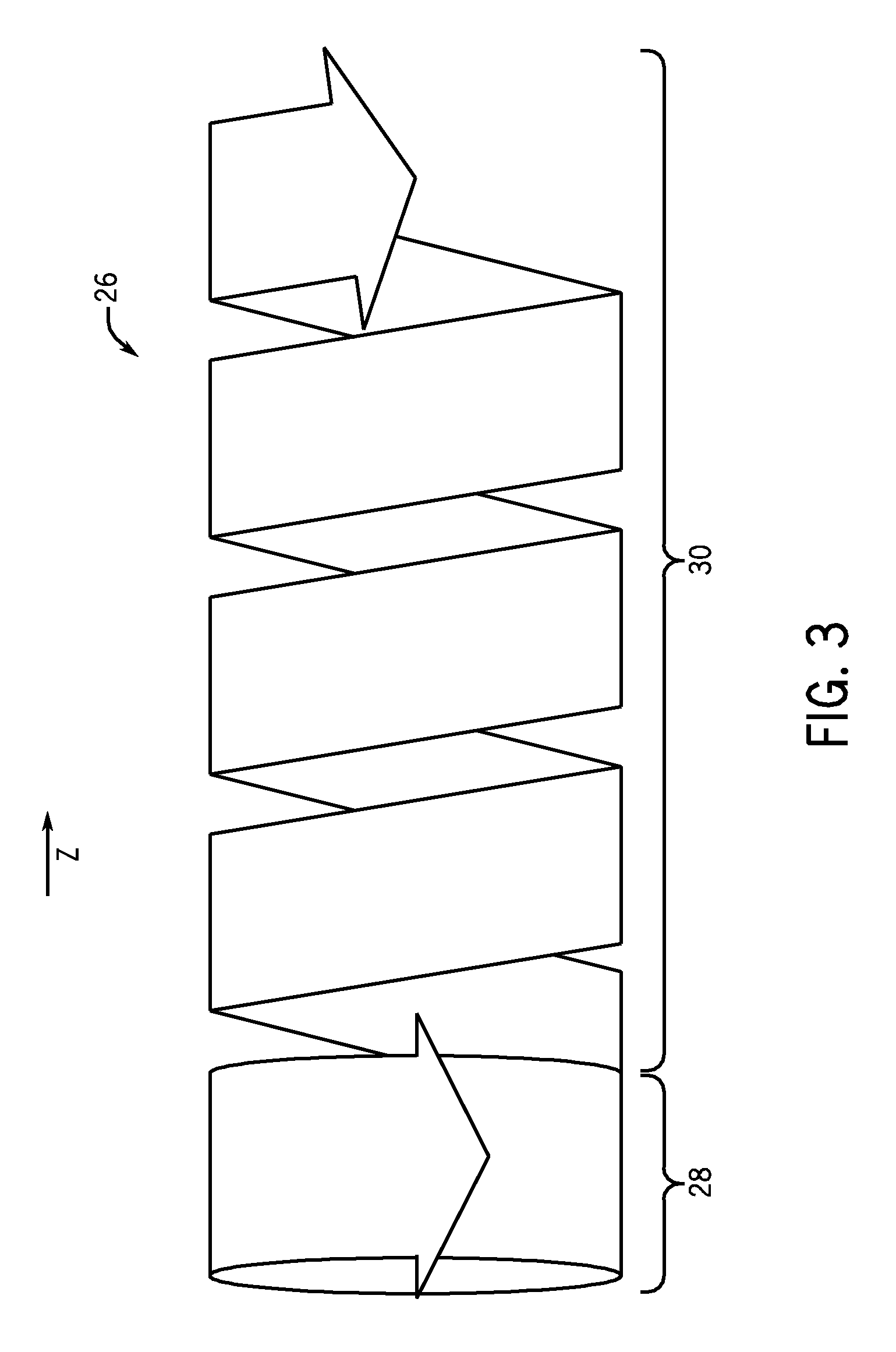
ActiveUS20100128838A1Reconstruction from projectionMaterial analysis using wave/particle radiationComputed tomographyTomography
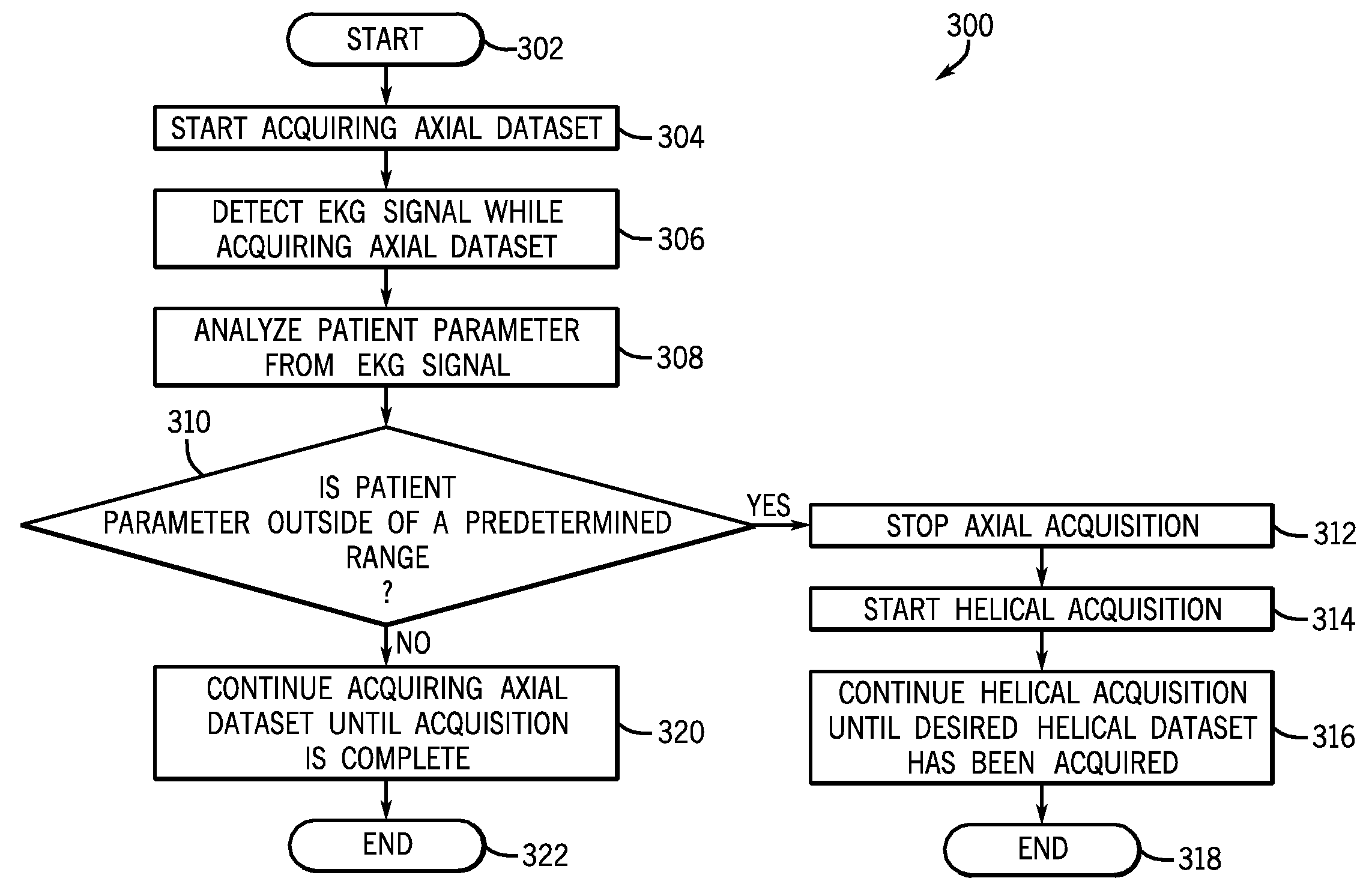
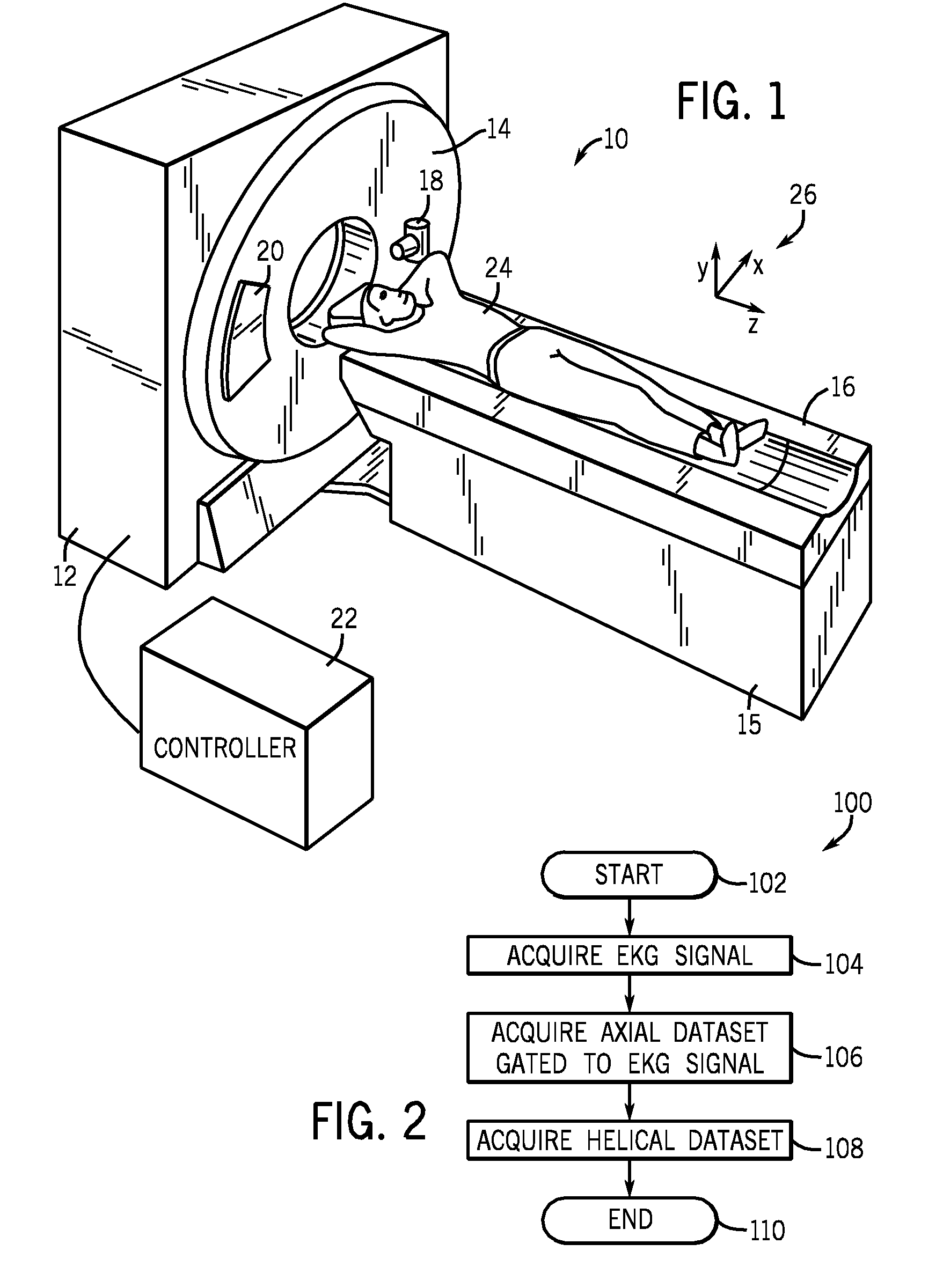
An method of computed tomography is disclosed herein. The method includes acquiring an axial dataset and acquiring a helical dataset as part of an acquisition protocol. A computed tomography system is also disclosed.
Owner:GENERAL ELECTRIC CO
Method for improving network application security and the system thereof
ActiveUS20110119750A1Improve network securityComputer security arrangementsMultiple digital computer combinationsApplication serverUser input
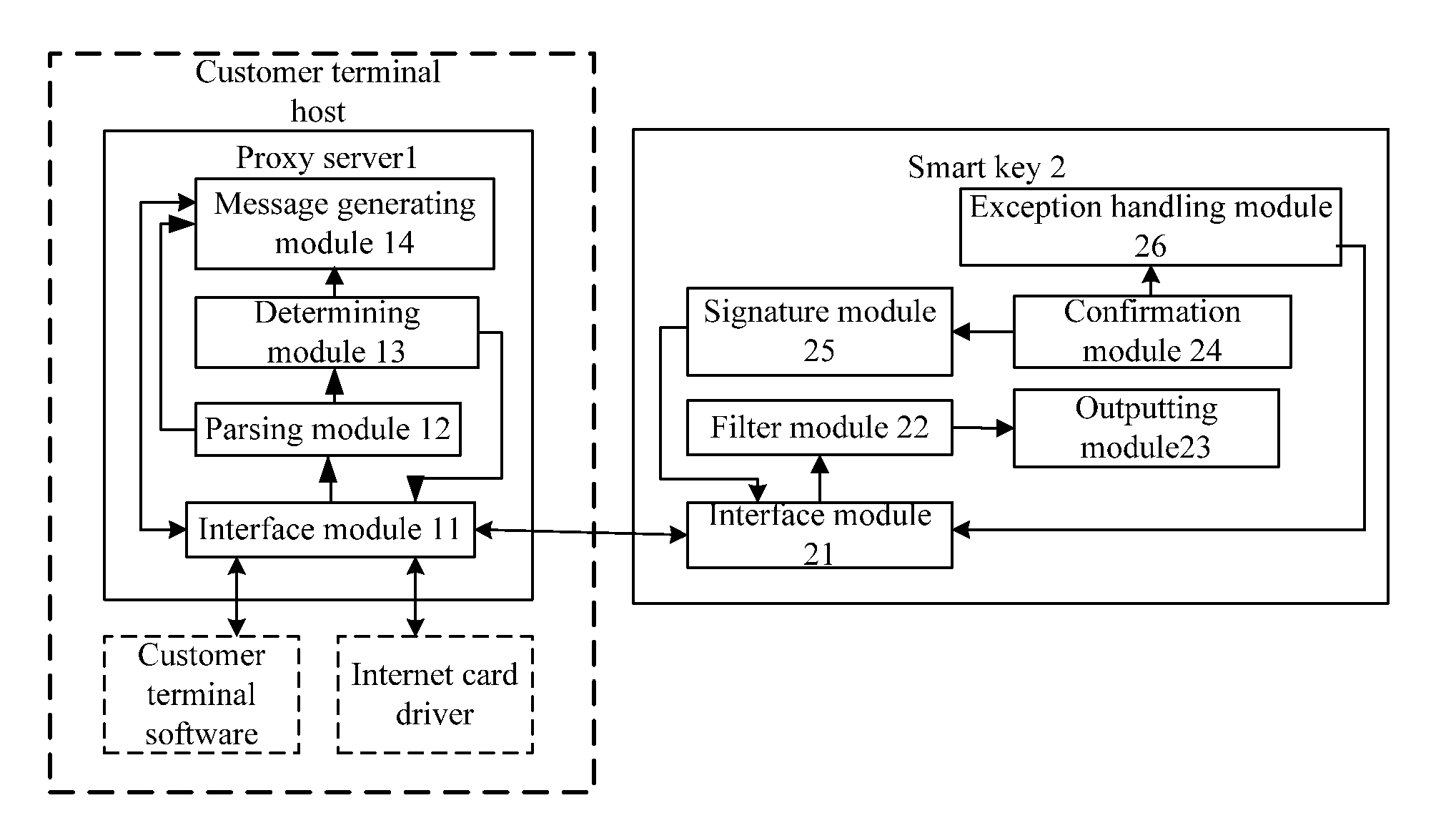
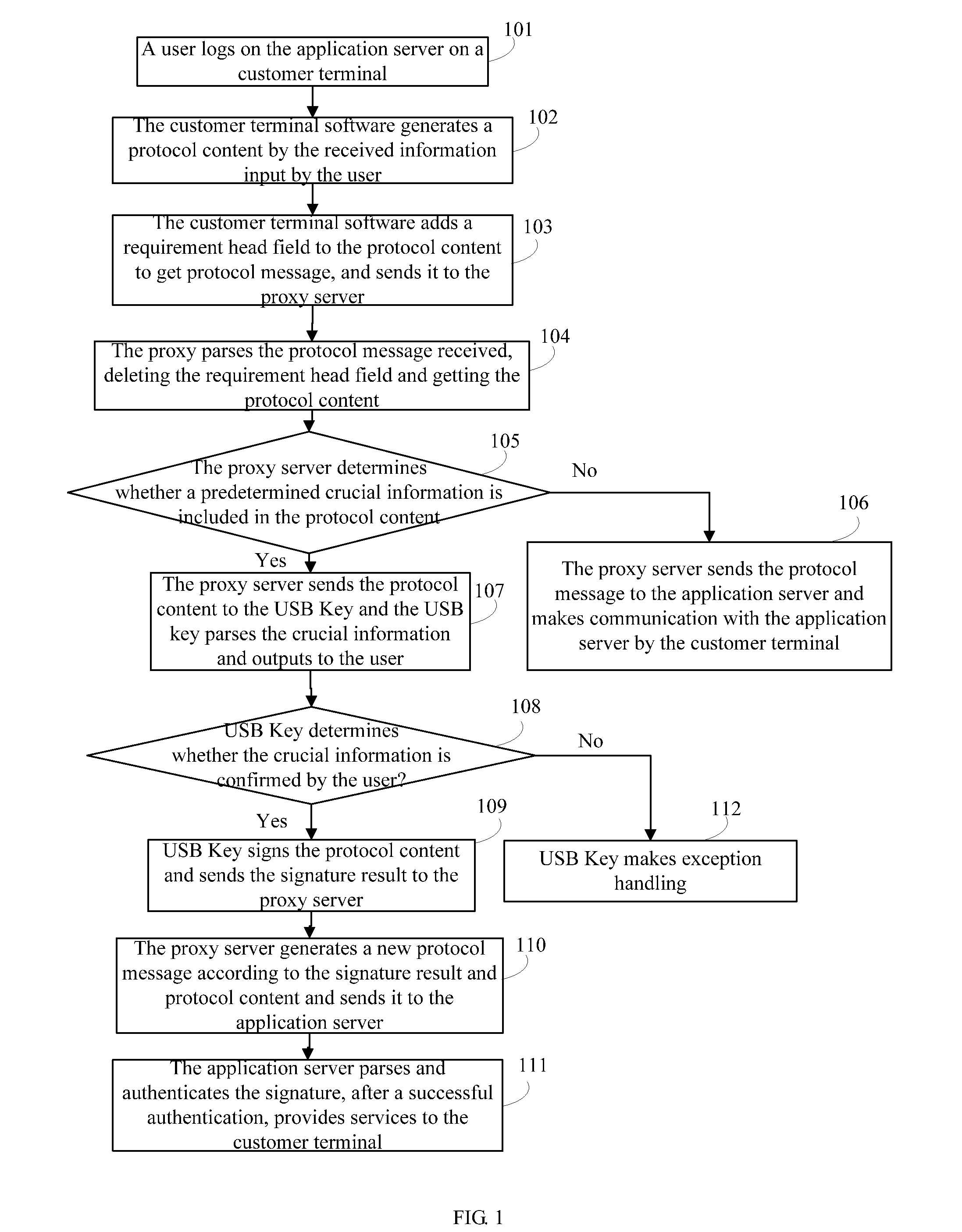
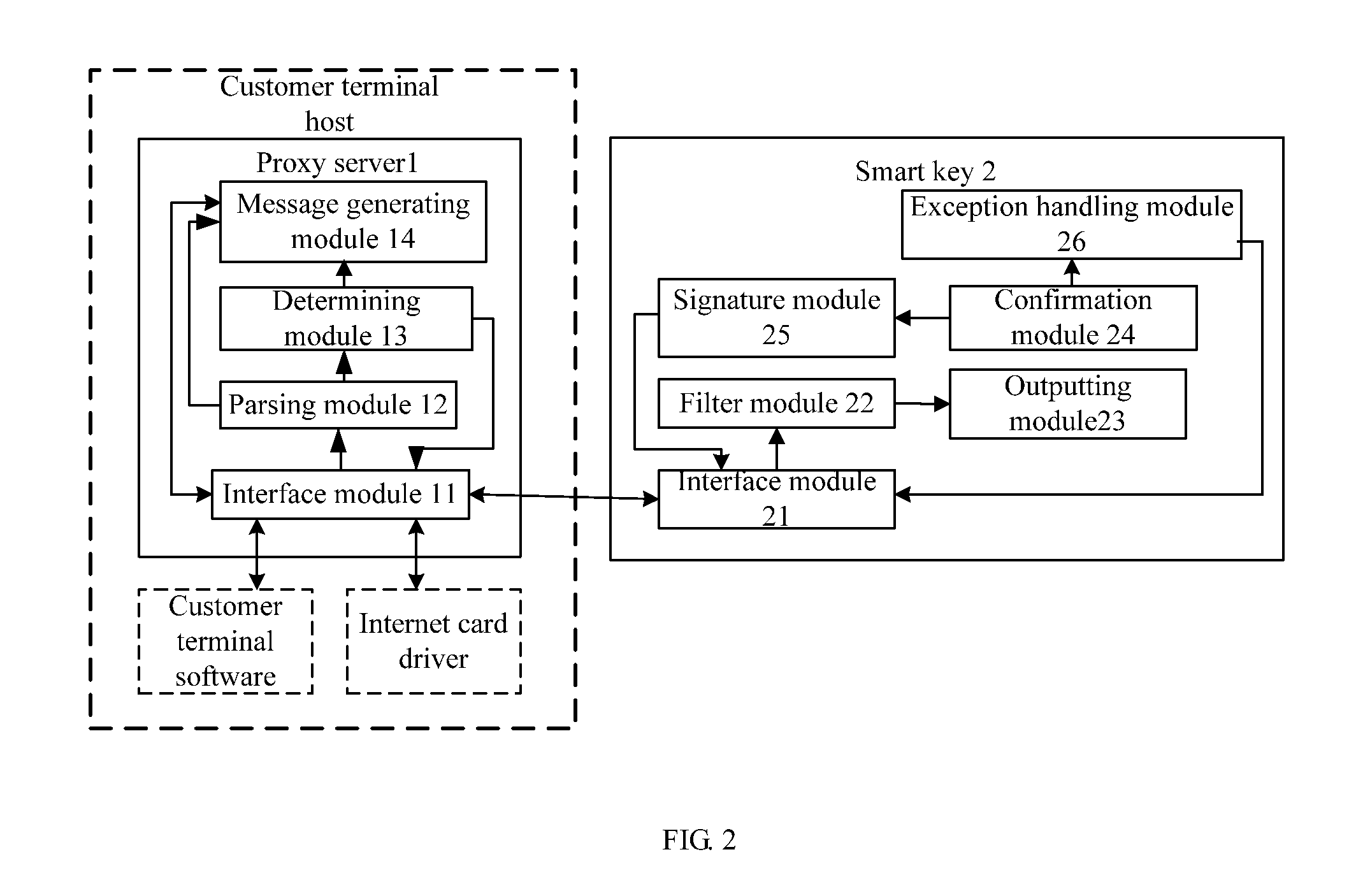
A method for improving network application security and the system thereof are disclosed in the invention, relating to the field of information security. The method includes: a proxy server in a customer terminal host receives a protocol message, generated and sent by the customer terminal software according to the information input by a user, and obtains the protocol content after parsing the protocol message, and determines whether critical information is included in the protocol content, if it is, the server sends the protocol content to the smart key device; and the smart key device obtains the critical information by parsing it and sends it to the user, and after a confirmation information is gotten from the user, the smart key device signs the protocol content and sends the signature result to the server; and then the server generates a new protocol message to an application server according to the signature result and the protocol content; after an error confirmation or no confirmation is received within a predetermined time period by the user, the smart key device performs the exception handling. The system includes a smart key device and a proxy server in the customer terminal host. The invention improves network application security on the premise of no change to the customer terminal, and it is usable and compatible.
Owner:FEITIAN TECHNOLOGIES
Dot product protocol-based protocol security quantizing method and system
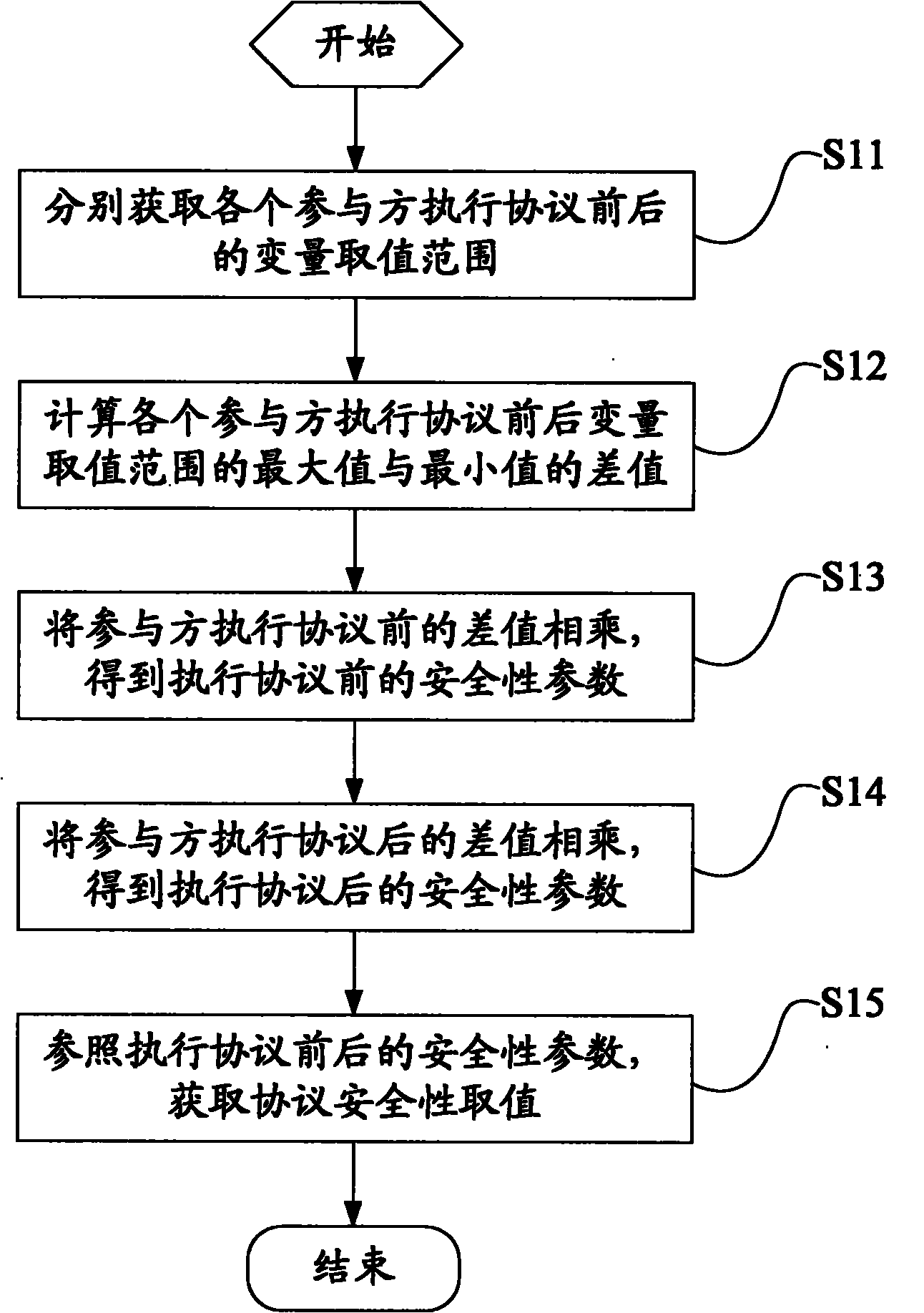
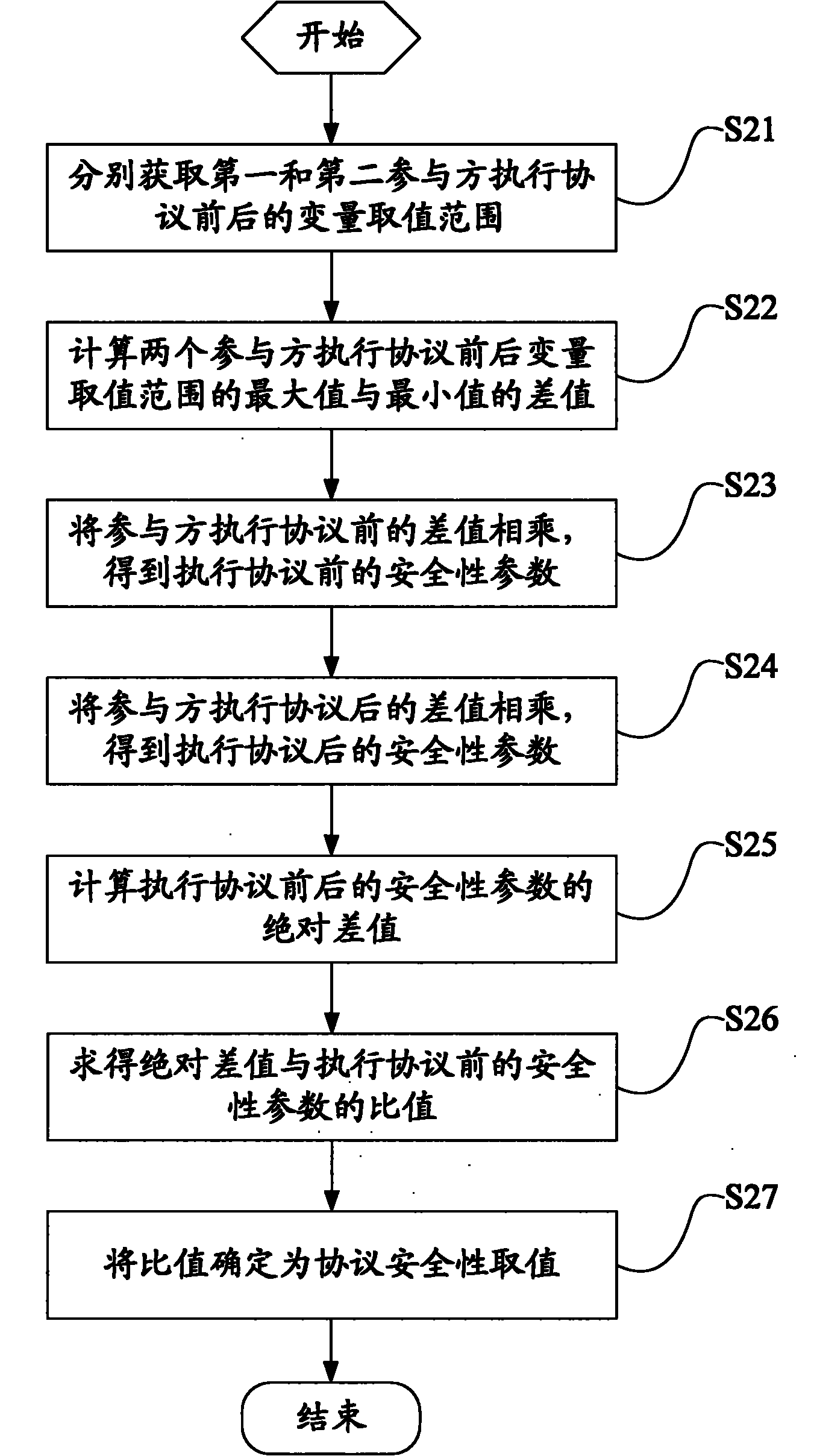
The invention discloses a dot method product protocol-based protocol security quantizing method and a dot product protocol-based protocol security quantizing system. The method comprises the following steps of: acquiring the variable value ranges before and after protocol execution of all parties respectively; computing the differences between the maximal values and the minimal values of the variable value ranges before and after the protocol execution of all the parties respectively; multiplexing the differences before the protocol execution of all the parties to obtain security parameters before the protocol execution; multiplexing the differences after the protocol execution of all the parties to obtain the security parameters after the protocol execution; and acquiring a protocol security value according the security parameters before and after the protocol execution. The method of the invention realizes the aim of quantizing the protocol security by processing the variable value ranges of all the parties before and after the protocol execution and using the processing results as representative values of the protocol security. The method and the system can quantify the security of different protocols, are favorable for selecting the protocol of which the security meets actual demands according to actual application conditions and improve the service efficiency of secure multi-party computation.
Owner:ANHUI NORMAL UNIV
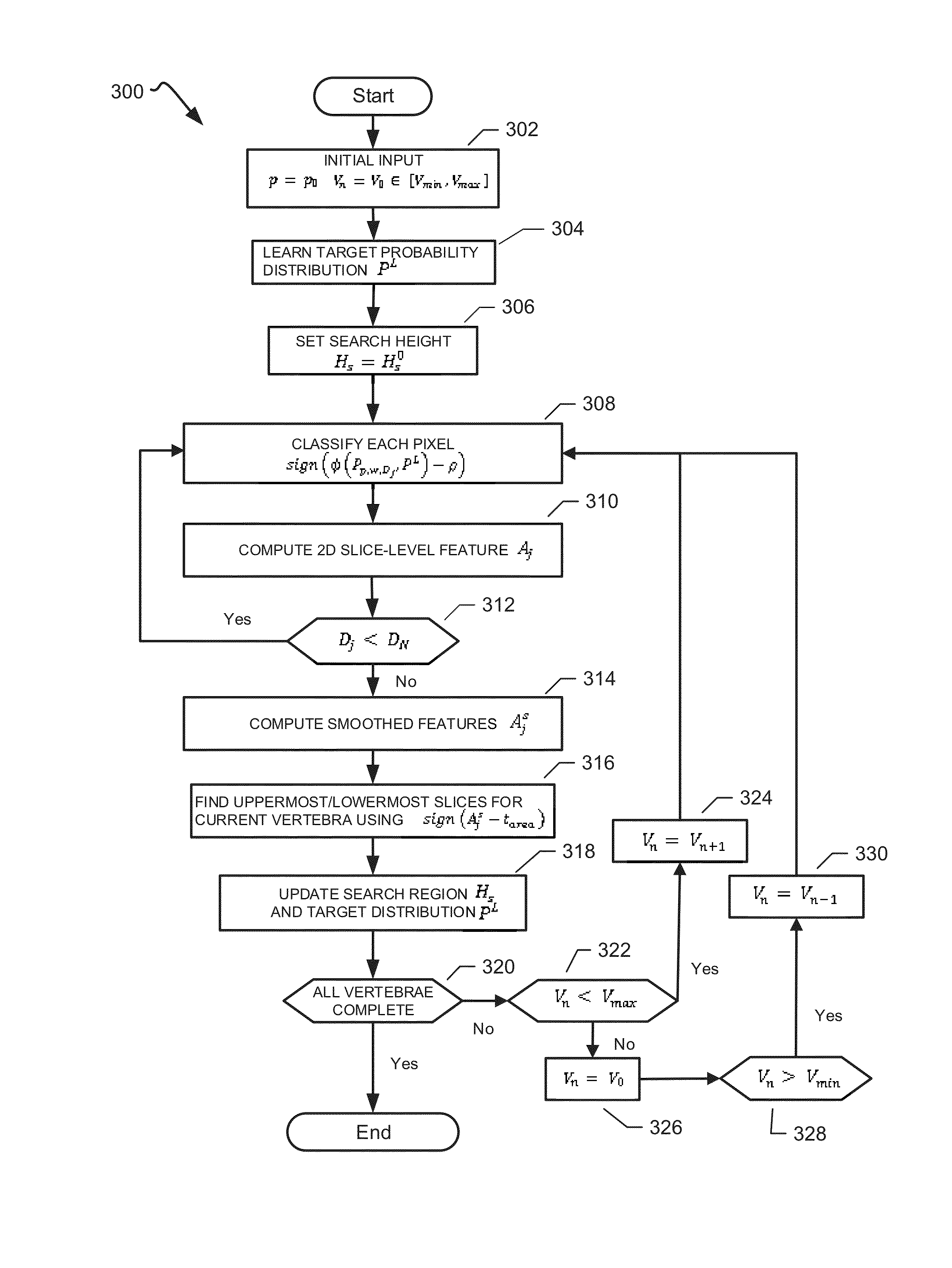
Standalone annotations of axial-view spine images
Systems, methods and computer program products to annotate axial-view spine images with the desired characteristics of not requiring additional views of the spine or cross-referencing features are provided. In one aspect, the disclosed method does not require external training from a manually-labeled data set while being applicable to different imaging modalities and acquisition protocols. In one aspect, the disclosed method achieves near real-time results using integral kernels when implemented on a Graphics Processing Unit.
Owner:LONDON HEALTH SCI CENT RES +1
Method and system for reduced dose x-ray imaging
ActiveUS20130003914A1High currentDose lessMaterial analysis using wave/particle radiationRadiation/particle handlingReduced doseX-ray
Approaches for acquiring CT image data corresponding to a full scan, but at a reduced dose are disclosed. In one implementation, X-ray tube current modulation is employed to reduce the effective dose. In other implementations, acquisition of sparse views, z-collimation, and two-rotation acquisition protocols may be employed to achieve a reduced dose relative to a full-scan acquisition protocol.
Owner:GENERAL ELECTRIC CO
Computed tomography method and system
ActiveUS7831011B2Reconstruction from projectionMaterial analysis using wave/particle radiationComputed tomographyTomography
An method of computed tomography is disclosed herein. The method includes acquiring an axial dataset and acquiring a helical dataset as part of an acquisition protocol. A computed tomography system is also disclosed.
Owner:GENERAL ELECTRIC CO
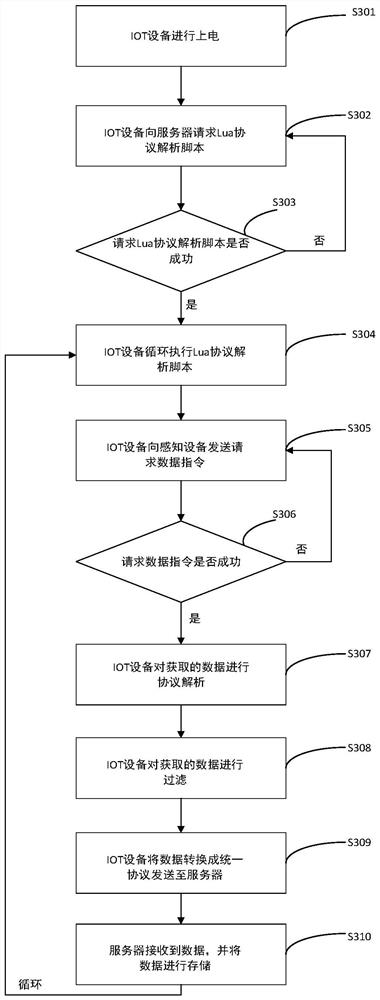
Dynamic control protocol analysis method based on Internet of Things and IOT equipment
ActiveCN112087426AReduce maintenance costsReduce development costsTransmissionThe InternetEngineering
The invention discloses a dynamic control protocol analysis method based on the Internet of Things and IOT equipment. The dynamic control protocol analysis method comprises the steps that: on the basis of power-on of the IOT equipment, the IOT equipment sends a request packet for acquiring a protocol analysis script to a server, so as to obtain the protocol analysis script corresponding to the IOTequipment, wherein a plurality of protocol analysis scripts corresponding to the IOT equipment are pre-stored in the server; running the protocol analysis script in real time according to a script interpreter so as to acquire data from a plurality of sets of target sensing equipment corresponding to the IOT equipment; and performing protocol analysis on the data according to the protocol analysisscript, and sending the data to the server. According to the dynamic control protocol analysis method, by acquiring the protocol analysis script pre-configured in the server, the communication protocol extension between the IOT equipment and the target sensing equipment can be flexibly controlled, and the development cost of the IOT device extension protocol is reduced.
Owner:华瑞新智科技(北京)有限公司 +1
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com