Method and system for downloading executable file securely
A file execution and security technology, applied in transmission systems, security devices, electrical components, etc., can solve problems such as wasting download traffic, wasting user upload traffic, increasing mobile terminal GPRS traffic, etc., to achieve the effect of saving traffic and charges
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
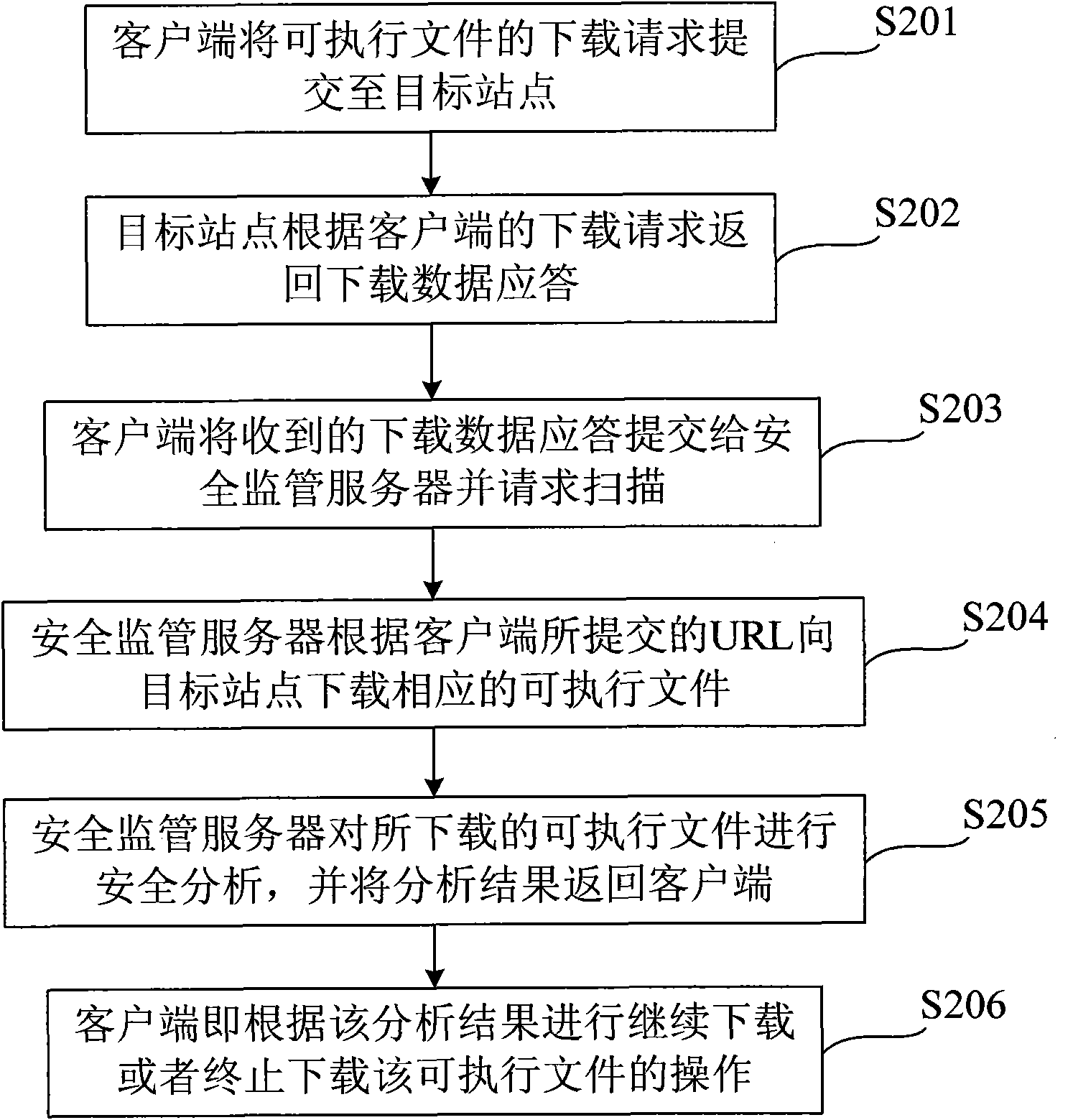
[0028] figure 2 A flow chart of a method for securely downloading an executable file according to Embodiment 1 of the present invention is shown.
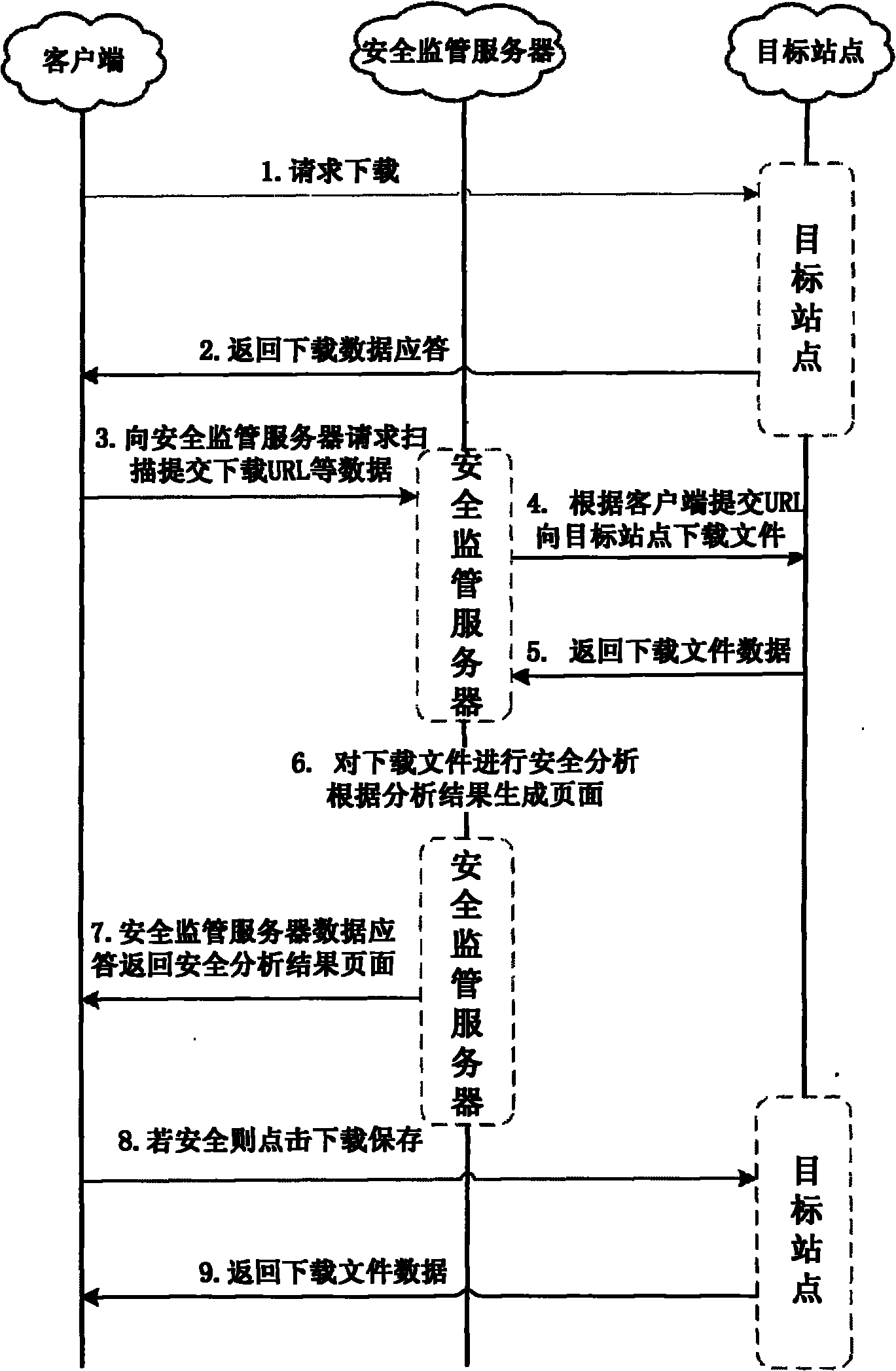
[0029] Such as figure 2 As shown, when the wireless access client wishes to download a certain executable file from the target site, first, the client submits the download request of the executable file to the target site (step S201); the target site returns the download request according to the download request of the client. Data response (step S202); After receiving the download data response of the executable file, the client submits it to the security supervision server, requesting to scan data such as the submitted download URL (step S203), to determine the location of the executable file Security; the safety monitoring server downloads the corresponding executable file to the target site according to the download data response information submitted by the client (step S204); after the target site returns the corresponding...
Embodiment 2
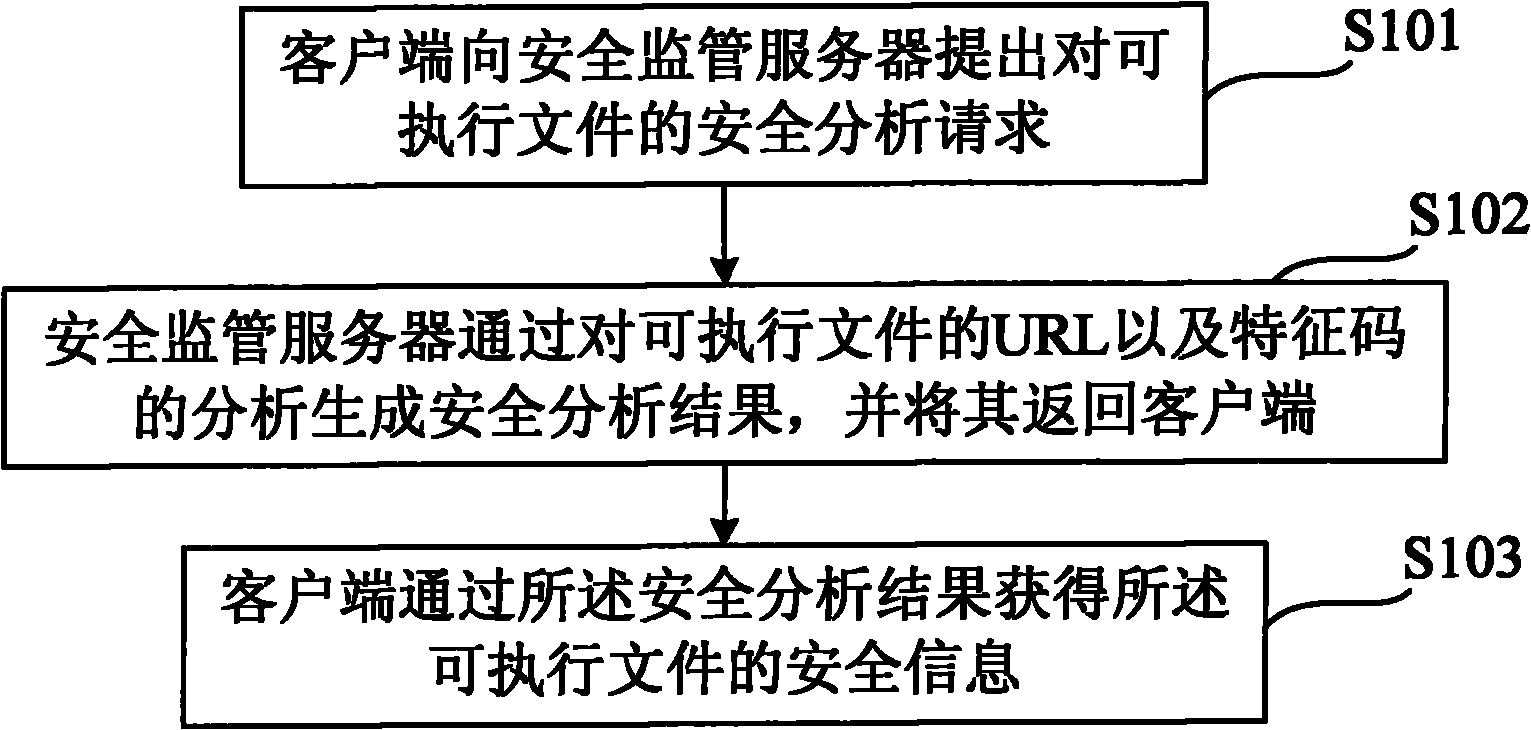
[0039] Figure 5 A flow chart of a method for securely downloading an executable file according to Embodiment 2 of the present invention is shown. Such as Figure 5 As shown, in another embodiment of the present invention, if the client has downloaded the executable file, the client determines its MD5, SHA-1 and other feature codes (step S501) by scanning and analyzing the executable file; Then the URL and the characteristic code of downloading the executable file are submitted to the security monitoring server and request security analysis (step S502); after receiving the security analysis request submitted by the client and the relevant information of the executable file, the security monitoring server The relevant information such as the URL of executable file, feature code carries out security analysis, and analysis result is returned client (step S503); Client installs according to this analysis result or does not install the operation of this executable file (step S504)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com