Method and device for removing malicious programs
A malicious program and program technology, applied in the field of information security, can solve the problems that the original program cannot run, cannot be opened normally and enter the user's computer system, and the user is afraid of virus removal actions, etc., and achieves a convenient, safe and effective virus removal solution. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] The present invention will be further described below with reference to the accompanying drawings.
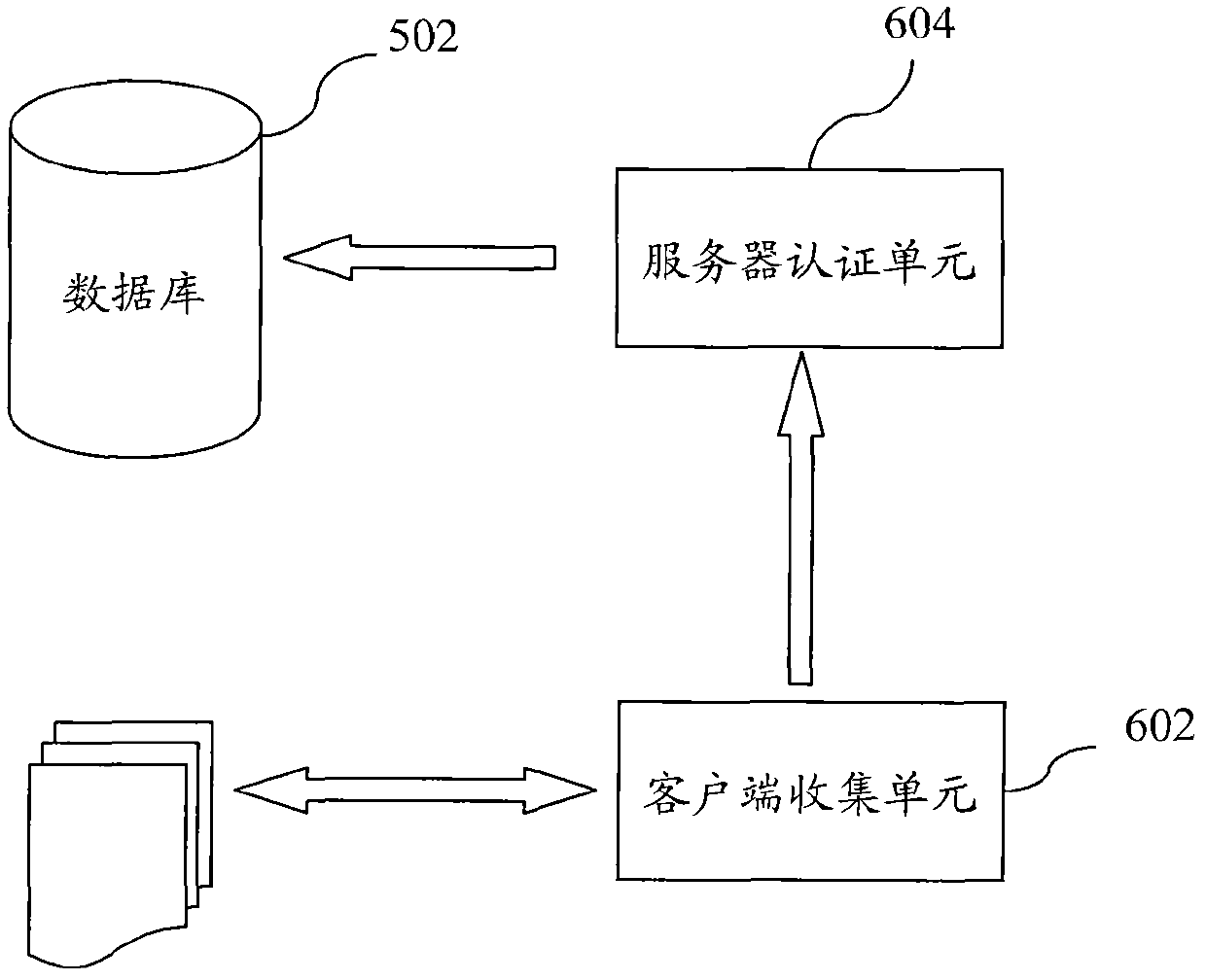
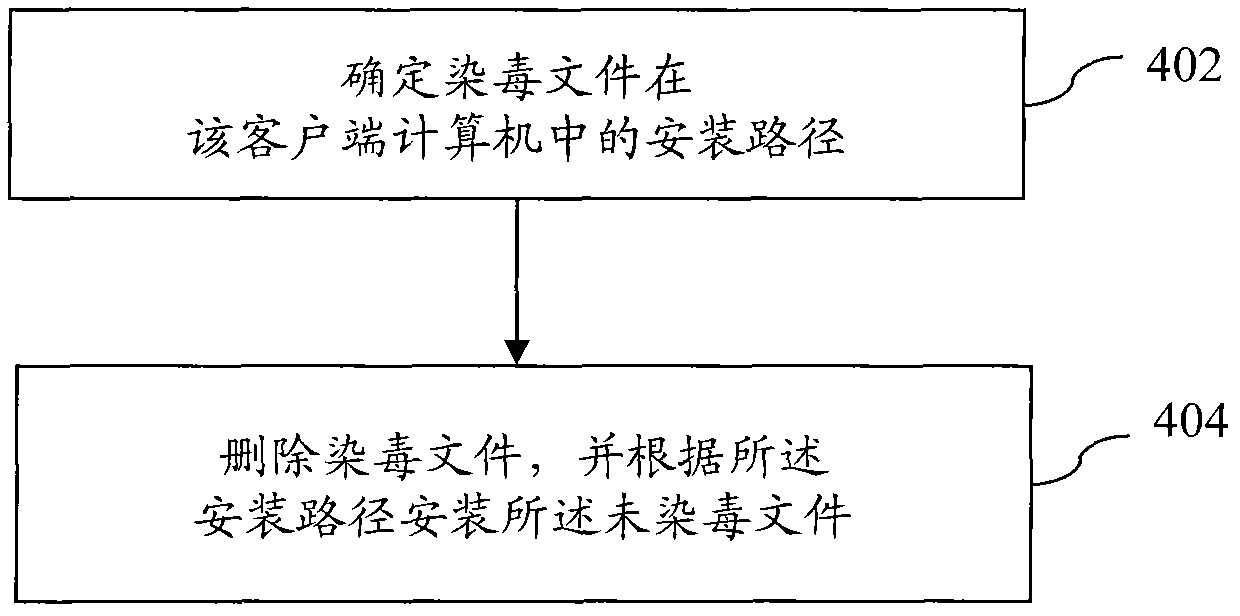
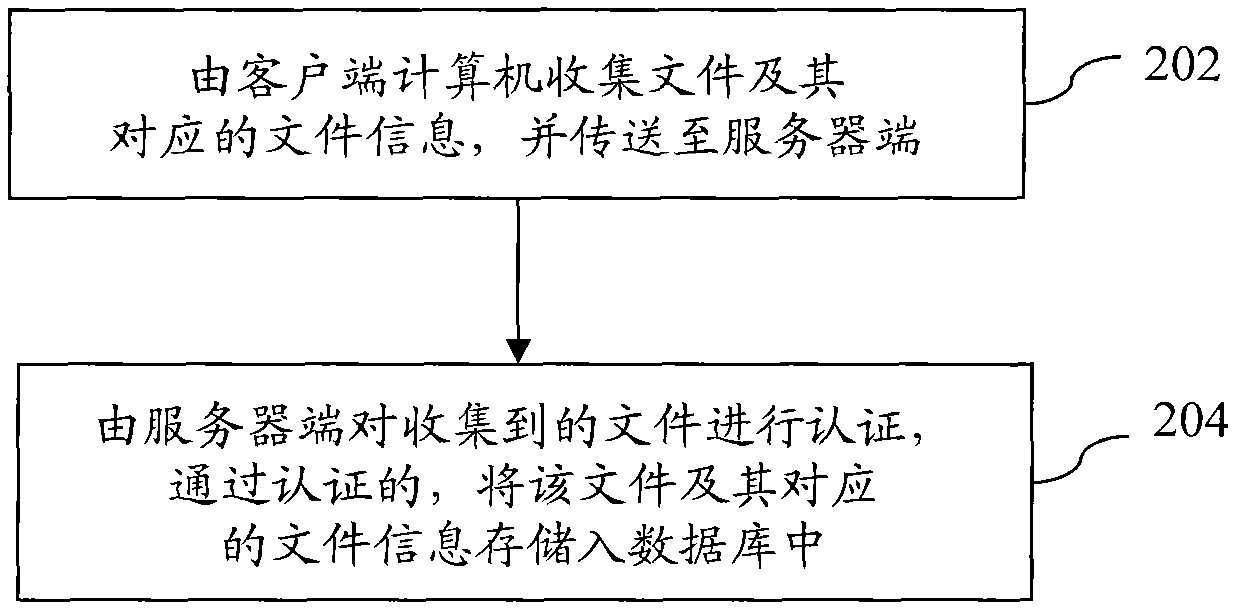
[0054] Aiming at the disadvantages of existing methods for removing malicious programs, the core idea of the present invention is to replace virus-infected files directly instead of using the method of removing virus codes. For this reason, it is necessary to build a file database in advance and pay attention to collecting the information of good files , when the infected file and its information can be determined, the file information can be used to search the database for a good file that has not been infected in advance, and after downloading the good file to the client computer infected by the virus, replace the infected file .
[0055]Please refer to figure 1 , which is a flow chart of a method for removing malicious programs according to an embodiment of the present invention. First, a database is constructed, and files not infected with viruses and correspondin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com