Hash function based RFID (Radio Frequency Identification Devices) authentication method
An authentication method and function technology, applied in the field of identity authentication, can solve problems such as authentication confusion, information leakage, and the legitimacy of unauthenticated readers, and achieve the effect of avoiding potential safety hazards and solving location leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0022] The present invention will be described in detail below with reference to the accompanying drawings and examples.
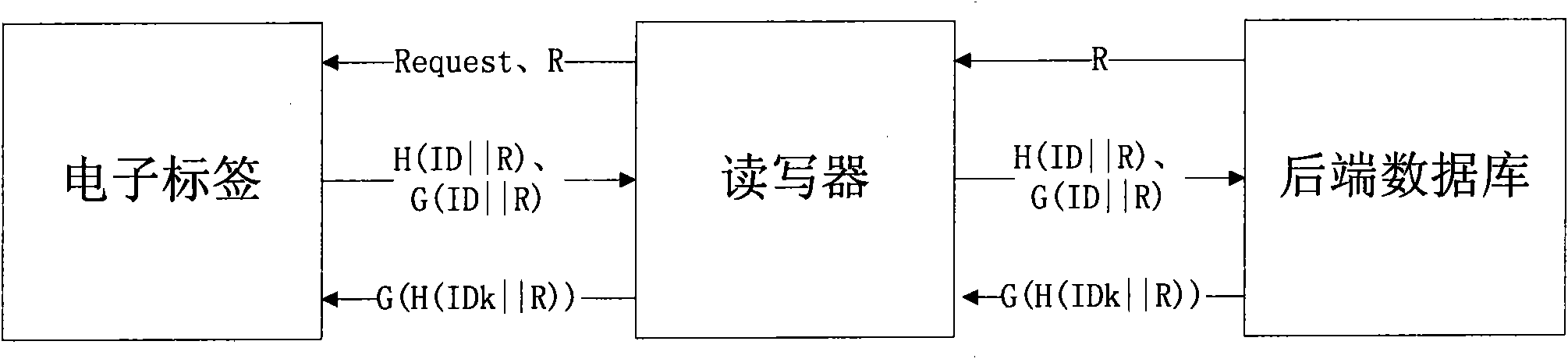
[0023] On the basis of the currently existing Hash-lock authentication protocol, the present invention proposes an improved RFID authentication method based on Hash function. Such as figure 1 As shown, the method is specifically:
[0024] First, the present invention introduces two different Hash functions H and G. H and G here refer to Hash functions constructed by different methods, for example, one Hash function can be selected to be composed of MD5 algorithm, and the other Hash function can be composed of SHA-1 algorithm. Introduce a random number module in the backend database. Before the authentication starts, the electronic tag stores its own ID, and the back-end database stores the IDs of all legal electronic tags. The specific authentication steps are as follows:
[0025] Step 1. A random number R is generated by the random number module in th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com