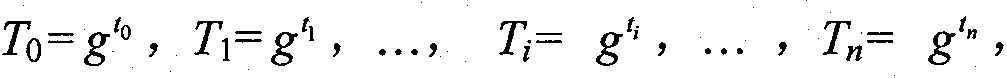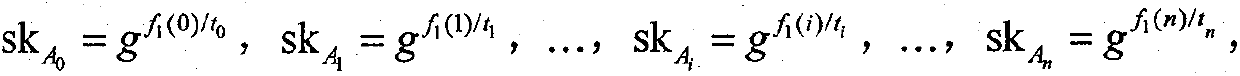Inter-domain authentication and key negotiation method
A key agreement and shared key technology, applied in user identity/authority verification, electrical components, transmission systems, etc., can solve the problems of low key agreement efficiency and failure to guarantee the reliability of domain representative nodes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
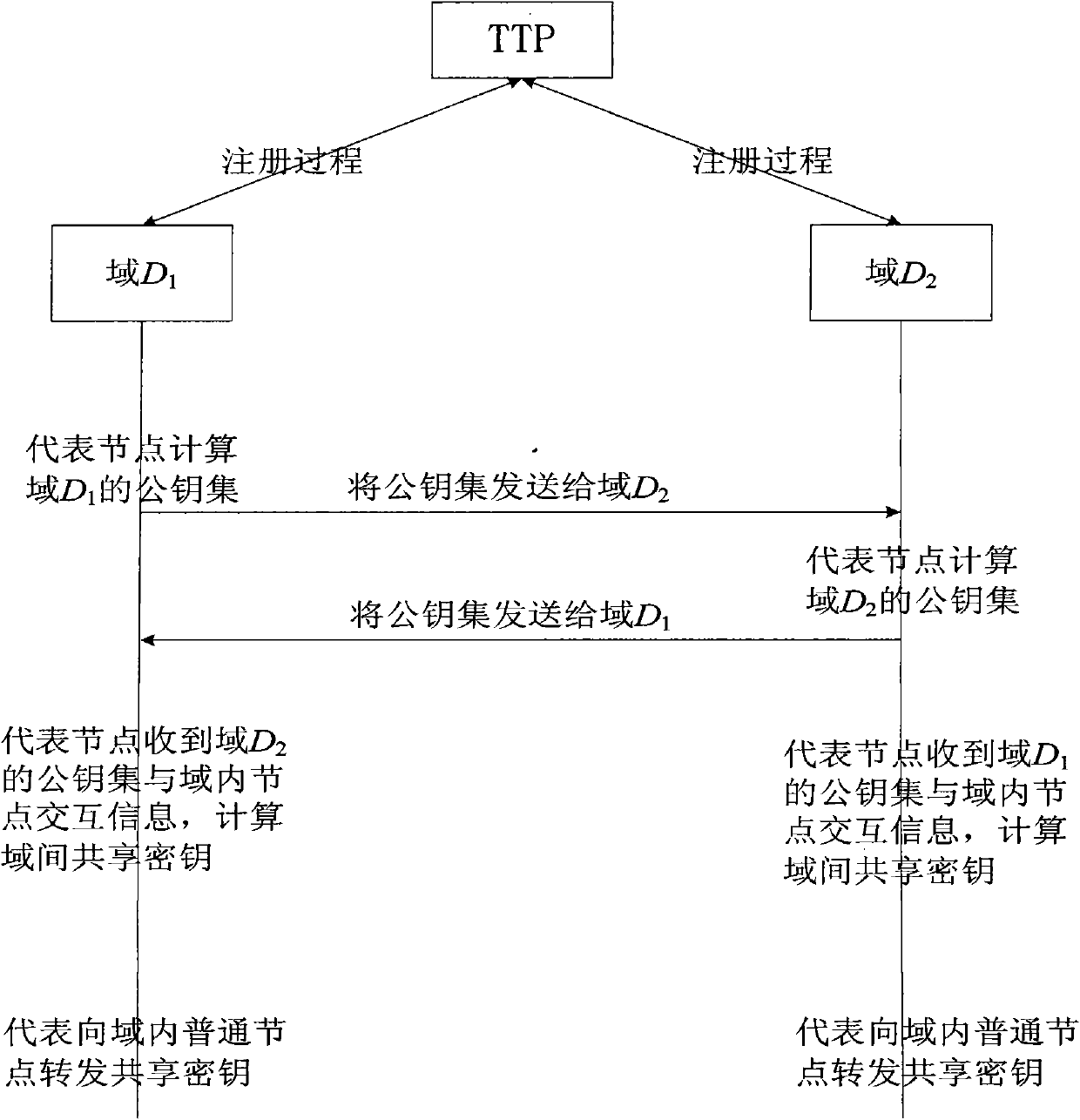
[0080] The inter-domain authentication and key agreement method proposed by the present invention converts the physical network for communication between nodes into a logical network for communication between domains. After the domain that wants to communicate registers with a trusted third party, different domains Negotiating the shared key requires only one communication between domains, and then all nodes in the domain can obtain the shared key needed for inter-domain secure communication through information exchange between representative nodes and ordinary nodes in the domain.
[0081] attached figure 1 The flow chart of the inter-domain authentication and key agreement method of the present invention is given, domain D 1 The randomly elected representative node is A 0 , domain D 2 The randomly elected representative node is B 0 , a complete process of authentication and key agreement between them will be described below.
[0082] 1) Trusted third party establishes sy...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com