Trusted computing platform chip applicable to mobile communication equipment and authentication method thereof
A mobile communication device and trusted computing technology, applied in the fields of information security and biometric identification, can solve the problems of inability to perform remote payment and low security, and achieve the effect of mobile on-site payment, security and high security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0060] Below in conjunction with accompanying drawing and embodiment the present invention will be further described:
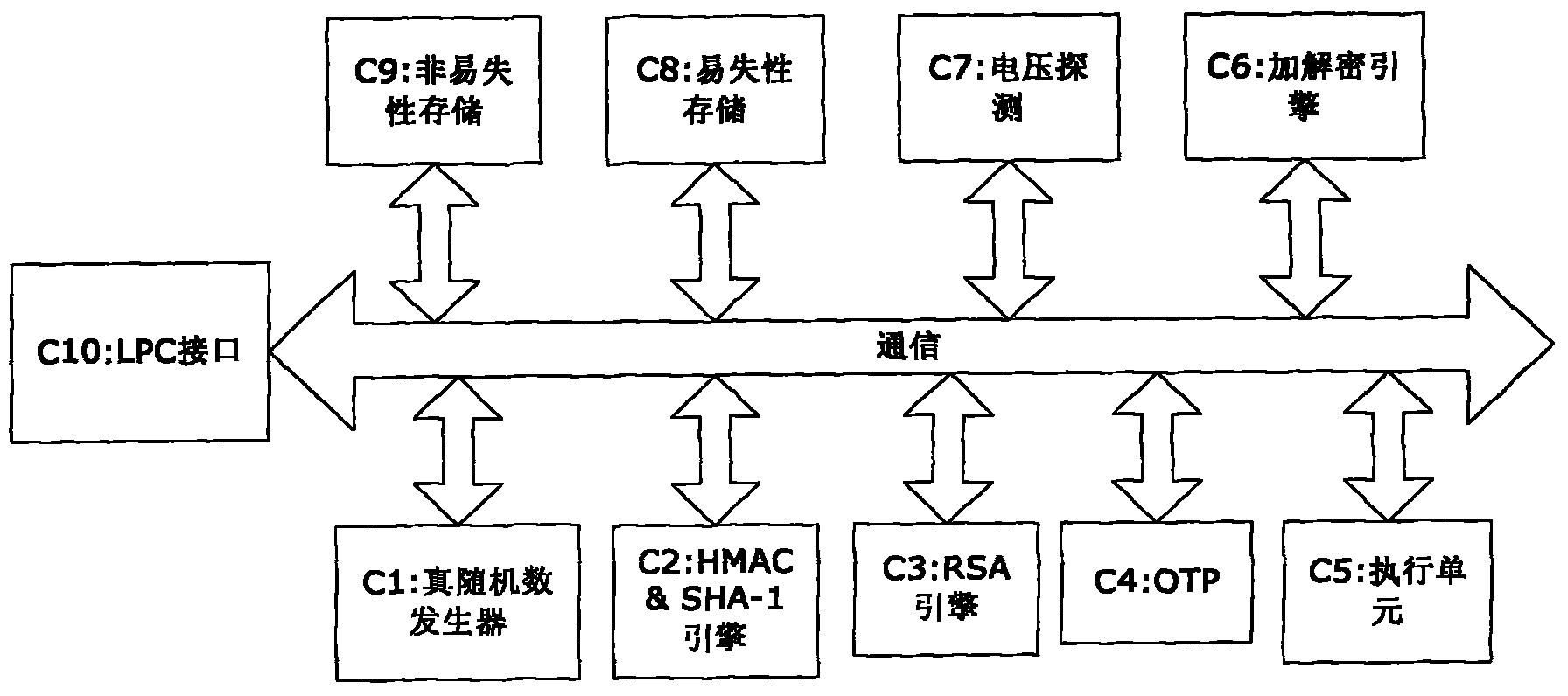
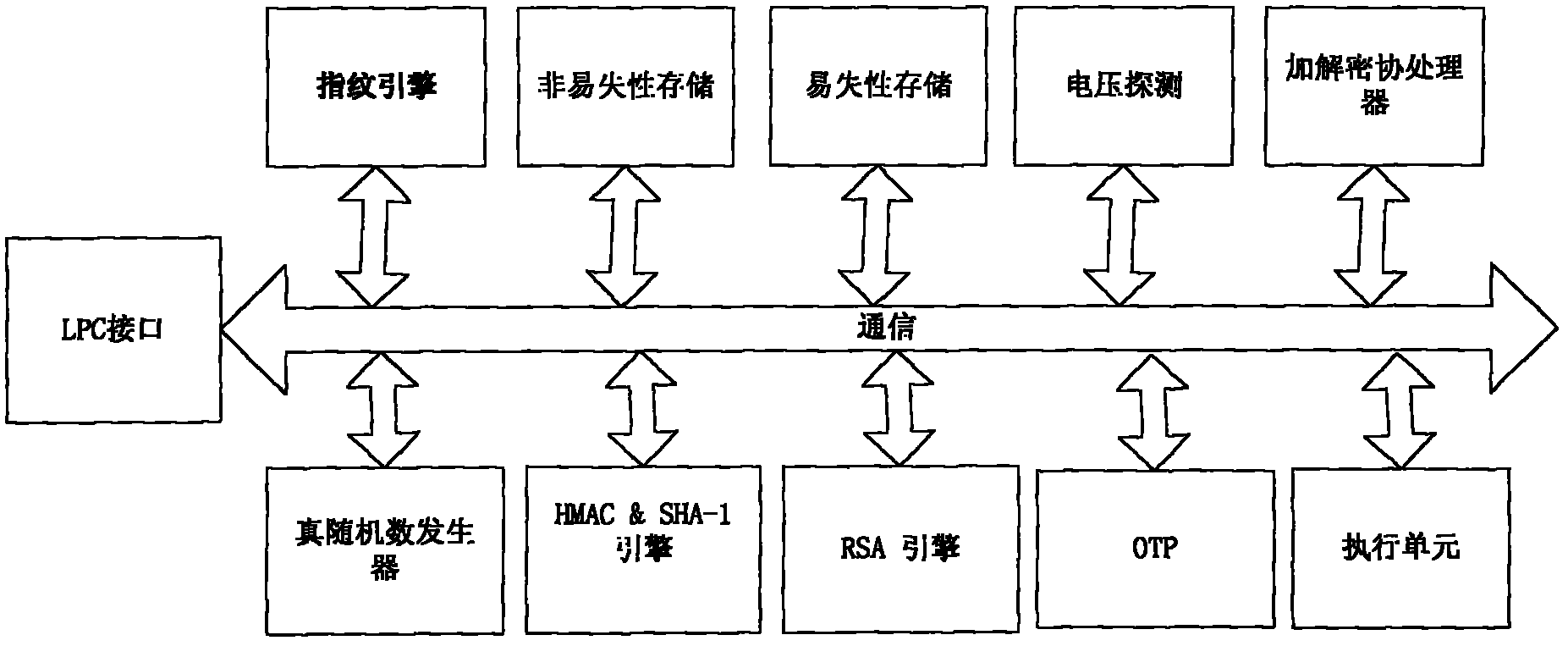
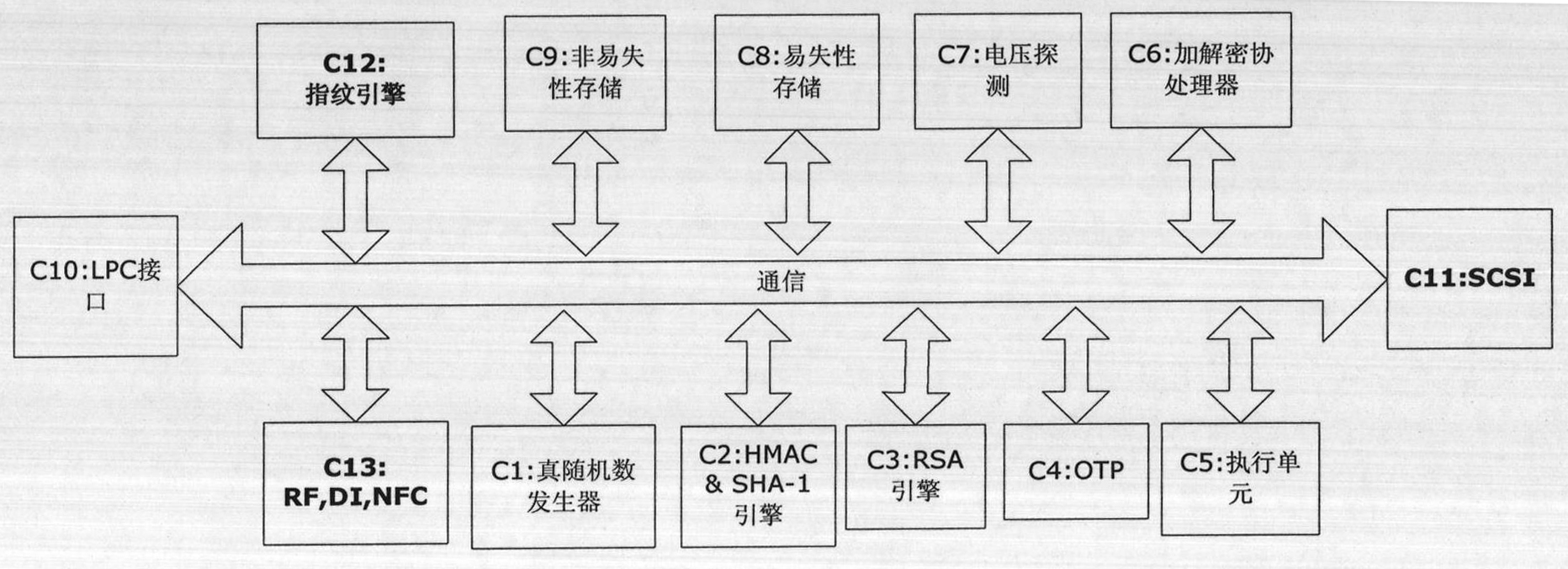
[0061] Such as image 3 As shown, this kind of trusted computing platform chip that can be applied to mobile communication equipment combines the high security of TPM with short-distance transmission technology, and the addition of fingerprint technology makes the equipment and people bind, which greatly strengthens the security of the SIM card. safety. The focus of the invention is to add a fingerprint processing engine module, a SCSI interface module supporting SIM card operation and a short-distance transmission module on the common TPM chip. The fingerprint processing engine module, the SCSI interface module and the short-distance transmission module are all connected to the communication bus, and the chip is packaged in the form of a SIM card or TPM, and supports both contact and non-contact operations. The common short-distance transmission modules ar...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com