Method for analyzing safety property of software based on sequence clustering
A sequence clustering and software security technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve problems affecting the quality of the vulnerability knowledge base and difficulty in collecting software vulnerability sequence sets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
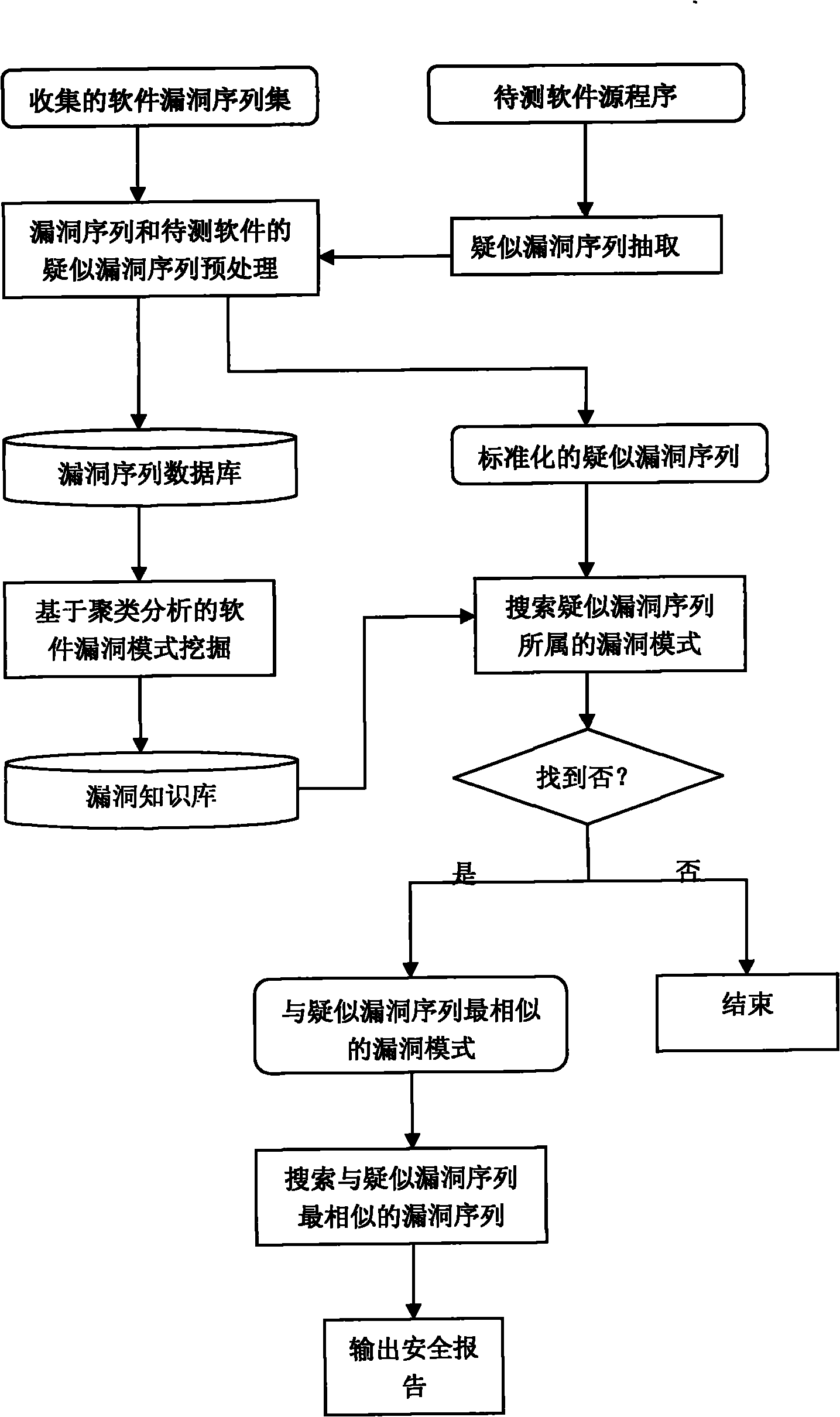
[0044] The technical solutions of the present invention will be described in detail below in combination with specific embodiments.
[0045] 1. Randomly select 6 vulnerability sequences from the collected software vulnerability sequences and preprocess them to create a software vulnerability sequence database, as shown in Table 1.
[0046] Table 1 Software Vulnerability Sequence Database SVSD
[0047]
[0048] 2. Using sequence clustering technology to mine the vulnerability patterns in the software vulnerability sequence database, the specific operation steps are as follows,
[0049] ①Set the value of K to 2, that is, the vulnerability sequence in SVSD is divided into two vulnerability patterns, and the two vulnerability sequences in the software vulnerability sequence database are selected as the initial central sequence of the vulnerability pattern, here S is selected 1 Vulnerability mode P 1 The initial center sequence of S 2 Vulnerability mode P 2 The initial cente...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com