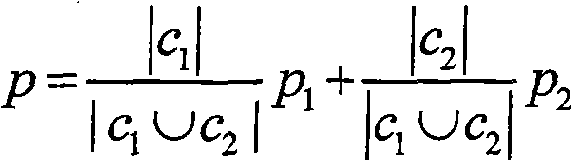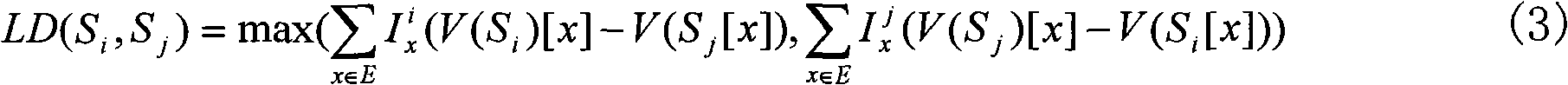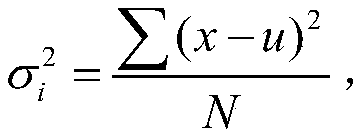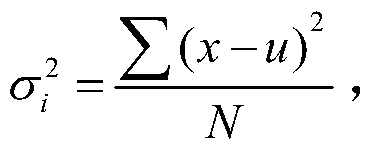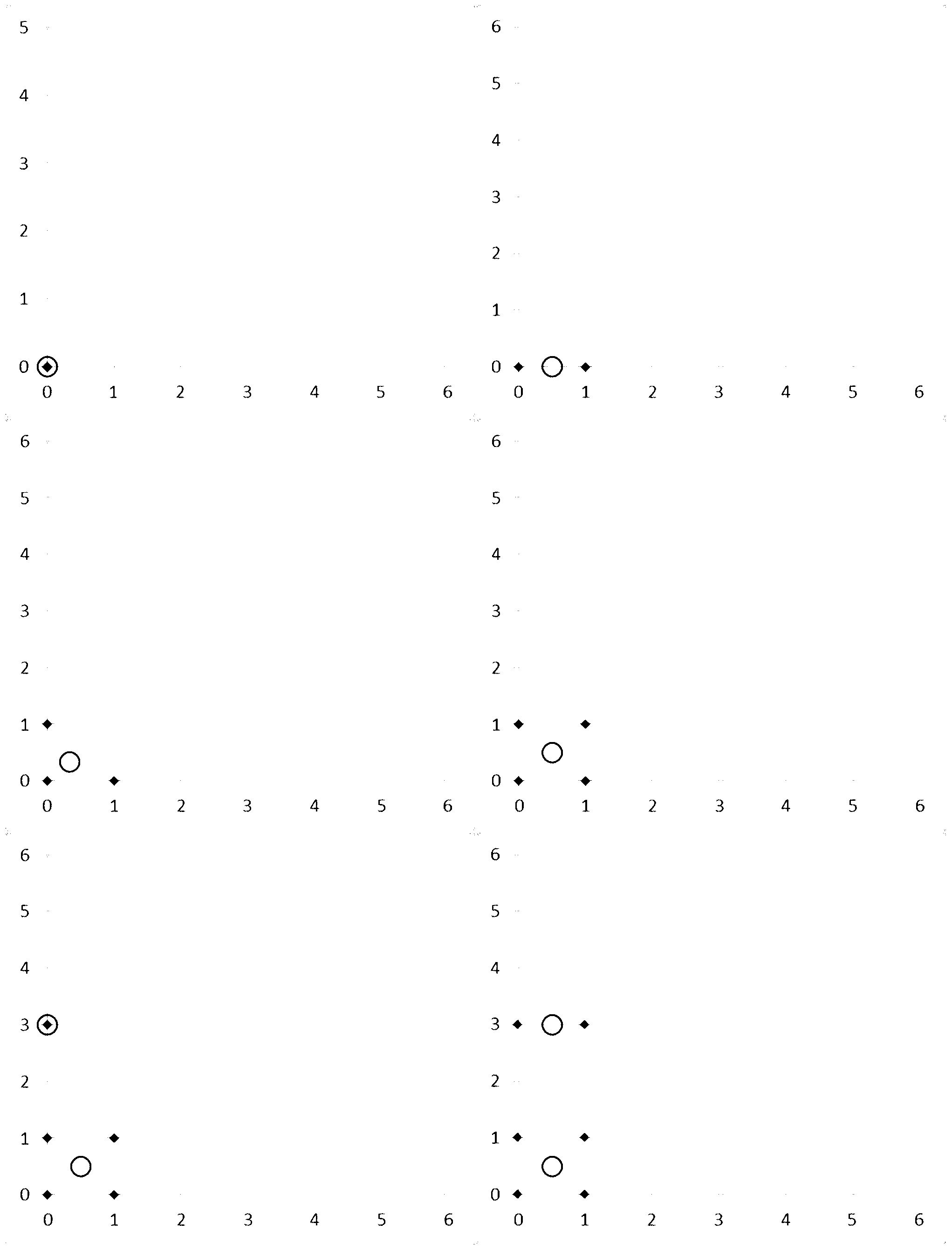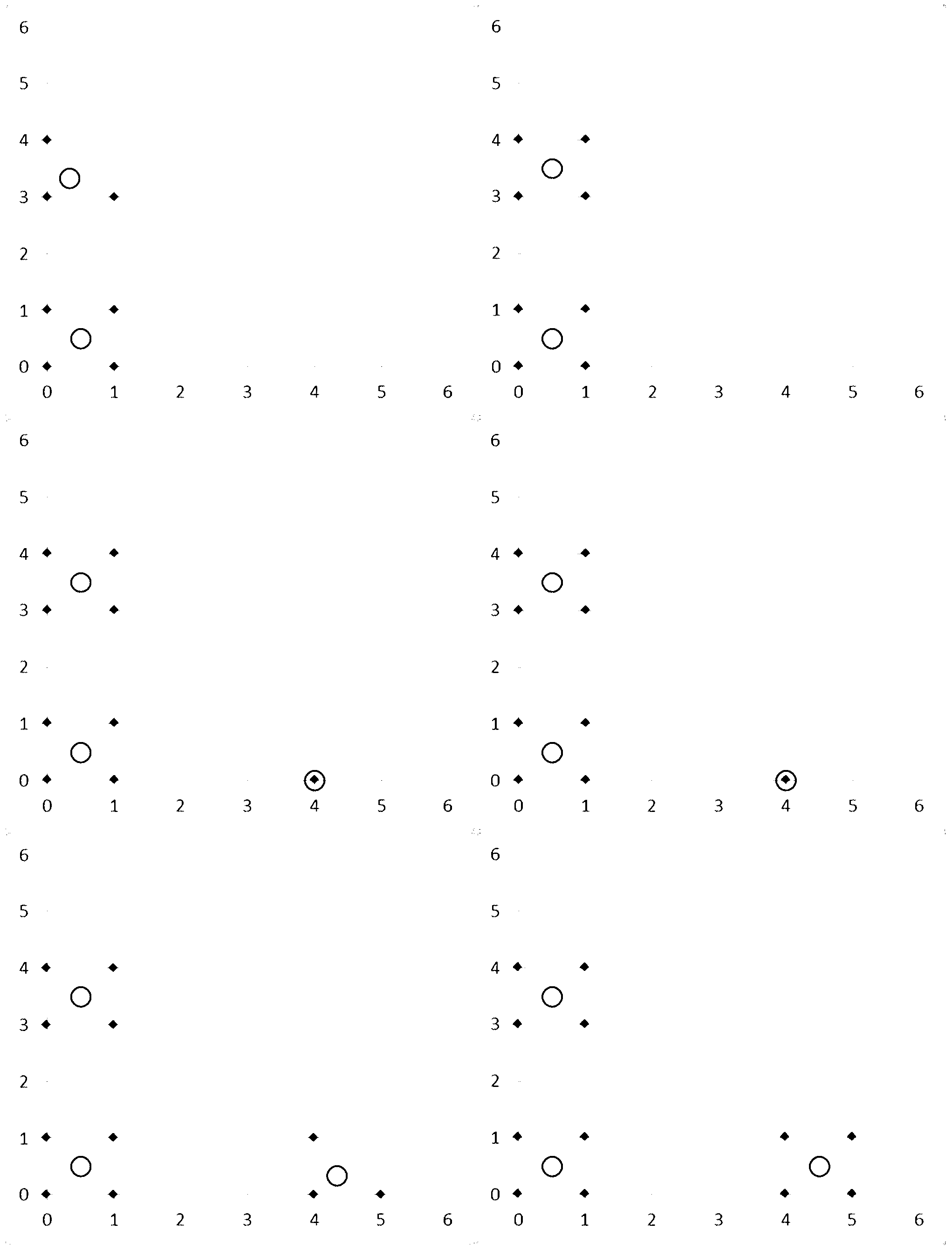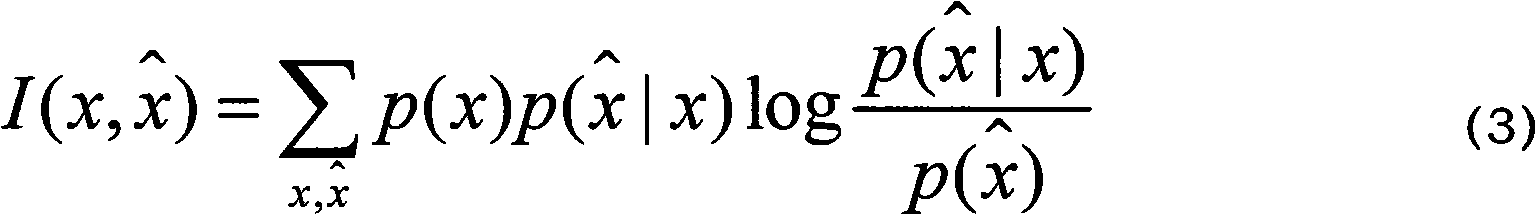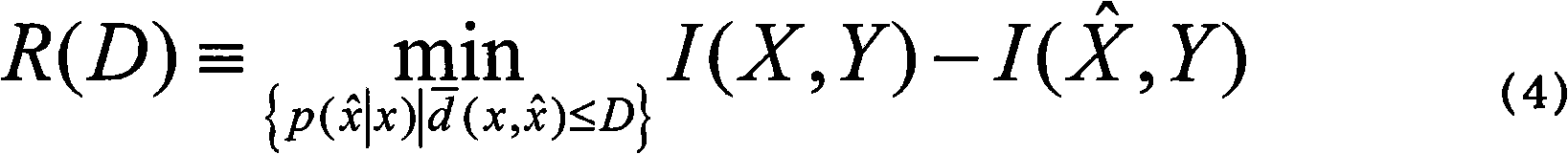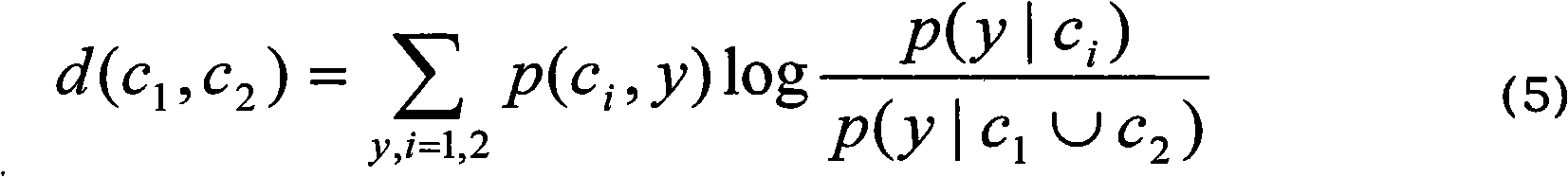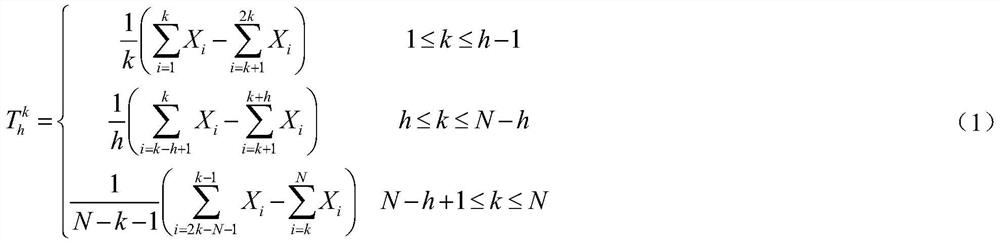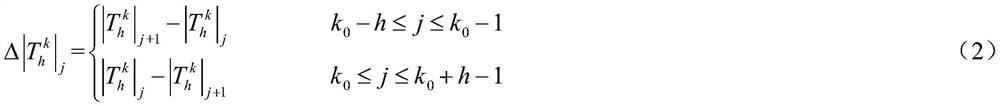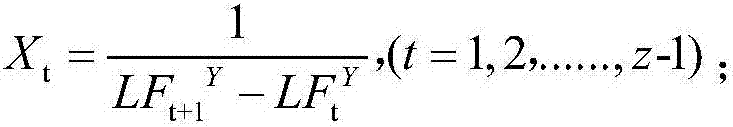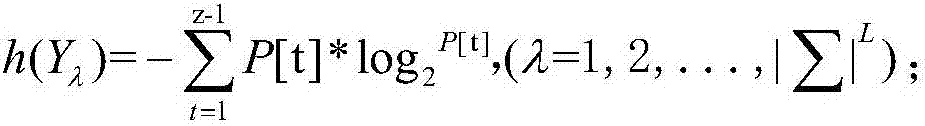Patents
Literature
63 results about "Sequence clustering" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
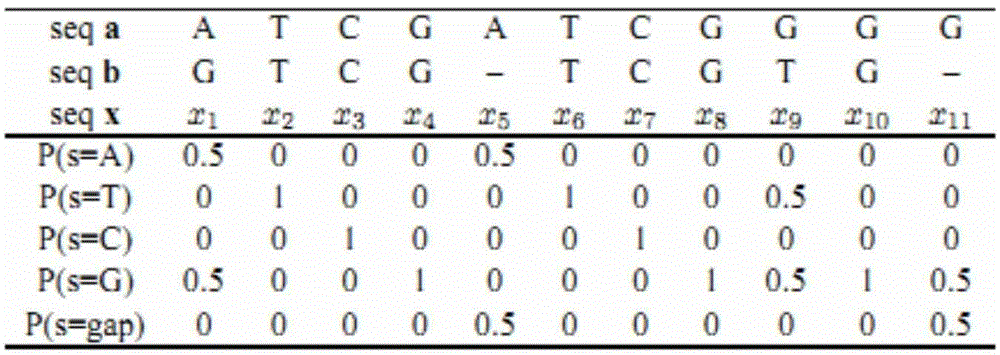
In bioinformatics, sequence clustering algorithms attempt to group biological sequences that are somehow related. The sequences can be either of genomic, "transcriptomic" (ESTs) or protein origin. For proteins, homologous sequences are typically grouped into families. For EST data, clustering is important to group sequences originating from the same gene before the ESTs are assembled to reconstruct the original mRNA.
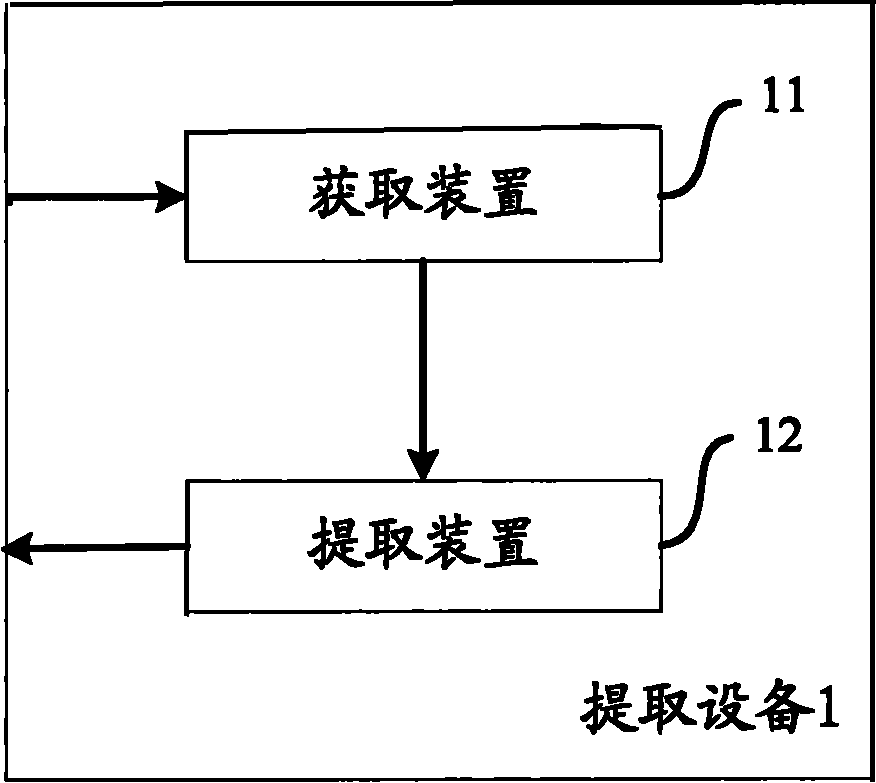
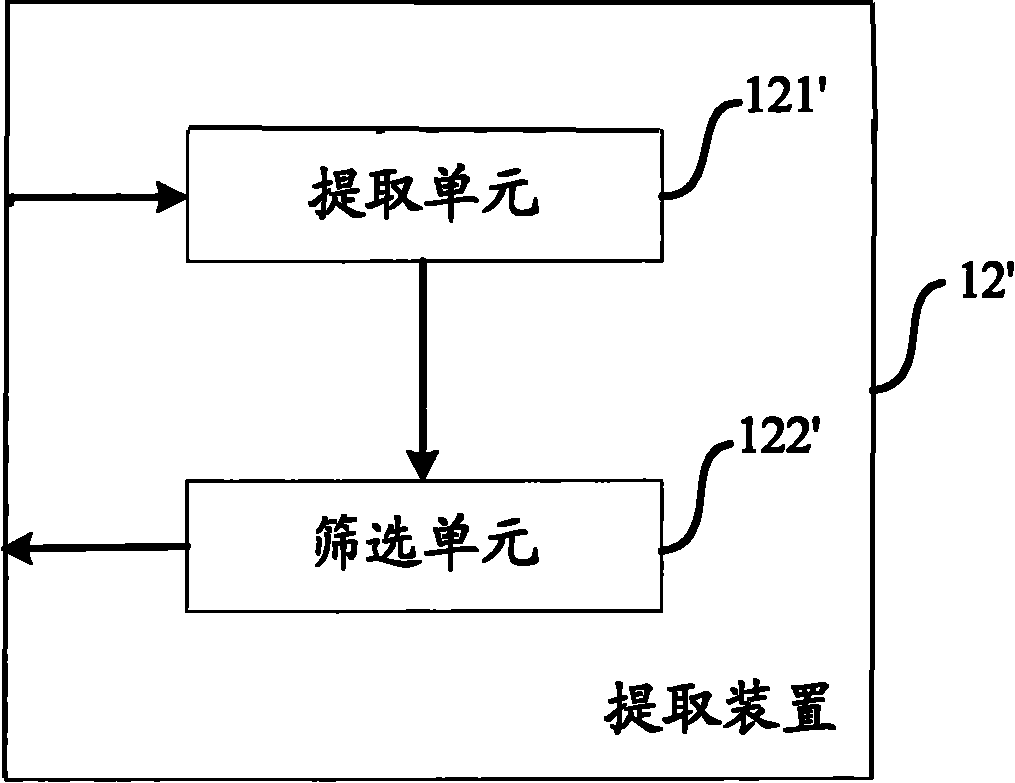
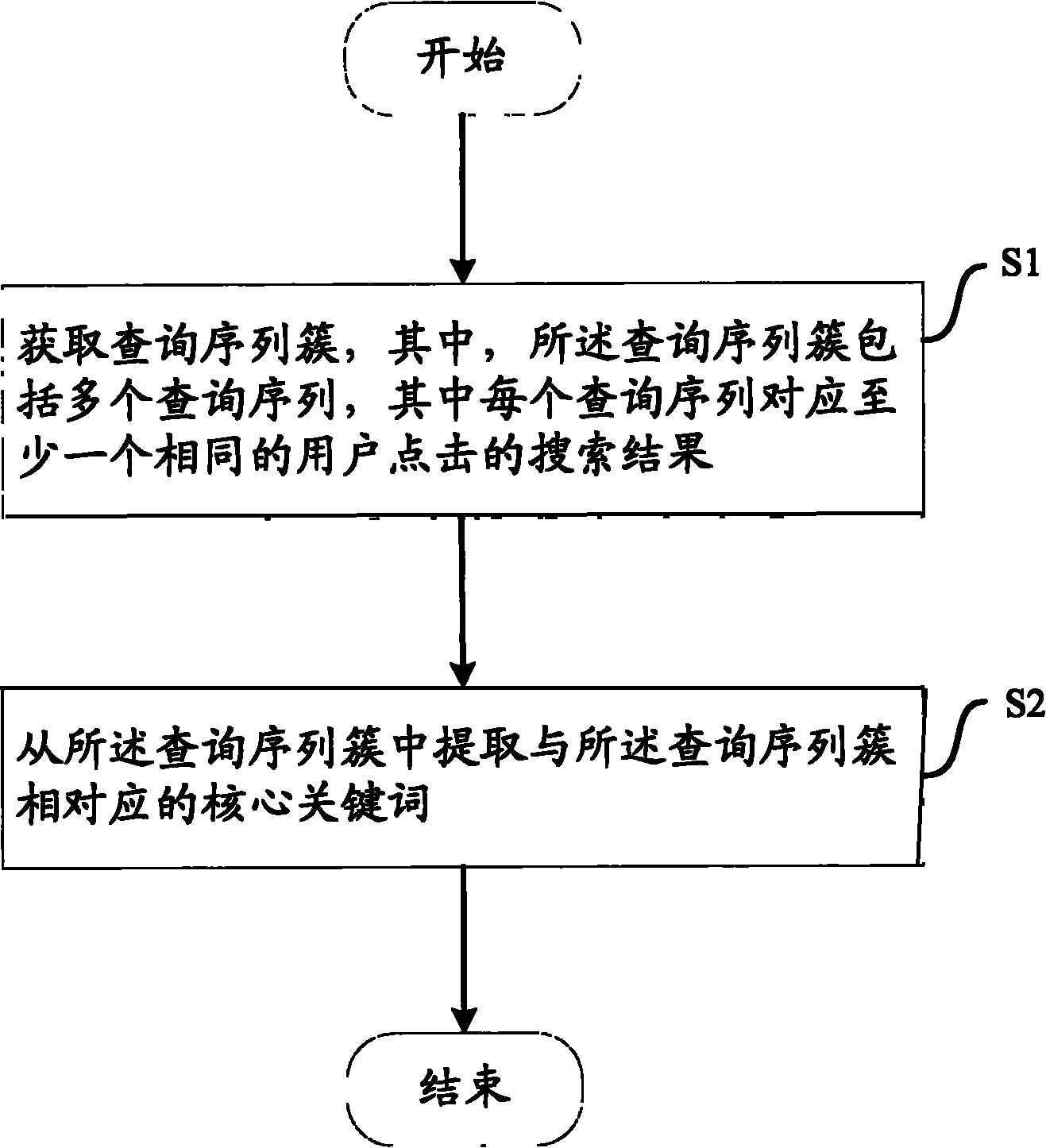
Method and equipment for extracting core keywords based on query sequence cluster
ActiveCN102043845AImprove the search experienceSpecial data processing applicationsSequence clusteringIndex term
The invention aims to provide a method and equipment for extracting core keywords based on a query sequence cluster. The method comprises the following steps of: acquiring the query sequence cluster by the extracting equipment, wherein the query sequence cluster comprises a plurality of query sequences and each query sequence corresponds to at least one same user clicked search result; and extracting the core keywords corresponding to the query sequence cluster from the query sequence cluster. Compared with the prior art, search requirements of users of the query sequences input to the query sequence cluster are acquired, and more appropriate search suggestions or more relevant search results or the like can be supplied to the users according to the core keywords, so that the users acquire better search experience. Furthermore, when a lexicon does not contain the core keywords, the core keywords can be used as new words and added into the lexicon for each application.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
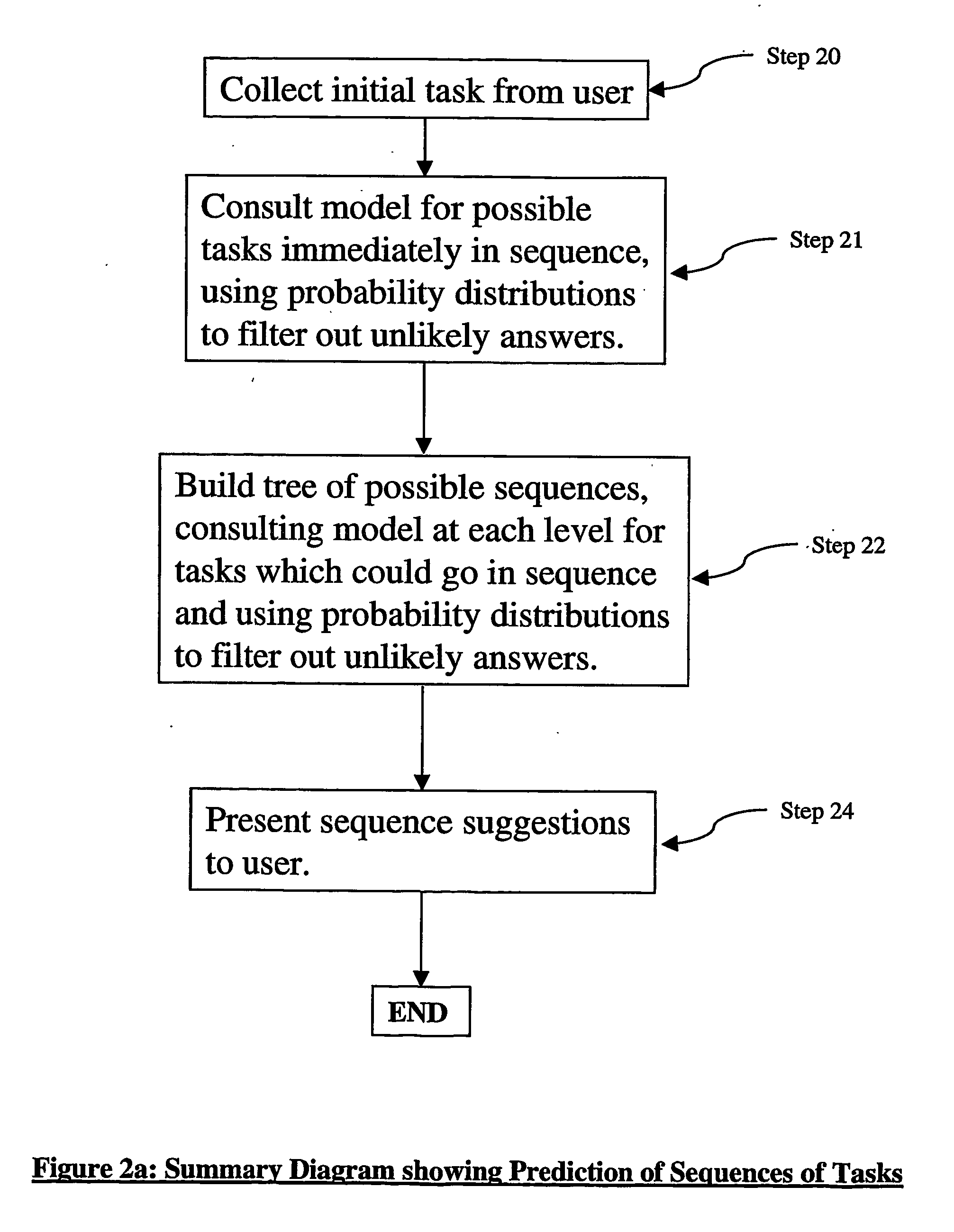
Method for adaptively and dynamically scheduling manufacturing systems
ActiveCN104635772AReduce trafficIntelligent search strategySpeed/accelaration controlSelf adaptiveSequence clustering
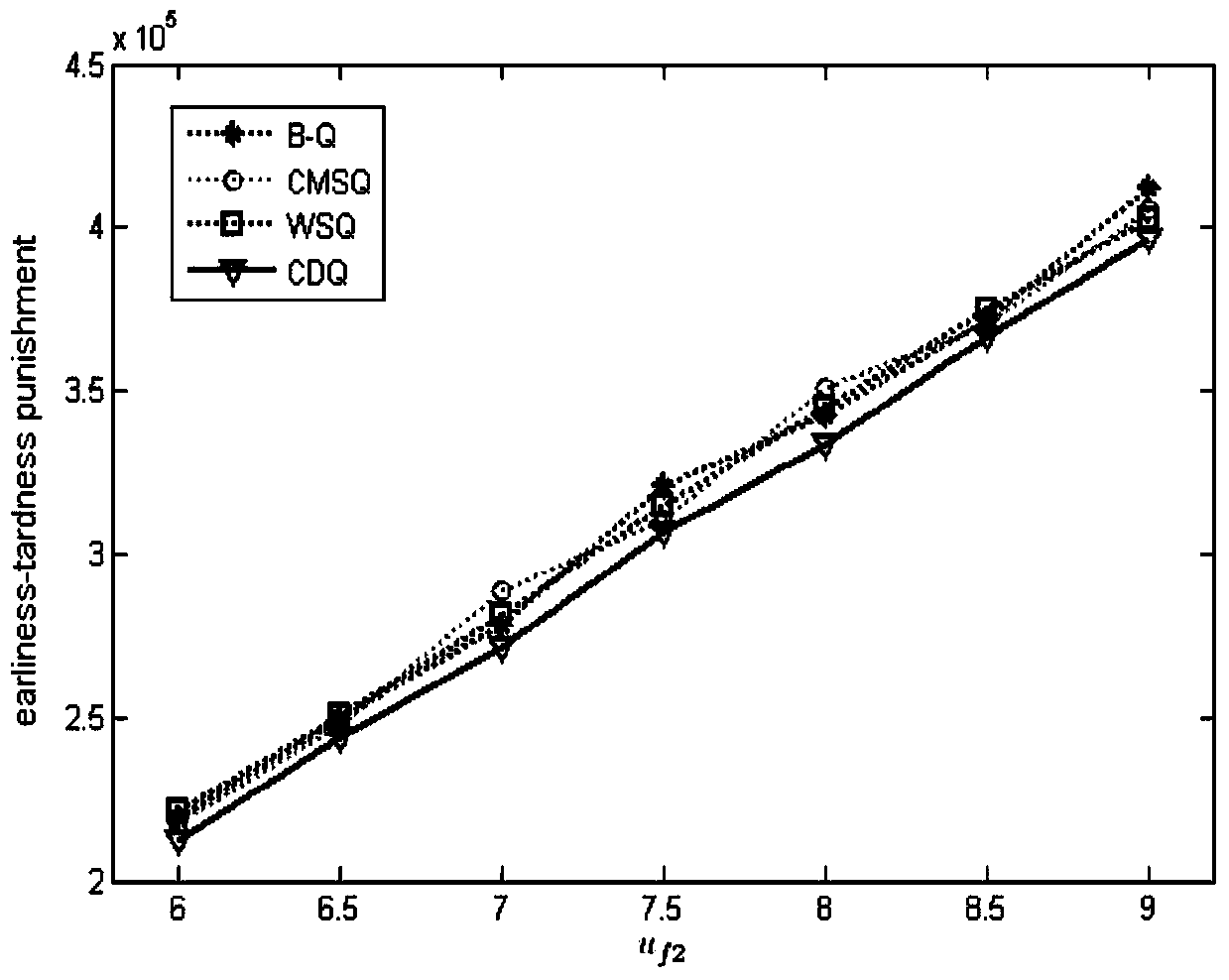
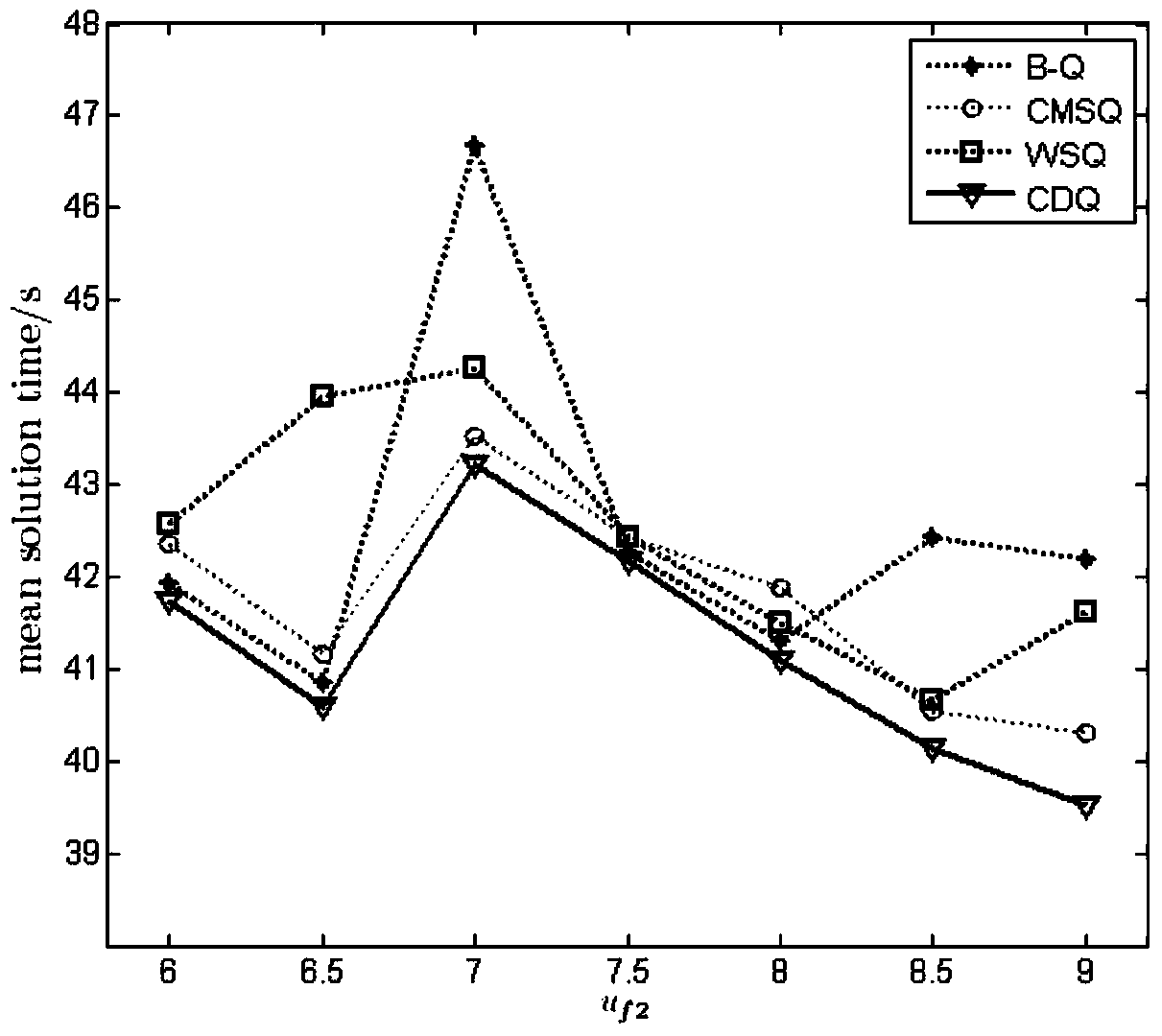
The invention discloses a method for adaptively and dynamically scheduling manufacturing systems, and relates to the field of production scheduling for manufacturing systems. The method has the advantages that a multi-Agent-based dynamic production scheduling system is constructed for the uncertainty of production environments of the manufacturing systems; an improved Q-learning algorithm on the basis of cluster-dynamic search is provided in order to guarantee that appropriate bid winning operation can be selected by equipment according to current system states, and dynamic scheduling strategies can be adaptively selected in the uncertain production environments under the guidance of the improved Q-learning algorithm; system state dimensions are reduced by the dynamic scheduling strategies by the aid of sequence clusters, and learning is carried out according to state different degrees and dynamic greedy search strategies; the convergence and the complexity of the algorithm are analyzed, and the effectiveness and the adaptability of the method for adaptively and dynamically scheduling the manufacturing systems are verified by simulation experiments.
Owner:江苏金猫机器人科技有限公司
Diary management method and system
InactiveUS20060282298A1Promote resultsOvercome problemsDigital data information retrievalSpecial data processing applicationsSequence clusteringData mining
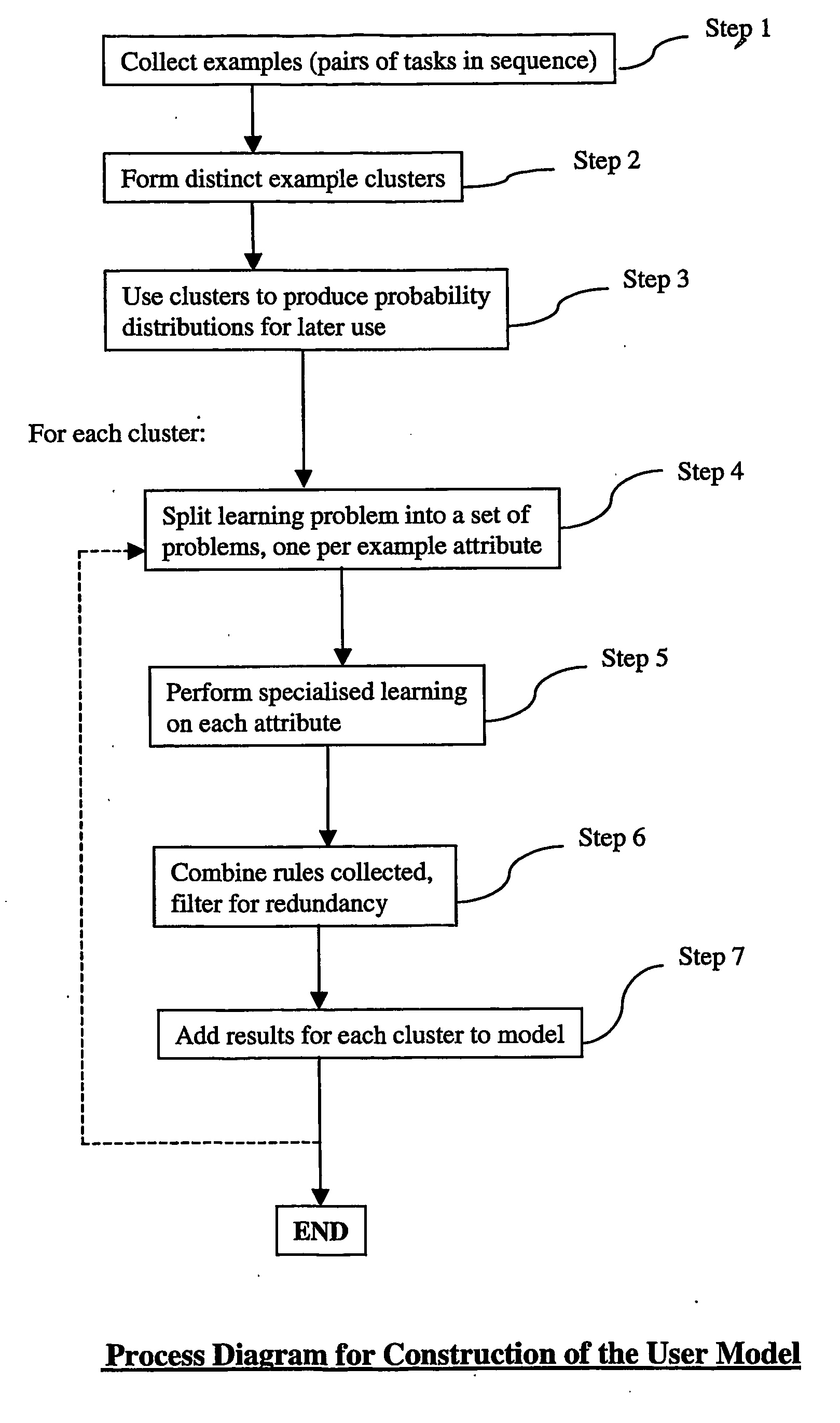
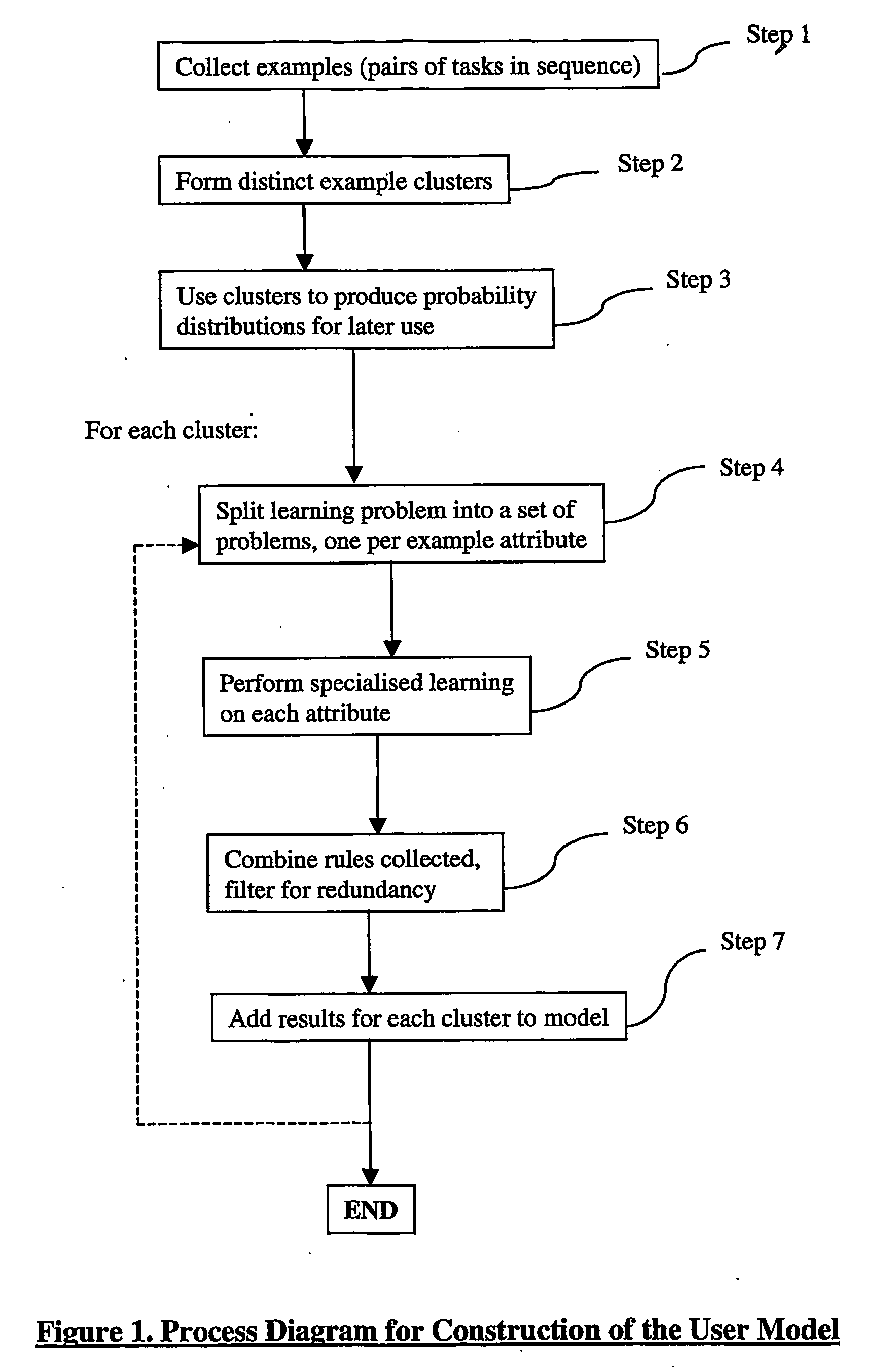
Methods and systems are provided for deriving a user model from a plurality of event records relating to events, each event record comprising data relating to attributes of an event, the method comprising: identifying a plurality of sequences of event records from said plurality of event records, each sequence containing a plurality of event records; determining a plurality of sequence clusters from said plurality of sequences, each sequence cluster comprising a plurality of related sequences; analysing the sequences in a cluster and deriving one or more rules relating to the sequences of that cluster; and providing a user model based on rules derived in relation to a plurality of clusters. Methods and systems are also provided for using a user model for suggesting possible events, or sequences of events, which may follow or precede known events, and for determining a potential sequential order for a plurality of known events.
Owner:BRITISH TELECOMM PLC
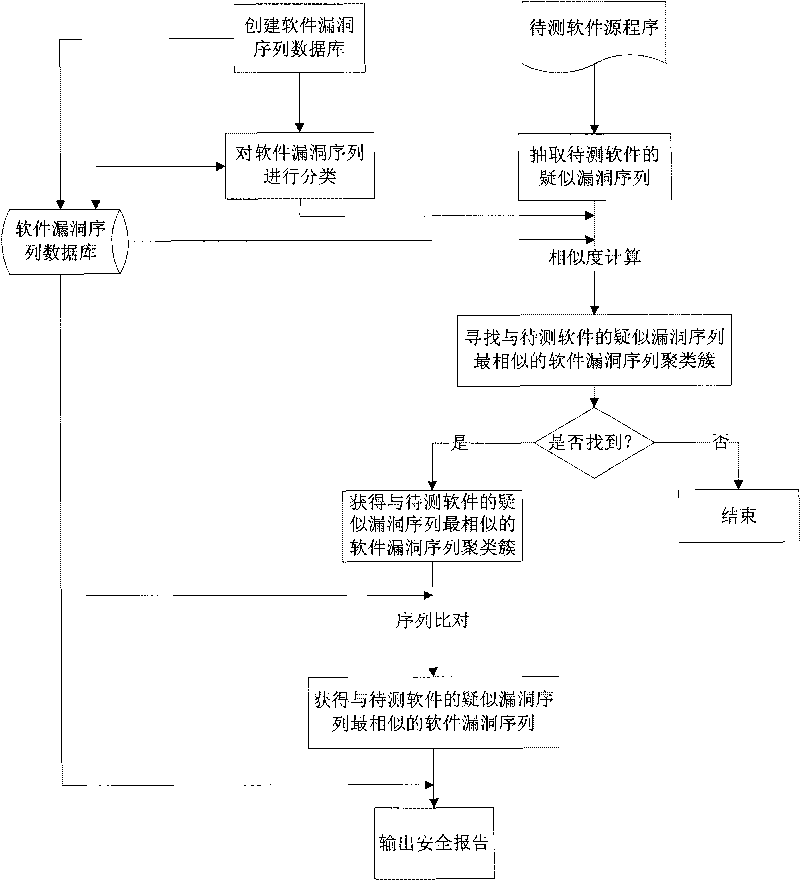
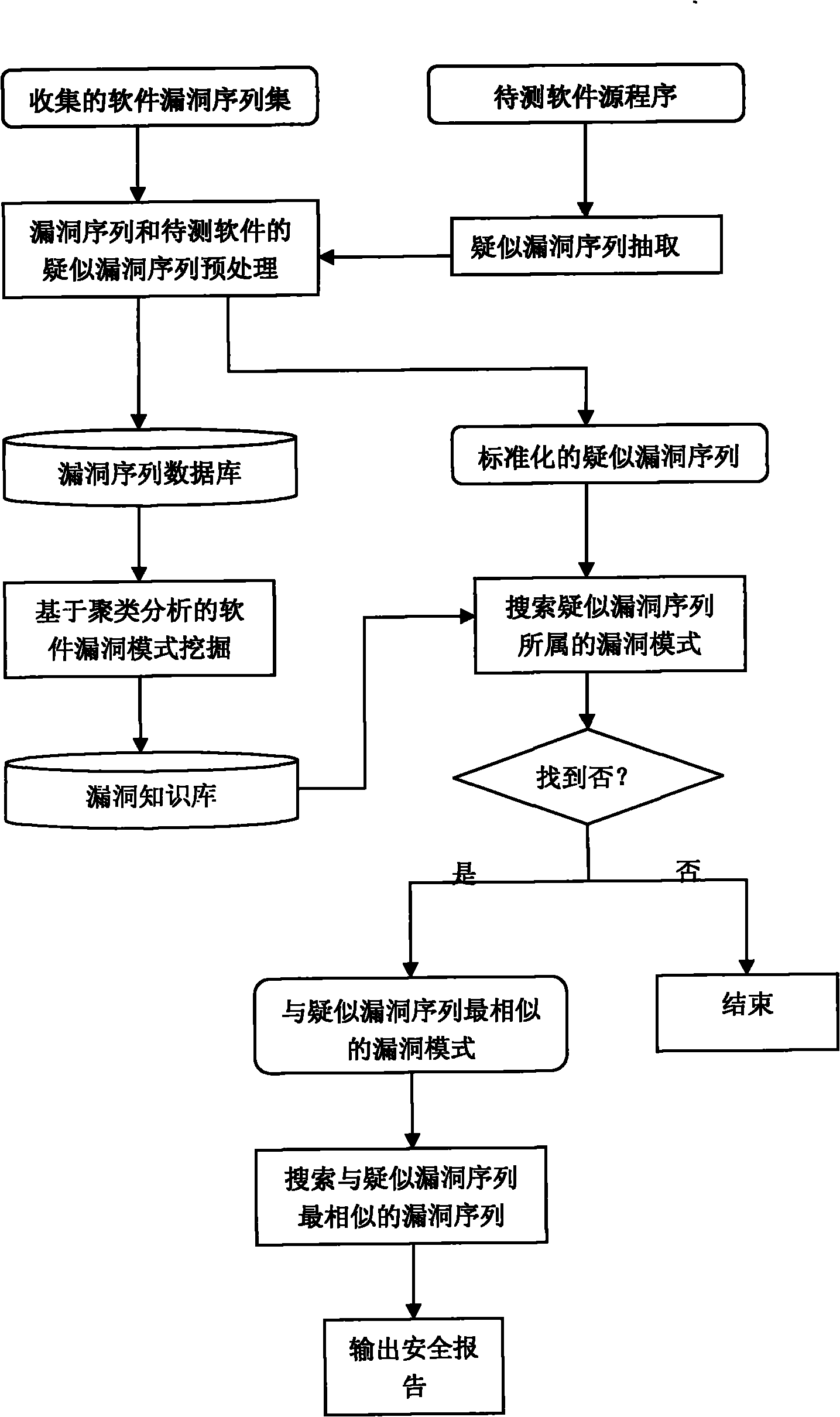
Method for analyzing characteristic of software vulnerability sequence based on cluster
InactiveCN101739337AImprove analysis efficiencyEasy to operateSoftware testing/debuggingSequence databaseSoftware engineering
The invention discloses a method for analyzing the characteristic of a software vulnerability sequence based on a cluster, which belongs to the technical field of information security. The method comprises the following steps: firstly, establishing a software vulnerability sequence database by using the conventional software vulnerability sequence; secondly, analyzing the software vulnerability sequence in the database by using clustering technology so as to generate a plurality of software vulnerability sequence clustering clusters; thirdly, finding the software vulnerability sequence clustering cluster which is most similar to a doubtful vulnerability sequence of software to be tested through similarity computation; fourthly, comparing the doubtful vulnerability sequence of the software to be tested with all software vulnerability sequences in the most similar software vulnerability sequence clustering cluster through a sequence comparison method, and further finding the software vulnerability sequence which is most similar to the doubtful vulnerability sequence of the software to be tested from the software vulnerability clustering cluster; and finally, outputting related vulnerability information, in the software vulnerability sequence database, corresponding to the most similar software vulnerability sequence as a security report. The method improves the analysis efficiency of the software vulnerability sequence.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
Method and computer software product for genomic alignment and assessment of the transcriptome
InactiveUS20050244883A1Reduce quality problemsMicrobiological testing/measurementBiostatisticsGenome alignmentNucleic Acid Probes
In one embodiment of the invention, computerized methods are provided for analyzing transcript sequence clusters by aligning the transcripts with genomic sequences to determine whether a cluster needs to be sub-clustered and whether clusters should be merged. In addition, in some embodiments, transcript sequences are trimmed according to their alignment with their corresponding genomic sequences. The modified clusters and trimmed sequences may be used for nucleic acid probe array design.
Owner:AFFYMETRIX INC
Lens clustering method based on information bottleneck theory
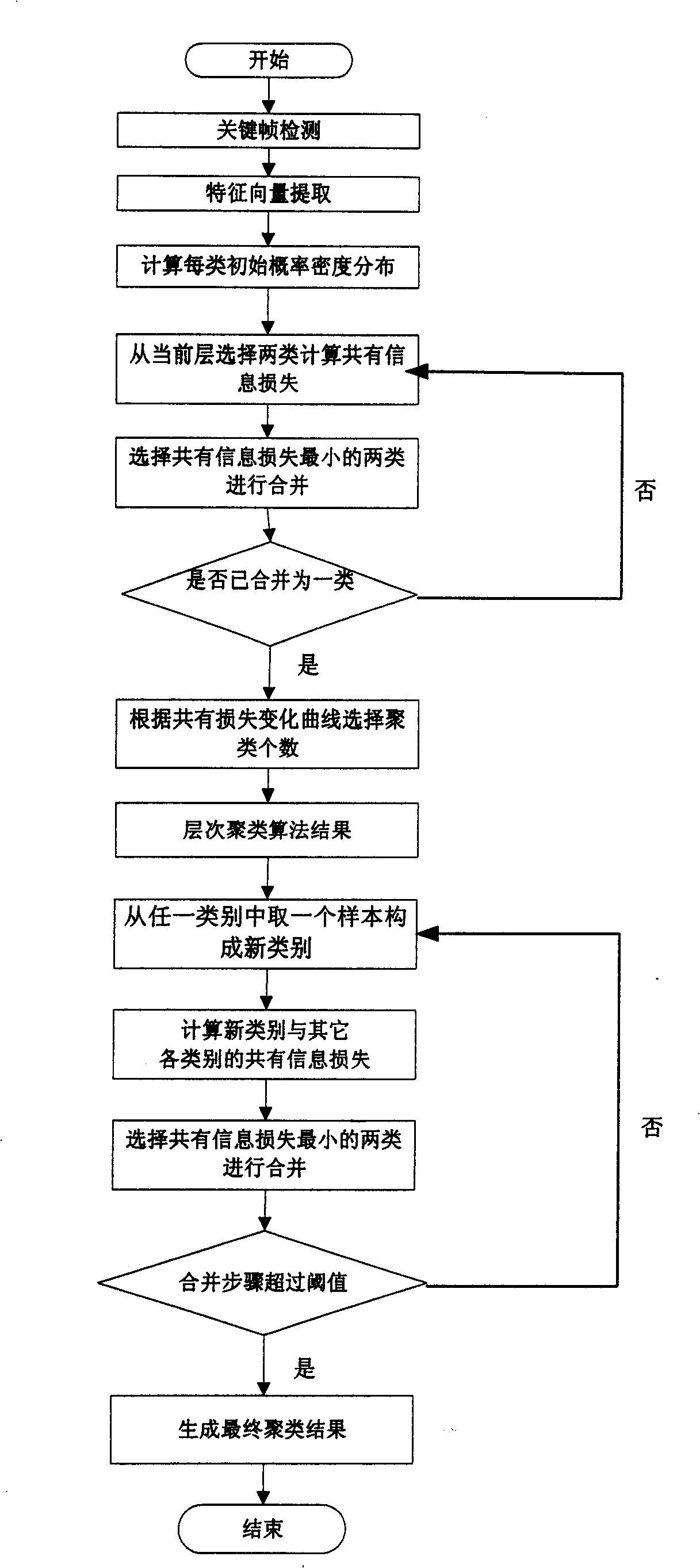
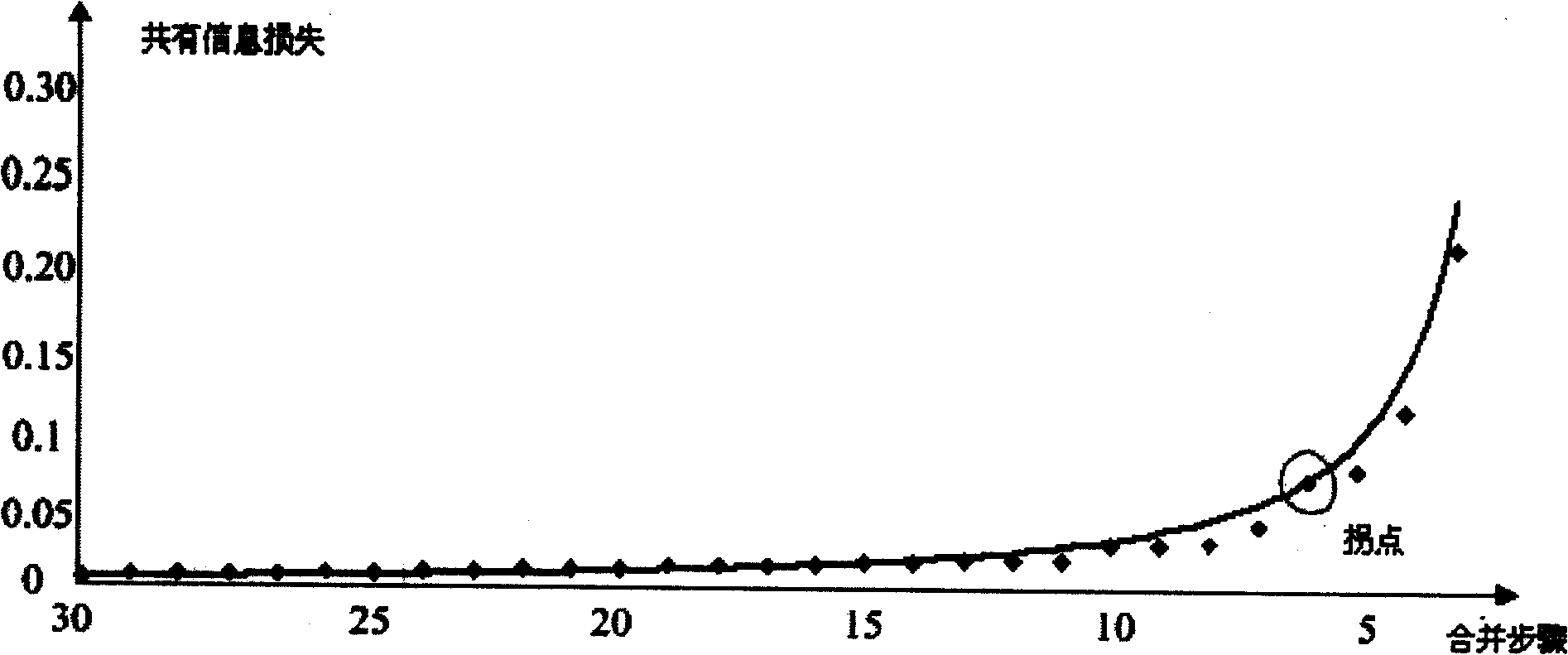
InactiveCN101271465ASolving optimal solution solving problemsAvoid estimationSpecial data processing applicationsLocal optimumSequence clustering
The invention relates to a lens clustering method based on an information bottleneck theory. The information bottleneck theory is used for the lens clustering. Every lens to be classified is initialized into one sort. Common information loss in a merging process is used as a measure for a category distance to implement the sort combination until all lenses are merged into one sort. The sort number corresponding to common information loss inflection points is used as the final sort number of the lens clustering. At the same time, in order to solve the problem of local optimal solution appearing in a hierarchical clustering, the classification result is regulated when combined with a sequence clustering method. The lens clustering method can apply the information bottleneck theory to the clustering method without estimating the number of the sort beforehand, thereby improving the precision and the recall ratio of the clustering results and avoiding the problem of local optical solution.
Owner:BEIHANG UNIV
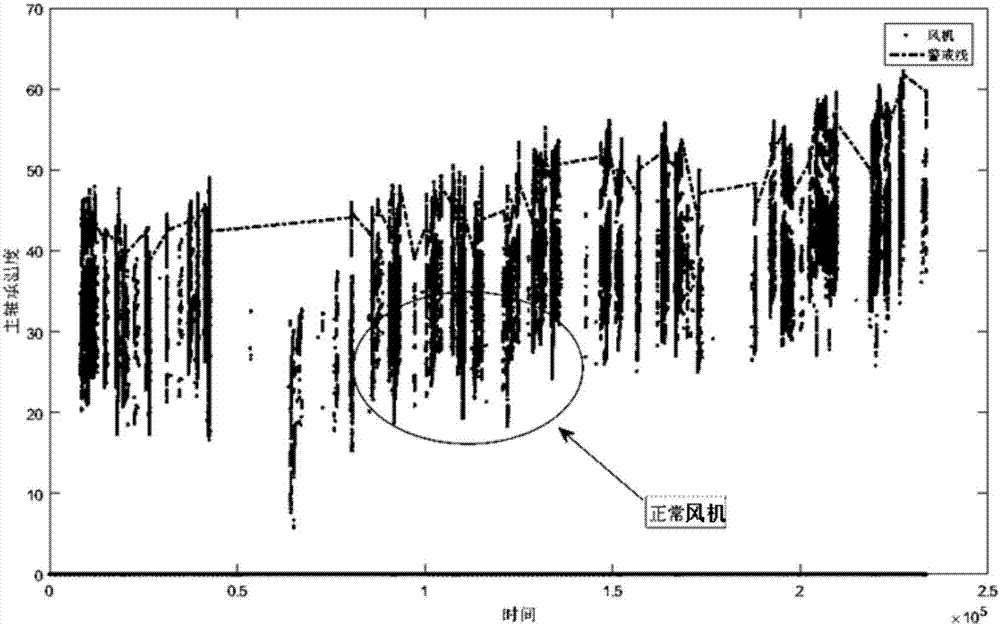
Method for diagnosing wind turbine main bearing fault based on temporal sequence clustering
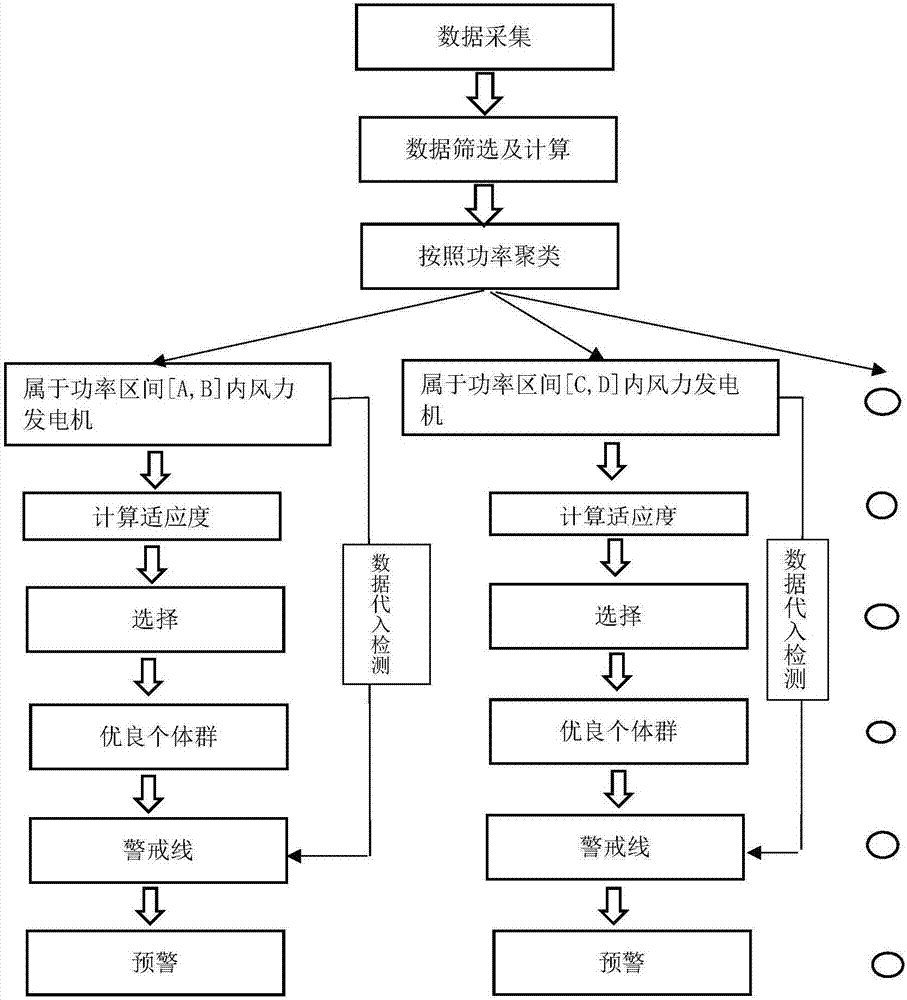
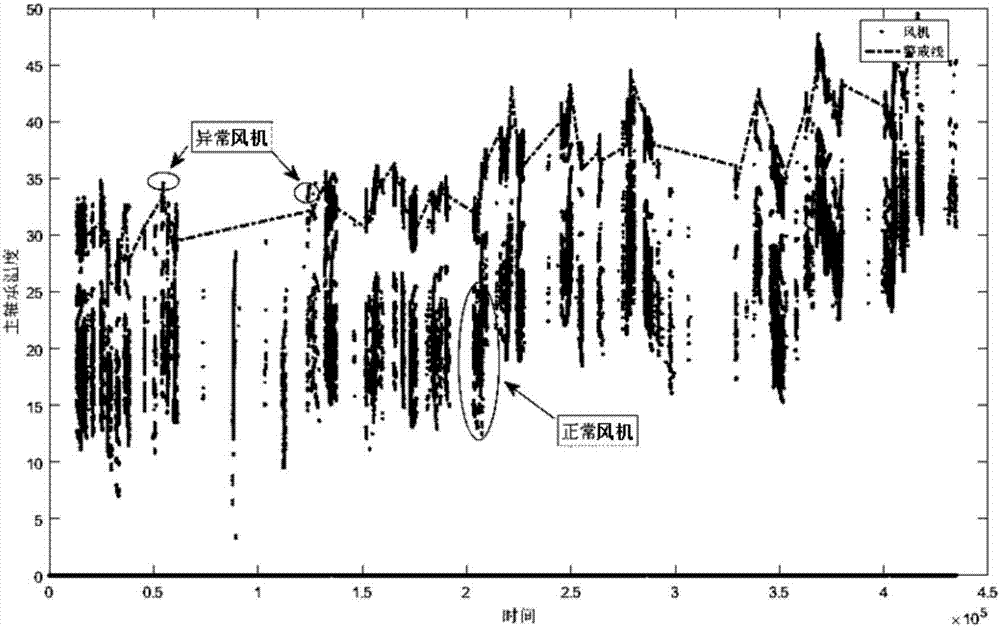
ActiveCN106870297AIncrease power generation rateImprove efficiencyEngine fuctionsWind motor combinationsGeneration rateEconomic benefits
The invention discloses a method for diagnosing a wind turbine main bearing fault based on temporal sequence clustering. The method comprises the following steps that step one, data (power data and main bearing temperature data) are collected, screened and calculated; step two, different power intervals are divided according power clustering, and all the power intervals are subjected to the flowing steps from step three to step seven; step three, fitness is evaluated; step four, good individual groups are selected; step five, a temperature datum line is obtained; step six, a temperature warning line is obtained; and step seven, the data are substituted for detection and early warning. According to the method, the wind turbine main bearing temperature is subjected temporal sequence power clustering and good individual group selection, whether a main bearing has an abnormal operation state or not is distinguished for diagnosis, the diagnosis result is reliable, the early warning capacity of the main bearing can be improved, manual troubleshooting is replaced by the data, targeted maintenance and defect elimination are achieved, the damage rate of the main bearing is decreased, the power generation rate and economic benefits of a wind turbine are increased.
Owner:GUODIAN UNITED POWER TECH
Method for analyzing safety property of software based on sequence clustering
InactiveCN101996292ASolve collection difficultiesQuality improvementComputer security arrangementsCluster algorithmSoftware bug
The invention relates to a method for analyzing the safety property of software based on sequence clustering. Based on reverse software bug analysis technology, the quality of a bug knowledge base and the analysis efficiency of software bugs are improved by collecting the conventional software bugs, preprocessing the software bugs, saving a processed software bug program operation sequence in a software bug sequence database, classifying the software sequences in the software bug sequence database by an integral sequence similarity-based clustering algorithm and saving the classified sequences in the bug knowledge base; and the accuracy of the software bug detection is improved by analyzing a suspected software bug sequence extracted from to-be-detected software, measuring similarity level between the sequences by using the logic distance-based similarity measurement and analyzing the software bug.
Owner:BEIJING INSTITUTE OF TECHNOLOGYGY
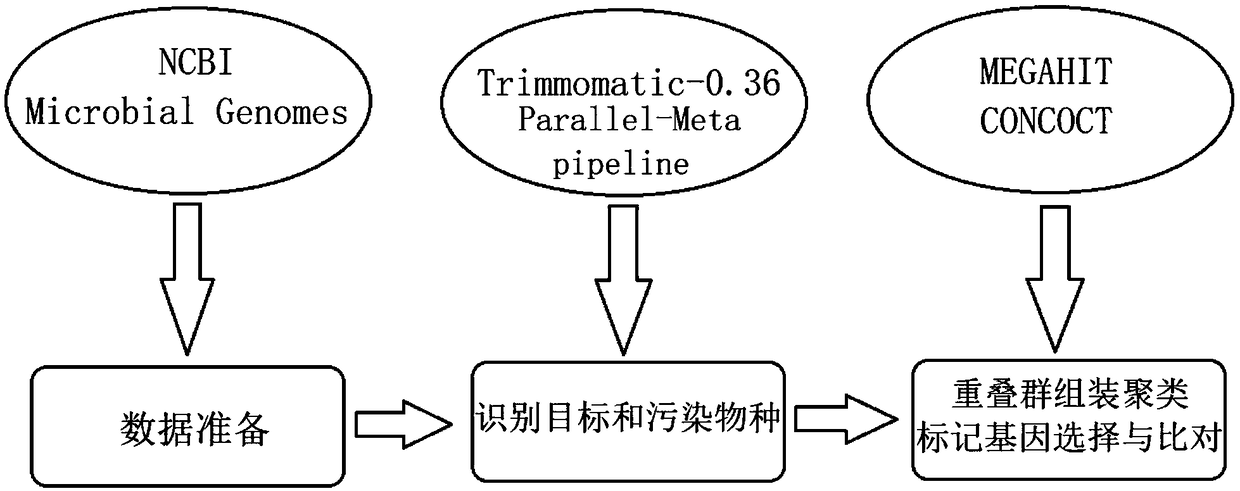
Microbial data processing method for high-throughput sequencing
The invention discloses a microbial data processing method for high-throughput sequencing. According to the method, contig assembling and binning are performed on microbial 16s RNA read segments of high-throughput sequencing; microbial contigs are marked with q-PCR, so that the microbial contigs comprise marker genes; biological contigs containing the marker gene are removed, so that high-qualitymicrobial metagenomic sequencing data are obtained. Sequence clustering and other methods are adopted to identify and remove sequences from pollutants, so that the microbial metagenomic sequencing data with higher purity can be obtained, and therefore, gene expression results based on the microbial metatranscriptomic sequencing data are more accurate. The method of the invention, with the microbial metagenomic sequencing data as a research object, can improve the quality of the microbial metagenomic sequencing data based on bioinformatics ideas.
Owner:EZHOU INST OF IND TECH HUAZHONG UNIV OF SCI & TECH +1
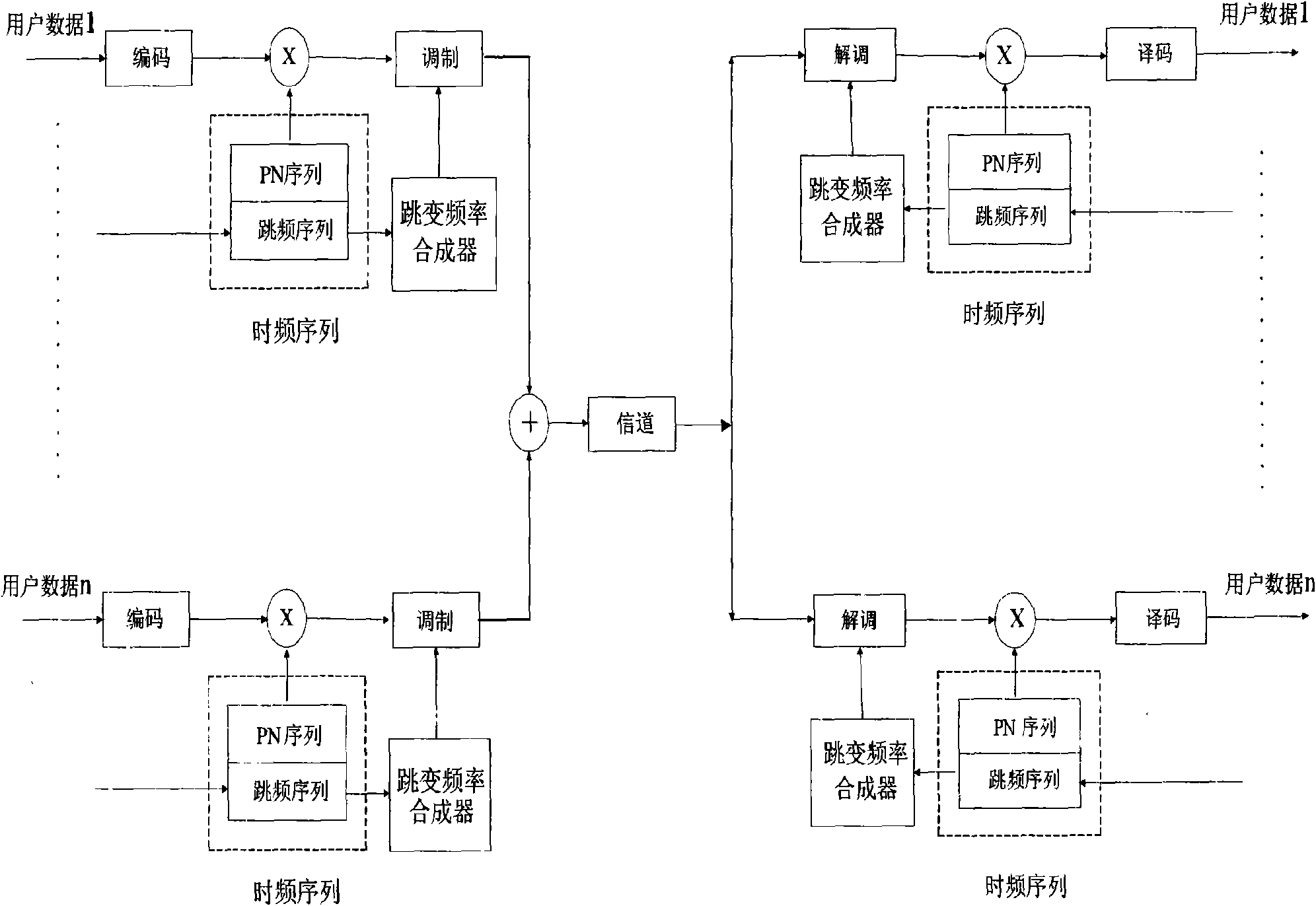
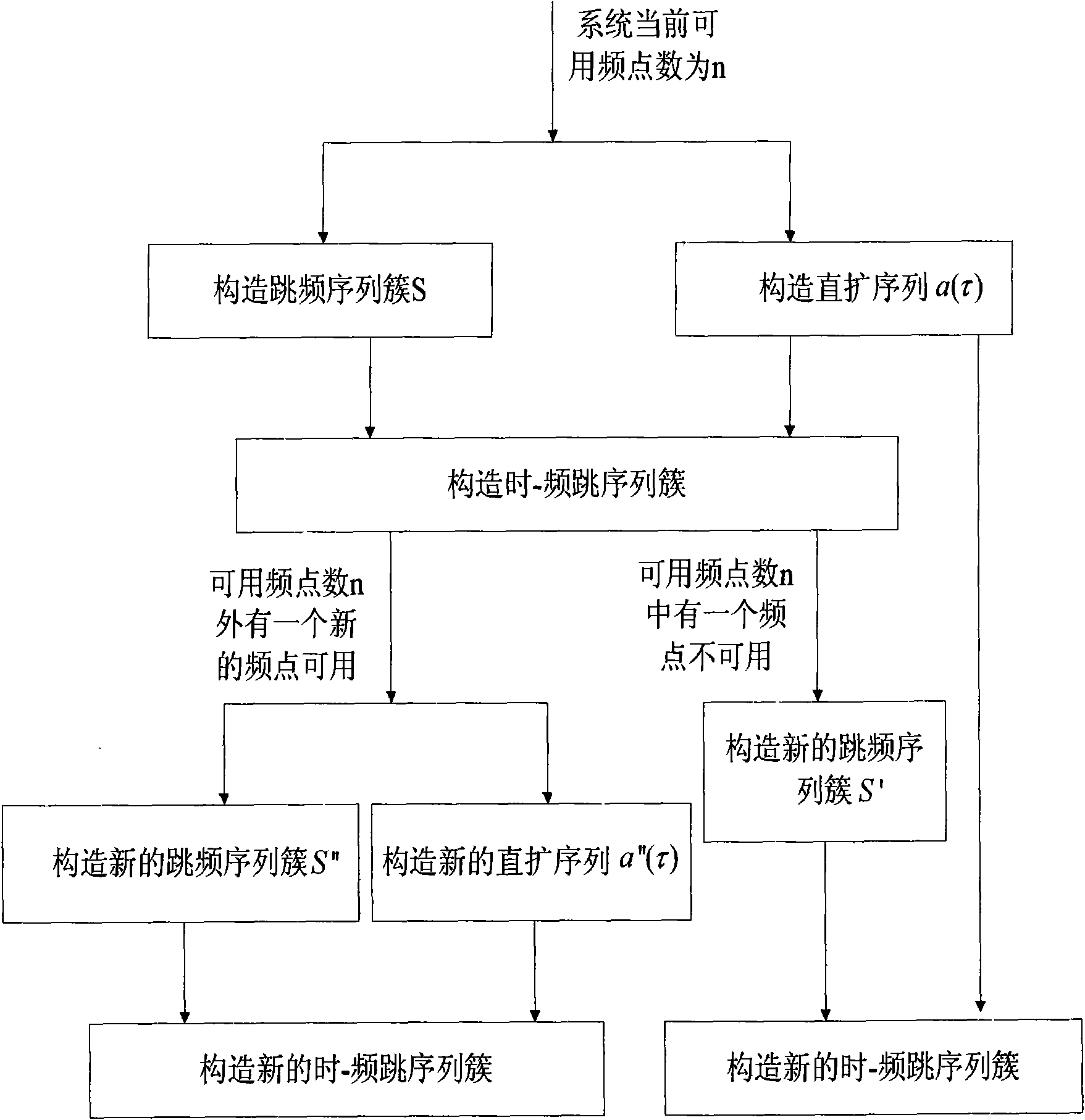
Method for constructing time-frequency hop sequences in cognitive radio TFH-CDMA system
InactiveCN101645725AIncrease the number ofLarge anti-multiple access interference intervalCode division multiplexTransmissionFrequency spectrumTelecommunications
The invention provides a method for constructing time-frequency hop sequence clusters in a cognitive radio TFH-CDMA system. The method comprises the following constructing processes: firstly, constructing q optimal hop frequency sequence clusters with the length of L according to the current available frequency point n of the system; then, constructing L direct expansion sequences with the lengthof L, forming one time-frequency hop sequence by any one pair of arbitrary hop frequency sequences and direct expansion sequences and constructing time-frequency hop sequence clusters with the numberof Lq; and constructing corresponding hop frequency sequences when increasing or reducing the number of the available frequency points of the system, and then reconstructing direct expansion sequences with the length equivalent to that of the hop frequency sequences, thereby generating novel time-frequency hop sequence clusters. The time-frequency hop sequence clusters constructed by the invention have the advantages of much number of the sequences, large impact-free interval and high utilization rate of frequency spectra and can be directly applied to a TFH-CDMA communication system based oncognition.
Owner:XIDIAN UNIV
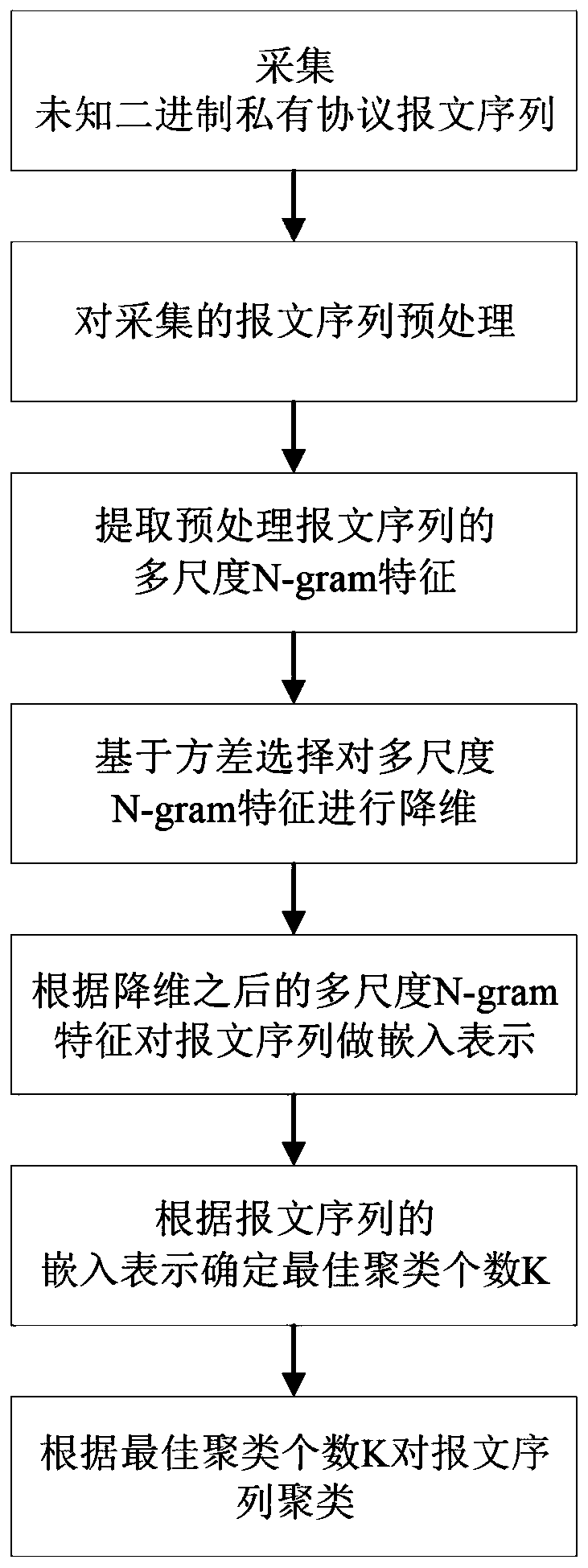
Message sequence clustering method of unknown binary private protocol
ActiveCN109951464AOvercoming the Embedding Representation Problem of Unequal LengthsFully mine semantic informationCharacter and pattern recognitionTransmissionGramDimensionality reduction
The invention discloses a message sequence clustering method of an unknown binary private protocol, and mainly solves the problem that similarity between protocol message sequences cannot be accurately measured in a protocol reverse process in the prior art. The implementation scheme comprises the following steps: 1) collecting an unknown binary private protocol message sequence; 2) preprocessingthe collected message sequence; 3) extracting multi-scale N-gram features of the preprocessed message sequence; 4) carrying out dimension reduction on the multi-scale N-gram features based on varianceselection; 5) according to the multi-scale N-gram features after dimension reduction, obtaining a multi-scale N-after dimension reduction; carrying out embedded representation on the message sequenceby the gram feature; 6) determining the optimal clustering number K according to the embedded representation of the message sequence, and 7) clustering the message sequence according to the optimal clustering number K. According to the method, the potential semantic information of the message sequence is fully mined, the similarity between the message sequences can be accurately measured, the clustering accuracy is improved, and the method can be used for clustering unknown binary private protocols.
Owner:南京赛宁信息技术有限公司
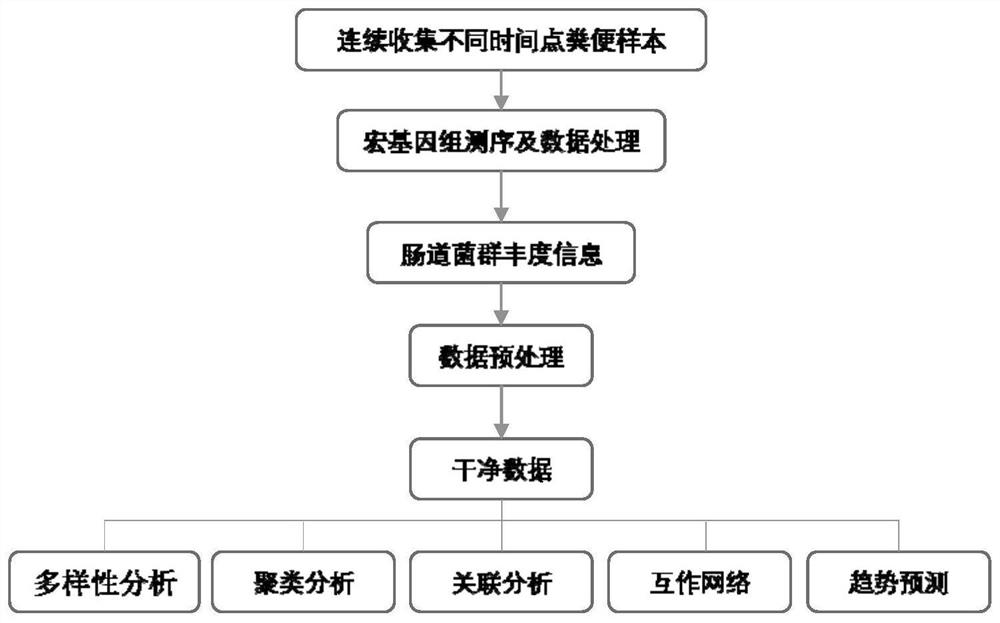
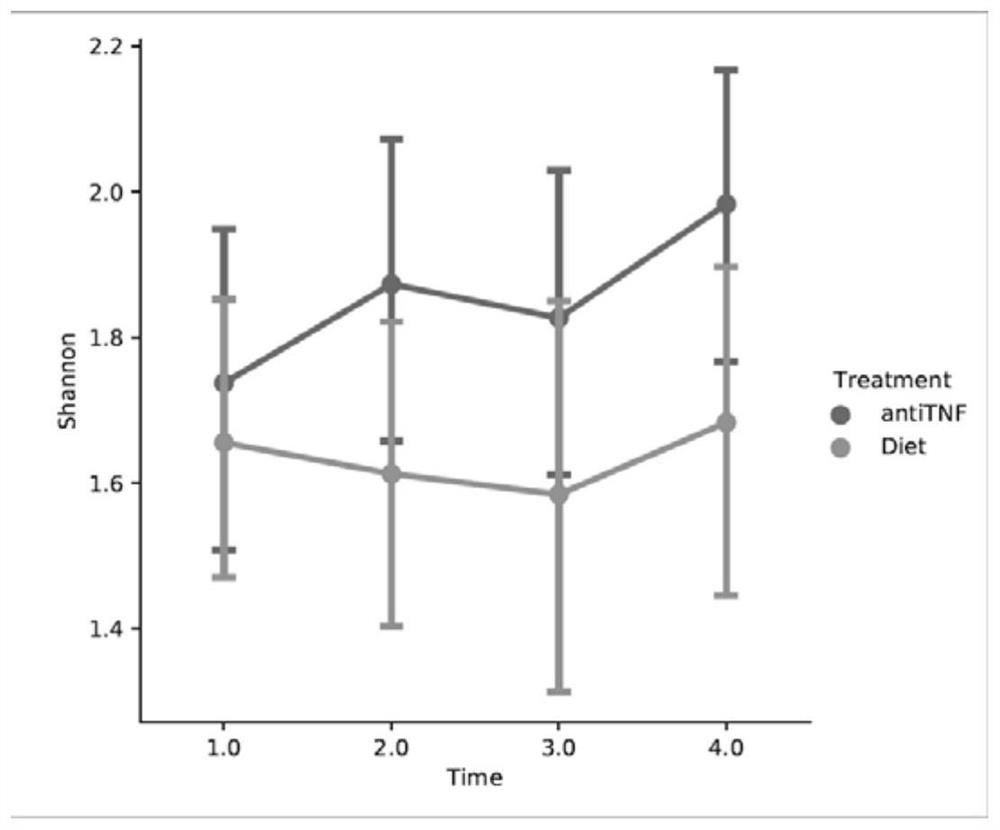
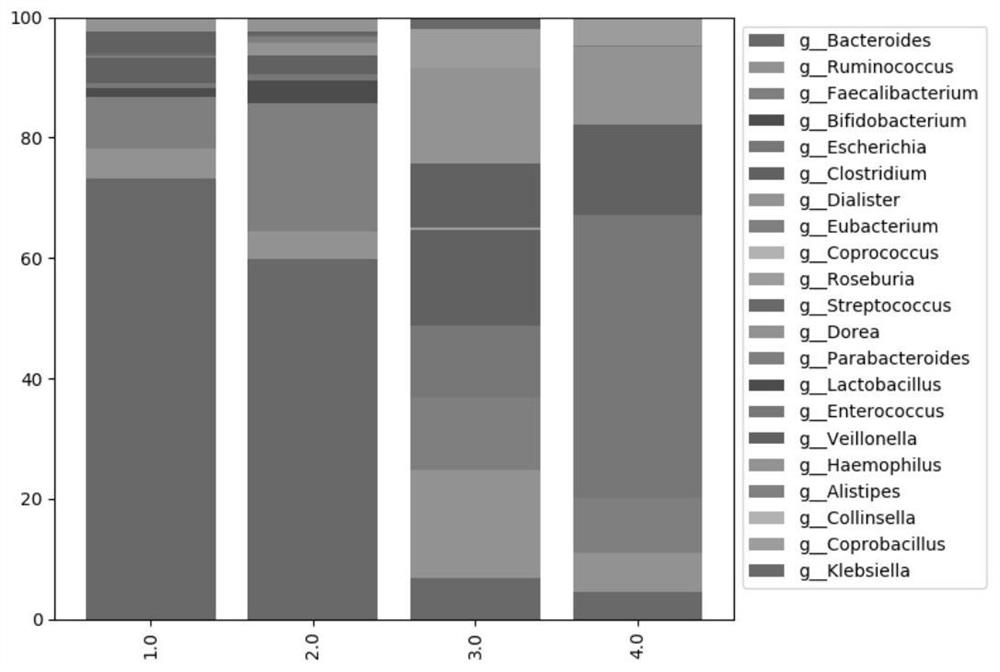
Multi-time-sequence intestinal flora data analysis process control method
ActiveCN112151118AImprove scientific research work efficiencyReduce research costsHealth-index calculationData visualisationEngineeringSequence clustering
The invention discloses a multi-time-sequence intestinal flora data analysis process control method. The analysis process mainly comprises the following stages: sample acquisition, intestinal flora data preprocessing, diversity analysis, (sequential sequence) clustering analysis, correlation analysis, bacterial colony interaction network construction and single strain change trend (sequence) prediction. A user inputs a file and corresponding parameters according to the requirements of a process file, and the system automatically analyzes data and outputs the corresponding file and a visualization result. Scientific researchers, including researchers who do not understand data analysis, can efficiently complete a set of standardized intestinal flora data analysis process based on a time sequence, and a final result is obtained. Therefore, the purposes of improving scientific research work efficiency and reducing scientific research cost are achieved.
Owner:康美华大基因技术有限公司
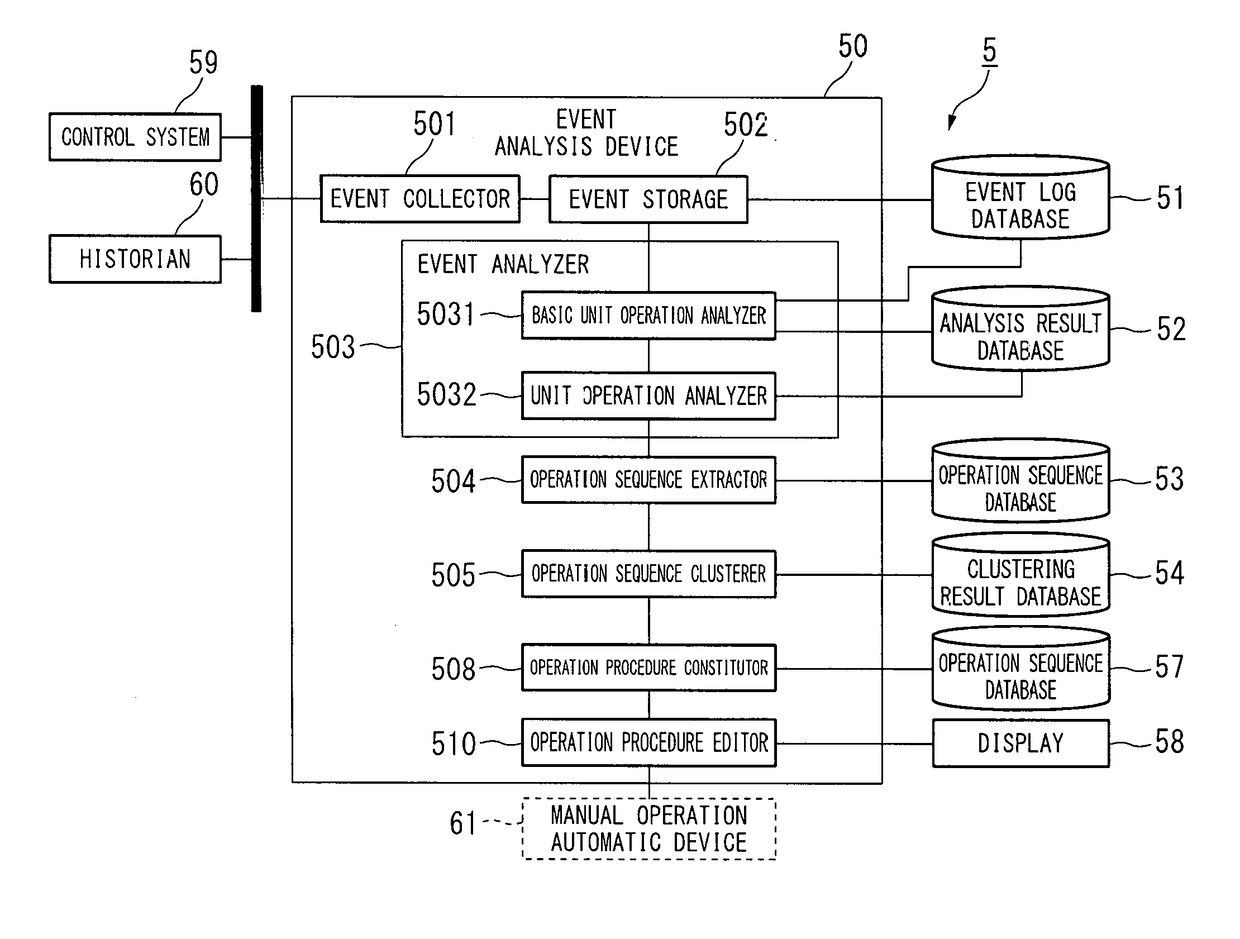
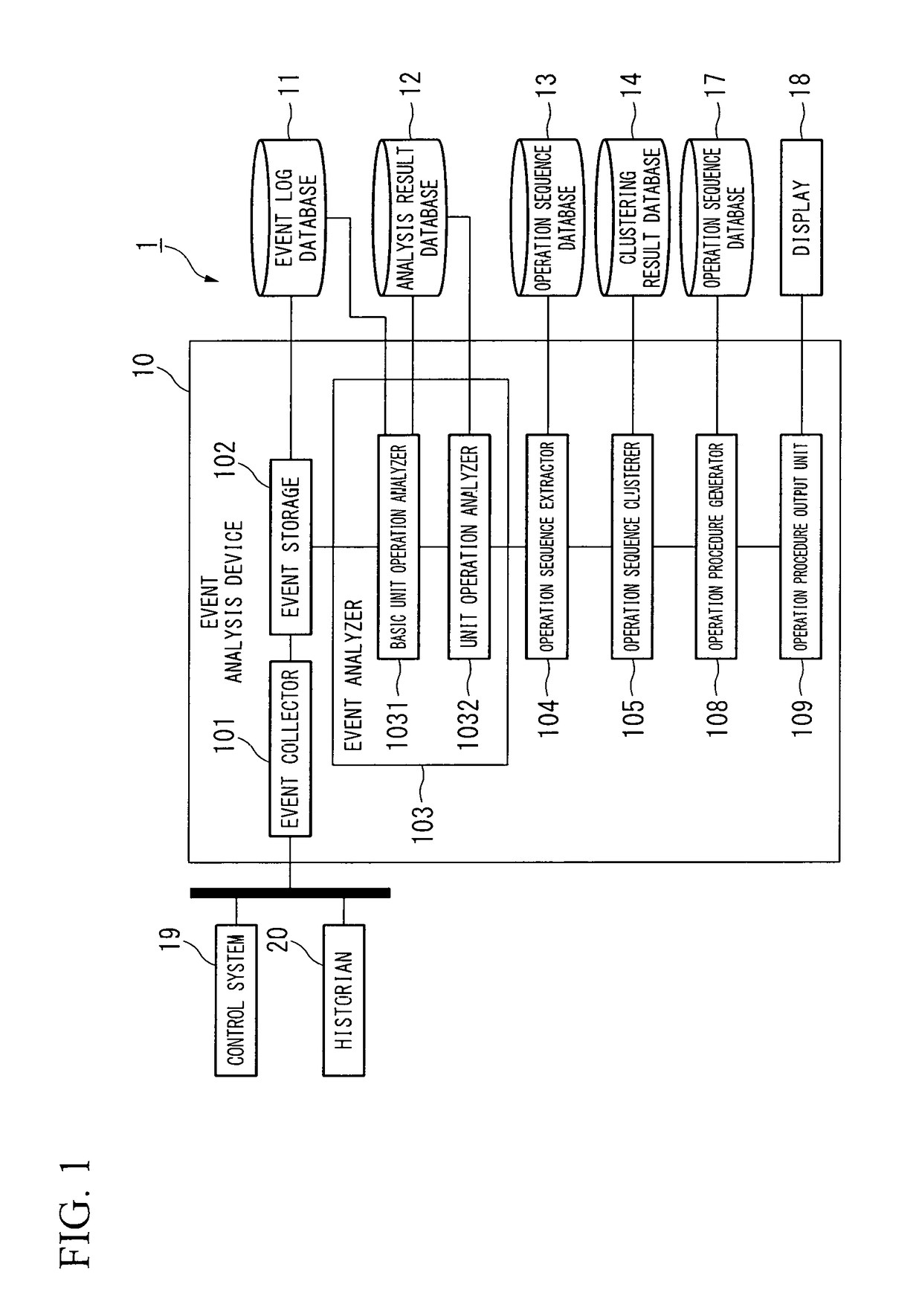
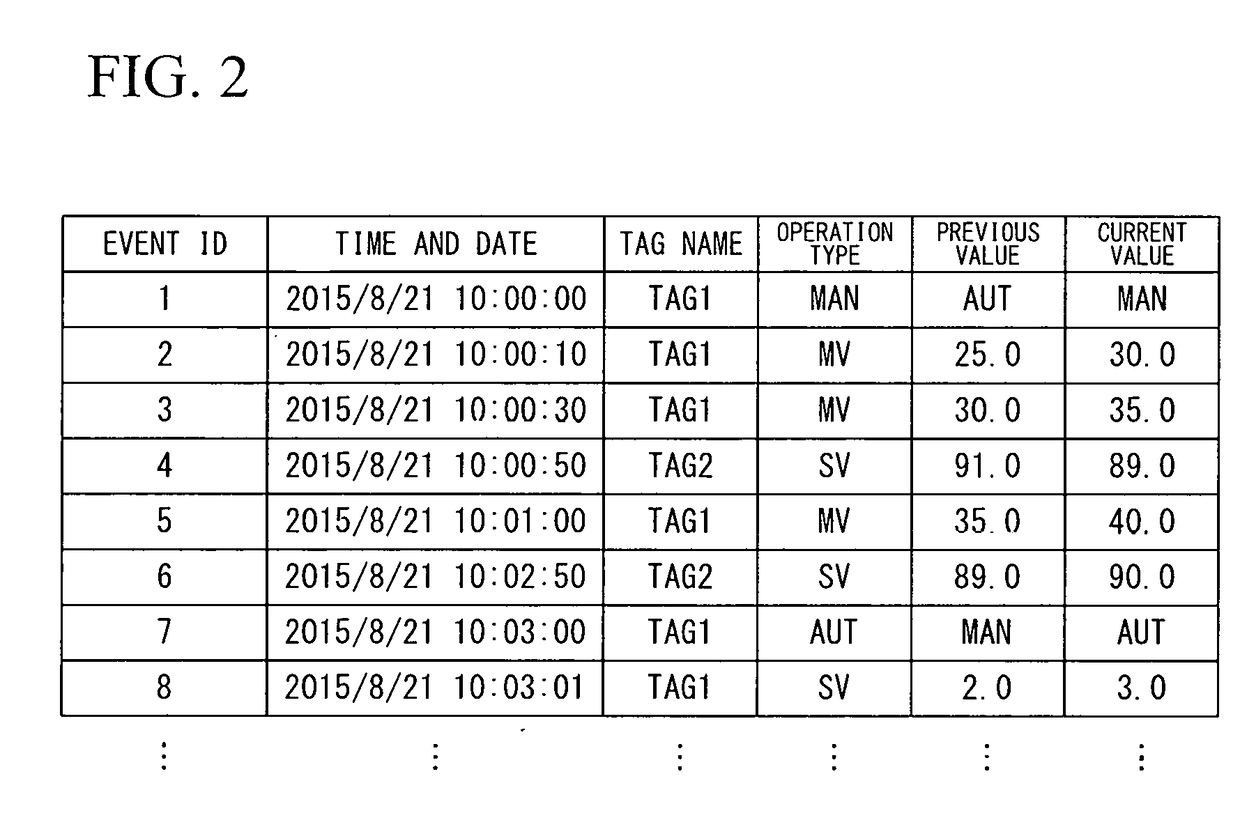
Event analysis device, event analysis system, event analysis method, and event analysis program
An event analysis device having an event collector for collecting event log data representing an operation history by a DCS operator; an event analyzer for analyzing the event log data, and extracting basic unit operations or unit operations representing an operation method based on operations of the DCS operator or an operation intention based on operations of the DCS operator; an operation sequence extractor for extracting operation sequences which the basic unit operations or the unit operations are aligned in accordance with time order in every service time period; an operation clusterer for clustering the operation sequences based on similarity among the operation sequences extracted in every service time period; and an operation procedure generator for analyzing the operation sequences clustered in same type, and estimating a structure of the operation procedure based on the operation of the DCS operator.
Owner:YOKOGAWA ELECTRIC CORP
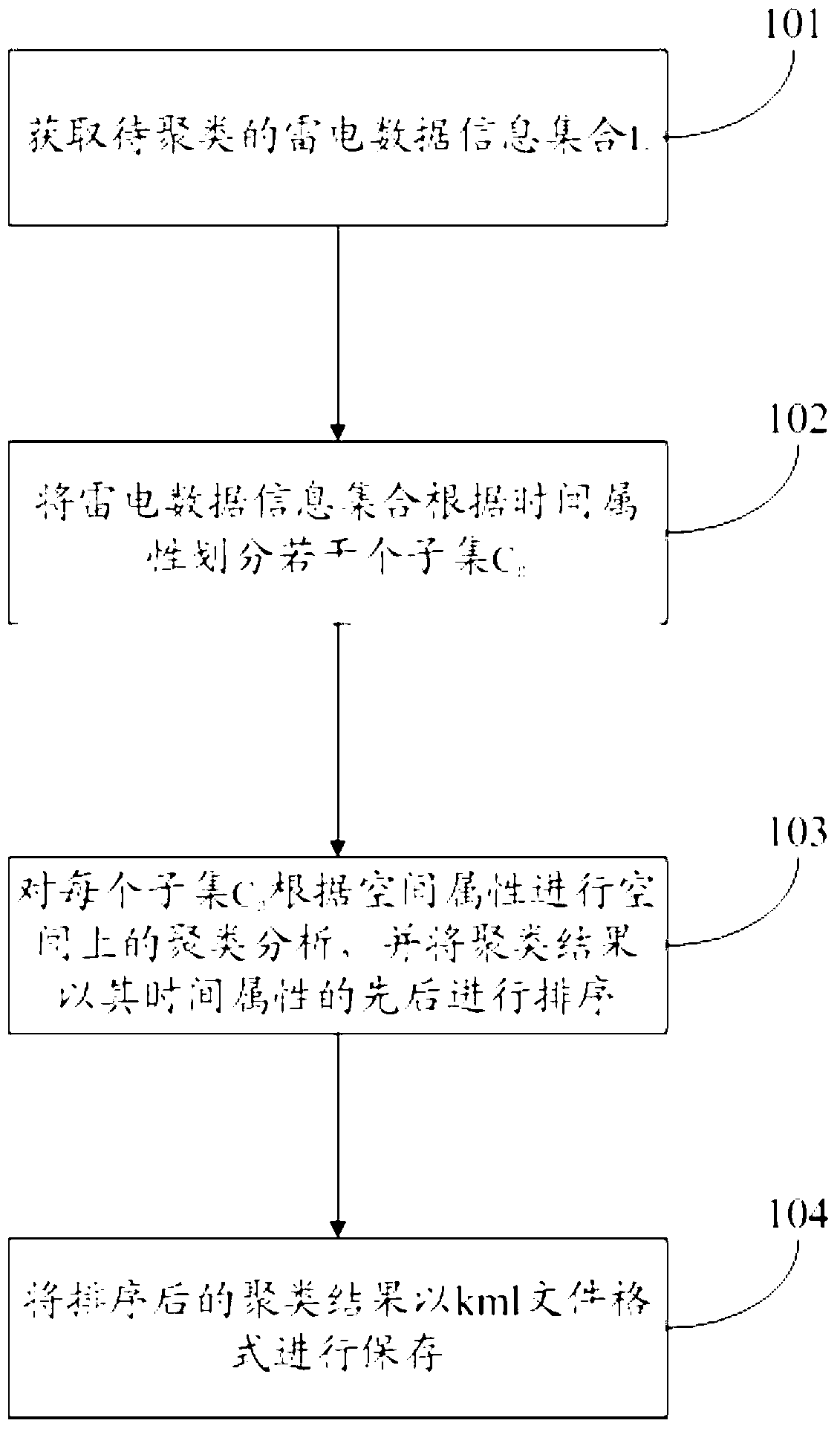
Method for realizing thunder and lightning space-time clustering
InactiveCN103279572AOvercoming elusive technical issuesFast convergenceSpecial data processing applicationsLightning strikeData information
The invention discloses a method for realizing thunder and lightning space-time clustering, belonging to the technical field of lightning prevention. The method comprises the steps of: obtaining a thunder and lightning data information collection L to be clustered; dividing the thunder and lightning data information collection into a plurality of sub-collections Cn based on time attribute; performing spatial clustering analysis on each sub-collection Cn based on spatial attribute, and sequencing clustering results according the sequence of the time attribute; and storing the sequenced clustering results in a km1 file format, wherein n is not less than 1. The method for realizing thunder and lightning space-time clustering overcomes the technical problem that a discharge centre is difficult to make a decision due to discreteness of thunder and lightning data in the prior art (decision made by the thunder and lightning centre is affected by edge thunder and lightning), and has the characteristics of fast rate of convergence and high clustering accuracy.
Owner:JIANGMEN POWER SUPPLY BUREAU OF GUANGDONG POWER GRID +1
File clustering method based on information bottleneck theory
InactiveCN101571868AImprove accuracyClustering implementationSpecial data processing applicationsSequence clusteringMachine learning
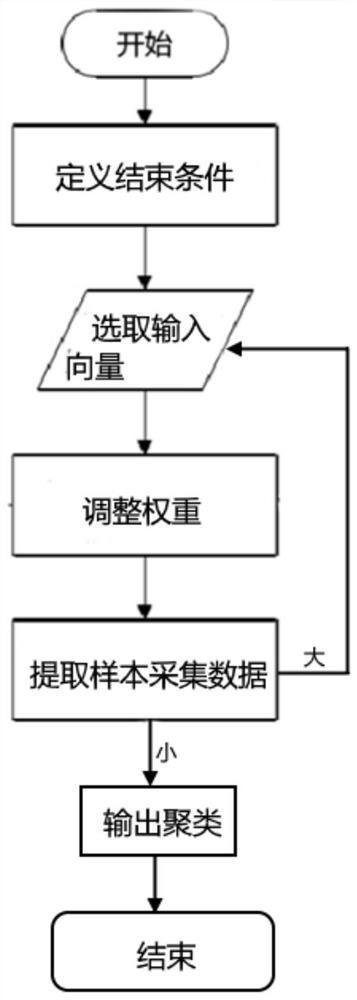
The invention discloses a file clustering method based on an information bottleneck theory. The method firstly utilizes the information bottleneck theory to calculate the similarity between files; increment clustering algorithm is used for clustering files; minimum shared information loss is calculated on clustering result; if the minimum shared information loss satisfies a set threshold, the file is combined with the nearest cluster, otherwise a new cluster is created to store the file. Sequence clustering method is adopted for adjusting the clustering result to improve clustering accuracy, each file is sampled in sequence during adjusting process, and sampling frequency is set to control adjusting intensity. The adjusting policy contains all sample files and contributes to improving clustering accuracy.
Owner:BEIHANG UNIV
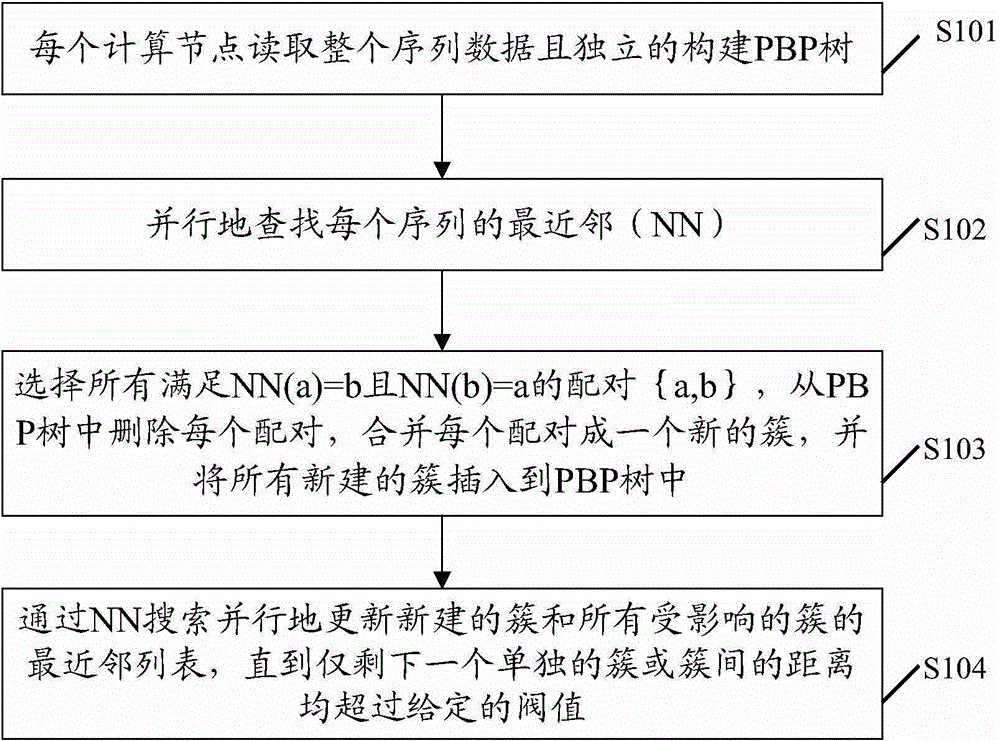
Sequence clustering method and device
InactiveCN104537279AEfficient and accurate processingStrong scalabilitySpecial data processing applicationsNODALTechnical standard
The embodiment of the invention discloses a sequence clustering method. The method comprises the steps that each computing node reads whole sequence data and builds a PBP tree independently; the nearest neighbour (NN) of each sequence is searched for concurrently; all pairs (a, b) meeting NN(a)=b and NN(b)=a are selected; each pair is deleted from the PBP tree and is combined into a new cluster, and all the newly-built clusters are inserted into the PBP tree; the newly-built clusters and all affected NN lists of the clusters are updated concurrently through NN searching until only one cluster is left or cluster distance exceeds a given threshold value. The embodiment of the invention further discloses a sequence clustering device. By the adoption of the sequence clustering method and device, hierarchical clustering of millions of sequences can be processed efficiently and accurately, the clustering result equivalent to standard hierarchical clustering is achieved, and the expansibility is good.
Owner:SHENZHEN INST OF ADVANCED TECH CHINESE ACAD OF SCI
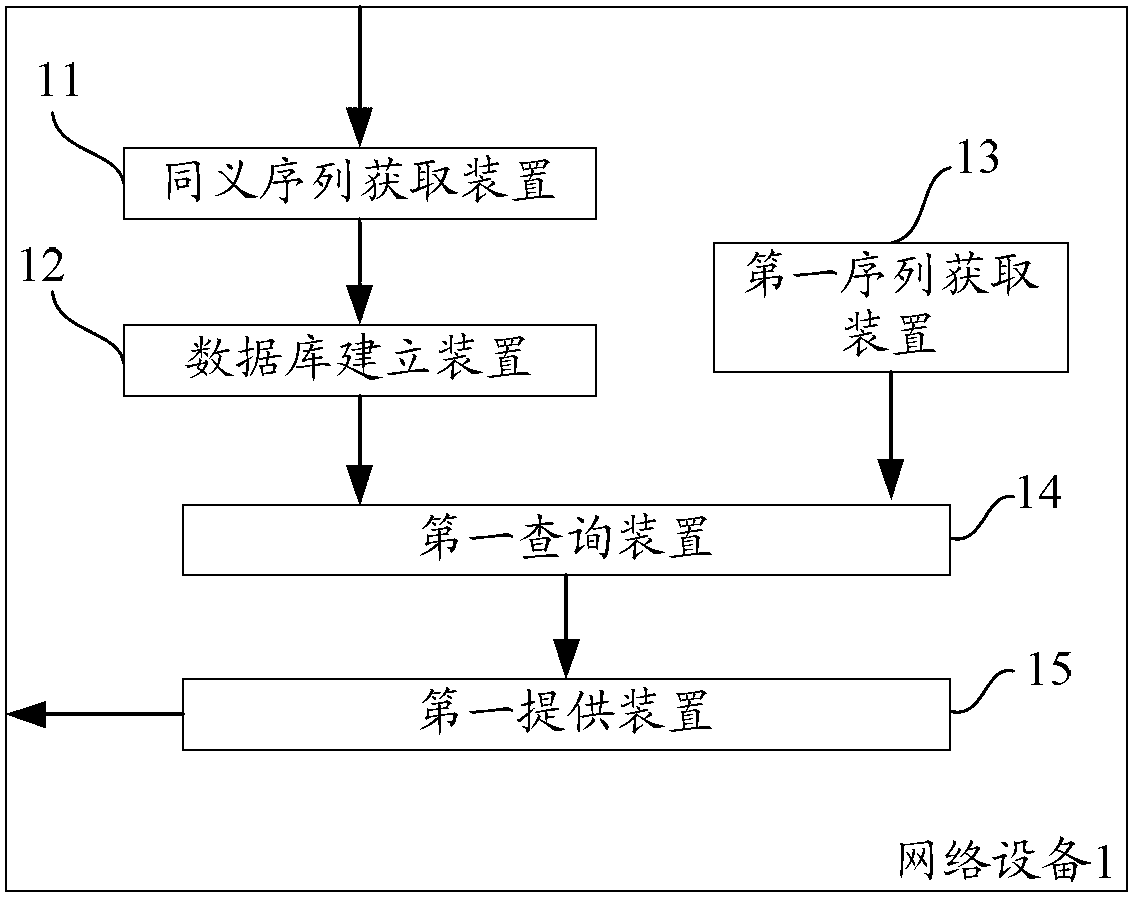
Method and equipment used for obtaining search results
InactiveCN103235784ACovering Search NeedsImprove the search experienceSpecial data processing applicationsUser inputSequence database
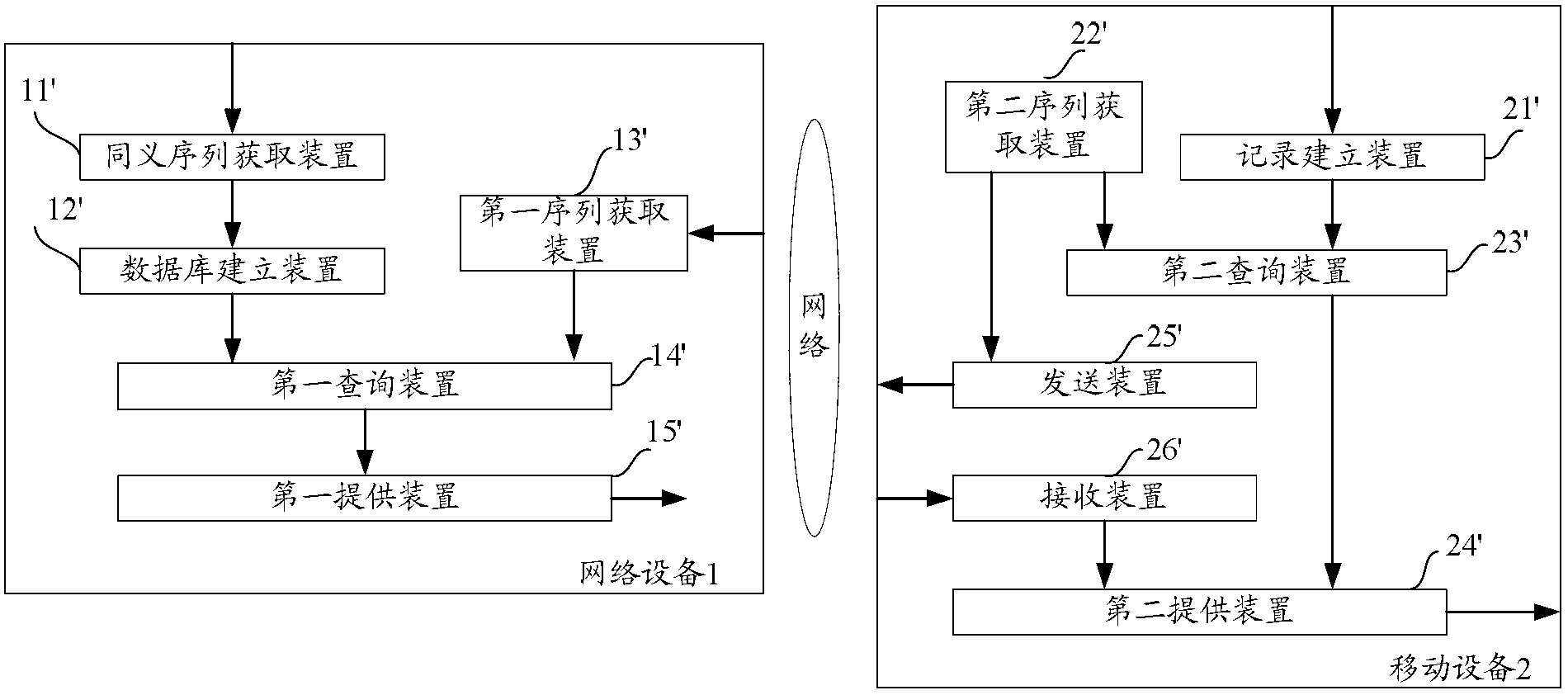
The invention aims at providing a method and equipment used for obtaining search results. Particularly, the method comprises the steps as follows: obtaining one or more synonymous sequence clusters according to a plurality of search logs; creating or updating a synonymous sequence database according to one or more synonymous sequence clusters; obtaining a target query sequence of a user; carrying out match query in the synonymous sequence database according to the target query sequence to obtain a target synonymous sequence cluster corresponding to the target query sequence; and providing a group of optimized search results corresponding to the target synonymous sequence cluster to the user. Compared with the prior art, the synonymous sequence database is created or updated through the synonymous sequence clusters obtained according to the search logs, the match query operation is carried out in the synonymous sequence database according to the target query sequence input by the user to obtain the target synonymous sequence cluster, and the group of optimized search results corresponding to the target synonymous sequence cluster are provided to the user, so that the search demands of the user are met and the information obtaining efficiency of the user is improved.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
Harmonic anomaly identification method based on variable point segmentation and sequence clustering
PendingCN111611961ACompliant with harmonic operationCharacter and pattern recognitionPattern recognitionSequence clustering
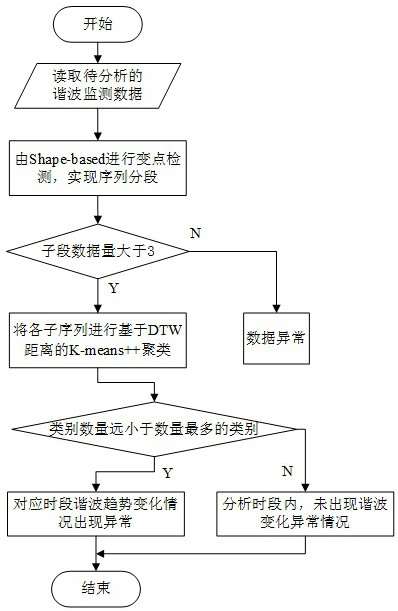
The invention relates to a harmonic anomaly identification method based on variable point segmentation and sequence clustering. A change point of harmonic monitoring statistical data in a long-term operation process is detected; the monitoring data sequence is segmented through each local variable point of the data to reflect harmonic state change points under an actual system, clustering based ona distance function for measuring form similarity is carried out on each section of sequence to obtain a form type of each section of sequence, so that identification of abnormal types is realized, and subsequent analysis of causes and governance of abnormal mechanisms are facilitated.
Owner:FUZHOU UNIV
Protein family phylogenetic analysis method based on amino acid sequence alignment
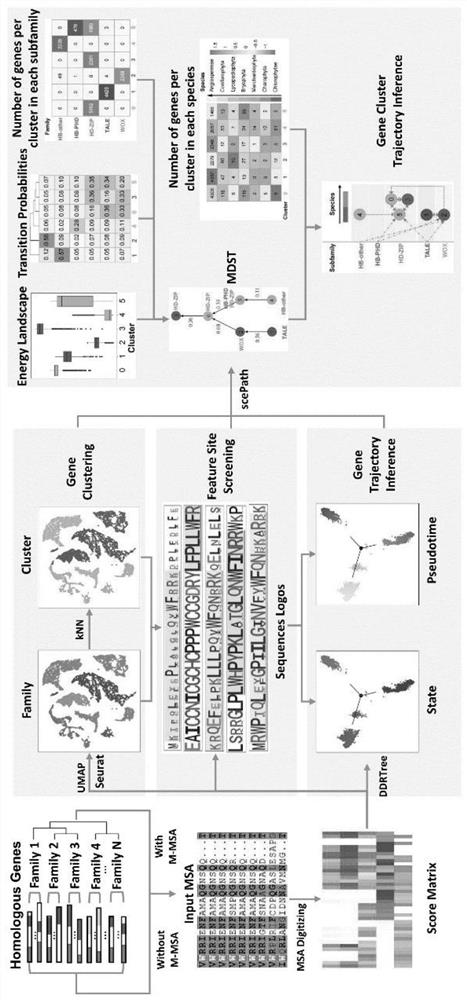
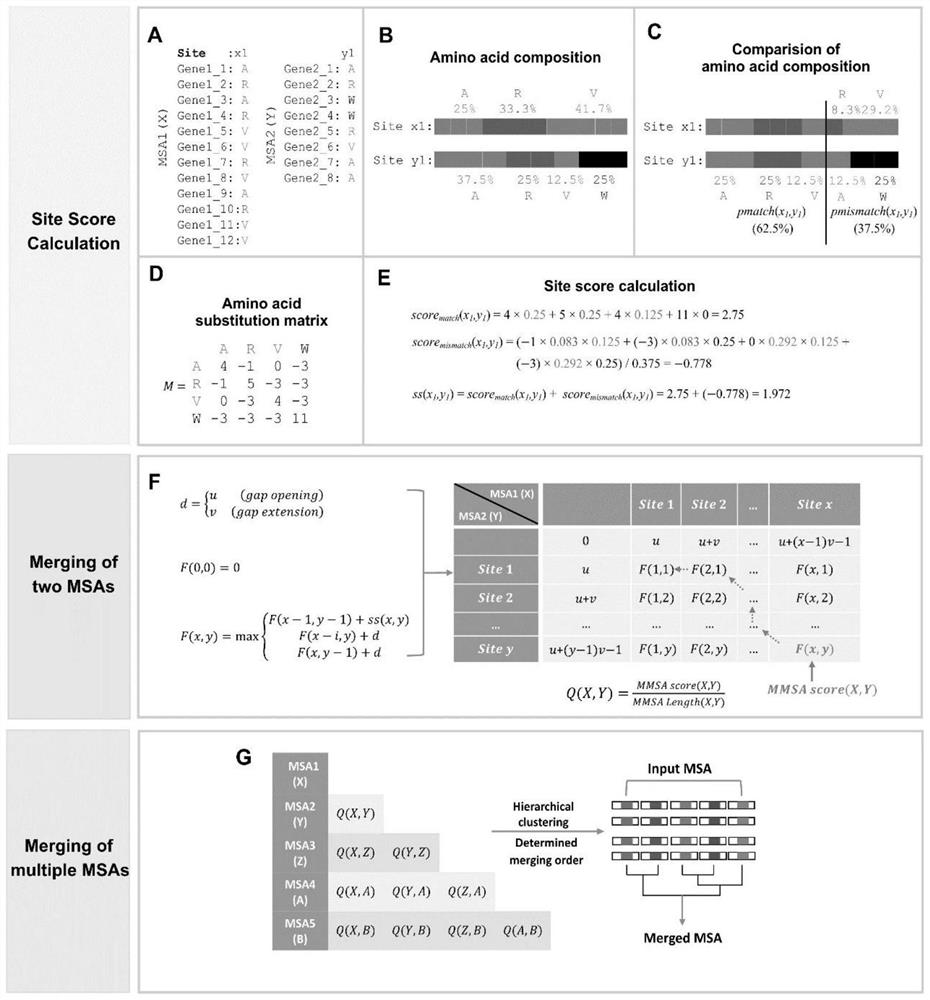
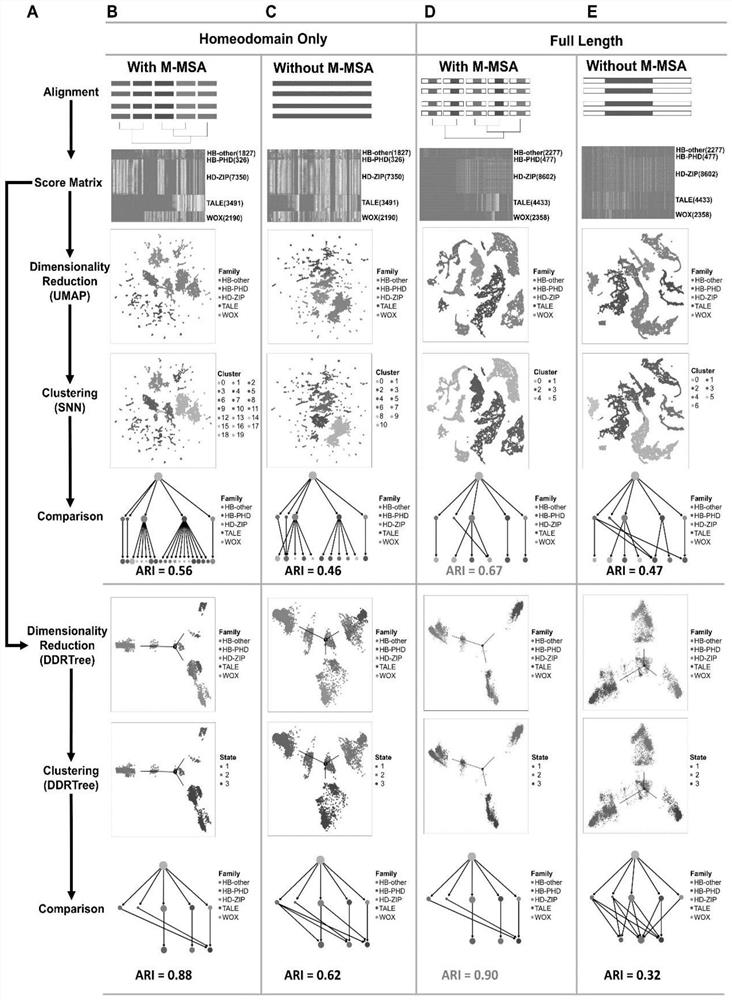
PendingCN114882949AEnsure cluster stabilityClustering is fastCharacter and pattern recognitionProteomicsAmino acid sequence alignmentGene cluster
The invention discloses a protein family phylogenetic analysis method based on amino acid sequence alignment, which comprises the following steps: obtaining a combined multi-sequence alignment result based on an amino acid sequence alignment fusion method; digitizing a combined multi-sequence comparison result, and constructing a fractional matrix; performing dimension reduction and clustering processing on the fractional matrix to obtain an input sequence; identifying a specific site and a conserved site of the input sequence; performing quasi-time analysis on the input sequence to obtain a track sequence of the input sequence; and obtaining a development trajectory of the input sequence based on the trajectory sorting. According to the method, fractional matrix construction and dimension reduction analysis are carried out through the sequence site features, so that the clustering and evolutionary relationship between gene families is deduced, the sequence gene clustering speed is effectively increased under the condition that the sequence clustering stability is guaranteed, and a new tool and method are provided for gene phylogenetic analysis and development trajectory analysis.
Owner:HUAZHONG AGRI UNIV
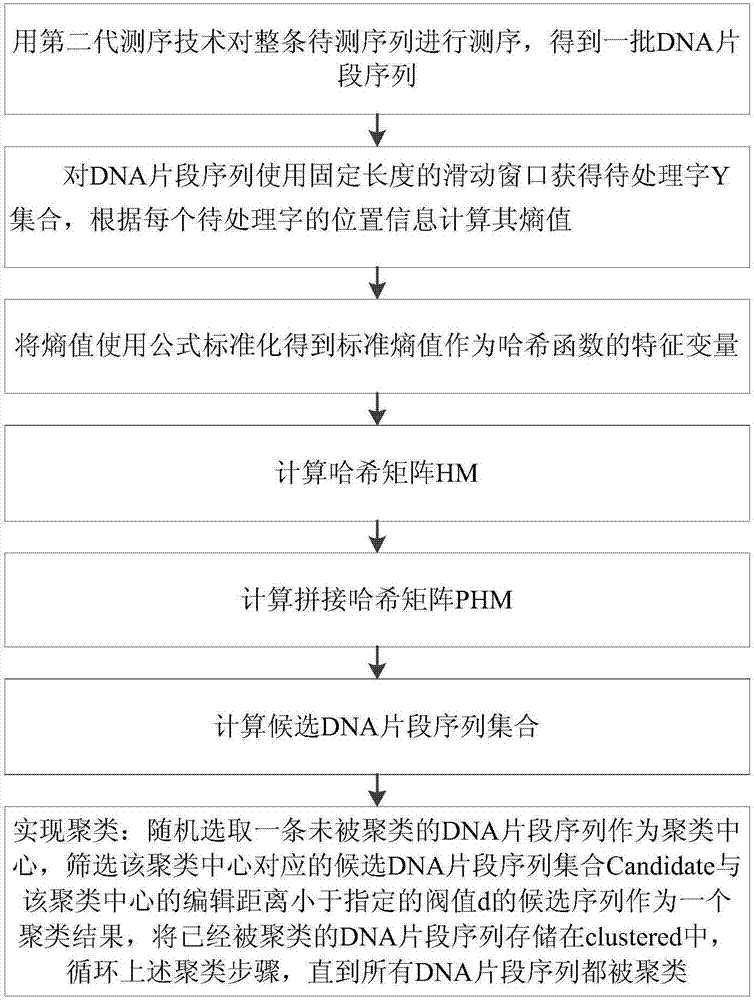
DNA sequence cluster of Locality Sensitive Hashing based on standard entropy
InactiveCN107103206AShorten comparison timeAvoid lossCharacter and pattern recognitionHybridisationGramCharacteristic space
The invention discloses a DNA sequence cluster of a Locality Sensitive Hashing based on standard entropy. The method comprises the steps of mapping an original DNA sequence according to an L-Gram model, calculating a matrix constituted by LF entropy values of N pieces of sequences to obtain the standard entropy of the matrix, using the Locality Sensitive Hashing to conduct Hashing mapping on the standard entropy to obtain a candidate set of DNA fragment sequences, and calculating DNA fragment sequences of which the editing distance is shorter than d in the candidate set to obtain a cluster result. According to the DNA sequence cluster of the Locality Sensitive Hashing based on the standard entropy, the situation that enough original DNA information is included in a converted characteristic space is taken into full consideration, missing of the DNA information is avoided, each fragment of the DNA sequences is turned into a new space, a candidate DNA fragment sequence set of each piece of DNA fragment sequences is calculated, and thus the operation speed can be increased, and the operation precision can be improved.
Owner:FUJIAN NORMAL UNIV
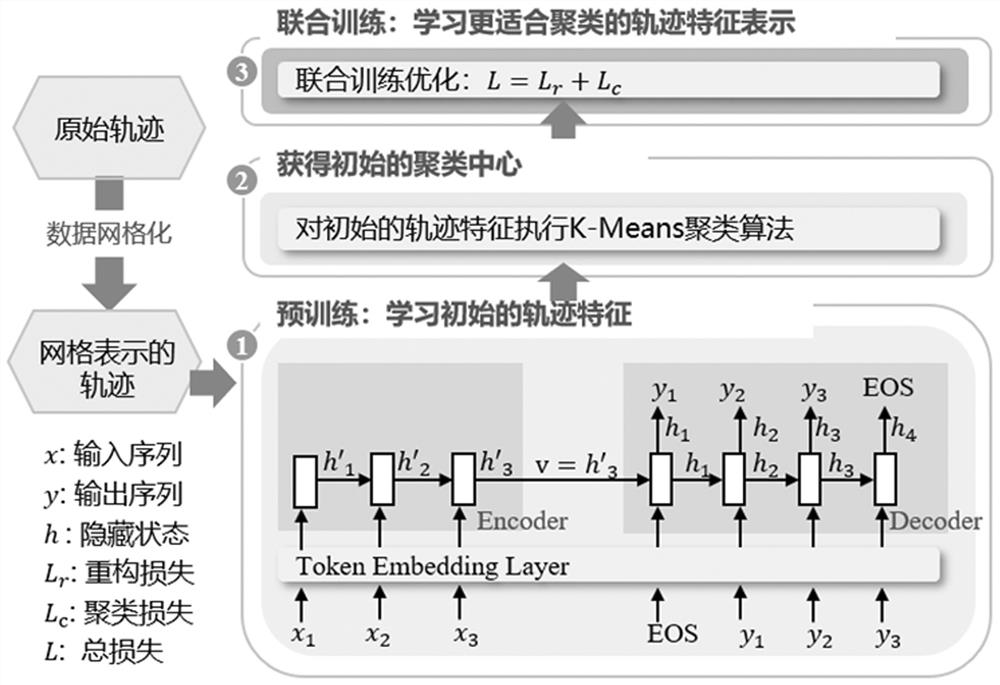
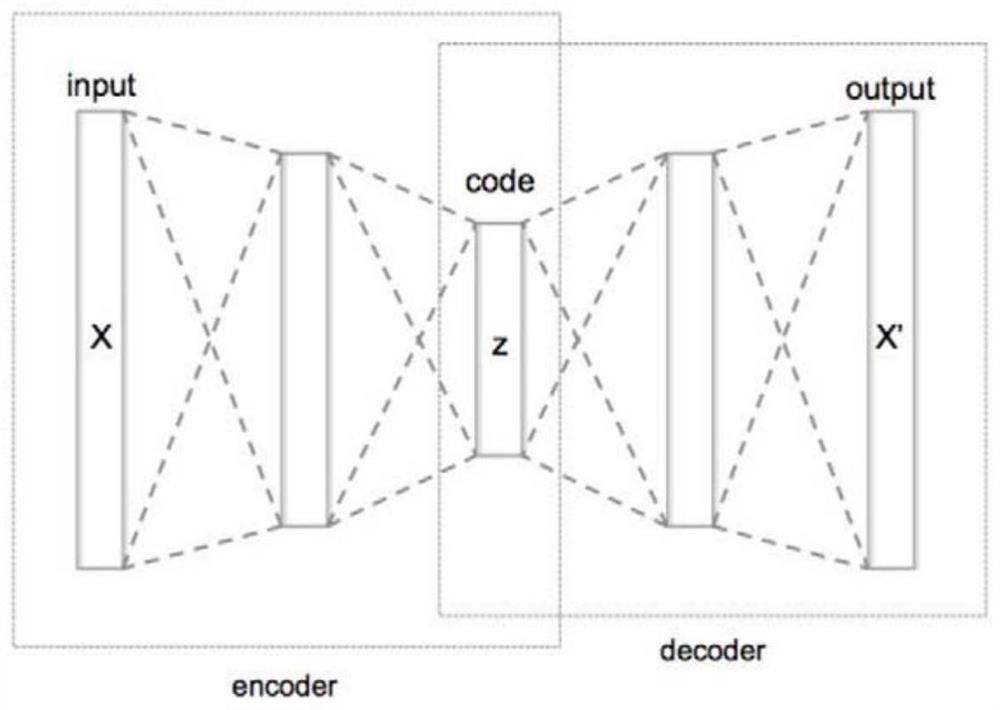
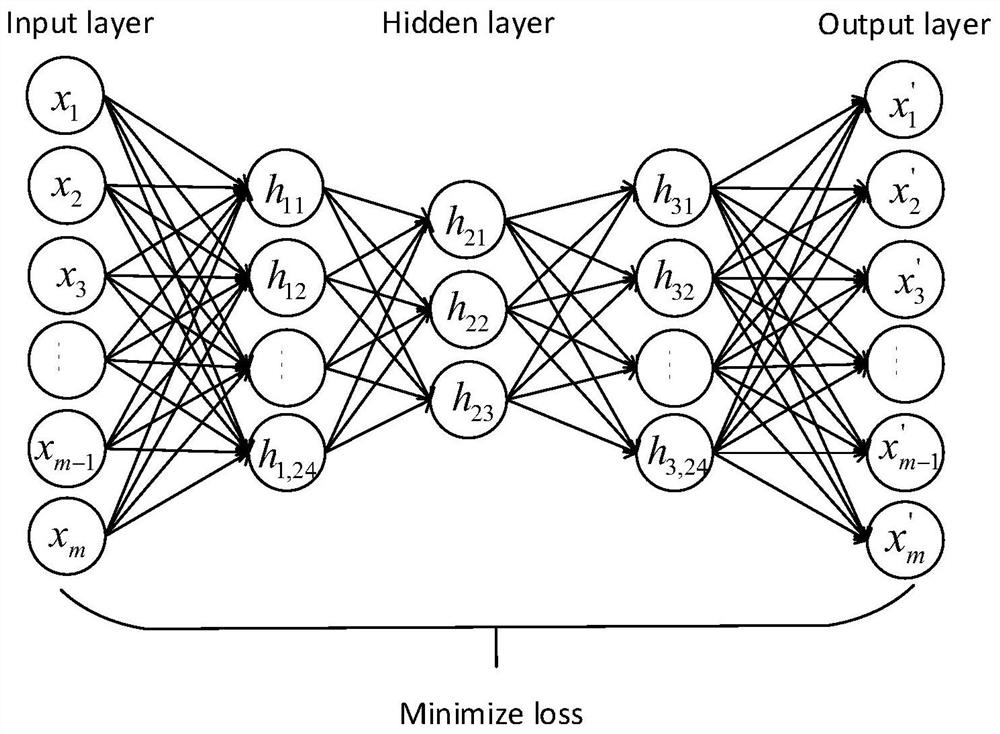
Track sequence clustering method based on deep learning
The invention relates to the field of data mining, in particular to a track sequence clustering method based on deep learning. The method comprises the following steps: step 1, a pre-training layer: learning low-dimensional feature representation of track data by using a sequence-to-sequence auto-encoder model; step 2, an initial clustering layer: executing a K-Means clustering algorithm for multiple times on track feature representation obtained by the pre-training layer, and selecting a clustering center in optimal clustering results as an initial clustering center; step 3, a joint training optimization layer: combining track clustering and a depth feature extraction method, proposing an optimization loss function combining reconstruction errors and clustering errors of the sequence-to-sequence auto-encoder model, and mapping the track feature representation to a feature space more suitable for clustering.
Owner:ZHEJIANG LAB +1
Typical court classification method and system based on clustering algorithm
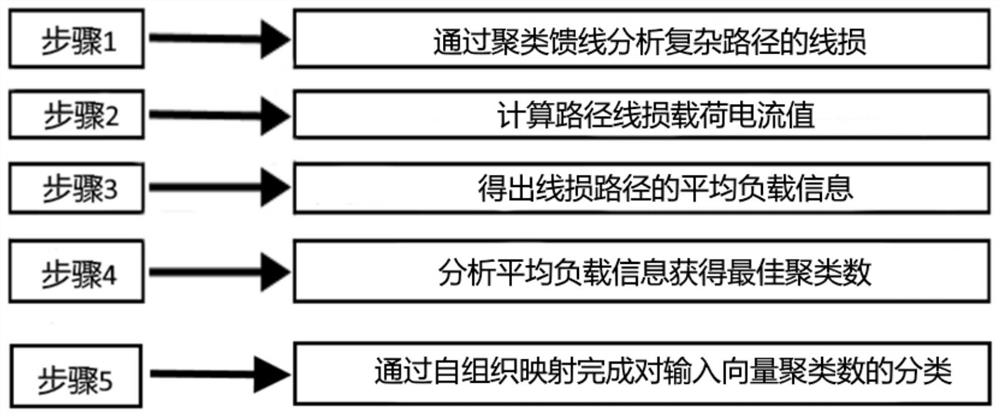
PendingCN112784870ARealize dimensionality reduction and denoisingReduce complexityData processing applicationsCharacter and pattern recognitionCluster algorithmAlgorithm
The invention discloses a typical court classification method and system based on a clustering algorithm, and relates to a court line loss classification technology. The method comprises the following steps: performing line loss calculation through the equivalent relationship between root-mean-square current and maximum current, comparing the electric energy loss generated by the maximum current flowing through the line with the electric energy loss generated by the actual load, achieving clustering analysis of the feeder line path of the court through a feeder line clustering method, and performing layer-by-layer resistance equivalence on the distribution line of the court with a complex structure through an equivalent resistance method to obtain a calculation model with a simple structure; obtaining an average load rate according to the calculation model; finding out an optimal cluster number through load rate feature sequence clustering; classifying the input vectors through self-organizing mapping; and providing line loss information for typical court classification of the clustering algorithm, and carrying out court line loss classification according to the line loss information.
Owner:STATE GRID ZHEJIANG ELECTRIC POWER +5
Compression and clustering-based batch protein homology search method
ActiveCN106022000AShorten the timeBiostatisticsSpecial data processing applicationsProtein DatabasesSequence clustering
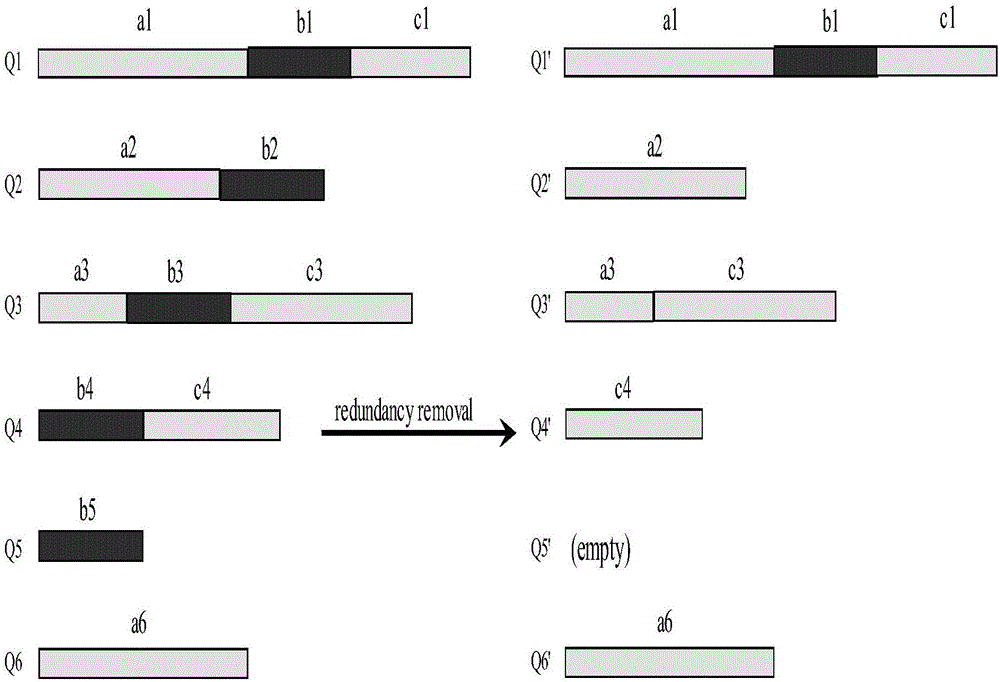
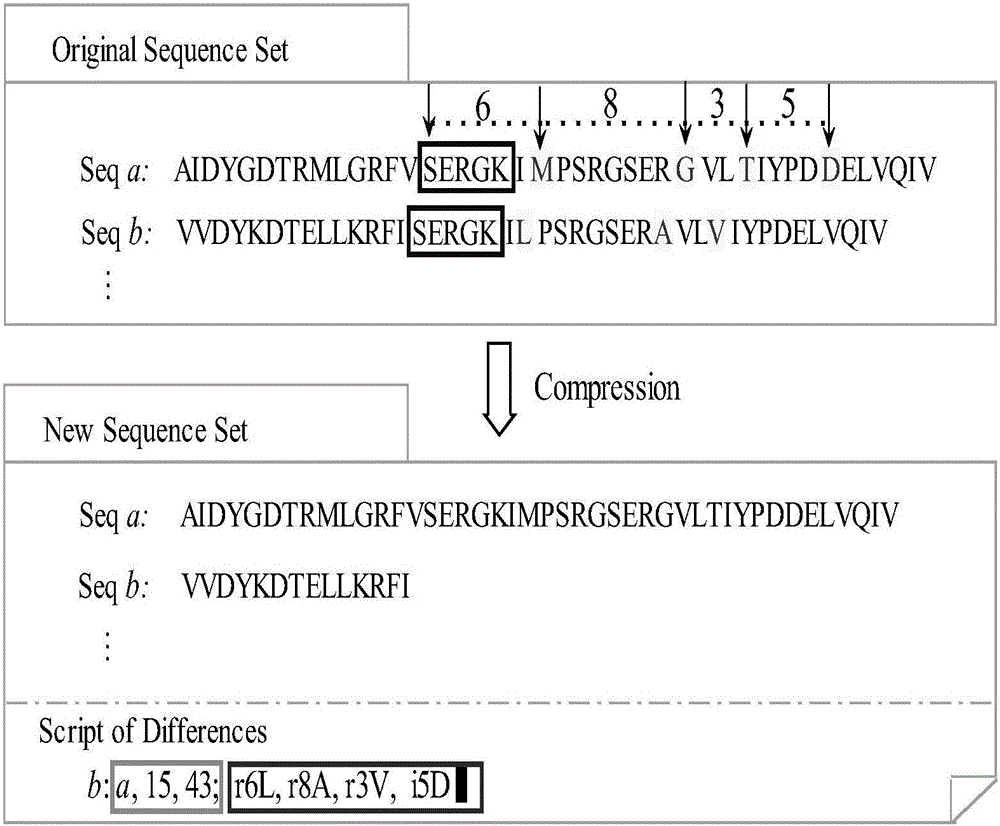
The invention discloses a compression and clustering-based batch protein homology search method and belongs to the cross field of computer application technologies and bio-technologies. The method comprises the steps of firstly performing compression operation on a query sequence and a protein database through redundancy analysis and redundancy removal processes by fully utilizing sequence similar information existent in a protein database sequence and the query sequence; secondly performing similar sub-sequence clustering on the compressed protein database; thirdly performing a search by utilizing a mapping principle based on the clustered database to discover potential results, and establishing an executable database according to the found potential result set; and finally performing a homology search in the executable database to obtain a final homology sequence. According to the method, the homology search is performed in the established executable database, so that the time for repeated sequence comparison and gapless expansion is greatly shortened.
Owner:DALIAN UNIV OF TECH
High-flux STR sequence core replication number detection method
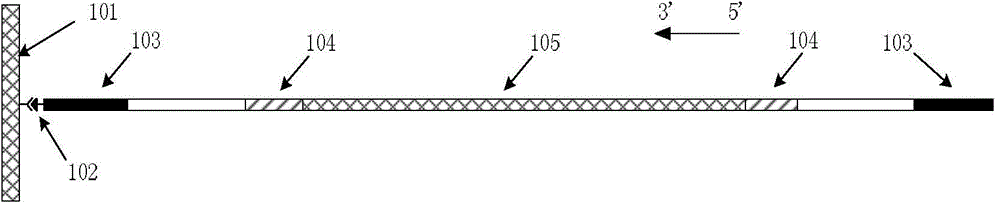
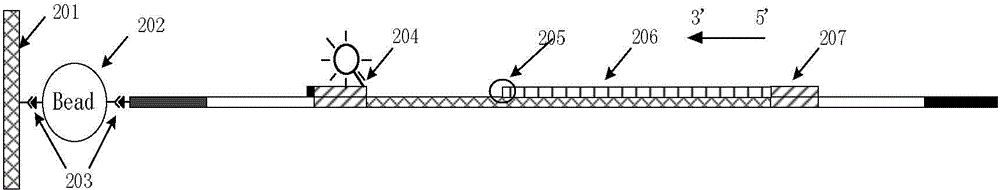
InactiveCN104152568AShorten detection timeReduce testing costsMicrobiological testing/measurementFluorescenceNucleotide
The invention provides a high flux STR sequence core replication number detection method with characteristics of high efficiency and rapidity, which is characterized in that a pair of detection primers are hybridized on a STR sequence cluster amplified on a detection substrate, wherein a fluorescence group is modified on a final primer, then a nucleotide combination is used for extension step by step, simultaneously, the fluorescence signal is detected after each time of extension until the basic group with fluorescence on the final primer is cut by polymerase, then the signal disappears, and then the condition of the fluorescence signal is finally analyzed to obtain the corresponding STR sequence core replication number. According to the invention, an employed biochemical reagent is widely used for the detection platforms of biology chip and high flux sequencing, the signal to noise ratio is high, accuracy for STR detection and resolution to STR heterozygosis can be obviously increased, The method can obtain more convinced result through detection of more STR locus due to high flux characteristic of the biochemical reagent and can detect more samples to realize rapid colony STR detection.
Owner:SOUTHEAST UNIV
Method and equipment for determining near-synonymy sequence clusters
ActiveCN103246697AAccurately determineImprove the efficiency of obtaining informationSpecial data processing applicationsFeature vectorSequence clustering
The invention aims to provide a method and equipment for determining near-synonymy sequence clusters. The method specifically includes acquiring a plurality of near-synonymy sequence pairs; determining initial near-synonymy sequence clusters corresponding to the near-synonymy sequence pairs; and clustering sequences in the initial near-synonymy sequence clusters according to feature vectors of the sequences in the initial near-synonymy sequence clusters to acquire one or a plurality of near-synonymy sequence clusters. Compared with the prior art, the method and the equipment have the advantages that the initial near-synonymy sequence clusters corresponding to the near-synonymy sequence pairs are determined, the sequences in the initial near-synonymy sequence clusters are clustered according to the feature vectors of the sequences in the initial near-synonymy sequence clusters to acquire the near-synonymy sequence clusters, accordingly, the near-synonymy sequence clusters can be accurately determined, the information acquisition efficiency is improved for users, and the search experience is enhanced for the users.
Owner:BAIDU ONLINE NETWORK TECH (BEIJIBG) CO LTD
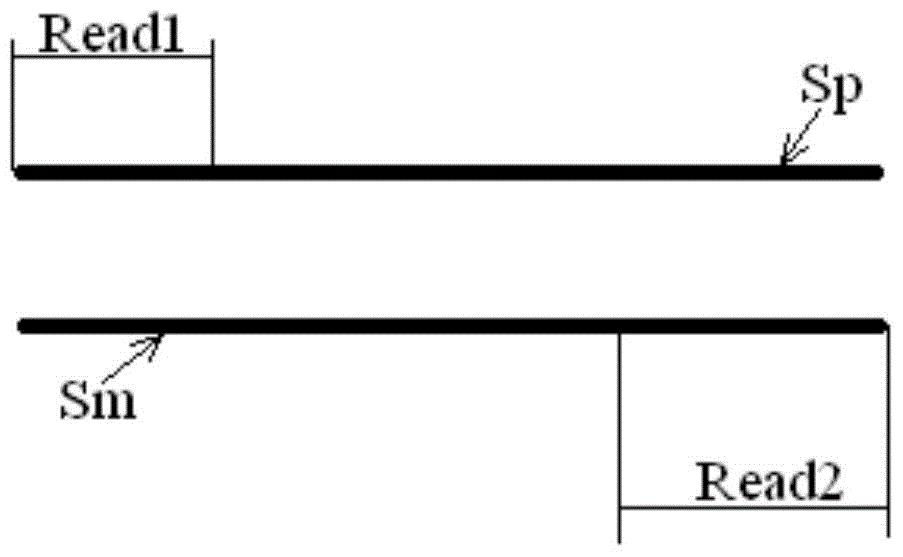
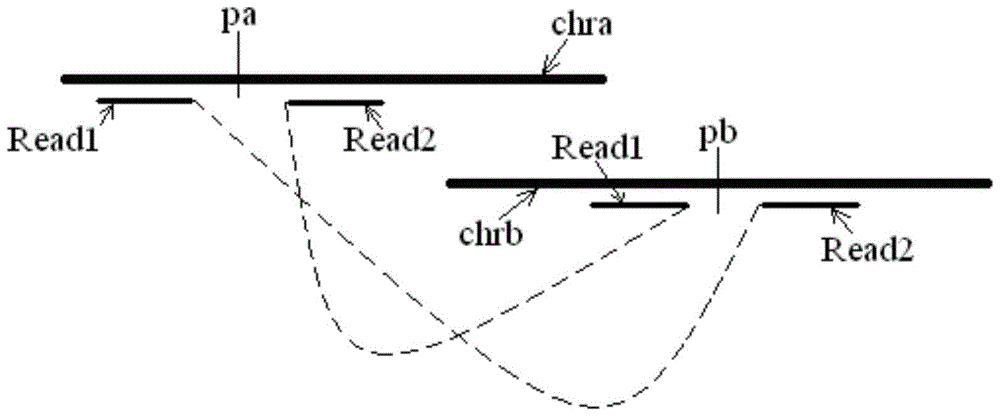
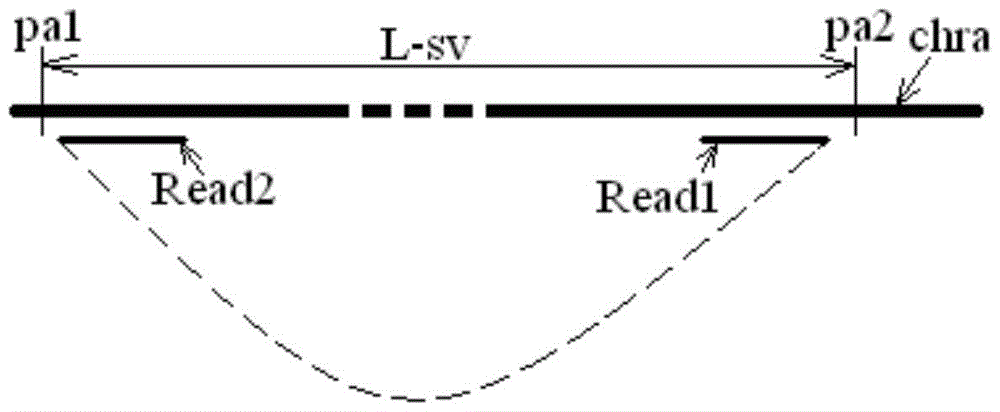
A method and device for detecting abnormal chromosome structure
ActiveCN104302781BImprove effectivenessImprove reliabilityMicrobiological testing/measurementBiostatisticsAlgorithmWhole genome sequencing
A method and device for detecting abnormal chromosome structure, wherein the method includes: obtaining the whole genome sequencing result of a target individual, that is, multiple pairs of read length pairs located at both ends of the measured chromosome segment; comparing the sequencing result with a reference sequence to obtain An abnormal match set, which includes two read length sequences that match the read length pairs of different chromosomes of the reference sequence; cluster the read length sequences in the abnormal match set into clusters according to the matched positions; use, for example, correlation with compactness The preset requirements of the clustering method are to filter the clusters obtained by clustering to obtain the filtered result clusters, which are used to judge the occurrence of structural abnormalities of chromosome translocations.
Owner:BGI CLINICAL LAB (SHENZHEN) CO LTD
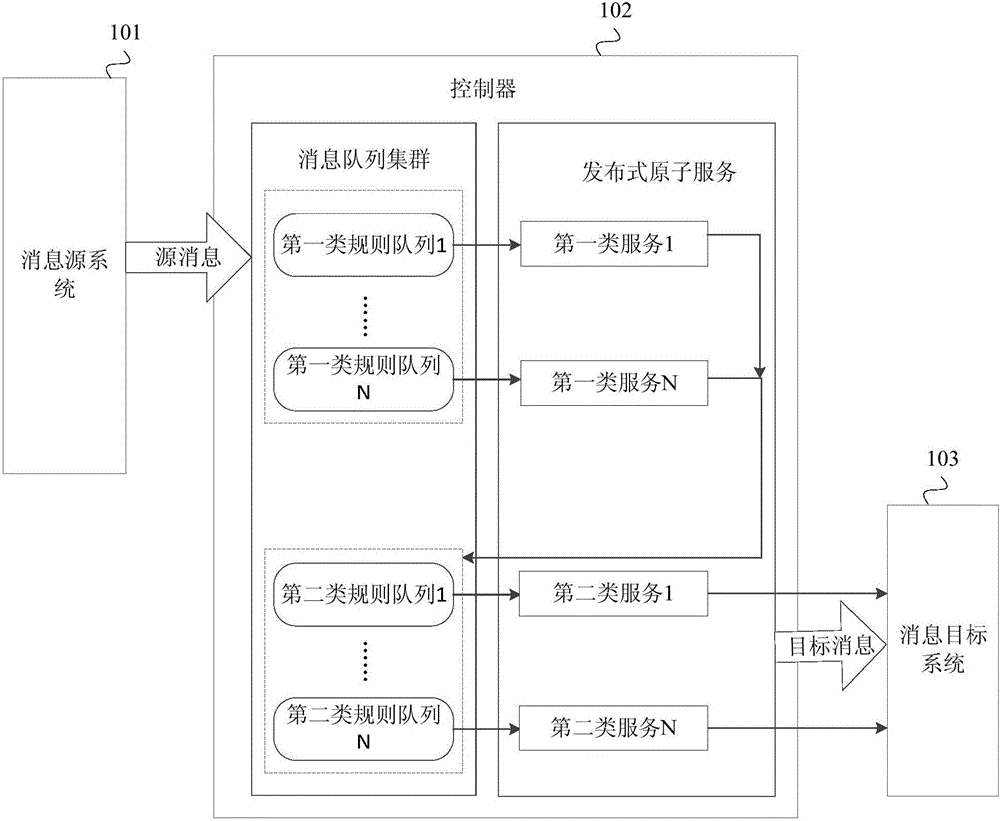
Message processing method and device, controller and system
The invention provides a message processing method and device, a controller and a system. The message processing method includes the steps that a source message sent by a message source system is received; a first-class rule sequence corresponding to the source message is determined from a preset message sequence cluster; the source message is sequentially processed according to at least one first-class rule in the first-class rule sequence corresponding to the source message; a second-class rule sequence corresponding to processed message is determined from the message sequence cluster; the first-class rule sequence and the second-class rule sequence are rule sequences of different types; the processed message is sequentially processed according to at least one second-class rule in the second-class rule sequence corresponding to the processed message to obtain the target message; the target message is sent to a message target system. Complexity of message processing is reduced.
Owner:MINSHENG BANKING CORP
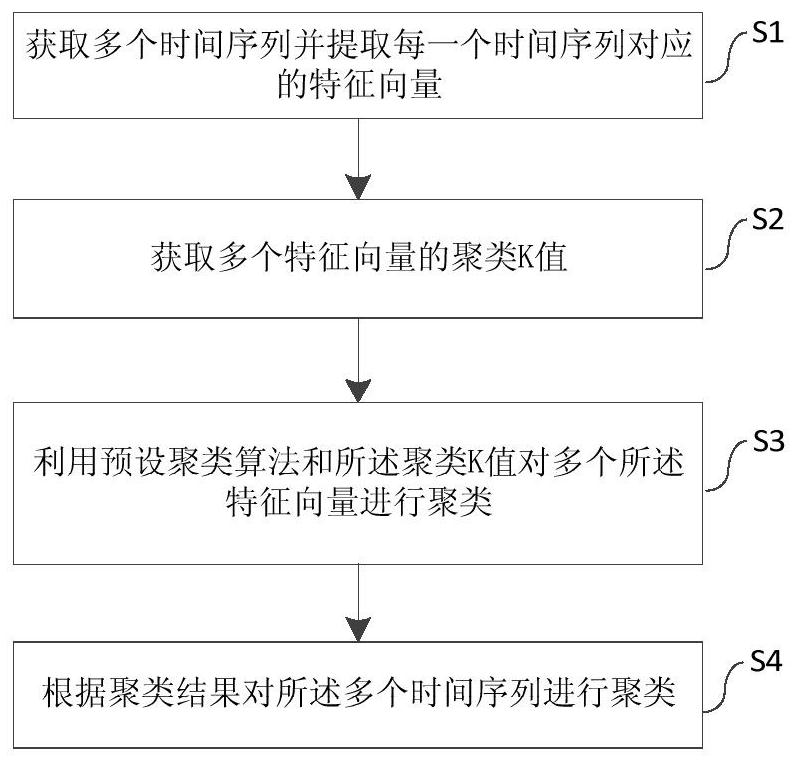
Time sequence clustering method and system, equipment and medium
PendingCN113988156AAchieve dimensionality reductionImplement cluster analysisCharacter and pattern recognitionNeural architecturesTime informationCluster algorithm
The invention discloses a time sequence clustering method. The method comprises the following steps: acquiring a plurality of time sequences and extracting a feature vector corresponding to each time sequence; acquiring a clustering K value of the plurality of feature vectors; clustering the plurality of feature vectors by using a preset clustering algorithm and the clustering K value; and clustering the plurality of time sequences according to a clustering result. The invention further discloses a system, computer equipment and a readable storage medium. According to the scheme provided by the invention, the feature vector of the time sequence is extracted, the dimension reduction of the time sequence is realized, the data after the dimension reduction is clustered by using the clustering algorithm, and finally the clustering analysis of the time sequence is realized. In this way, it is guaranteed that the dimensions of the feature spaces of all the time sequences are consistent, meanwhile, the sampling step length of the time sequences is not required, and time information is also considered when the feature vectors are extracted.
Owner:SHANDONG YUNHAI GUOCHUANG CLOUD COMPUTING EQUIP IND INNOVATION CENT CO LTD
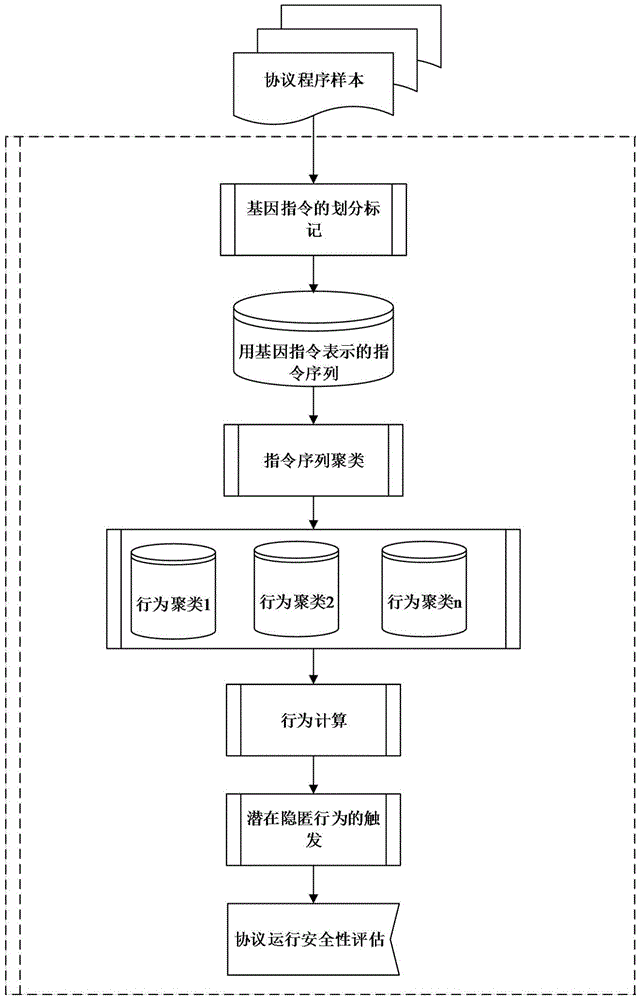
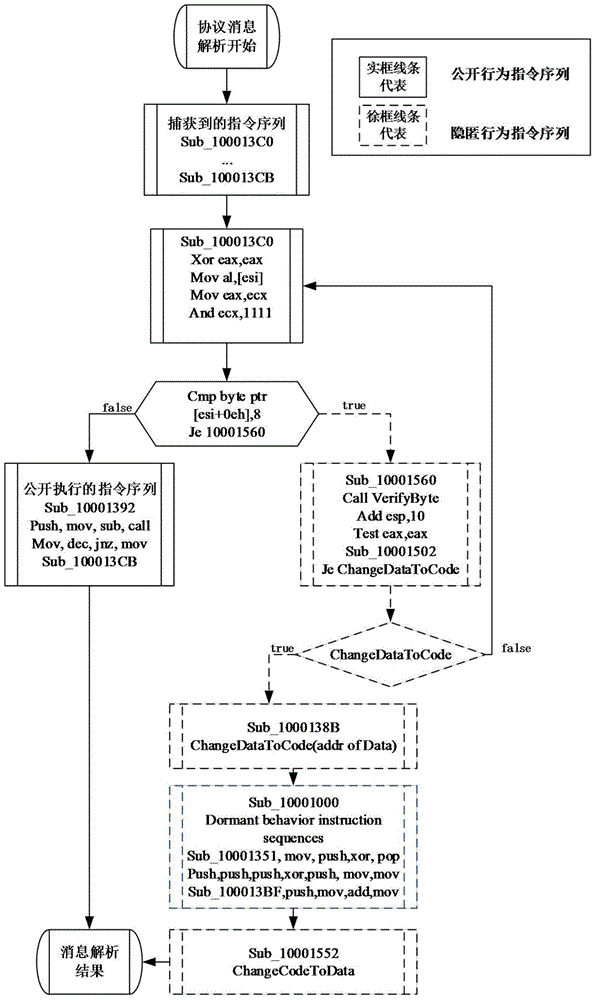
Method for mining unknown network protocol hidden behaviors through clustering instruction sequences
The invention discloses an instruction sequence cluster mining method for concealed behavior of an unknown network protocol, which mainly solves the problem that the existing protocol reverse analysis method only analyzes the format of the protocol message, but cannot analyze the protocol behavior, especially the hidden behavior. The implementation steps are: (1) divide and mark all the instructions of the protocol program into three types of genetic instructions; (2) cluster the instruction sequence; (3) calculate the protocol behavior; (4) find the comparison instructions before all potential hidden behaviors , extract the constants involved in the comparison, use these constants to replace the relevant fields in the protocol message, generate new messages with triggering capabilities, and use the new messages to trigger potential hidden behaviors; (5) Calculate the three types of genes between hidden behaviors and known behaviors The absolute difference RS of the instruction distribution rate, if RS>0.3, the protocol operation is not safe, and the protocol has malicious behavior; otherwise, the protocol operation is safe, and the mining is over. The invention improves the speed and accuracy of excavation, and can serve more users and wider application fields.
Owner:XIDIAN UNIV +1
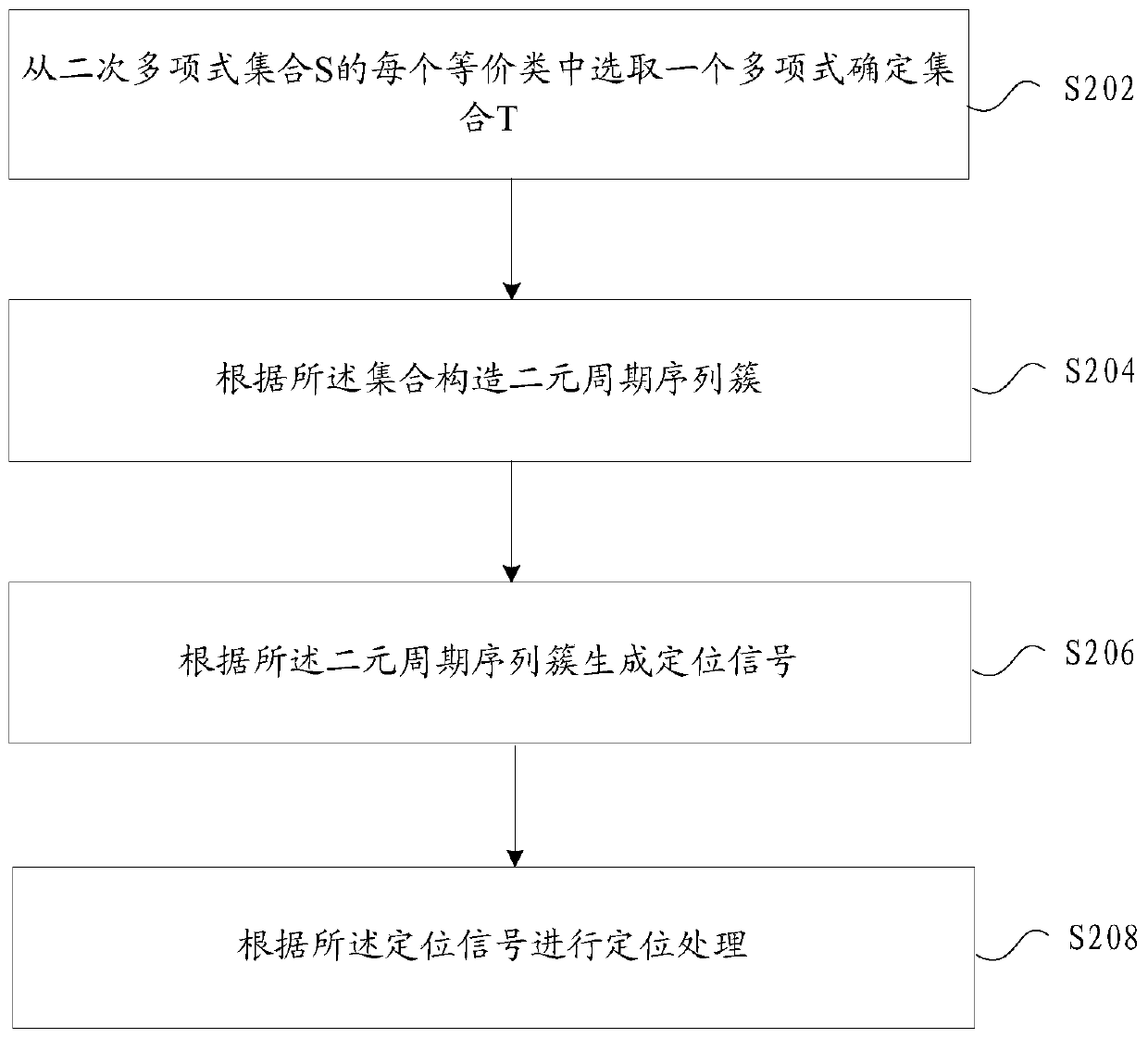
Positioning method and device based on binary periodic sequence
PendingCN111083629AReduce peakPosition fixationMultiplex code generationCorrelation coefficientAlgorithm
The invention provides a positioning method and device based on a binary periodic sequence, and the method comprises the steps: selecting a polynomial from each equivalence class of a quadratic polynomial set S, and determining a set T; constructing a binary periodic sequence cluster according to the set T, generating a positioning signal according to the binary periodic sequence cluster, performing the positioning processing according to the positioning signal, so that the problem that a correlation average value of the binary sequence constructed in the related technology is good and a peakvalue of the correlation coefficient of the positioning signal generated in the positioning application is relatively high can be solved; due to the fact that the binary sequence with the new length is constructed and has the good correlation coefficient, the peak value of the positioning correlation coefficient generated in the positioning application is small.
Owner:ZTE CORP
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com