Method for realizing embedded secure socket layer virtual private network (SSL VPN)
An implementation method and embedded technology, applied in electrical components, transmission systems, etc., can solve problems such as poor data processing capabilities, equipment support problems, and low security, and achieve the goal of improving forwarding efficiency, simplifying forwarding rules, and ensuring stability Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
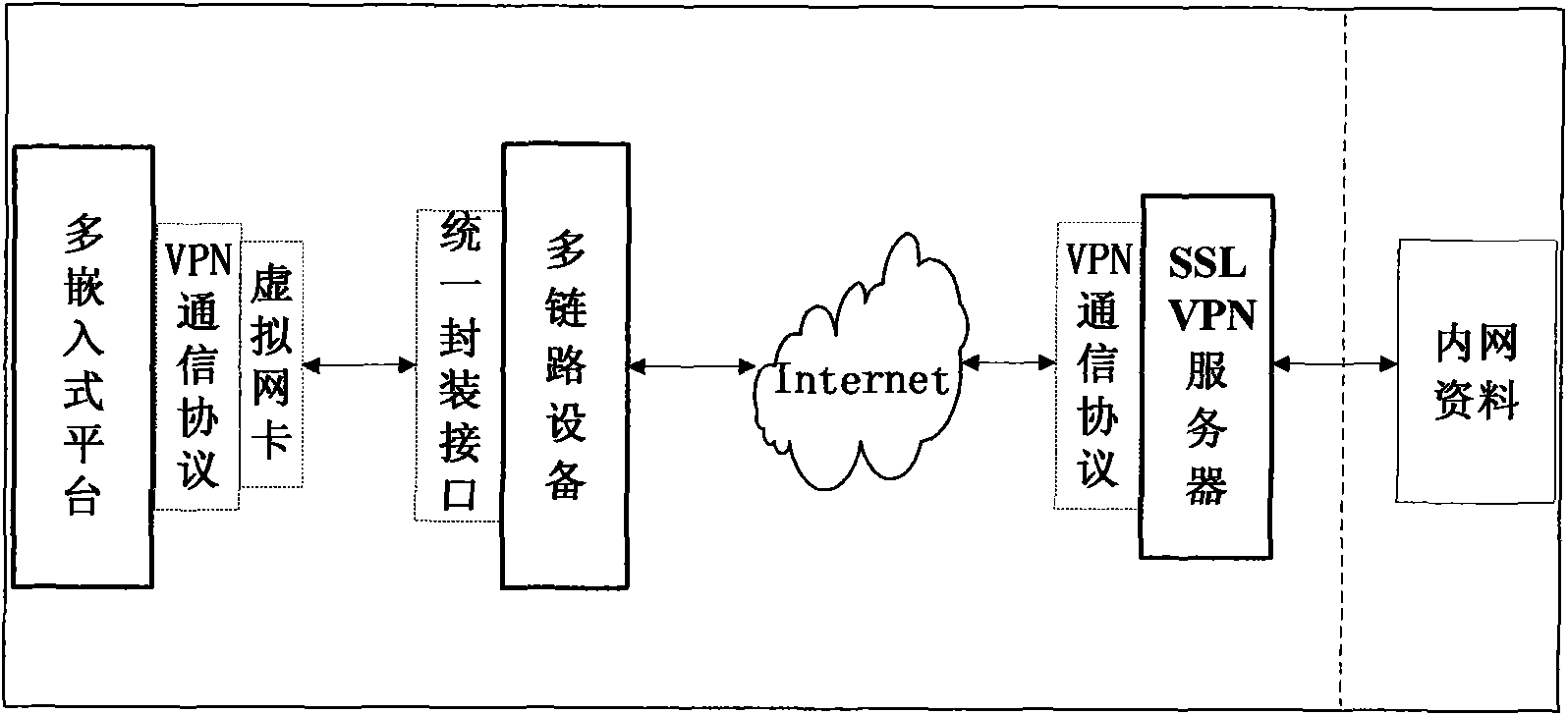
[0272] Such as figure 1 Shown, the concrete workflow of the inventive method is as follows:
[0273] (1) Assume that there are four different clients with different operating systems installed, namely WinCE, Linux, WinXP, and uCOS. These clients are in different intranet environments and are connected to the VPN server through different links.
[0274](2) To connect to the VPN server, the WinCE client must first have the certificate and key issued by the CA, so that the VPN server allows the WinCE client to connect and enter the virtual private network. Similarly, other clients must have corresponding certificates and keys to connect to the VPN server. Once the client is connected to the server, the server will obtain various information of the client through a predetermined protocol, including client type, product model, OS identifier used, protocol version number used, and the current link used.
[0275] (3) When the WinCE client is connected to the server, it will send ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com