Secure encryption method for database
A technology of security encryption and data encryption, which is applied in the computer field, can solve the problems of data security, integrity and non-tamperable modification, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
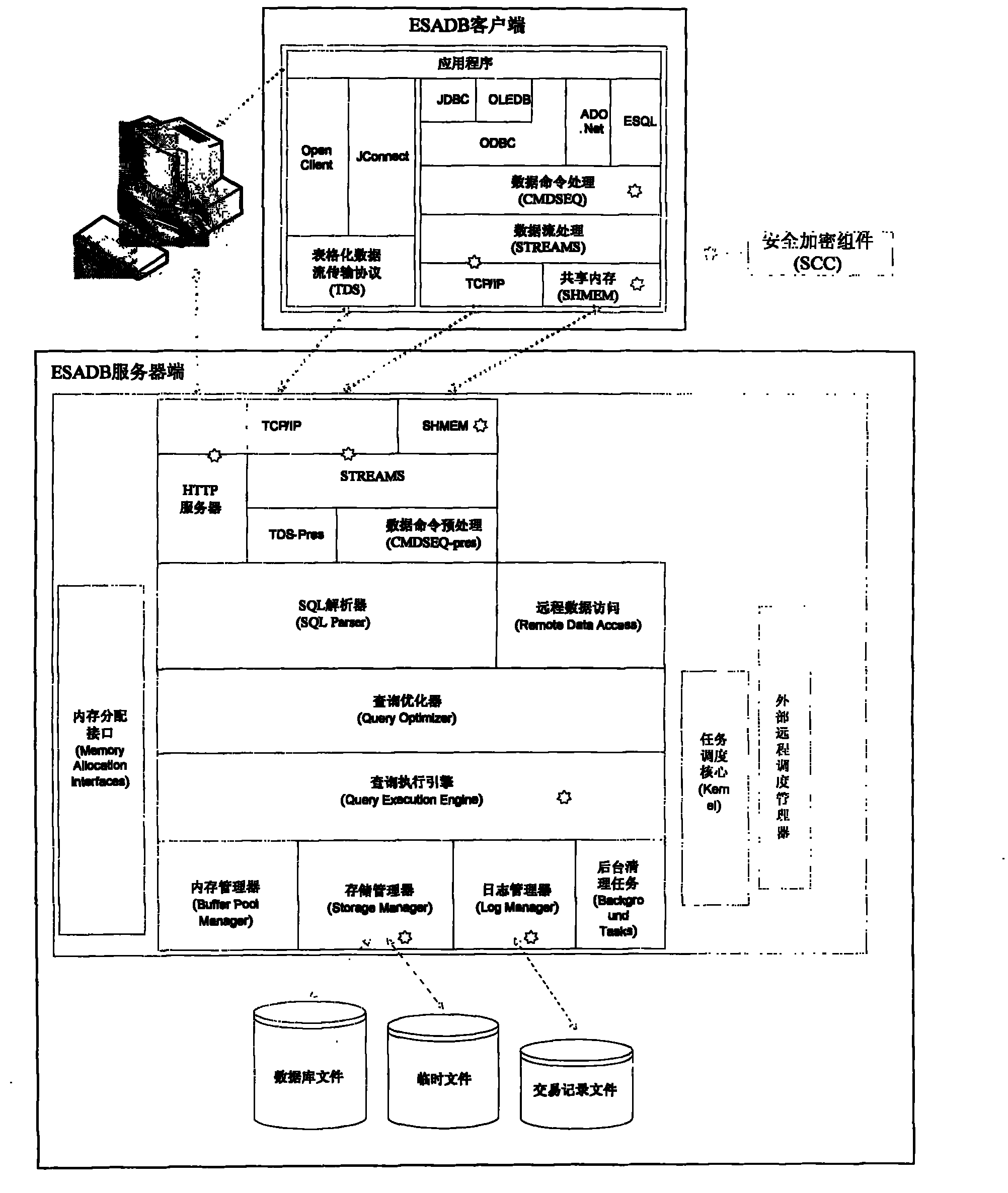
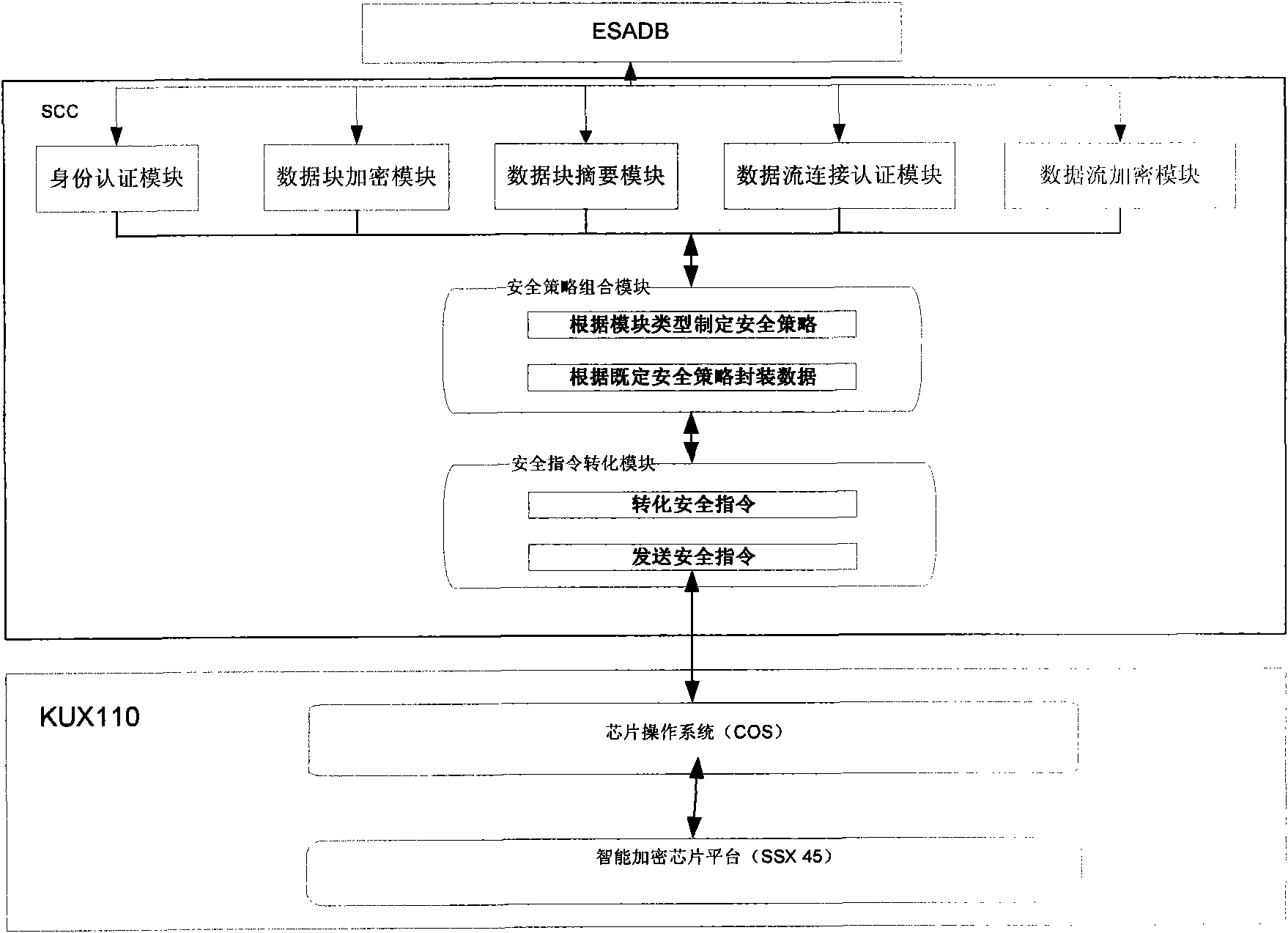
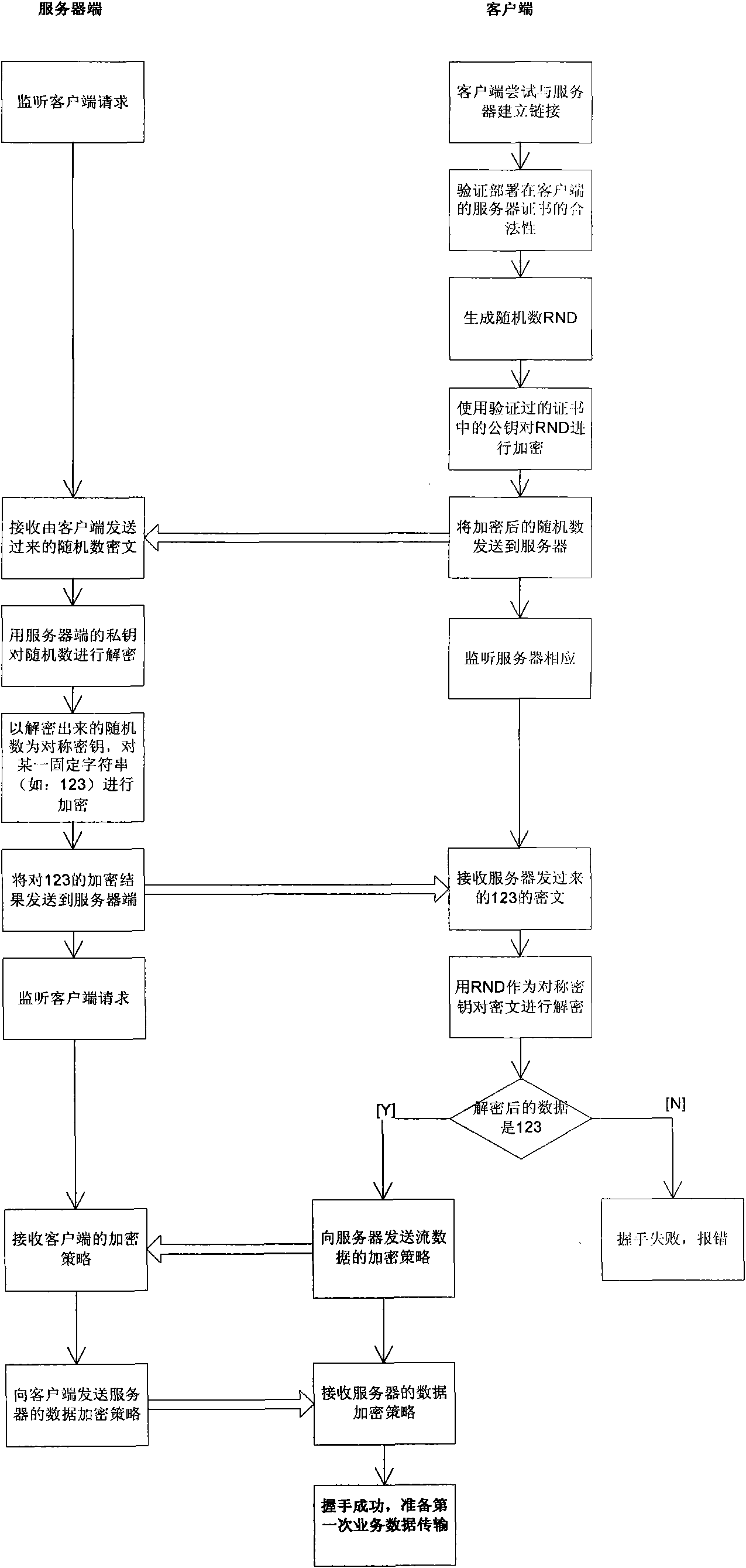
[0011] The technical solution of the present invention will be described in further detail below with reference to the accompanying drawings.
[0012] figure 2 A schematic diagram of the method according to the invention is shown. The technical solution of the present invention is to install the security encryption component SCC on the client and server of the database, which includes an identity authentication interface, a data block encryption interface, a data block digest interface, a data stream connection authentication interface, a data stream encryption interface, and security Strategy combination module, security instruction conversion module; after the database engine inputs the data to be processed, SCC calls the interface, and the called interface formulates a security policy through the security policy combination module and combines it into an application protocol data unit based on the security policy and sends it to the high-speed For mobile storage devices, the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com