System and method for realizing Phishing identification based on challenge password token
A technology of challenging passwords and phishing websites, applied in the information field, can solve problems such as user loss, counterfeiting of legitimate user identities, and information theft cannot be guaranteed, and achieve the effect of increasing security, improving security, and preventing user property loss
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0047] The present invention will be described in further detail below in conjunction with the accompanying drawings.
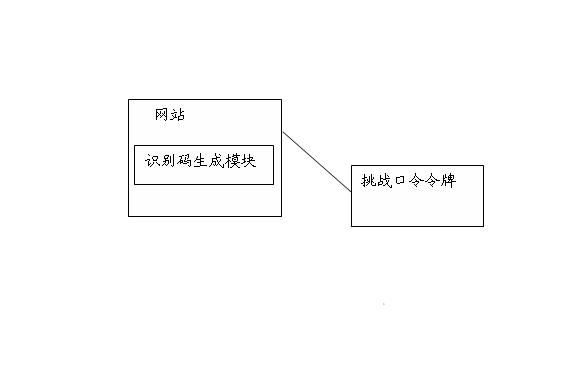
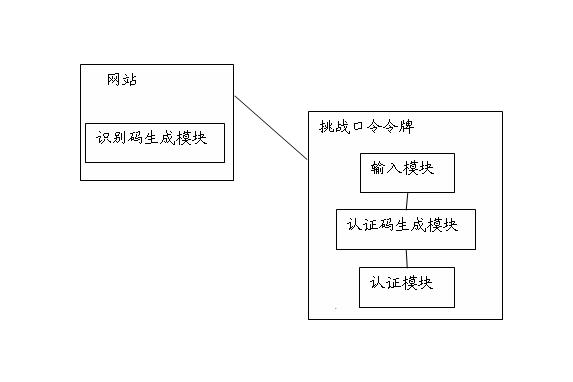
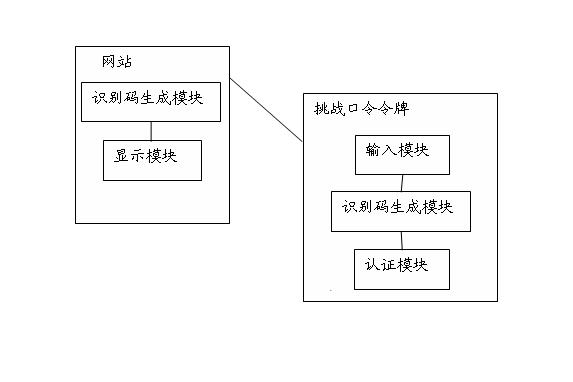
[0048] like figure 1 As shown, it is a schematic diagram of the composition of a phishing website identification system based on a challenge password token in Embodiment 1 of the present invention, and the system includes:
[0049] An identification code generation module, the identification code generation module is located in the website, and is used to generate a group of dynamic identification codes according to the website identification code, the personal account information input by the user and the current time factor when the user performs an account operation;
[0050] The challenge password token is used to generate a set of dynamic authentication codes, and match the dynamic identification codes and dynamic authentication codes to perform website identity authentication.
[0051] Said sites include banking or other payment sites.
[0052] When u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com