Data signature authentication method and data signature authentication system
A technology of data signature and authentication method, which is applied in the field of information security and can solve problems such as loss of users, loss or tampering of transaction information and personal information, and deception of the system.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
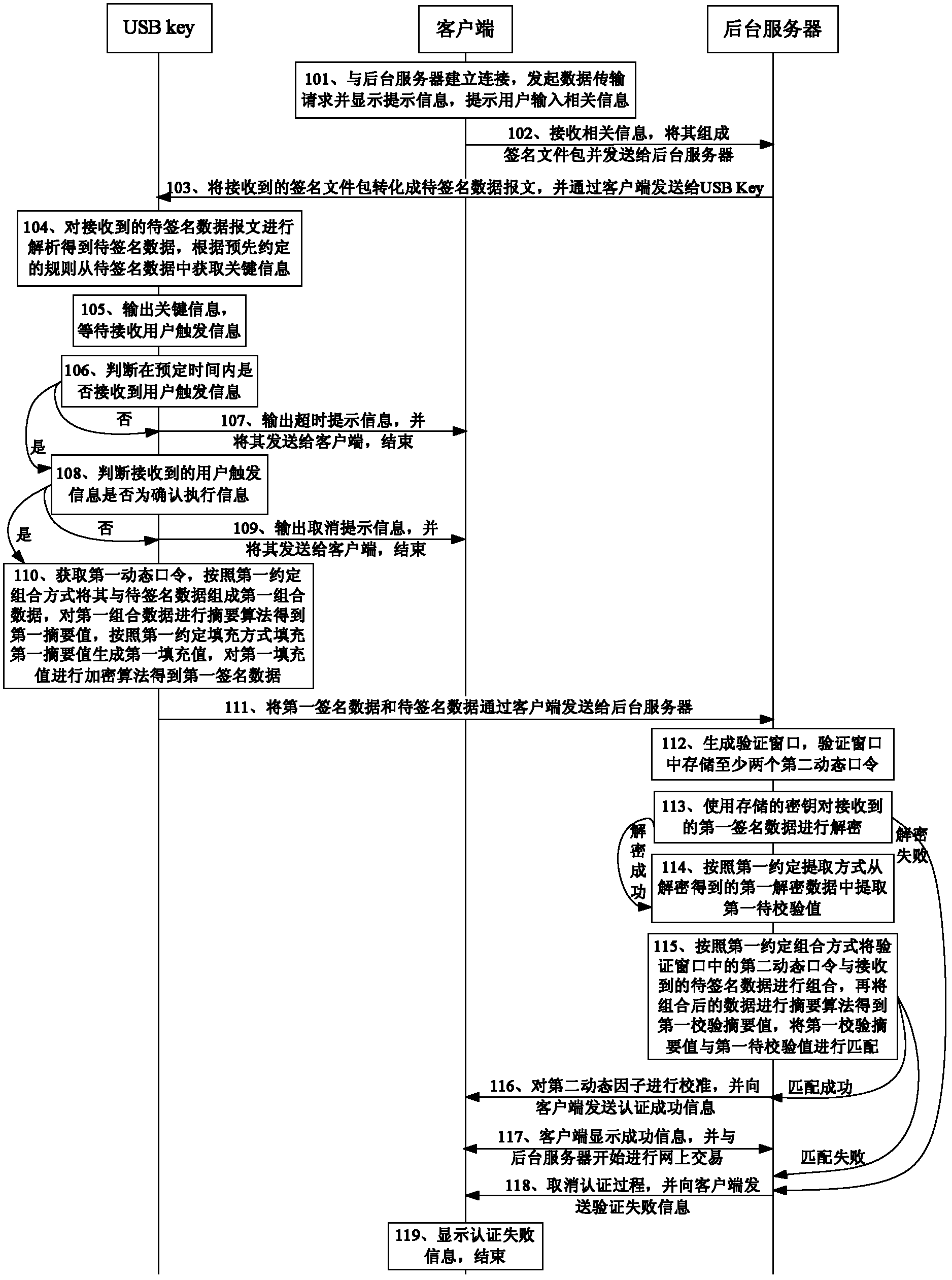
[0048] Embodiment 1 of the present invention provides a data signature authentication method. Take the user using USB Key to conduct online transactions between the client and the background server as an example. The USB Key connected to the client uses the method provided by the embodiment of the present invention to verify the The transfer data involved in the process and the dynamic password generated by the USB Key are signed to improve the security of online transactions. The key stored in the USB Key corresponds to the key stored in the background server, see figure 1 , the method includes:
[0049] Step 101: the client establishes a connection with the background server, initiates a data transmission request and displays a prompt message, prompting the user to input relevant information;
[0050] Specifically, the relevant information in this embodiment includes account, amount, user name, and password;
[0051] Step 102: the client receives relevant information, form...
Embodiment 2
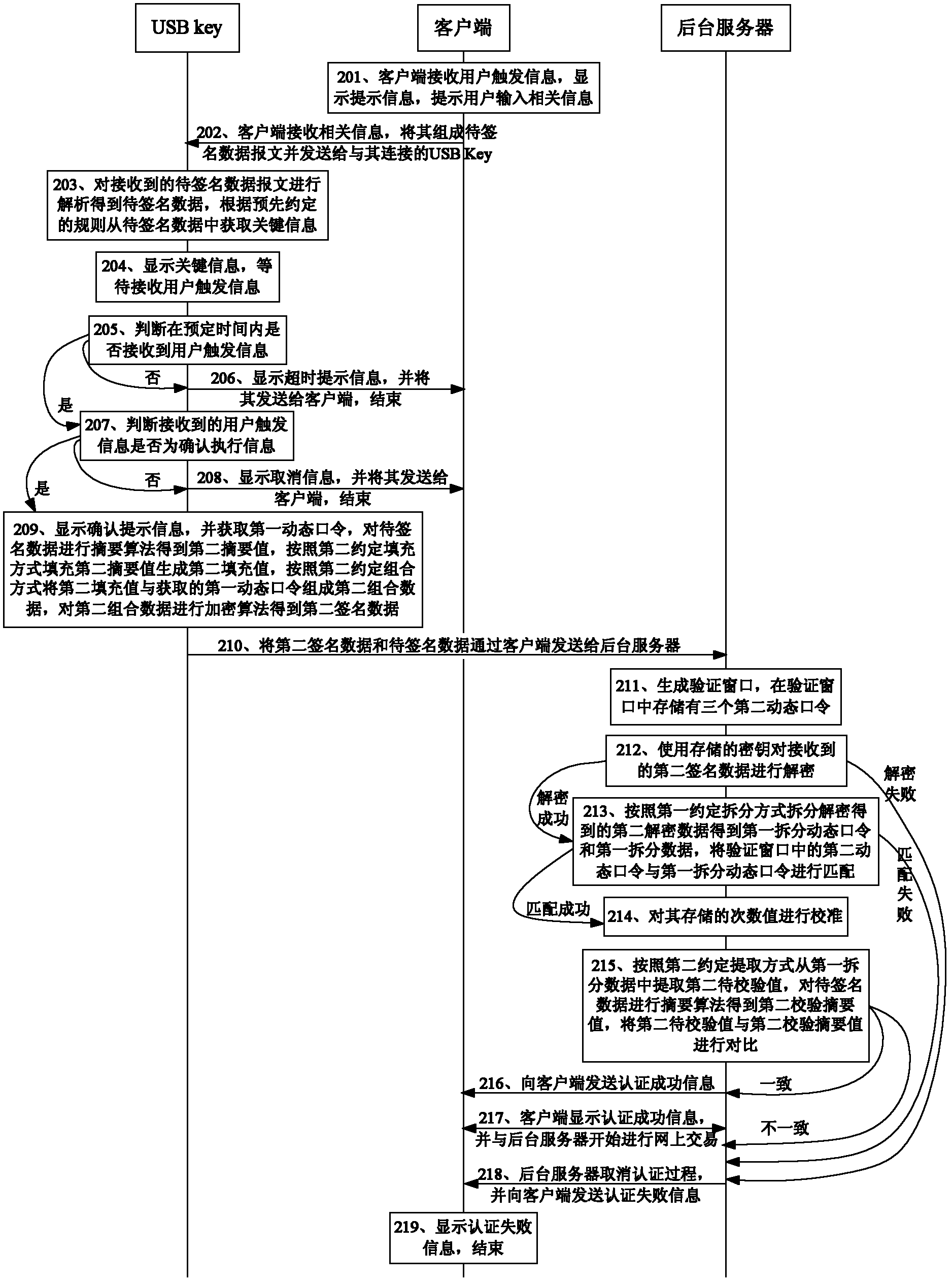
[0081] Embodiment 2 of the present invention provides another data signature authentication method, wherein, the first dynamic factor and the second dynamic factor are USB Key and the number of times stored in the background server, such as figure 2 shown, including:
[0082] Step 201: the client receives user trigger information, displays prompt information, and prompts the user to input relevant information, such as account, amount, user name, password, etc.;
[0083] Step 202: The client receives relevant information, composes it into a data message to be signed and sends it to the USB Key connected to it;
[0084] Step 203: The USB key analyzes the received data message to be signed to obtain the data to be signed, and obtains key information from the data to be signed according to the pre-agreed rules;
[0085] The data to be signed includes account number, amount, user name, password and other information; specifically, the key information in this embodiment is compose...
Embodiment 3
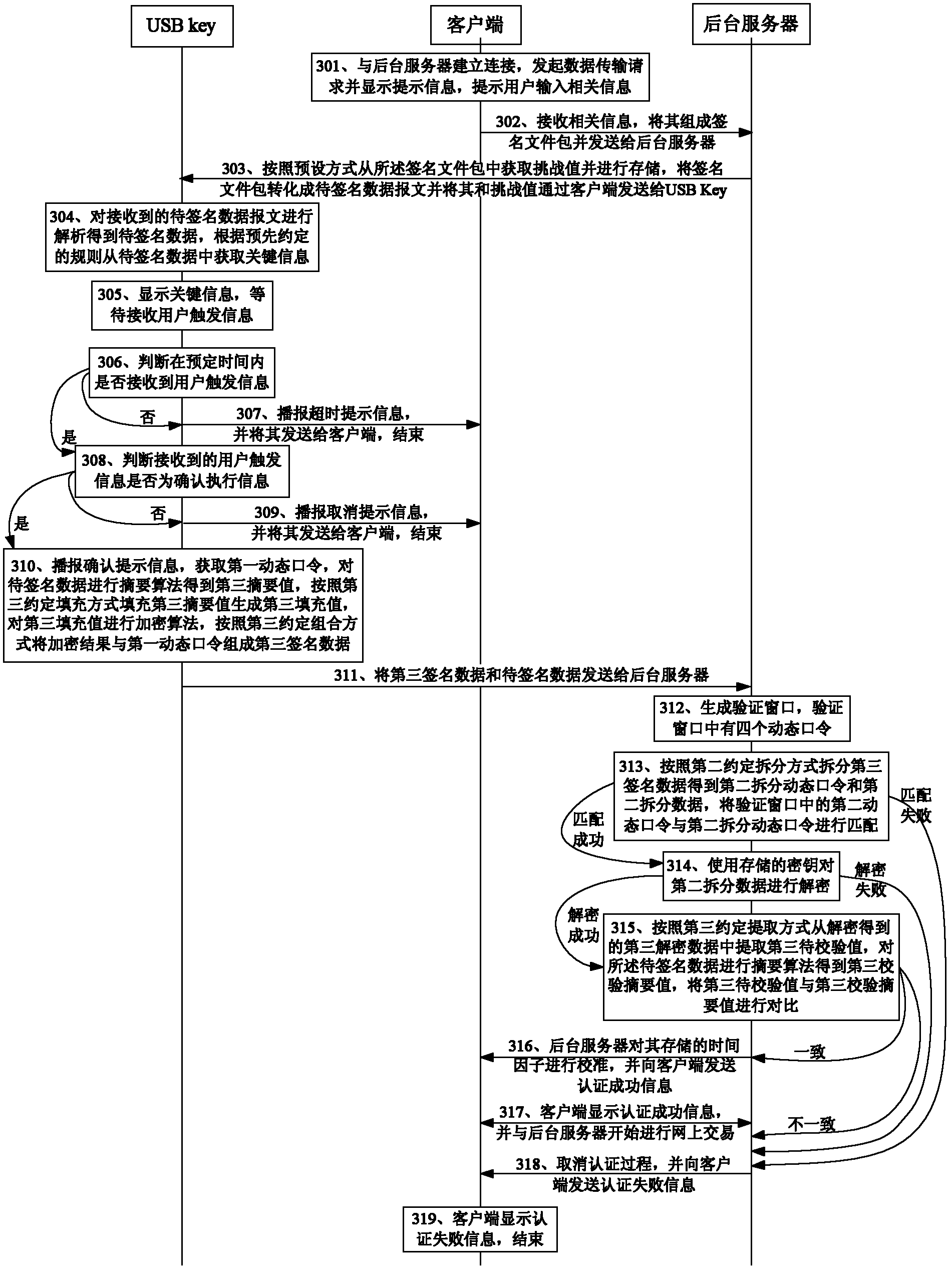
[0108] Such as image 3 As shown, there is another data signature authentication method provided by Embodiment 3 of the present invention, wherein the first dynamic factor and the second dynamic factor are USB Key and the time factor stored in the background server respectively, including:
[0109] Step 301: The client establishes a connection with the background server, initiates a data transmission request and displays prompt information, prompting the user to input relevant information; specifically, the relevant information in this embodiment includes account, amount, user name, and password;
[0110] Step 302: the client receives relevant information, forms a signature file package and sends it to the background server;
[0111] Step 303: The background server obtains the challenge value from the signature file package according to a preset method and stores it, converts the signature file package into a data message to be signed and sends it and the challenge value to th...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap