A document rights management method, device and system
A permission management device and technology of permission management, applied in the security field, can solve the problems of file permission information storage increase, etc., and achieve the effect of solving unlimited storage growth, reducing storage burden, and clearing useless data
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
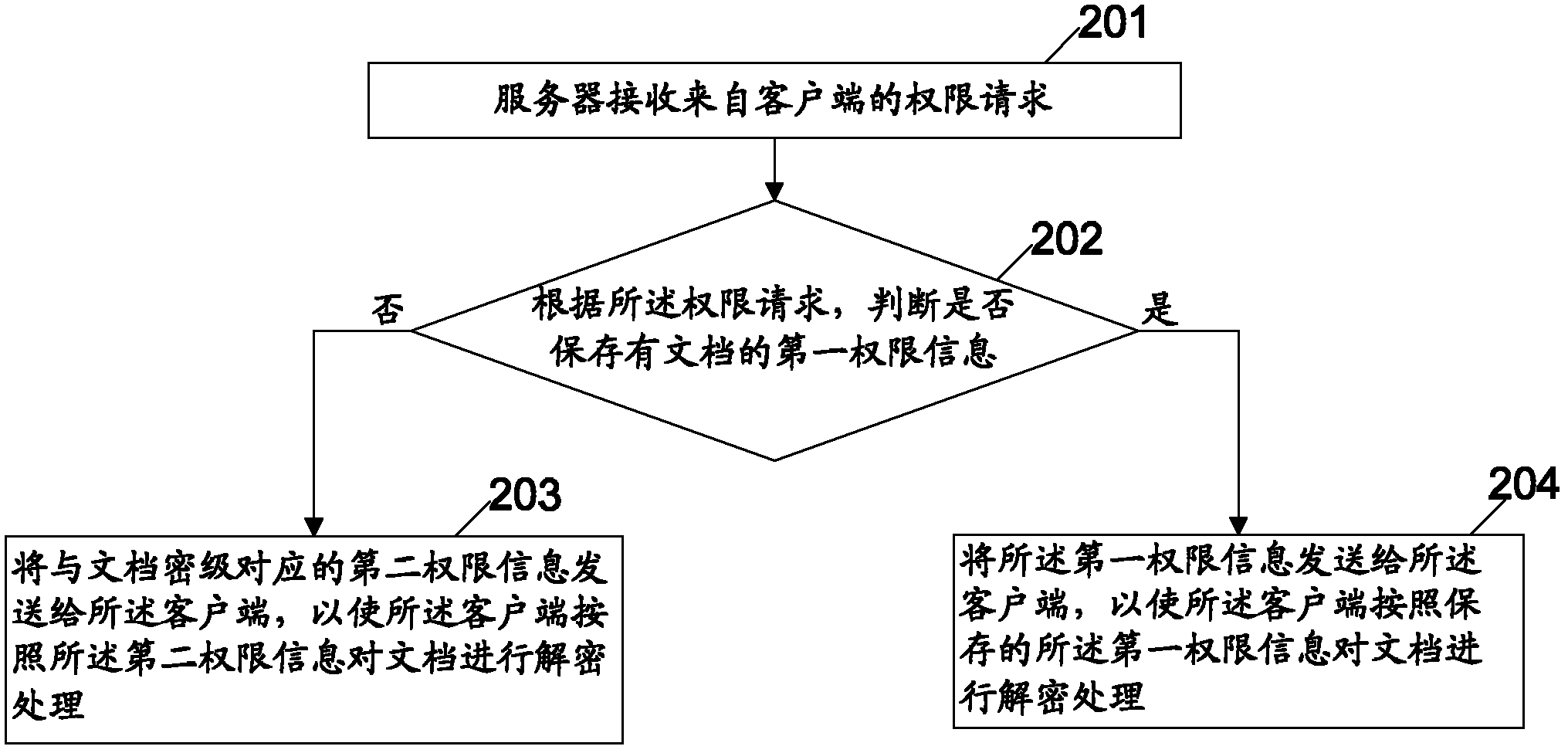
[0045] The embodiment of the present invention provides a method for document authority management, taking the server 102 as an example, in this embodiment, the authority information of the document is uniformly stored on the server 102, and when the client 101 opens the document, it is retrieved from the server 102 The permission information of the document, and then the server 102 sends the retrieved permission information to the client 101, such as figure 2 As shown, the method includes:
[0046] Step 201, the server receives a permission request from the client;
[0047] Wherein, the permission request is used to obtain permission information of the document, and the permission information is used to decrypt the document of the client.
[0048] Step 202, according to the permission request, determine whether the first permission information of the document is saved; if the first permission information of the document is saved, jump to step 204 for execution; if there is ...
Embodiment 2
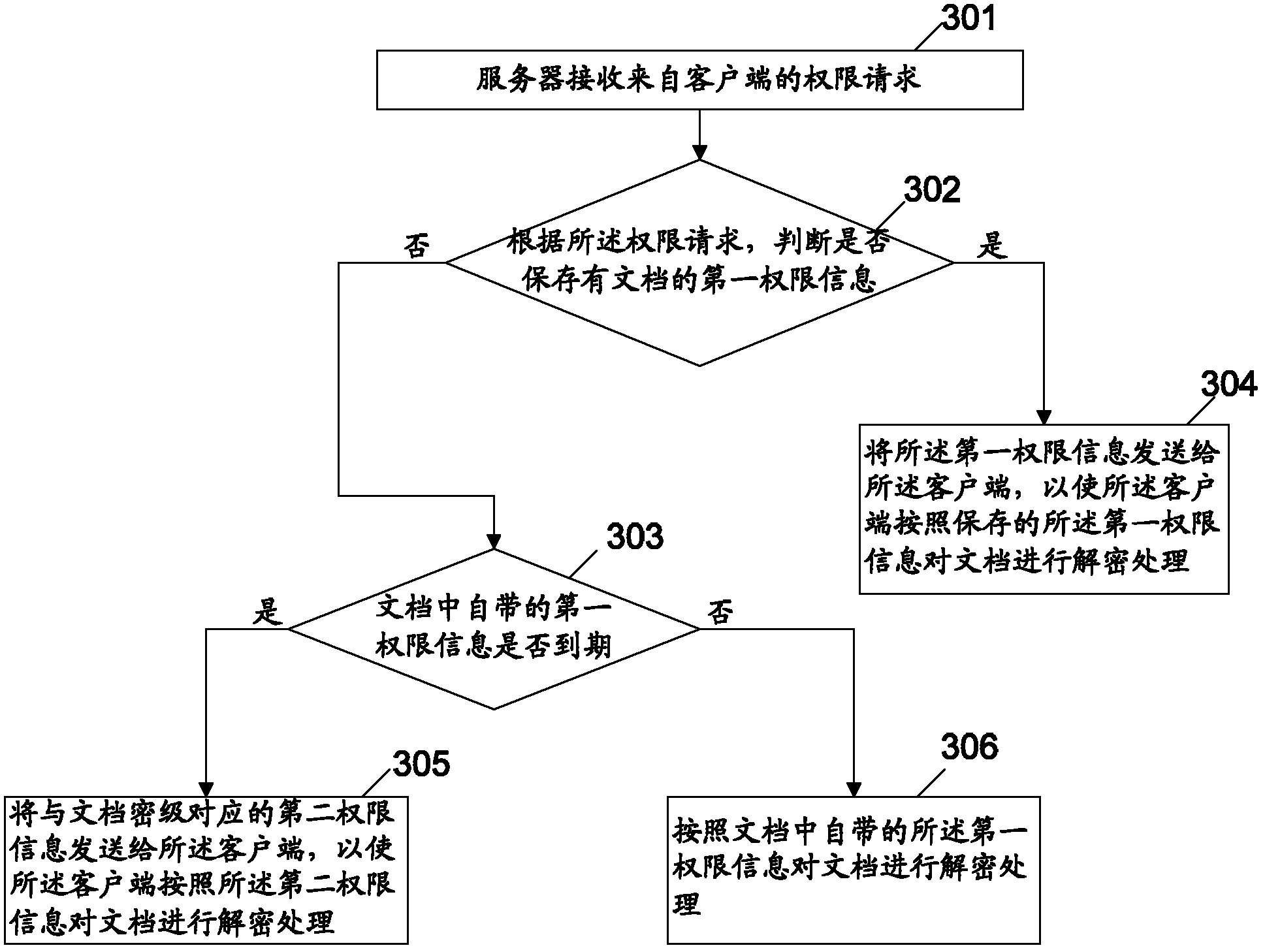
[0058] The embodiment of the present invention provides another method for document authority management, taking the server 102 as an example, in this embodiment, the first authority information of the document is stored in the encrypted document. At the same time, if the first permission information has been modified, the latest first permission information will be saved in the server 102 . When decrypting a document each time, the client 101 can go to the server 102 to detect whether the first authority information of the document has been modified. If it has been modified, the first authority information saved by the server will be used. If it has not been modified, the encrypted file itself will be used. The saved first permission information, such as image 3 As shown, the method includes:
[0059] Step 301, the server receives a permission request from the client;
[0060] Step 302. According to the permission request, determine whether the first permission information...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - Generate Ideas
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com