UNIX host safety configuration auditing method based on configurable knowledge base
A security configuration and knowledge base technology, applied in the field of security configuration auditing and security assessment of UNIX host systems, can solve problems such as leakage of enterprise sensitive information, security monitoring of UNIX host systems, information system damage, etc., to prevent audit content and results. The effect of leakage, protection of security and confidentiality, and avoidance of duplication of work
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
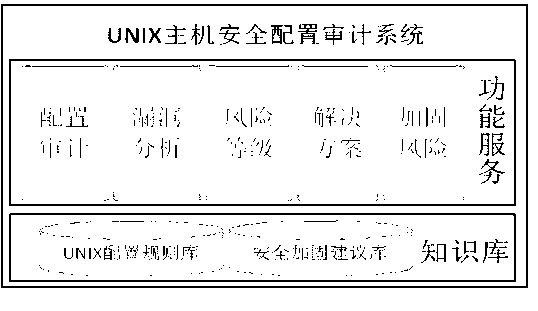
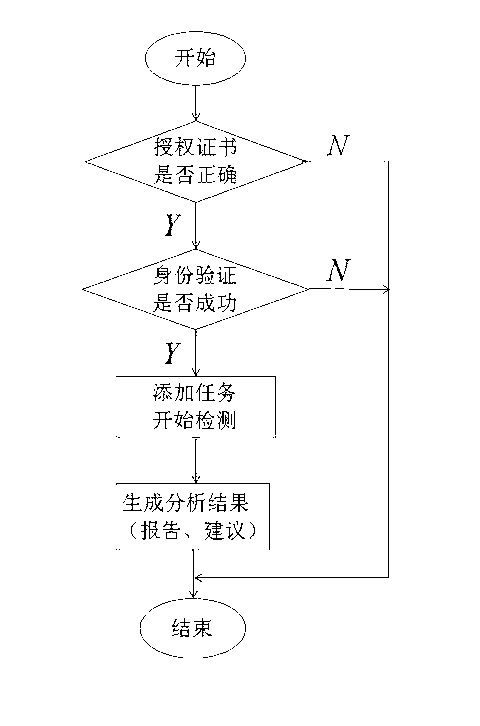
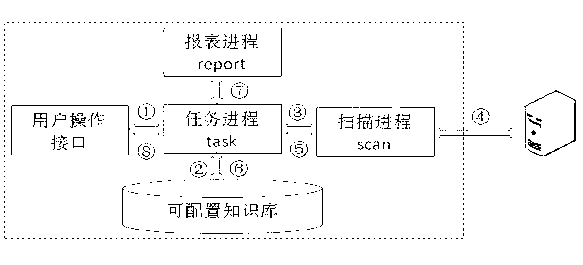
[0035] as attached figure 1 As shown, this method is supported by a "configurable knowledge base", including a UNIX configuration rule base and a security hardening suggestion base, and transmits user requirements in the form of scripts to the host system under test for security audit scanning, and organizes the scan results into structured data After the conversion, it is matched with the standard configuration rules and security hardening suggestion library in the knowledge base again to perform configuration audit, vulnerability analysis, risk rating, hardening implementation risk analysis, and form a report to provide users with security audit evaluation results and security implementation suggestions.
[0036] The "configurable knowledge base" is implemented by Access, which has the function of remote independent matching and analysis with user needs and background databases, so as not to affect the normal operation of the host business under test and leave no traces of o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com