Password authentication method in network application and system
A password verification and network application technology, applied in transmission systems, digital data authentication, instruments, etc., can solve problems such as user passwords being cracked, network application security reduction, password brute force cracking, etc., and achieve extraction security and brute force cracking Possibility reduction and safety improvement effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
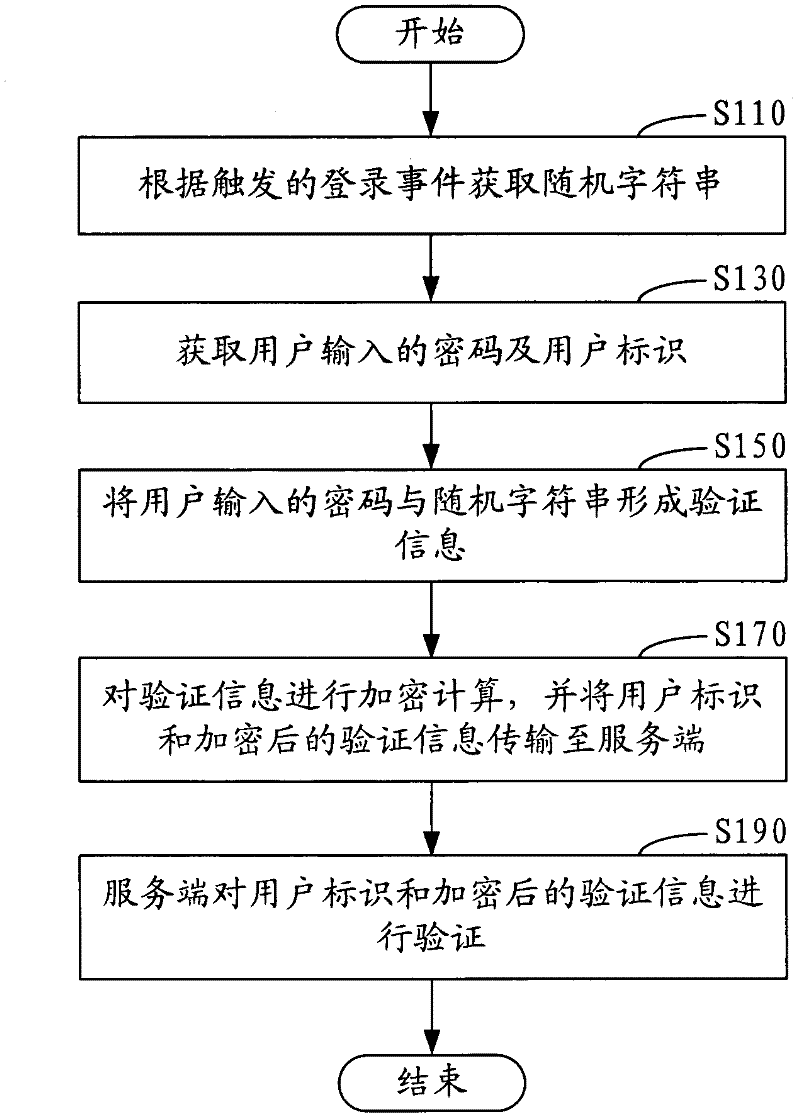
[0057] figure 1 It shows a password verification method in a network application in an embodiment, including the following steps:
[0058] Step S110, obtaining a random character string according to the triggered login event.
[0059] In this embodiment, the user enters the user ID and the corresponding password in the interactive interface of the network application, and clicks the "login" button, which triggers the login event. At this point, get a random string based on this triggered login event. Random character strings are randomly generated through random functions, etc., and the random character strings obtained by users every time they log in are different.
[0060] Step S130, acquiring the password and user ID input by the user.
[0061] In step S150, the password input by the user and the random character string are combined to form verification information.
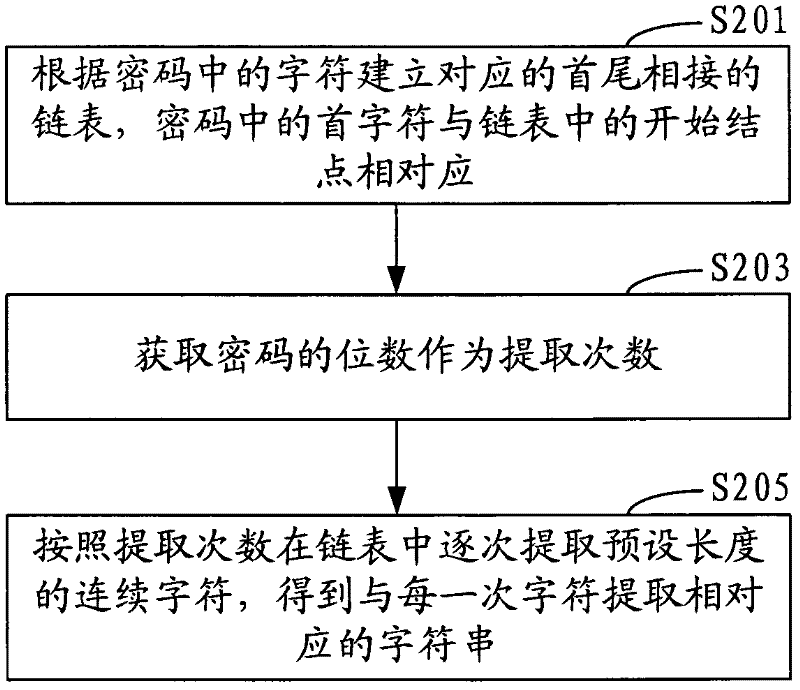
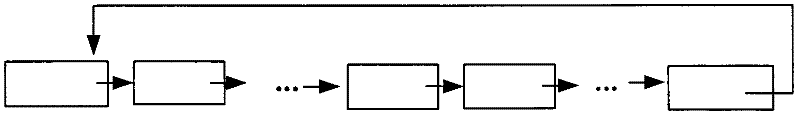
[0062] In this embodiment, the more digits of the password, the higher the security of the password may...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com