Three-layer key encryption method and bank transaction system
An encryption method and technology of a transaction system, applied in the field of bank transaction systems, can solve problems such as transmission failure, transaction data being cracked, and tampered with, and achieve the effect of ensuring transaction security, preventing internal control risks, and preventing cracking.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
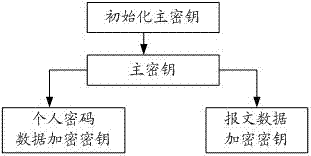
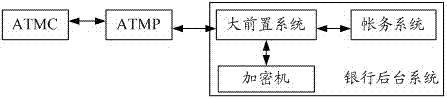
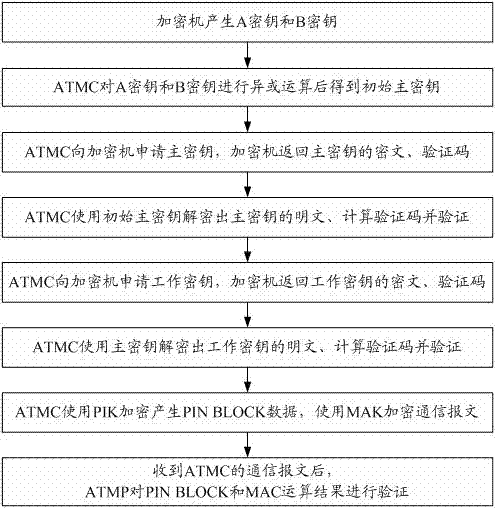
[0029] Such as figure 1 The flow chart of the three-layer key encryption process shown:
[0030] The first-level key is the Initial Master Key (IMK), which is used to encrypt / decrypt the master key using the 3DES algorithm. In a preferred embodiment, the length of the initialization master key is 16 bytes and 128 bits in length. For the convenience of use, it is generally converted into BCD code and provided, so it is 32 ASC code characters.
[0031] The second layer key is the master key (Master Key, MK), and the 3DES / DES algorithm is used to encrypt / decrypt the third layer. In a preferred embodiment, the length of the master key is 16 bytes and 128 bits, represented by 32 ASC code characters.
[0032] The third layer of keys is the work key, including personal password data encryption key (PIK) and message data encryption key (MAK). PIK is used to encrypt the cardholder's personal account number and password, with a length of 16 bytes and 128 bits, which can be expressed...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com