Method and system for triggering fixed-mobile convergence policy negotiation
A fixed network mobile convergence and policy technology, applied in the field of communication, can solve the problems of inability to initiate proactively, uncertainty, and not always guaranteed to trigger policy negotiation between fixed network and mobile network, etc., to achieve reliable support and stable QoS control.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
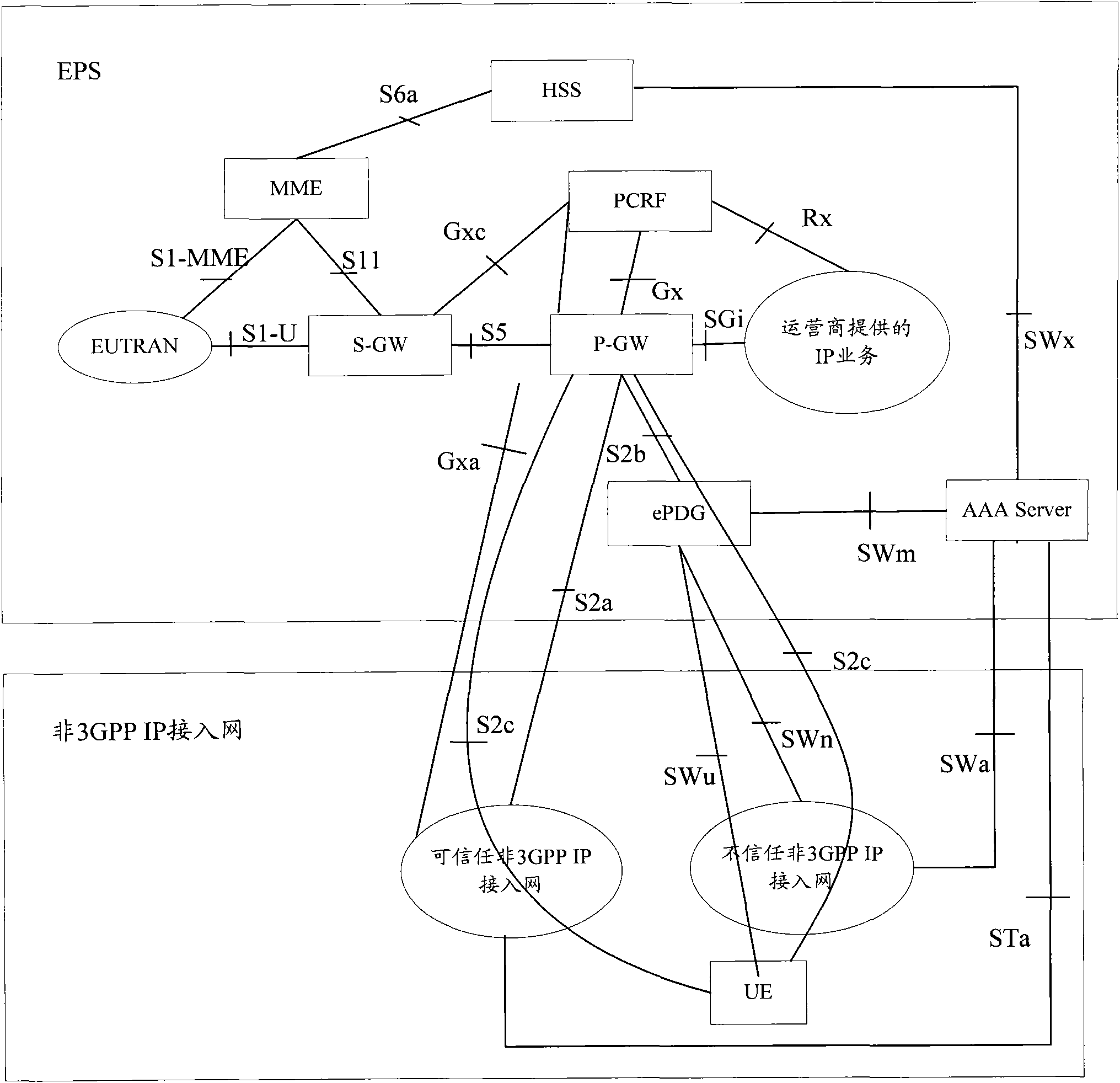
[0045] Image 6 In the S2b access scenario of the present invention, the ePDG and the 3GPP AAA Server / Proxy decide to activate the policy negotiation flow chart with the fixed network. This embodiment is applicable to the case where the fixed network is an untrustworthy non-3GPP access network, and the UE accesses the 3GPP core network through the S2b interface. Image 6 The process includes the following steps:
[0046] In step 601, the UE accesses through the BBF fixed network, and performs 3GPP-based access authentication. This step is optional. When 3GPP-based access authentication is not performed, the UE only needs to perform traditional fixed network access authentication. In this scenario, the BBF access network cannot perceive that the UE accesses the 3GPP core network.
[0047] Step 602, after the UE accesses the BBF access network, the BBF access network allocates a local IP address for the UE.
[0048] In step 603, the UE initiates an IKEv2 tunnel establishment ...
Embodiment 2
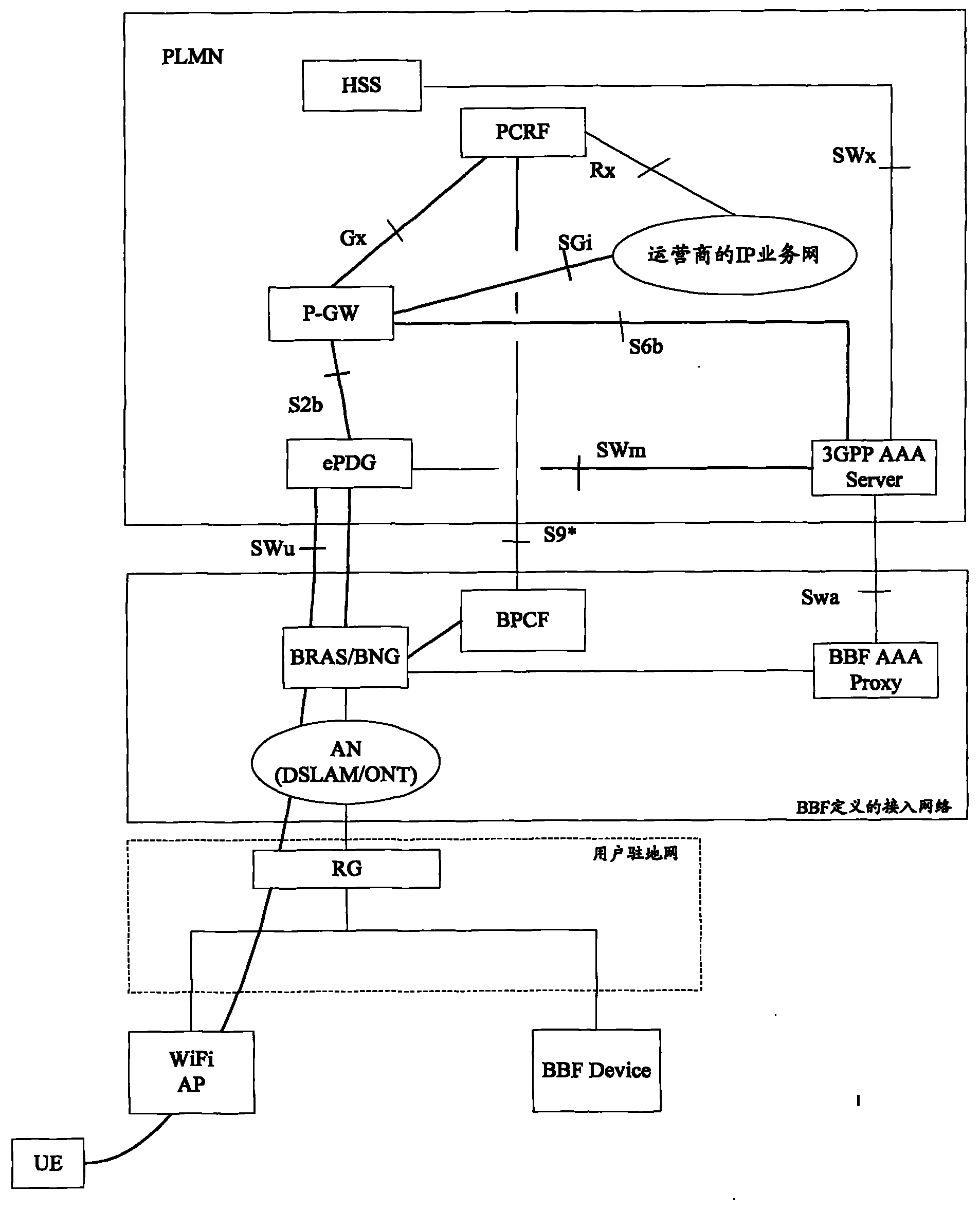
[0082] Figure 7 In the S2b access scenario of the present invention, the 3GPP AAA Server / Proxy decides to activate the policy negotiation flow chart with the fixed network. This embodiment is applicable to the case where the fixed network is an untrustworthy non-3GPP access network, and the UE accesses the 3GPP core network through the S2b interface. Figure 7 The process includes the following steps:
[0083] Step 701-Step 702: Same as Step 601-Step 602.
[0084] In step 703, the UE initiates an IKEv2 tunnel establishment process and uses EAP for authentication. In roaming scenarios, ePDG interacts with AAA Server through AAA Proxy (AAA Server further interacts with HSS) to complete EAP authentication,
[0085] Step 703a, step 703b, step 703c, and step 703d belong to the EAP authentication process. In the non-roaming scenario, execute step 703a, step 703b, and step 703d, and execute step 703a, step 703c, and step 703d in the roaming scenario.
[0086] Step 703a, the DER...
Embodiment 3
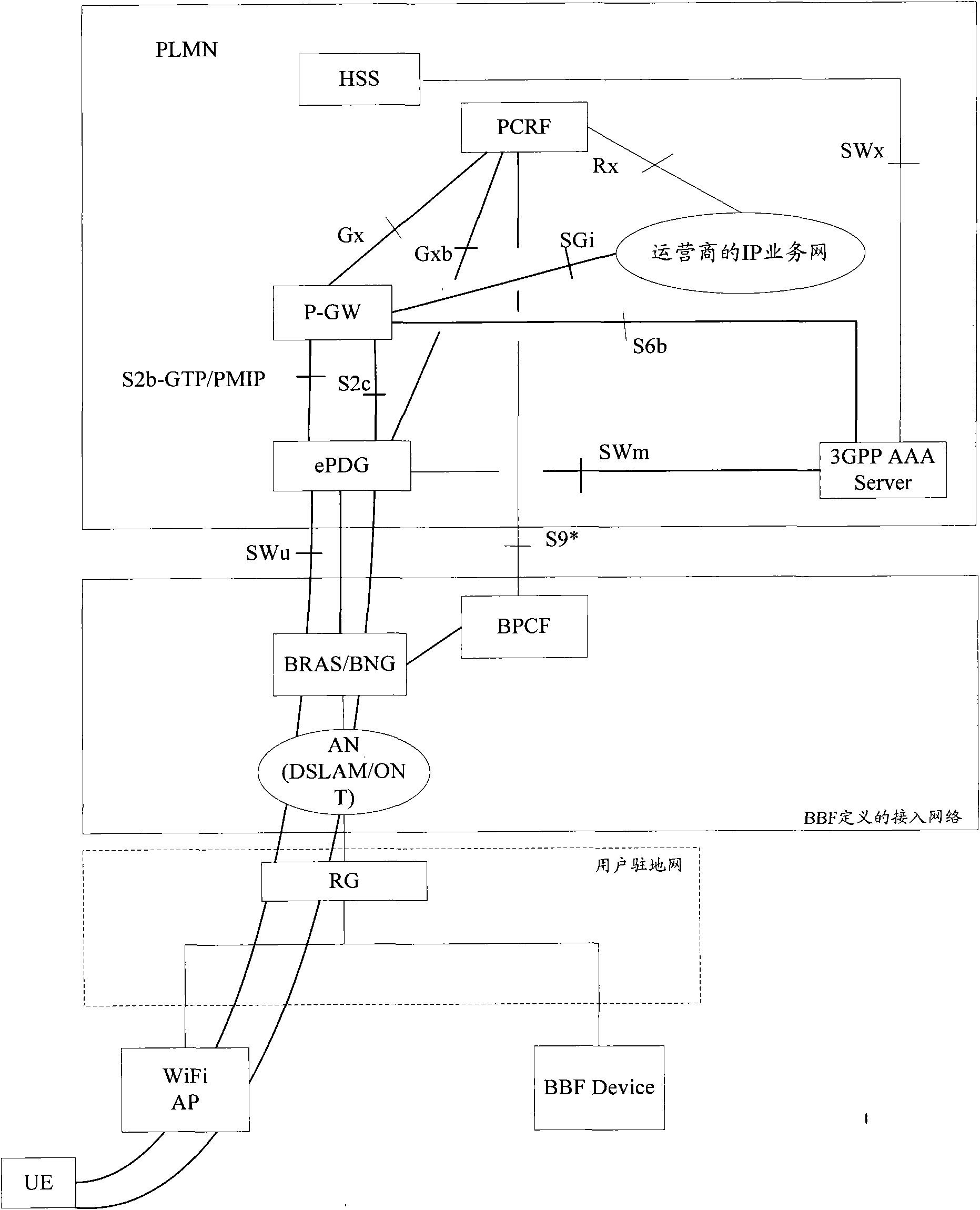
[0104] Figure 8 In the S2c access scenario of the present invention, the ePDG and the 3GPP AAA Server / Proxy decide to activate the policy negotiation flow chart with the fixed network. This embodiment is applicable to the case where the fixed network is an untrustworthy non-3GPP access network, and the UE accesses the 3GPP core network through the S2c interface. Figure 8 The process includes the following steps:
[0105] Step 801-Step 806: Same as Step 601-Step 606.
[0106] Step 807-step 808 are the same as: step 611-step 612.
[0107] In step 809, the UE executes the Bootstraping process. The UE performs DNS lookup according to the APN to obtain the IP address of the P-GW to access the PDN. In order to protect the DSMIPv6 message between UE and P-GW, UE uses IKEv2 to establish a security association and uses EAP for authentication. The P-GW communicates with the AAA Server (the AAA Server further interacts with the HSS) to complete EAP authentication, and at the same ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com