Coordinated monitoring method for preventing BGP routing hijacking
A border gateway protocol and routing technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problem of not getting targeted and effective network security services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
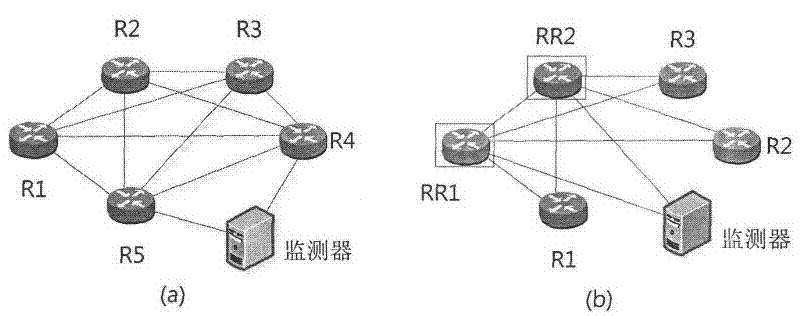
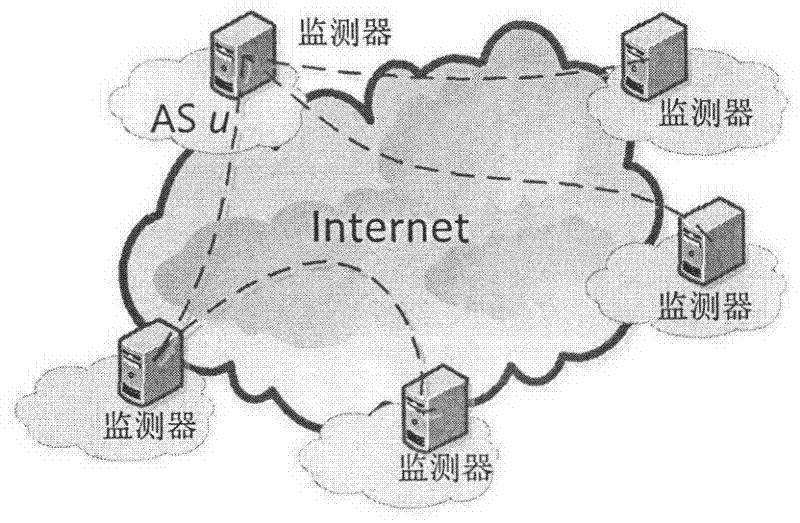
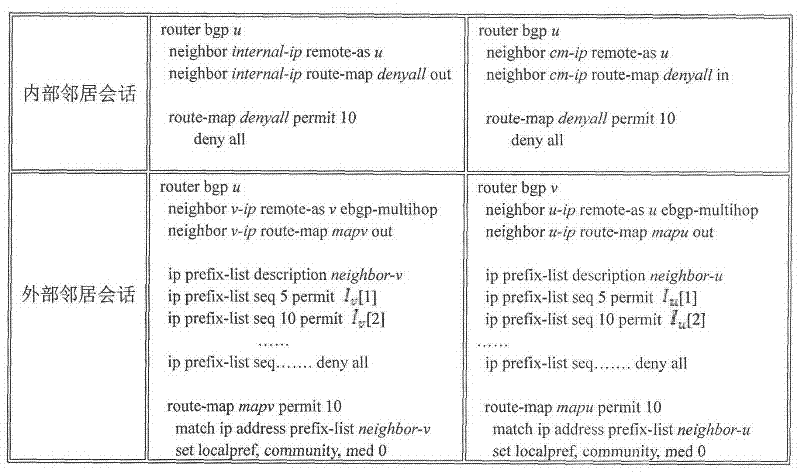
[0115] figure 1 It is a schematic diagram of the interconnection of monitors in an autonomous system (AS). For backup purposes, each monitor is preferably interconnected with two or more internal neighbors. There are various organizational forms of border routers inside an AS, including iBGP full mesh, route reflector, and BGP federation. Depending on the interconnection mode between the border routers inside the AS, the internal neighbors that the monitors are connected to are also slightly different. (1) For ASs using iBGP fully interconnected border routers, such as figure 1 As shown in (a), the monitor needs to establish a BGP session with any two or more routers among them; (2) for the AS that adopts the route reflection deployment method, such as figure 1 As shown in (b), the monitor needs to establish a BGP session with any two or more of the route reflectors (Route Reflector, RR), and the monitor is configured as a client (Route Client, RC) of the route reflector; (...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com