Process threading-based copy-protection system and copy-protection storage medium
A storage medium and anti-copy technology, applied in the direction of preventing unauthorized use of memory, program/content distribution protection, special data processing applications, etc., can solve problems such as complex systems, unsupported output devices and ports, and inability to guarantee document security, etc. , to achieve the effect of solving the security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0064] The following is attached Figure 1-6 Embodiments of the present invention are further described:
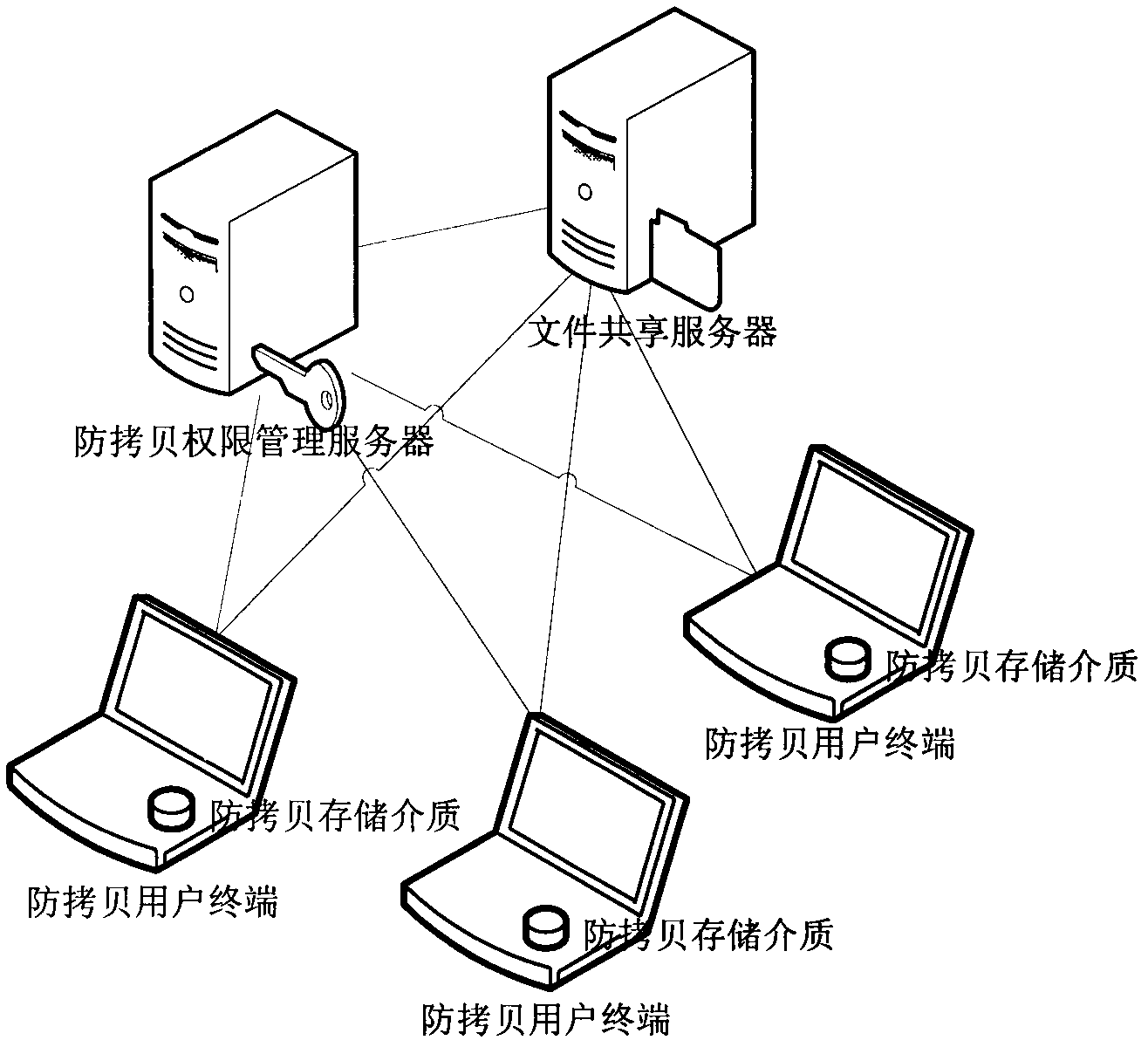
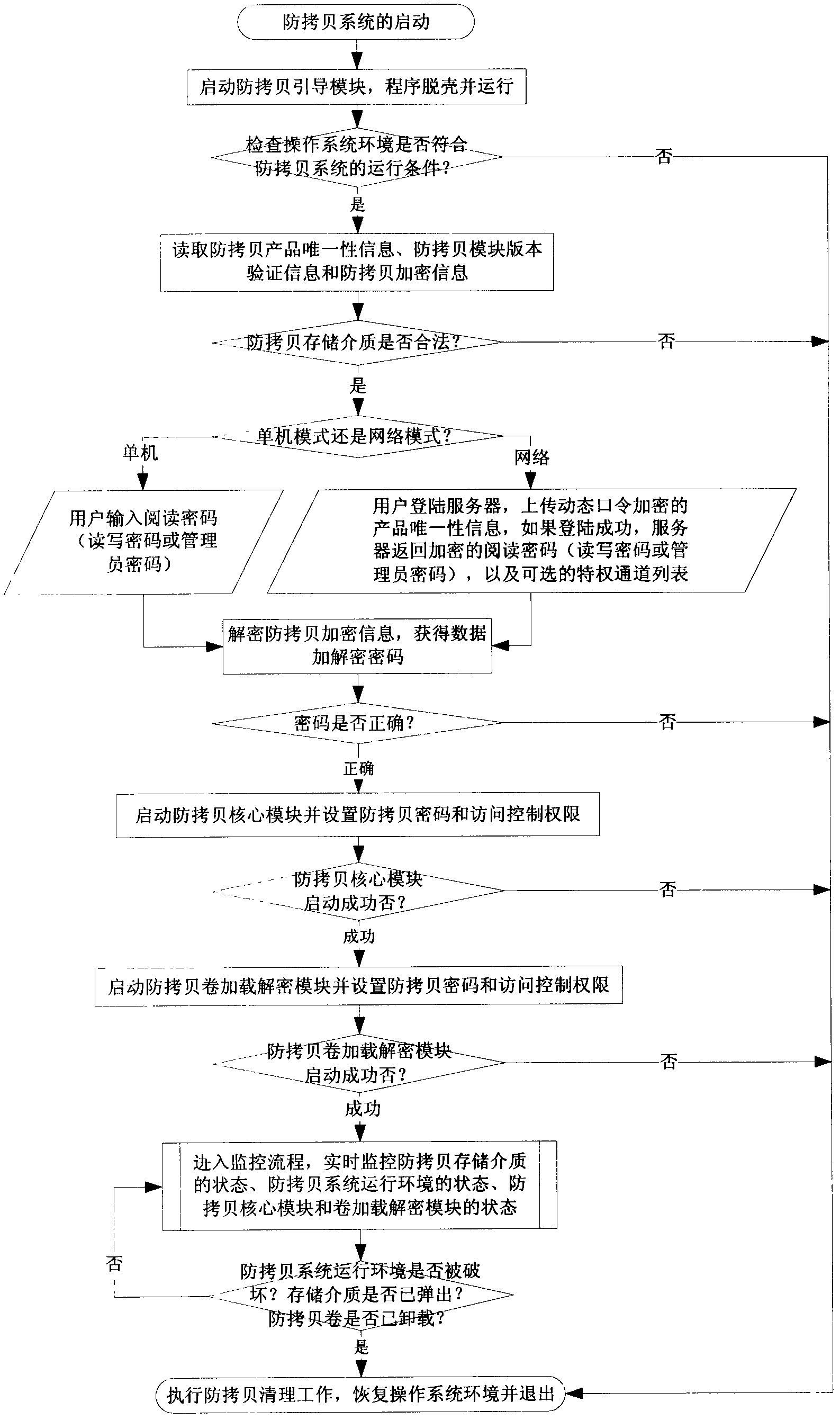
[0065] The present invention provides a process thread-based anti-copy system and method, and the corresponding storage medium technology. Using the method described in this technology can not only protect users in a stand-alone environment, but also in a network environment. The content of files in the copy-proof storage medium cannot be browsed, copied or stolen by unauthorized users, and it can also ensure that the entire storage medium is not illegally copied. This method encrypts the documents and data that the user needs to protect the copyright and content, and stores them in the anti-copy storage medium in a disorderly manner. The rules of encryption and decryption keys are encoded in the code of the anti-copy system protected by the encryption shell, which forms a strong protection for the user's digital copyright content; any process and thread that opens the a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com