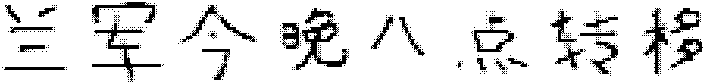Method for carrying out secret communication by using word document
A technology for confidential communication and documents, applied in the field of confidential communication using word documents, can solve the problems of inapplicable confidential letters, easy leakage of character passwords, etc., and achieves the effect of saving software costs, not easy to leak, and having good versatility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] 1. Assume that the confidential content to be transmitted is: "Lanjun transfer at 8 o'clock tonight", the specific operation steps are as follows:
[0032] (1) Use the TrueType word-making program to make confidential characters and generate keys: open the TrueType word-making program attached to the windows operating system, click "Choose Code" in the "Edit" drop-down menu, and a code box will appear, choose one arbitrarily Code (assuming aaa1 is selected), press Enter, and an edit box appears, select a tool in the "Tool" drop-down menu, and write the first secret character "lan" in the edit box, or first write the first secret character of the electronic version "Lan" is copied on the office clipboard, and then after the above edit box appears, select "Copy Character" in the "Edit" drop-down menu. After the dialog box appears, follow the prompts to paste the characters in the office clipboard into the edit box , and then click "Save Characters" in the "Edit" drop-down...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com