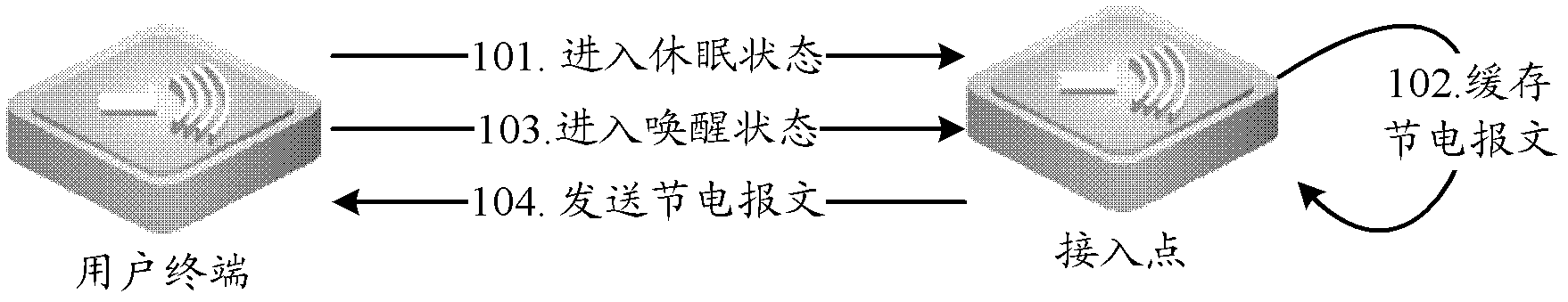
Message caching method and access point
A message buffering and access point technology, applied in advanced technologies, data switching networks, power management, etc., can solve problems such as system failures, cache power-saving message occupation, etc., to avoid system failures, effectively control storage space, Guaranteed effect of power saving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
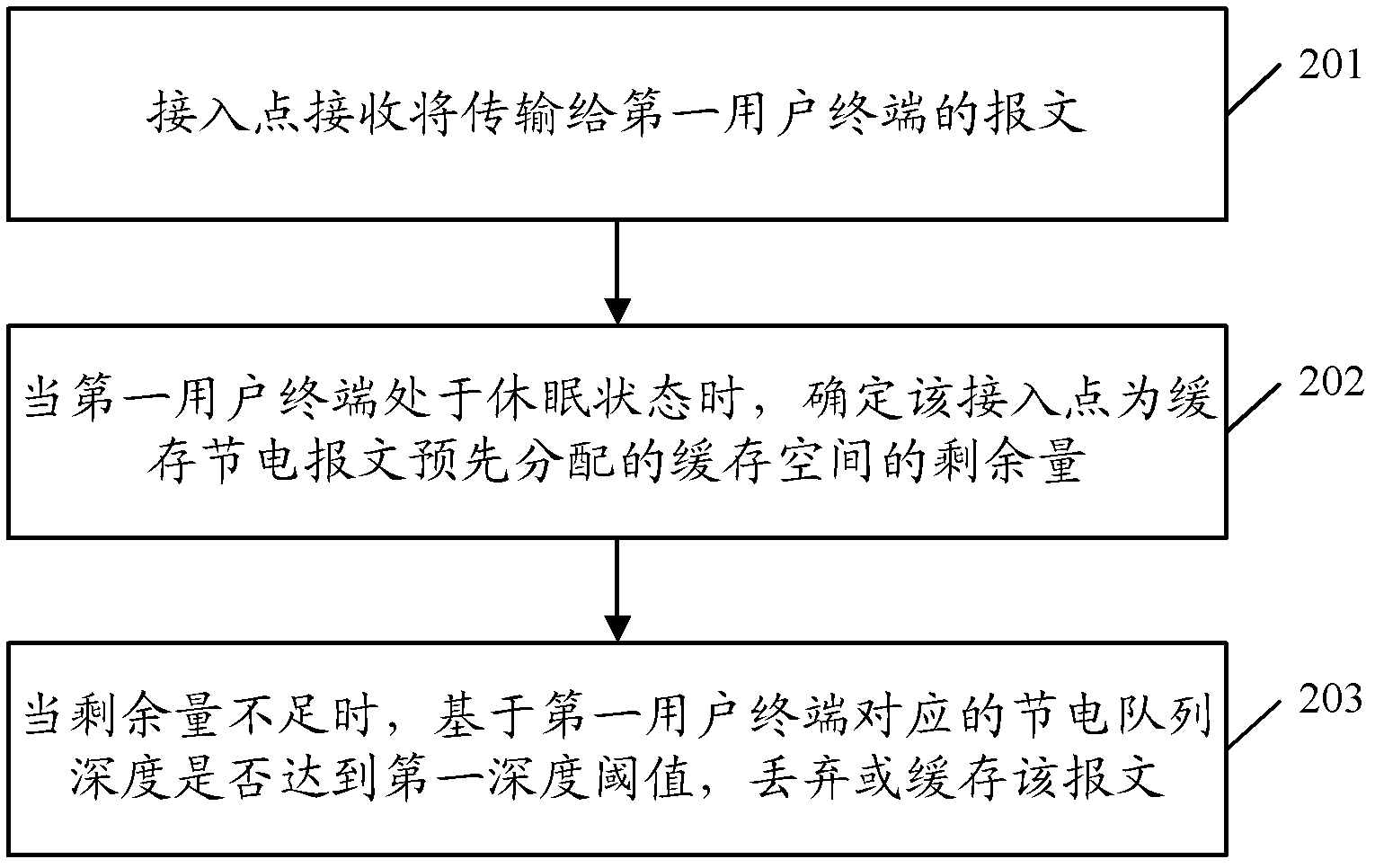
[0043] image 3 Shown is a flow chart of the message buffering method provided in Embodiment 1 of the present invention, which specifically includes the following processing steps:
[0044] In step 301, the access point receives a message to be transmitted to the first user terminal, and the first user terminal belongs to the access point.
[0045] Step 302 , judging whether the first user terminal is in a dormant state, if not in a dormant state but in an awake state, proceed to step 303 , and if in a dormant state, proceed to step 304 .
[0046] Step 303: Send the message to the first user terminal.
[0047] Step 304 , the access point determines the remaining amount of buffer space pre-allocated by itself for caching the power-saving message, that is, the value of the allocated buffer space minus the space occupied by the current cache of the power-saving message.
[0048] In this embodiment, the remaining amount of the pre-allocated buffer space can be updated and saved ...
Embodiment 2
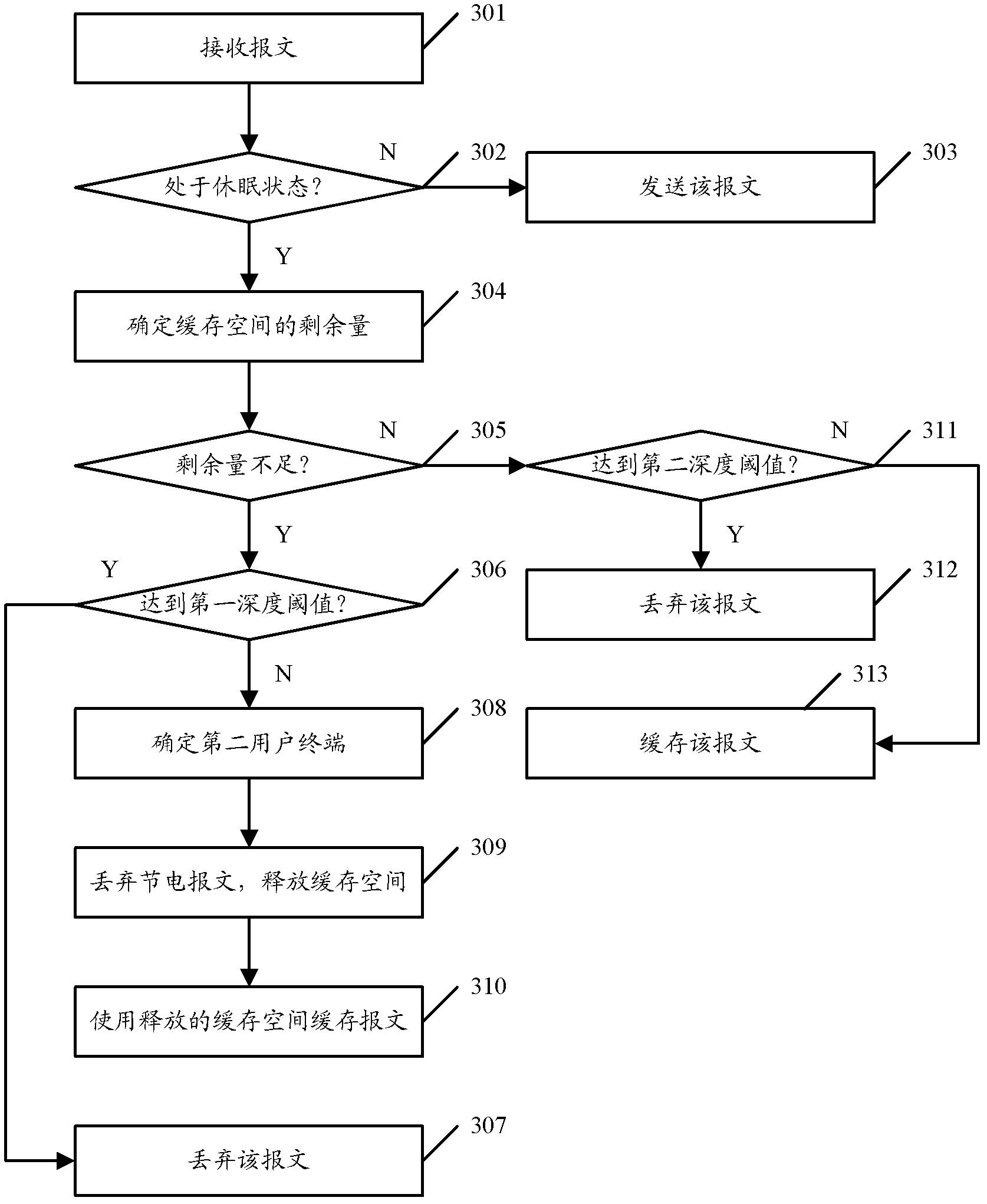
[0065] Figure 4 Shown is a flow chart of the message caching method provided in Embodiment 2 of the present invention, which specifically includes the following processing steps:
[0066] Step 401, the access point receives a message to be transmitted to the first user terminal, and the first user terminal belongs to the access point.
[0067] Step 402 , judging whether the first user terminal is in a dormant state, if not in a dormant state but in an awake state, proceed to step 403 , and if in a dormant state, proceed to step 404 .
[0068] Step 403: Send the packet to the first user terminal.
[0069] Step 404 , judging whether the power saving queue depth corresponding to the first user terminal reaches the second depth threshold, if yes, proceed to step 405 , if not, proceed to step 406 .
[0070] Wherein, the second depth threshold is used to limit the maximum value of the power-saving queue depth corresponding to each user terminal.
[0071] Step 405: When the depth...
Embodiment 3
[0086]Based on the same inventive concept, according to the message caching method provided by the above-mentioned embodiments of the present invention, correspondingly, Embodiment 3 of the present invention also provides an access network, whose structural diagram is as follows Figure 5 shown, including:
[0087] a receiving unit 501, configured to receive a message to be transmitted to the first user terminal;
[0088] A buffer space determining unit 502, configured to determine the remaining amount of buffer space pre-allocated by the access point for buffering power-saving messages when the first user terminal is in a dormant state;
[0089] The cache processing unit 503 is configured to discard the message when the remaining amount is insufficient and the power-saving queue depth corresponding to the first user terminal reaches a first depth threshold, and the first depth threshold is the allocated The value of dividing the buffer space by the number of user terminals c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com