Method and device for collecting malicious software automatically
A malicious software and automatic collection technology, applied in computer security devices, instruments, electrical digital data processing, etc., can solve the problems of low reliability and detection rate, high difficulty and cost, easy failure of malicious software, etc., and achieve reliability and the effect of improving the detection rate and improving efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
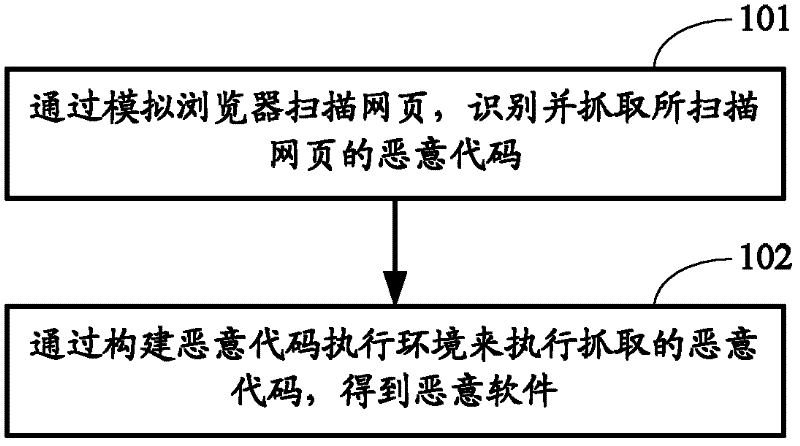
[0058] figure 1 The flow chart of the method for automatically collecting malware provided by Embodiment 1 of the present invention, such as figure 1 As shown, the method includes:
[0059] Step 101: Scanning a webpage by simulating a browser, identifying and capturing malicious codes of the scanned webpage.
[0060] In this step, the webpage is actively scanned by simulating the browser, and the malicious code is identified and captured from the scanned webpage in combination with malicious code identification technology. The specific malicious code identification method may include: firstly, analyze the scanned webpage script, if the corresponding function is obtained in the memory through pre-installed function hooks for writing shellcode during the analysis process For binary data, one or any combination of blacklist matching, disassembly detection, and high-risk bytecode statistics is used to identify malicious code. The specific process will be described in detail in ...
Embodiment 2
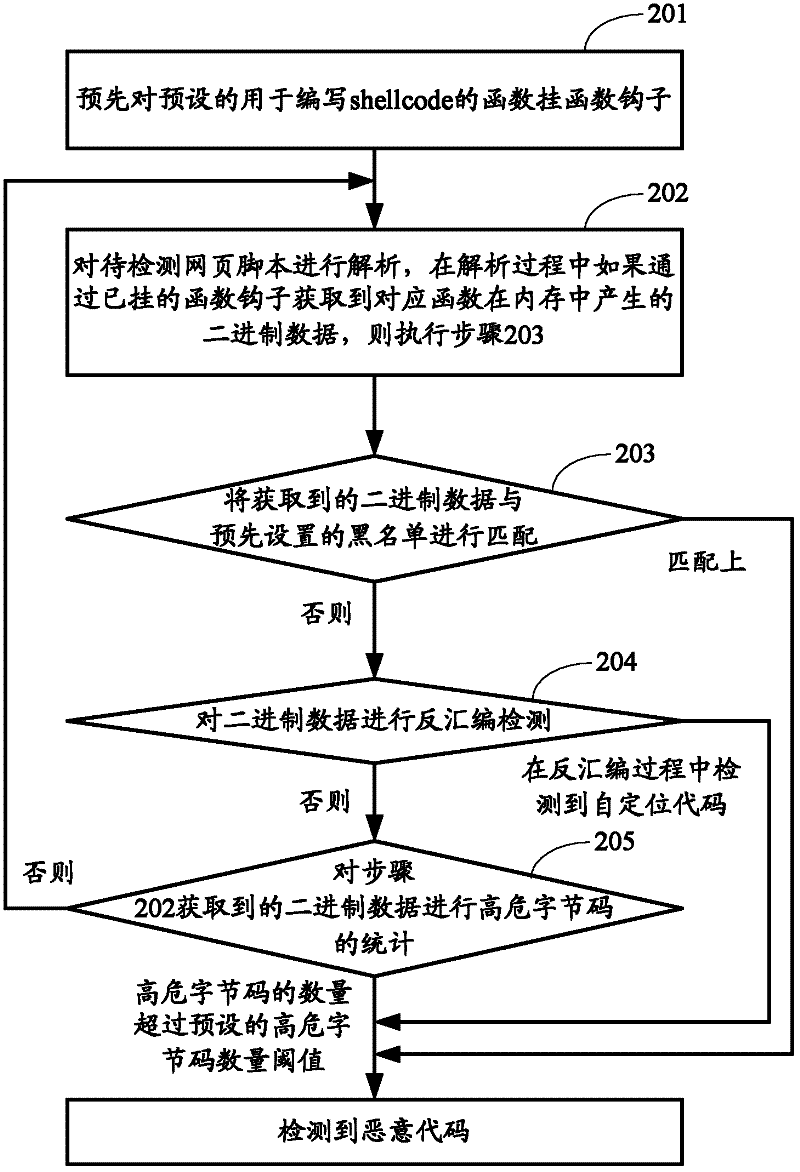
[0064] figure 2 The flow chart of the method for identifying malicious codes provided by Embodiment 2 of the present invention, such as figure 2 As shown, the method may include the following steps:
[0065] Step 201: pre-hooking a preset function for writing shellcode.
[0066] Usually, webpage scripts write shellcode through a series of script functions, so that controllable malicious data can be generated in memory for attack, that is, these functions used to write shellcode can generate binary data in a specified format in memory. These preset functions for writing shellcode may include, but are not limited to: the \u function for escaping in javascript-type scripts, the unescape function for string decoding, or string for returning a string represented by an ASCII value. at least one of the fromcharcode function, the unescape function of the vbscript type script, the string.fromcharcode function, or the chrw function for returning the character associated with the spe...
Embodiment 3
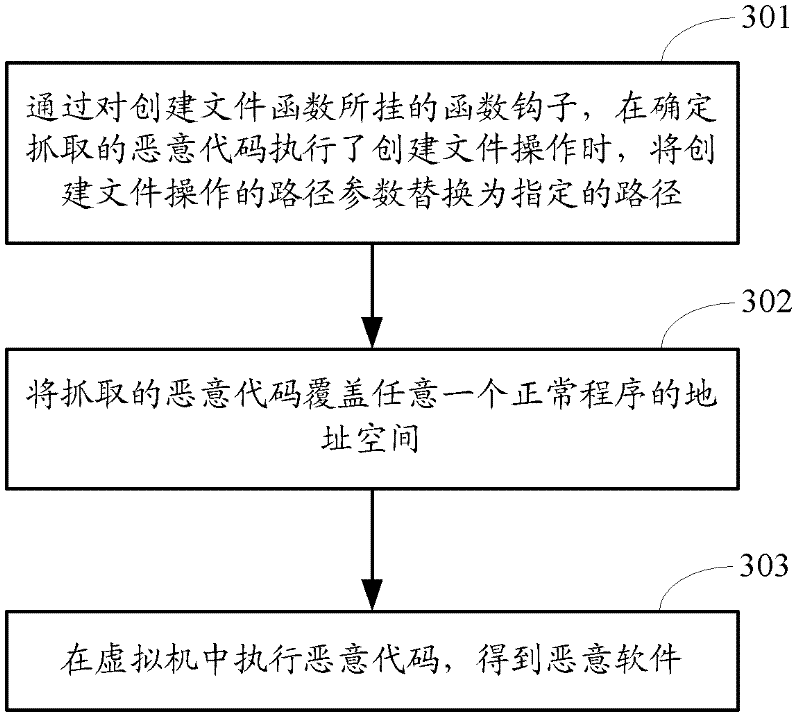
[0093] image 3 The flow chart of the method for obtaining malicious software provided by Embodiment 3 of the present invention, such as image 3 As shown, the method may include the following steps:
[0094] Step 301: By hooking the function hook of the file creation function, when it is determined that the captured malicious code executes the file creation operation, replace the path parameter of the file creation operation with the specified path.
[0095] The file creation function here may include but not limited to: functions such as NtCreateFile, ZwCreateFile, etc. Function hooks are hung on the bottom layer of the system in advance to monitor whether the malicious code executes the file creation operation.
[0096] The replacement of the path parameter is to enable the malicious code to transfer the malicious software to the specified path, that is, to the specified directory when creating the malicious software.
[0097] Step 302: Cover the address space of any norm...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com