Memory protection method based on unequal-length counter
A technology of memory protection and long counter, which is applied in the protection of internal/peripheral computer components, instruments, calculations, etc., and can solve the problem of consuming large main memory space
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
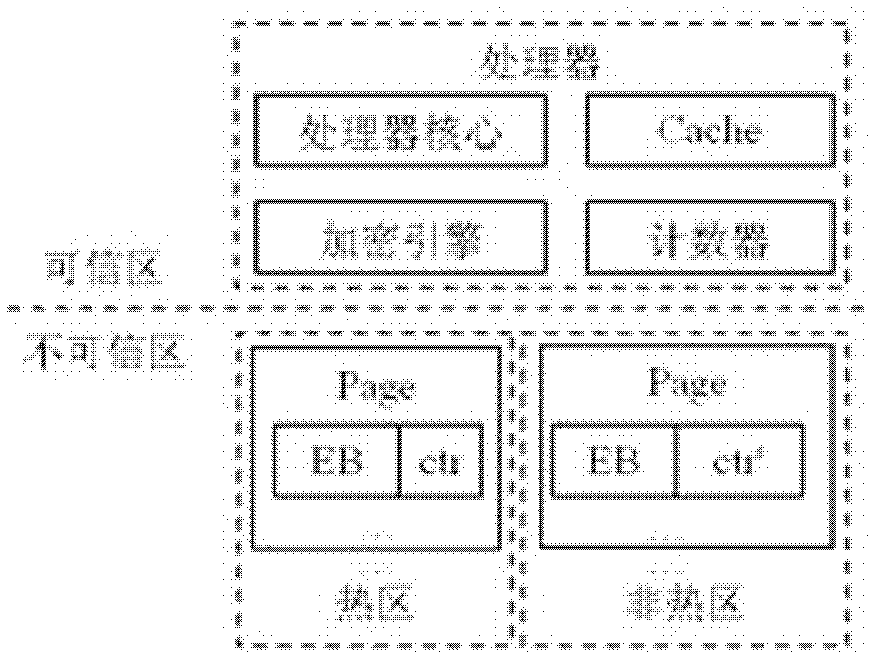
[0020] to combine figure 1 . The upper part of the picture is the processor, which is the trusted zone, which can prevent software and hardware attacks. The processor has processor core, L2-cache, encryption engine and counter and other components. The lower part of the picture is the memory, which is the untrusted zone. May be attacked by hardware, it includes non-hot area and hot area, each area has multiple pages (Page), a page has multiple ciphertext blocks (EB) and counter value (ctr or ctr'), the hot area The space occupied is small, and the ctr is long; the non-hot area occupies a large space, and the ctr is short.
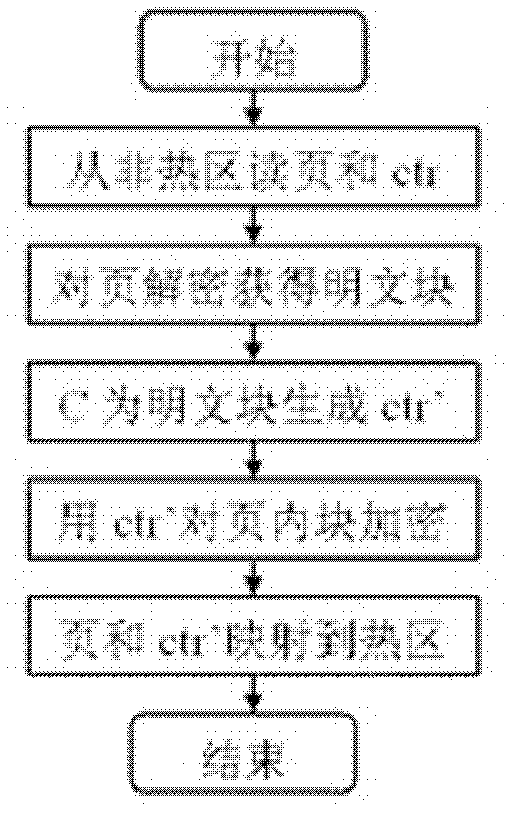
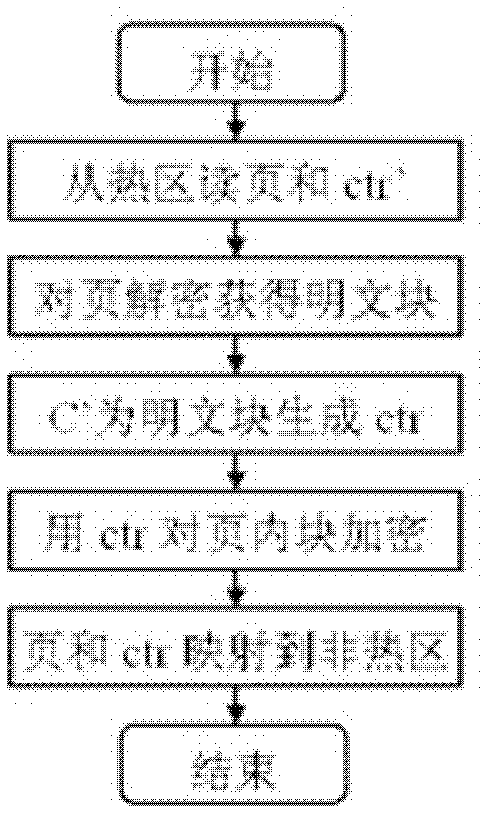
[0021] to combine figure 2 . Read the page and the corresponding counter value (ctr) from the non-hot area; use the non-hot area key to decrypt the page in counter mode to obtain the plaintext block; the counter (C) in the hot area generates a new counter value for each plaintext block in the page (ctr'); counter-mode encryption of a plaintext block wi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com