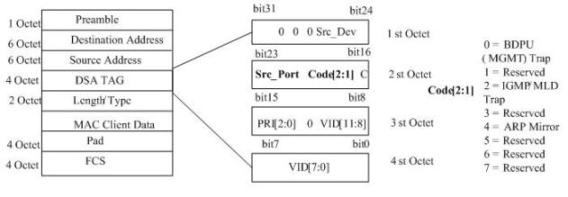
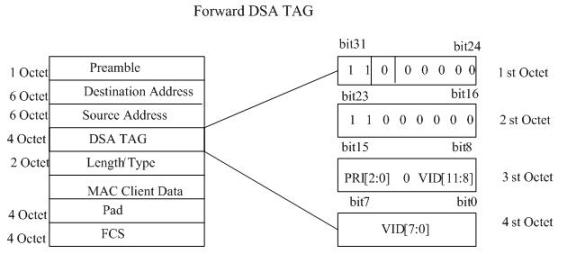
Method for implementing network bridge IGMP (internet group management protocol) Snooping based on DSA TAG (digital signature algorithm tag) and user-defined protocol stack
A technology of self-defined protocol and implementation method, which is applied in the direction of network interconnection, data exchange network, data exchange through path configuration, etc. It can solve the problems affecting the VLAN function of the device and the inability to realize the IGMPSnooping function, so as to fill the gap in the market and save Effect of hardware cost
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
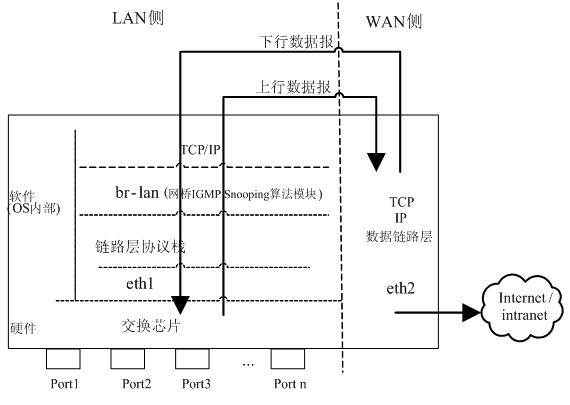
[0020] The present invention proposes a bridge IGMP (Internet Group Management Protocol) Snooping implementation method based on DSA (Distributed Switching Architecture) TAG and self-defined protocol stack, using the combination of software and hardware to realize the IGMP Snooping function well, saving hardware cost, filling a gap in the market.
[0021] The implementation method of bridge IGMP Snooping based on DSA TAG and custom protocol stack involves bridge IGMP Snooping algorithm module, custom data link layer IGMP protocol stack and switching chip, and the three work together to realize IGMP Snooping function under Linux bridge. The positions of the three in the three-layer network equipment are as follows: figure 1 As shown, it is set that the switch chip of this network device has n physical ports, eth1 is the network device node, and is the abstraction of the main processor MAC (Media Access controller) in the Linux system. On the LAN side, the main processor MAC an...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com