Coding-decoding method based on communication of access control system
An encoding and decoding method and access control system technology, which are applied in the directions of instruments, time registers, individual input/output registers, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
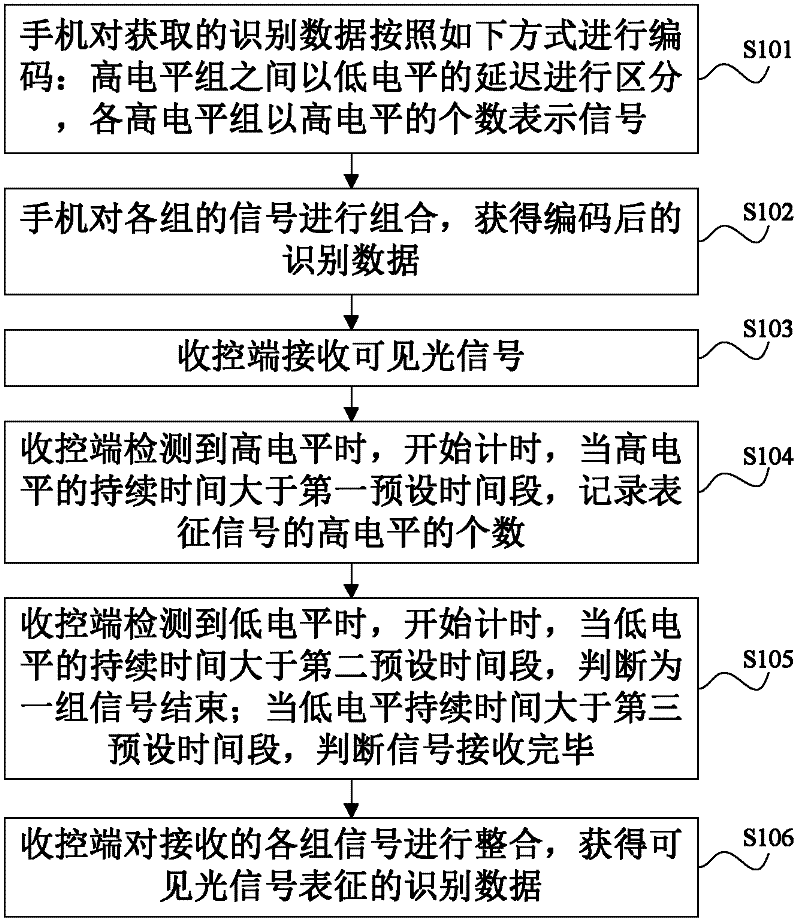
[0015] see figure 1 , is a flowchart of an encoding and decoding method based on communication of an access control system provided in Embodiment 1 of the present invention, and the encoding method includes:
[0016] S101: The mobile phone encodes the acquired identification data in the following manner: high-level groups are distinguished by low-level delays, and each high-level group represents a signal by the number of high levels.
[0017] Among them, the mobile phone is used as the sending end of the access control system.
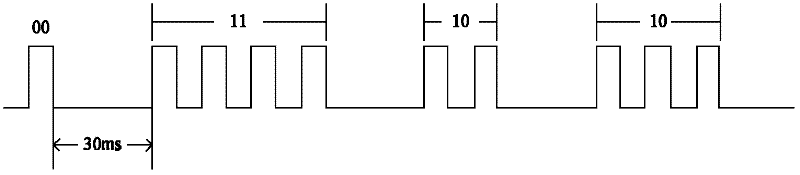
[0018] For example, the duration of each high level is 2ms, each group has a maximum of four high levels, each group of levels represents a 2bit signal, and four groups of signals represent a byte. That is: when the number of high levels in a group of signals is 1, it represents 00; when the number of high levels is 2, it represents signal 01; when the number of high levels is 3, it represents signal 10; when the number of high levels is 3, it repres...
Embodiment 2
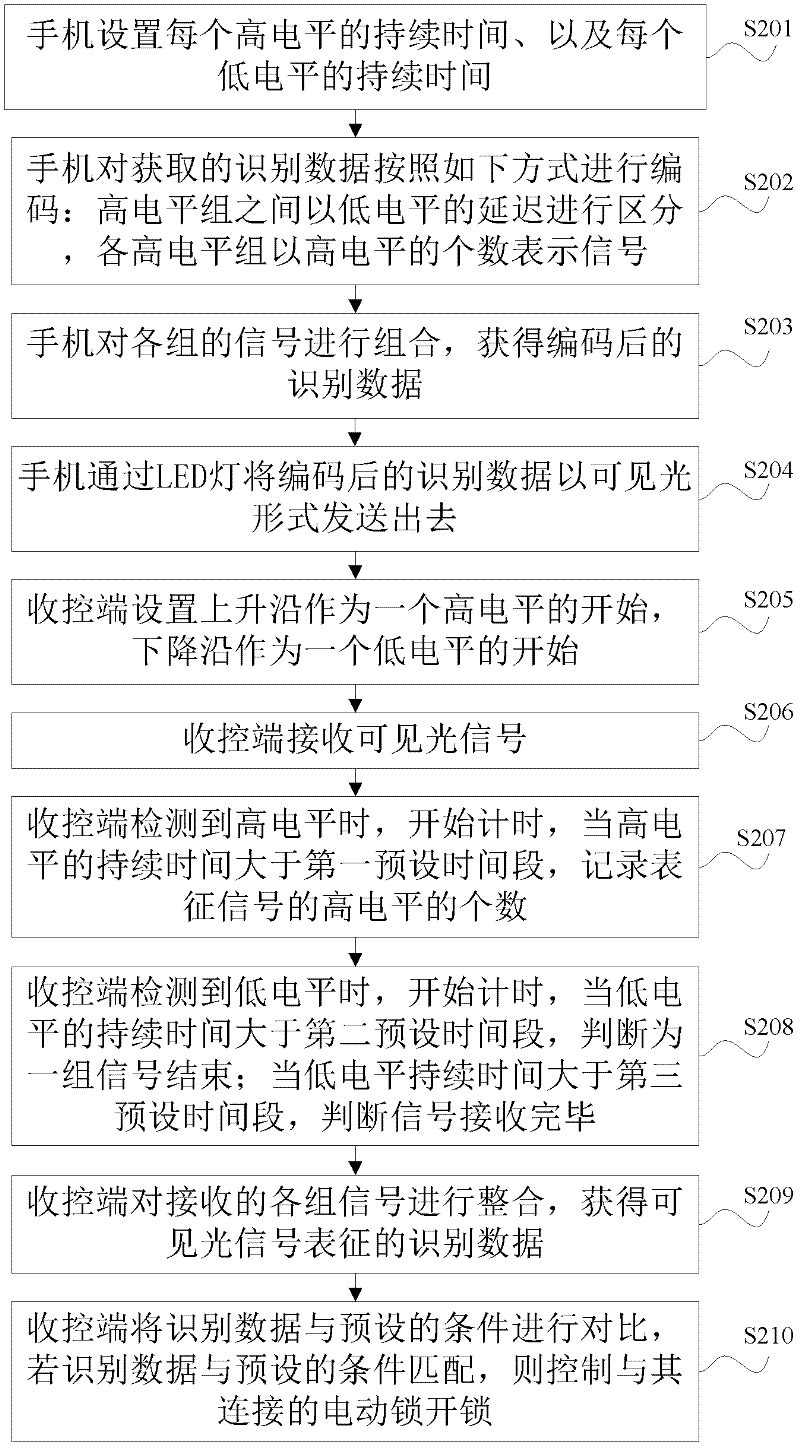
[0030] see image 3 , is a flow chart of an encoding and decoding method based on communication of an access control system provided in Embodiment 2 of the present invention, and the method includes:
[0031] S201: The mobile phone sets the duration of each high level and the duration of each low level. For example, set the duration of each high level to be 2ms, and the duration of each low level to be 30ms.
[0032] Among them, the mobile phone is used as the sending end of the access control system.
[0033] S202: The mobile phone encodes the acquired identification data in the following manner: high-level groups are distinguished by low-level delays, and each high-level group represents a signal by the number of high levels.
[0034] For example, the duration of each high level is 2ms, each group has a maximum of four high levels, each group of levels represents a 2bit signal, and four groups of signals represent a byte. That is: when the number of high levels in a group...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com