Processing system and method for internet key exchange (IKE) remote access
A remote access and processing system technology, applied in the field of IKE remote access processing system, can solve problems affecting server performance, limited number of firewall users, and other users cannot access the server, etc., to achieve the effect of improving performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
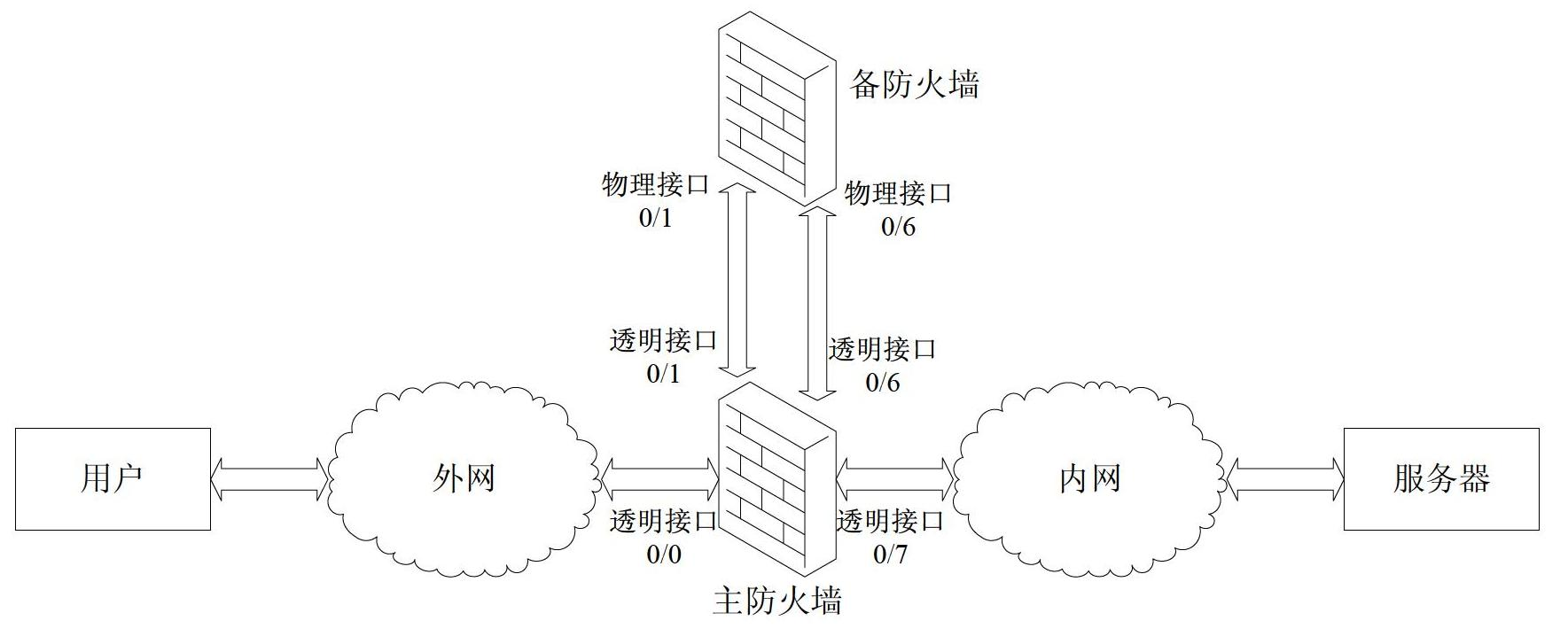
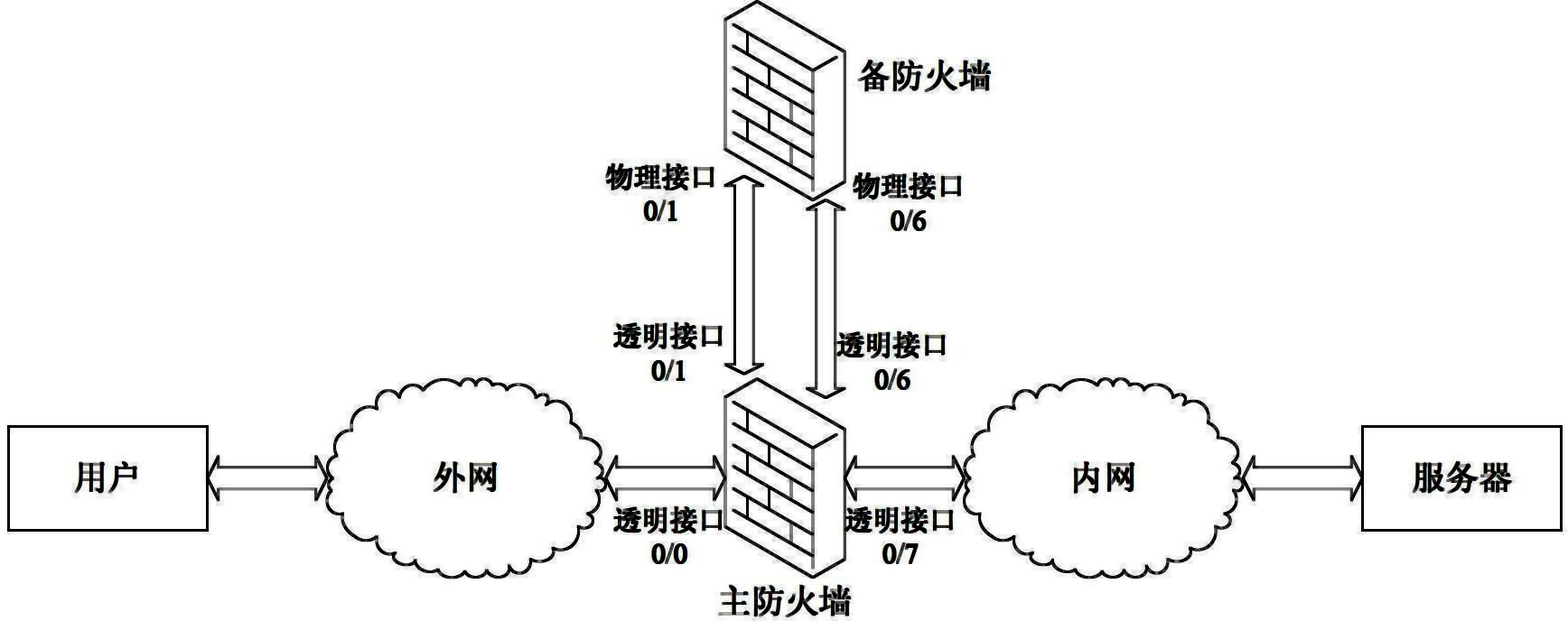
[0035] figure 1 It is a structural diagram of a processing system for IKE remote access according to an embodiment of the present invention. In this embodiment, a firewall is used as an example to illustrate the present invention, but it is not used to limit the protection scope of the present invention; refer to figure 1 , the system includes: a main firewall and a backup firewall, the server of the internal network and the user of the external network are connected through the main firewall, and when the main firewall receives the current IKE negotiation message, the total number of negotiations of the main firewall is judged Whether the maximum value has been reached, if so, then the current IKE negotiation message is sent to the standby firewall for negotiation, otherwise the main firewall negotiates the current negotiation message, preferably, the standby firewall and the standby firewall above the primary firewall connection.
[0036] In this embodiment, the four physic...
Embodiment 2
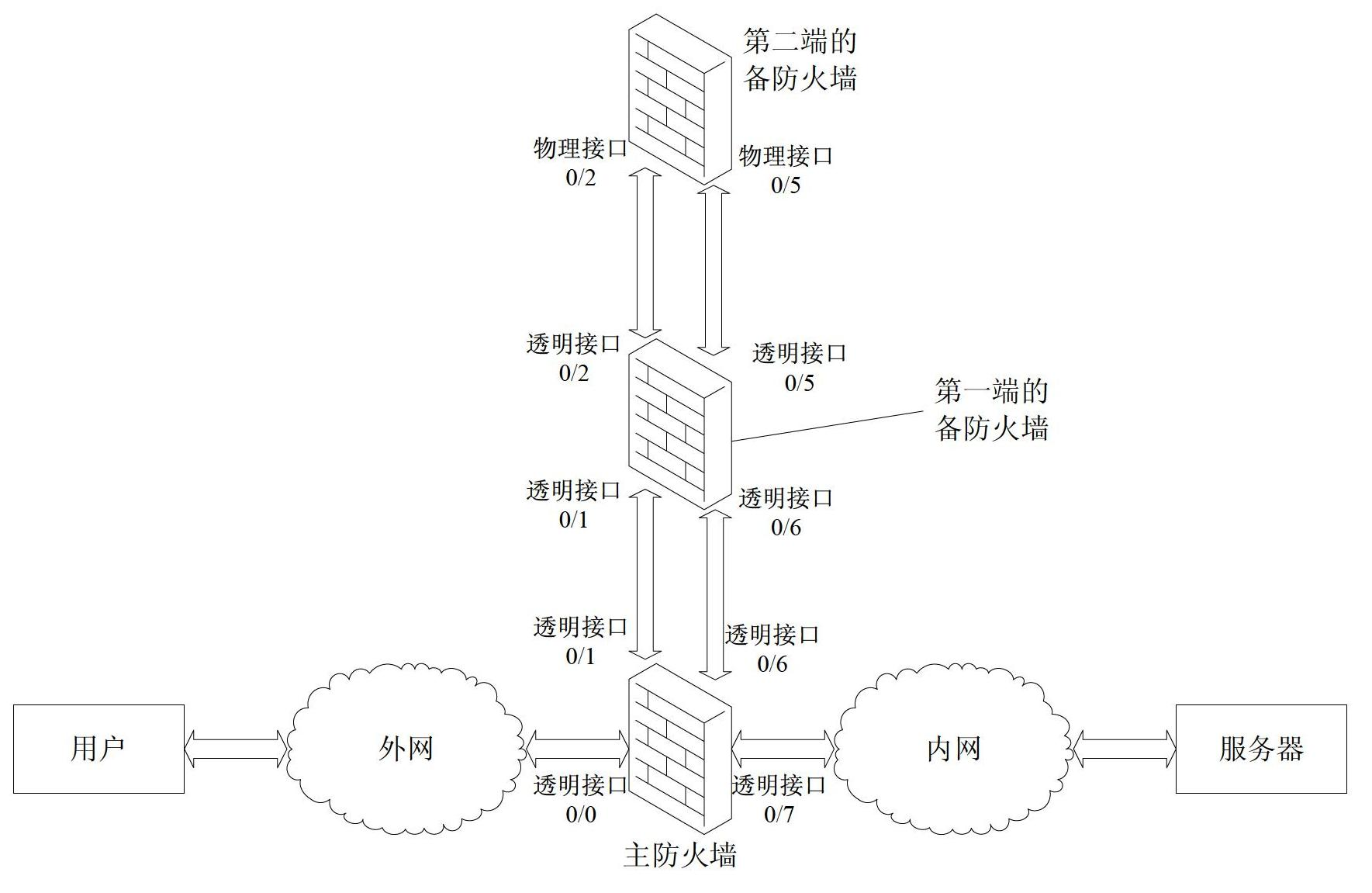
[0060] refer to figure 2 , the structure of the system of this embodiment is basically the same as that of the embodiment, the difference is that this embodiment is provided with two backup firewalls, the two backup firewalls are connected in a chain, and the backup firewall at the first end is connected to the above the primary firewall connection.
[0061] In this embodiment, the four physical interfaces on the main firewall are configured as transparent interfaces (that is, transparent interfaces "0 / 0", "0 / 1", "0 / 6" and "0" on the main firewall in the figure / 7"), and divide the transparent interfaces on the main firewall into two groups evenly (the transparent interfaces "0 / 0" and "0 / 1" on the main firewall in the figure are the first group, and "0 / 6" and "0 / 7" are the second group), and each group of transparent interfaces is configured with a virtual interface;
[0062] The four physical interfaces on the standby firewall at the first end are configured as transparent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com