SQL (structured query language) injection attack protection method based on database
A technology of injection attacks and databases, applied in the field of network security, it can solve problems such as tangible and intangible losses, great harm, and external access impact.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The specific embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
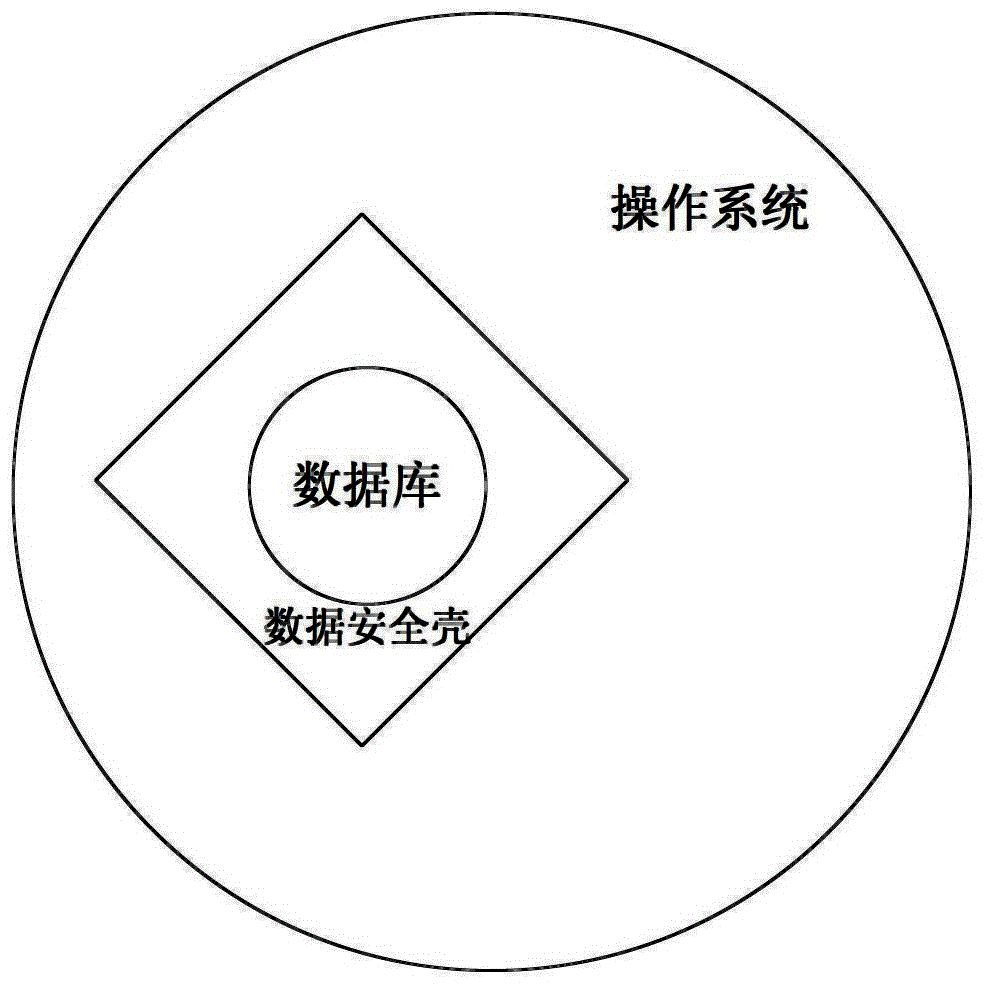
[0030] Such as figure 1 As shown, the data security shell of the present invention is a bottom driver built on the operating system layer, and uses a virtual space made of a hard disk cache (caching), and loads the database in this space. When external data accesses the database, it must pass through the data security shell, and the data security shell is responsible for the internal and external exchange of data.
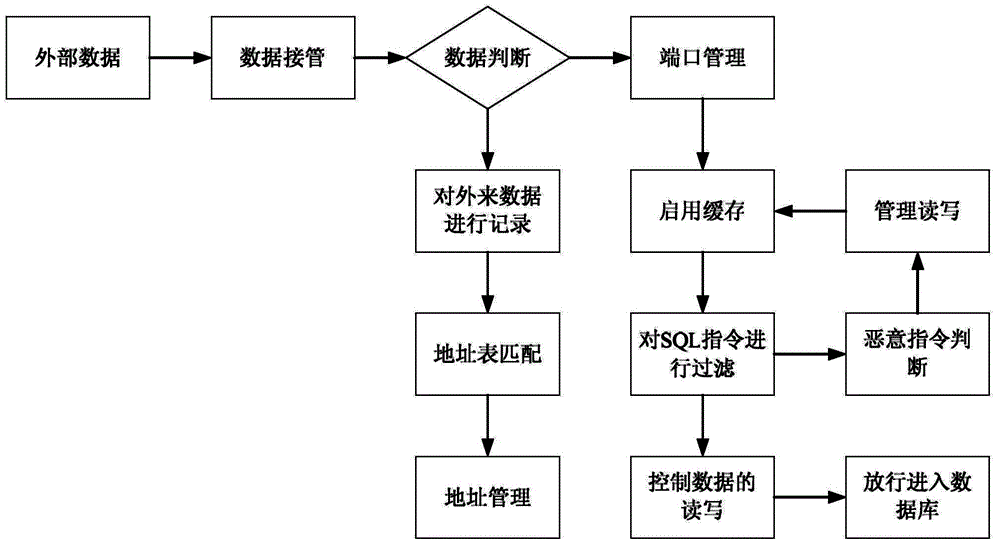
[0031] Such as figure 2 As shown, the flow process of the database-based SOL injection attack protection method of the present invention is as follows:
[0032] (1) Establish a data security shell for the database
[0033] The data security shell is a low-level driver built on the operating system layer. It uses a virtual space formed by the hard disk cache to load the database in this virtual space. The data security shell i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com