IPSec SA consultation method and device
An initiator and responder technology, applied in the field of network security, can solve problems such as traffic interruption and instantaneous traffic jitter
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
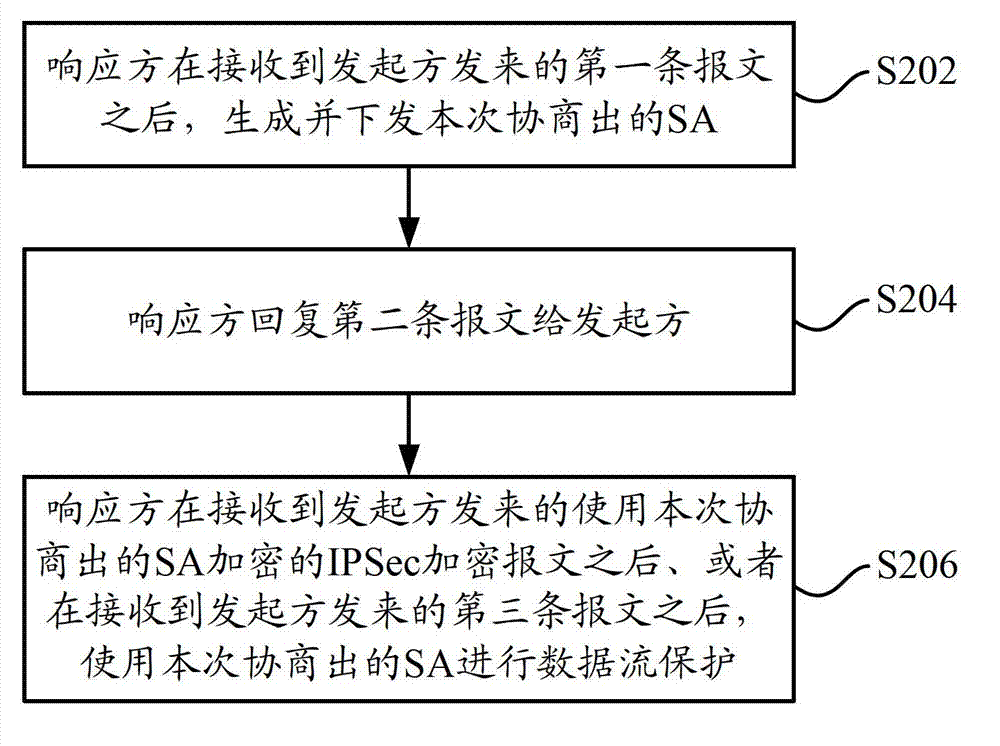
[0048] In order to solve the problem of instantaneous traffic jitter or traffic interruption of the responder in the process of initial IPSec SA negotiation and re-negotiation in the prior art, the embodiment of the present invention provides an IPSec SA negotiation in the fast mode of the second phase of IKE negotiation method, which is executed by the responder of the negotiation. Such as figure 2 shown, including the following steps:
[0049] Step S202, after receiving the first message from the initiator, the responder generates and delivers the negotiated SA;
[0050] In the second phase of IKE negotiation, the initiator of the negotiation first sends the first message to the responder, which contains all the security parameters that need to be negotiated by the responder, for example, the protocol defined by the IPSec policy (AH, ESP) , encryption algorithm, authentication algorithm, etc., and also includes a hash summary that can be verified.
[0051] After receivin...
Embodiment 2
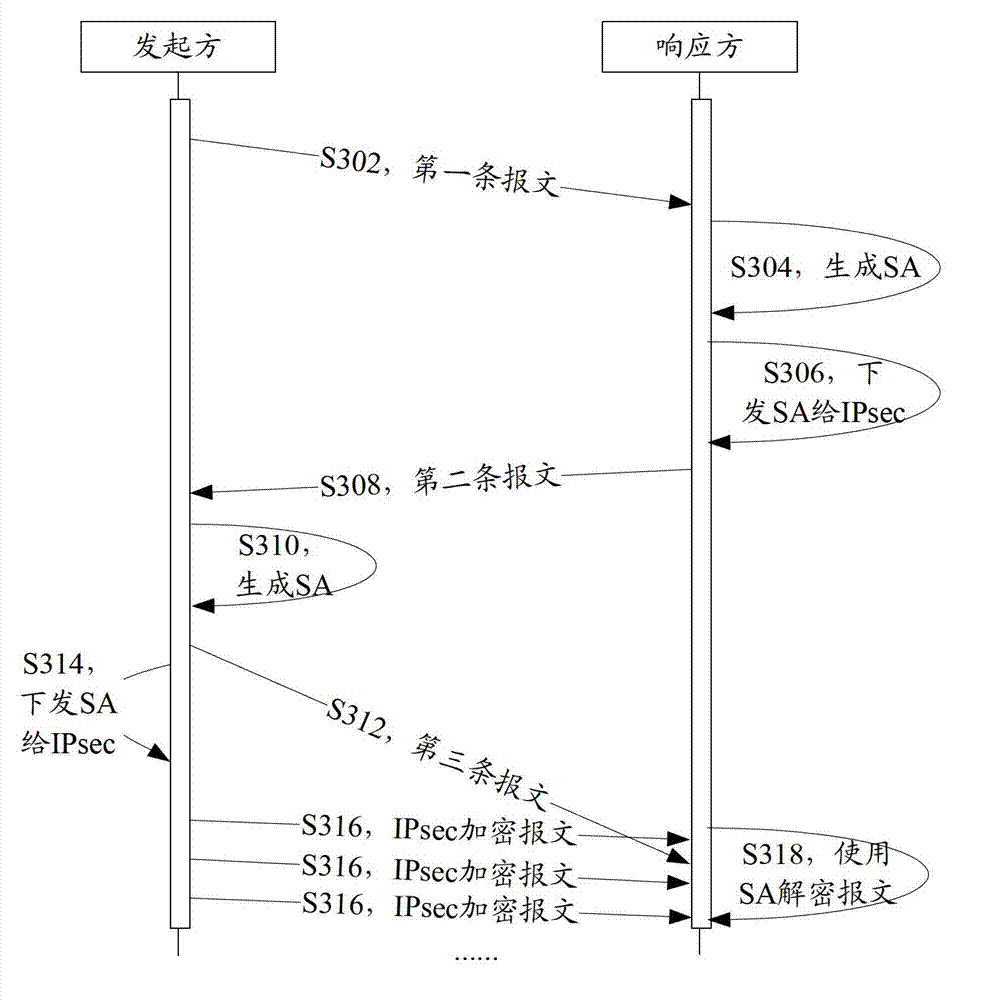
[0062] Such as image 3 As shown, in the quick mode of the second phase of IKE negotiation, the interaction process between the initiator and the responder when negotiating the IPSec SA for the first time can be as follows:
[0063] Step S302, the initiator of the IKE negotiation sends the first message to the responder of the negotiation;
[0064] Step S304, after receiving the first message, the responder selects a security parameter that matches itself according to the security parameter carried in the message, and generates an SA according to the selected security parameter;
[0065] Step S306, the responder sends the generated SA to IPSec;
[0066] Step S308, the responder sends a second message to the initiator, the message carrying the security parameters selected by the responder in step S304;
[0067] Step S310, after receiving the second message, the initiator generates an SA according to the security parameters selected by the responder carried in the message;
...
Embodiment 3
[0074] Such as Figure 4 As shown, in the quick mode of the second phase of IKE negotiation, the interaction process between the initiator and the responder when renegotiating the IPSec SA can be as follows:
[0075] Step S402, the soft timeout of the old SA triggers the initiator of the negotiation to renegotiate the IPSec SA;
[0076] Step S404, the initiator sends the first message to the negotiated responder;
[0077] Step S406, after receiving the first message, the responder selects a security parameter that matches itself according to the security parameter carried in the message, and generates a new SA according to the selected security parameter;
[0078] Step S408, the responder sends the generated new SA to IPSec;
[0079] Step S410, the responder sends a second message to the initiator, the message carrying the security parameters selected by the responder in step S406;
[0080] Step S412, after receiving the second message, the initiator generates a new SA accord...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com