Malicious code capturing method and system
A malicious code and source code technology, applied in the field of malicious code capture methods and systems, can solve problems such as inability to capture malicious code, failure to fully consider malicious code, etc., and achieve the effect of improving capture capability and increasing coverage.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
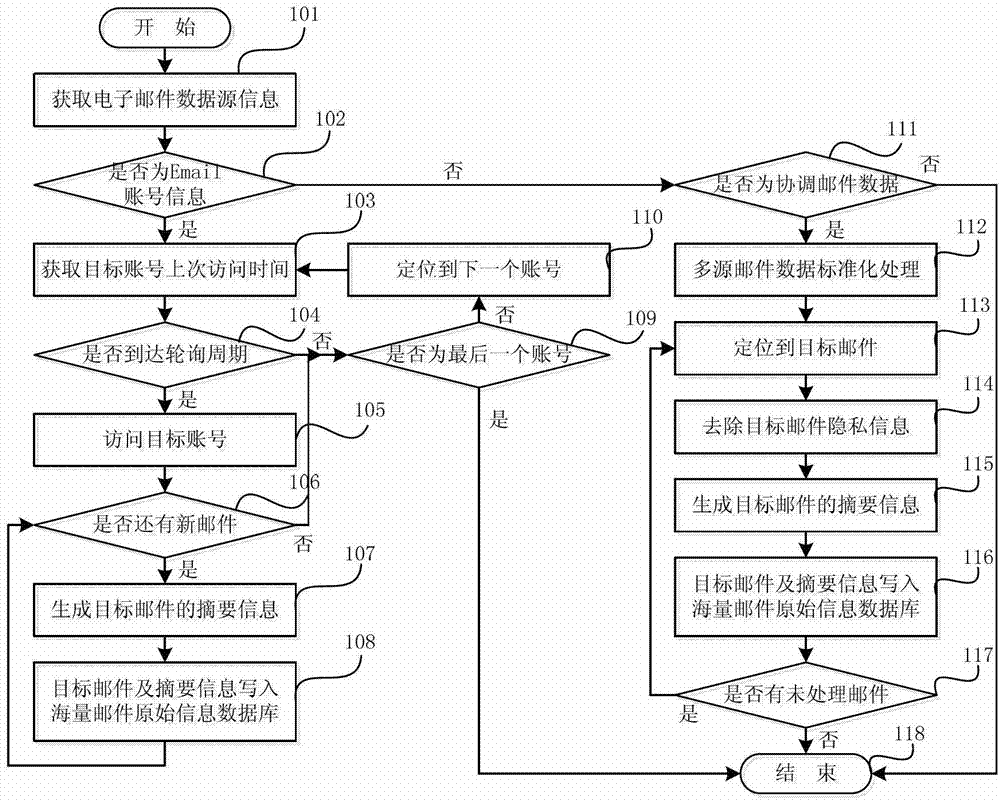
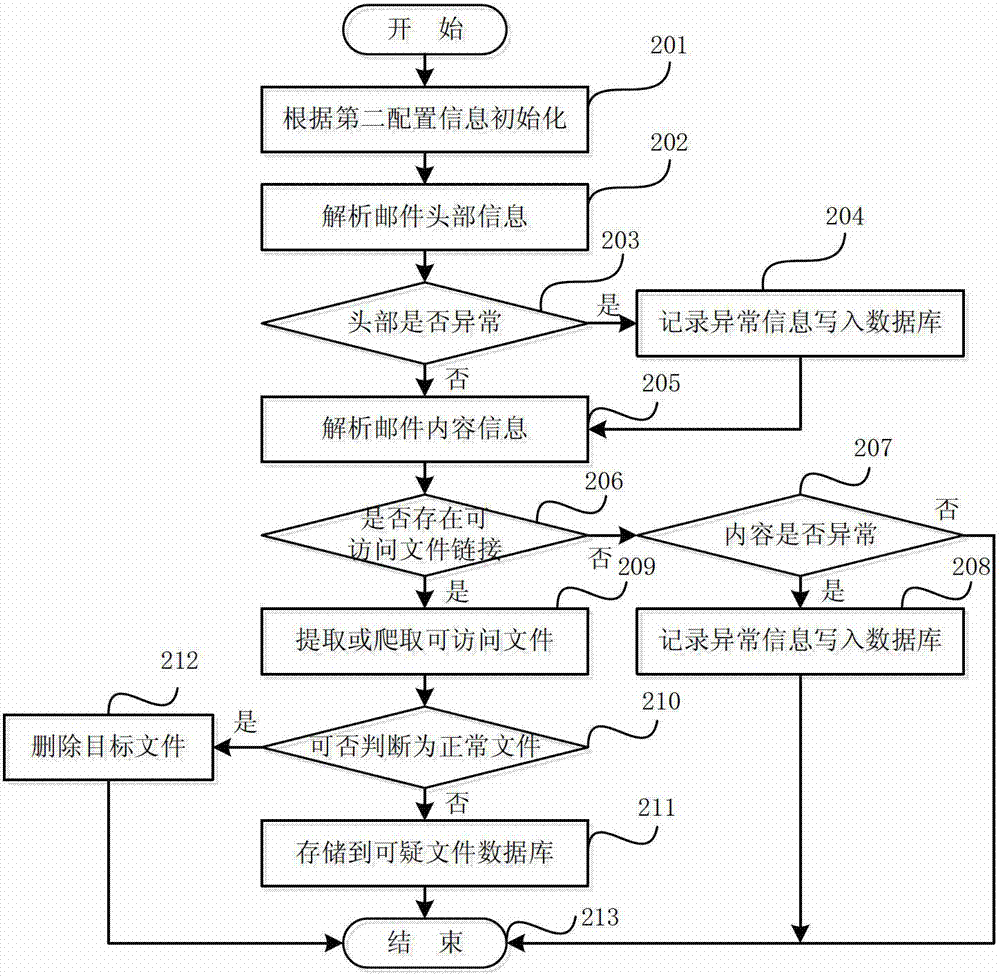
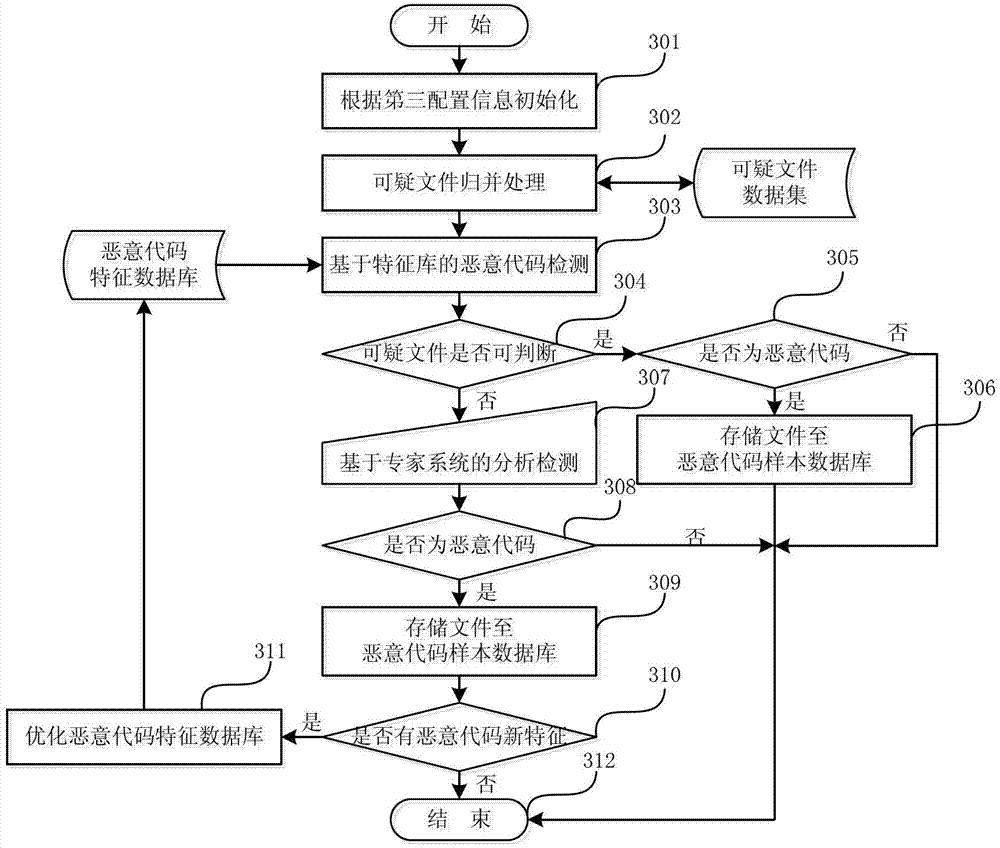
[0058] The principles and features of the present invention are described below in conjunction with the accompanying drawings, and the examples given are only used to explain the present invention, and are not intended to limit the scope of the present invention.
[0059] The invention adopts the selection and deployment algorithm of the Email terminal virtual honeypot to allocate and optimize the use of virtual honeypot resources. This algorithm (that is, the selection and deployment algorithm of the virtual honeypot of the Email terminal, the same below) abstracts the Email network where the malicious code spreads into a social network weighted directed graph model composed of points and edges with the characteristics of a small-world model (denote is G=). Among them, the point (denoted as v i ) represents an Email account, and the edge (denoted as e k ) represents the communication mail between Email accounts, and the weight of the edge (denoted as w(e k )) indicates the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com