Email forensic analyzing method based on community characteristics analysis
A technology of e-mail and analysis methods, which is applied in the fields of electrical components, electrical digital data processing, and special data processing applications, etc., and can solve problems such as the absence of massive e-mail associations and comprehensive mining and analysis of communication content
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
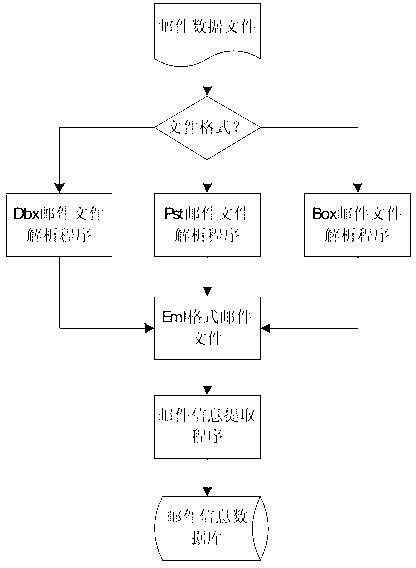
[0027] The implementation of the entire solution will go through three stages: email file analysis and data extraction, email communication relationship network construction, and community extraction and analysis. The following will focus on the workflow of the three stages.
[0028] 1. Analysis and extraction of Email files, mainly for the compound documents of the three software client softwares of Microsoft Outlook, Outlook Express and Foxmail, that is, the mail storage documents in the three formats of Pst, Dbx and Box, and analyze these documents into The Eml format document with a single email as the storage unit, and then the Eml format document as the analysis object, from which information such as the email address, subject, sending time, email content, and attachments of the sending and receiving accounts that have sent and received emails are extracted, and the obtained emails The information is stored in the mail information database. The processing flow of the ent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com