Identity information de-identification device
An anonymous, information-rich technology, applied in computer security devices, digital data information retrieval, instruments, etc., to achieve the effect of reducing operating costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
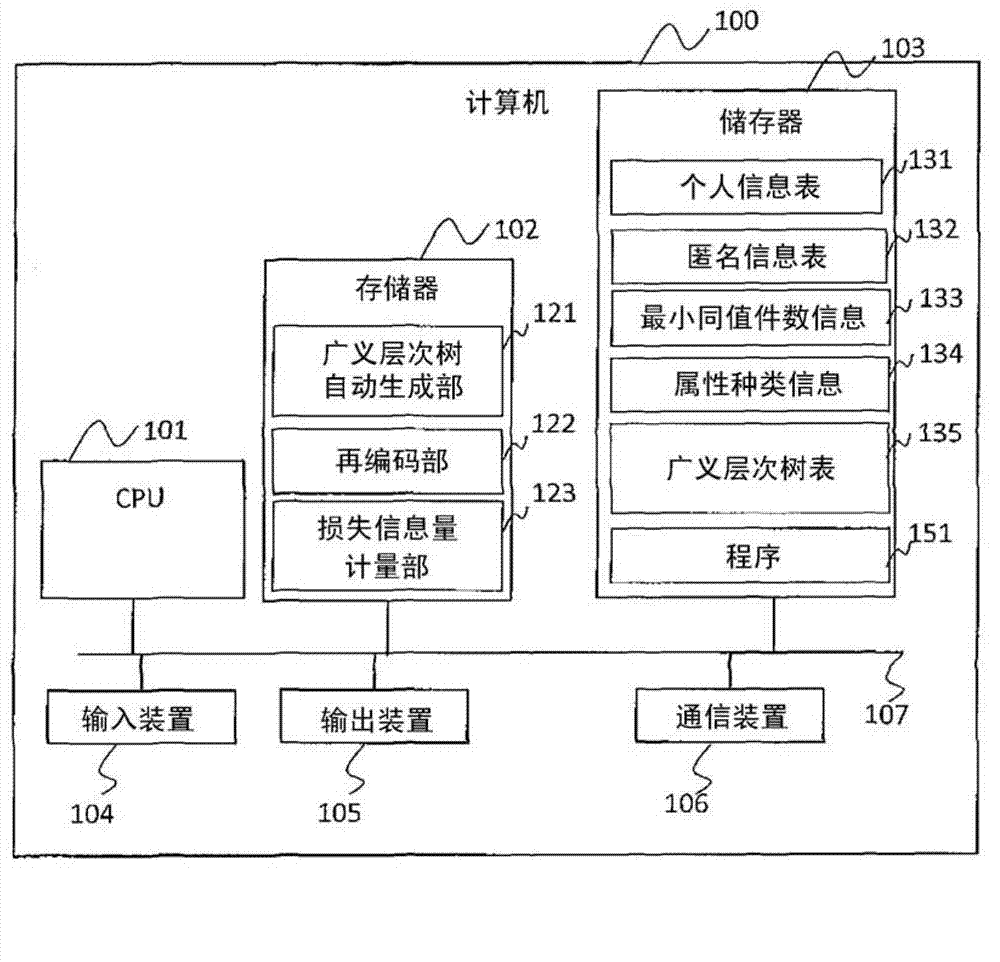
[0053] refer to figure 1 , a configuration example of an apparatus for realizing the technique of Embodiment 1 will be described.
[0054] figure 1 It is an example of configuring a device on a computer. exist figure 1 Here, the computer 100 is, for example, an arbitrary information processing device such as a PC (Personal Computer), a server, or a workstation. The computer 100 has a CPU (Central Processing Unit) 101 , a memory 102 , a storage 103 , an input device 104 , an output device 105 , a communication device 106 , and the like. These are all connected to each other via an internal communication line 107 such as a bus.
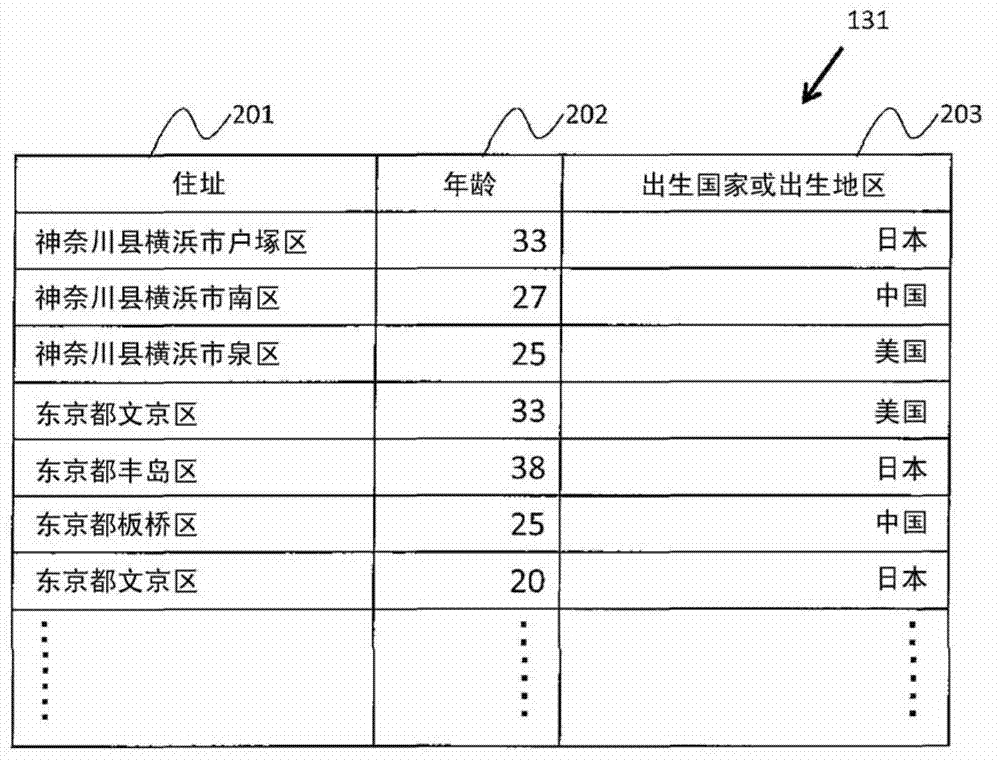
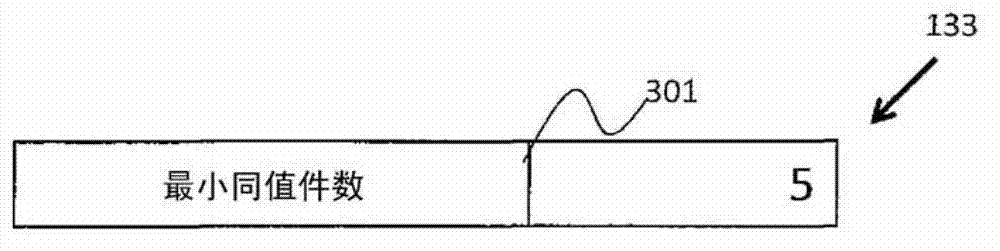
[0055]The storage 103 is, for example, a storage medium such as a CD-R (Compact Disc Recordable), a DVD-RAM (Digital Versatile Disk Random Access Memory), or a silicon disk, and a drive device HDD (Hard Disk Drive) for the storage medium. The storage 103 stores a personal information table 131, an anonymity information table 132, minimum equivalent...
Embodiment 2
[0139] Next, Example 2 will be described.
[0140] Embodiment 2 improves the usefulness of data. Hereinafter, when the second embodiment is described, the same symbols are given to the same configurations as those of the above-mentioned first embodiment, and description thereof will be omitted. In addition, most of the operations of the second embodiment are the same as those of the first embodiment. The same symbols are given to the operations of this part, and explanations are omitted.
[0141] First, refer to Figure 13 A configuration example of the computer 100 according to the second embodiment will be described.
[0142] exist Figure 13 In this case, the memory 103 of the computer 100 has a program 1331 instead of the program 151 . The program 1331 is loaded into the memory, and the CPU 101 implements the pseudo-personal information generating unit 1321 in addition to the units 121, 122, and 123 of the first embodiment. Also, a generation information table 1332 i...
Embodiment 3
[0155] Next, Example 3 will be described.
[0156] In the third embodiment, the usefulness of data is improved by using classification of attribute values desired by the user. There are prescribed classifications in various fields such as the International Classification of Diseases, Book Classification, and Patent Classification. In addition, as for age, there are commonly used classifications such as 10 to 19 years old and 20 to 29 years old. In Embodiment 3, by only predefining the hierarchical structure desired by the user for the generalized hierarchical tree, the generalized hierarchical tree considering the classification desired by the user is automatically generated. For example, by predefining the classification of age as "20 to 24 years old" and "25 to 29 years old", it is possible to prevent data such as "24 to 27 years old" from being recoded in a form deviated from the classification desired by the user.
[0157] In addition, in the third embodiment, when con...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com