Access control method and system, network side network element
An access control and access network technology, applied in access restriction, electrical components, wireless communication, etc., can solve the problems of inability to set EAB parameters correctly, and inability to learn the load information of different types of UEs, so as to improve user experience, The effect of ensuring the quality of business services
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
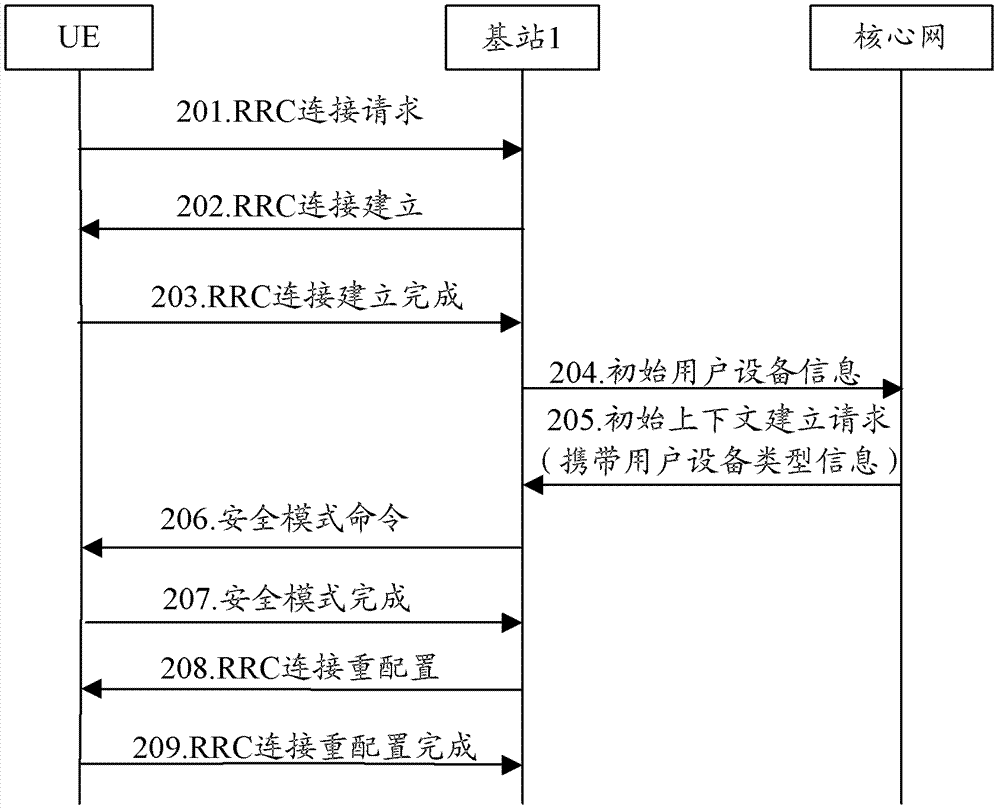
[0072] This embodiment describes a method for configuring extended access control parameters on the network side in an LTE system.
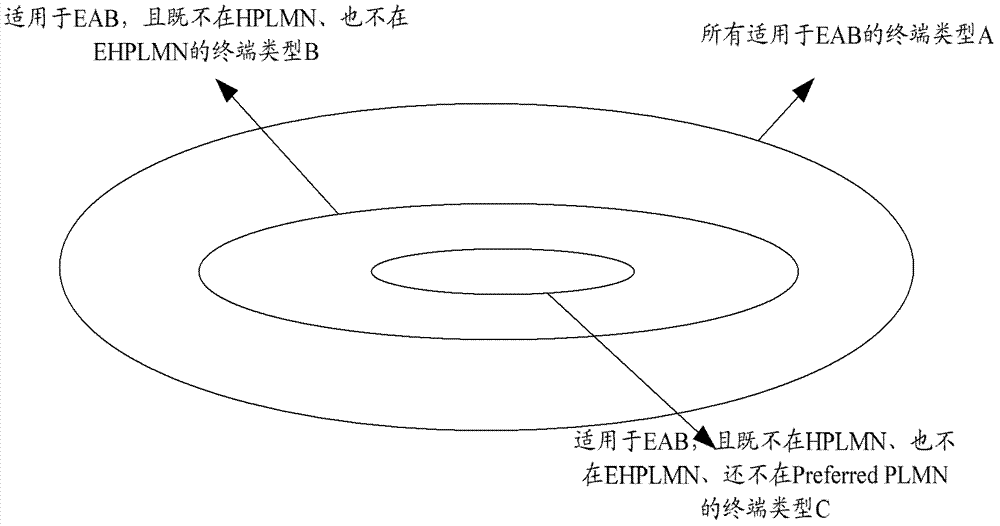
[0073] In this embodiment, UE1 and UE2 reside in cell 1 under the jurisdiction of base station 1, and are in an idle state. Both UE1 and UE2 are configured as EAB-compliant UEs. In addition, the USIM card of UE1 indicates that the access class of the UE is 2, that is, the Access Class is 2. The USIM cards of UE1 and UE2 also store HPLMN identifiers, and may also include EHPLMN identifiers and preferred public land mobile network identifiers (preferred PLMN). In this embodiment, the HPLMN stored in the USIM card of UE1 is PLMN1, EHPLMN is PLMN2 and PLMN3, and the preferred PLMN is PLMN4. The PLMN broadcast in the system message of cell 1 is PLMN4. The HPLMN saved in the USIM card of UE2 is PLMN2, EHPLMN is PLMN4, and the Preferred PLMN is not set.
[0074] According to the classification criteria of user equipment:
[0075] Category A (Category A): ...
Embodiment 2
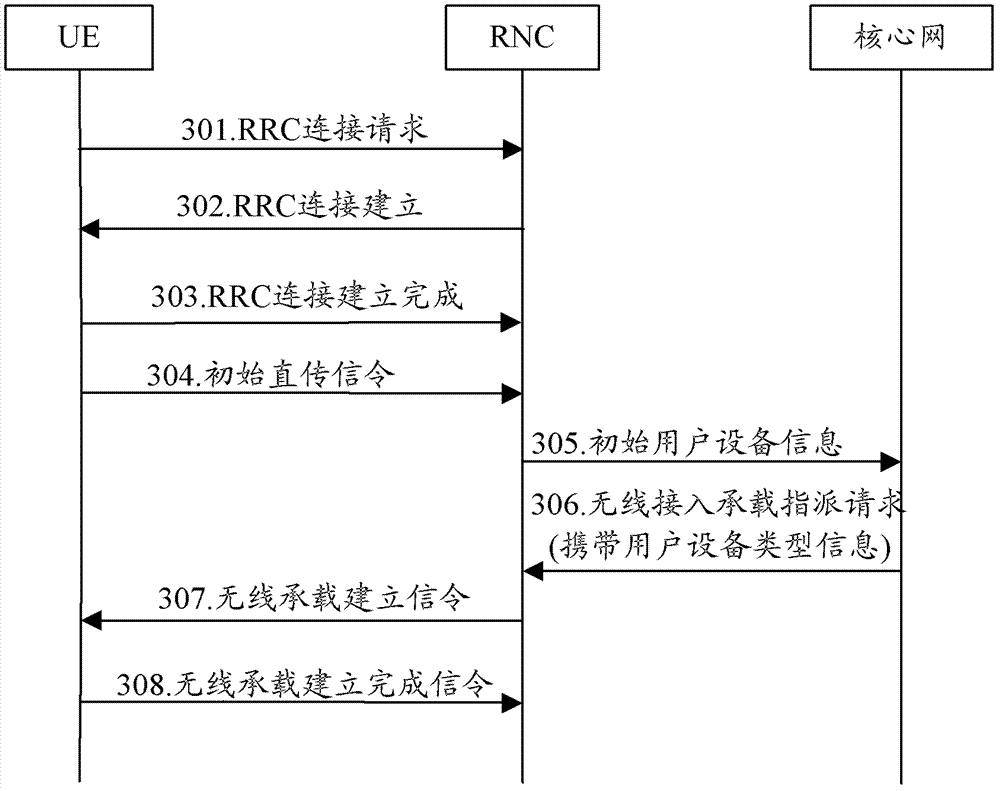
[0101] This embodiment describes a method for configuring extended access control parameters on the network side in a universal mobile communication system.
[0102] In this embodiment, UE3 and UE4 reside in a cell 2 under the jurisdiction of base station 2 and are in an idle state, and base station 2 is under the jurisdiction of a radio network controller (RNC, Radio Network Controller). Both UE3 and UE4 are configured as EAB-compliant UEs. In addition, the USIM card of UE3 indicates that the access class of the UE is 4, that is, the Access Class is 4. The USIM cards of UE3 and UE4 also store HPLMN identifiers, and may also include EHPLMN identifiers and preferred public land mobile network identifiers (preferred PLMN). The HPLMN stored in the USIM card of UE3 is PLMN1, EHPLMN is PLMN2 and PLMN3, and the preferred PLMN is PLMN4. The HPLMN stored in the USIM card of UE4 is PLMN2, and EHPLMN is PLMN4, and the Preferred PLMN is not set. In this embodiment, the PLMN broadcast in ...
Embodiment 3
[0122] In this embodiment, the UE5 resides in the cell 3 under the jurisdiction of the base station 3 and is in an idle state. UE5 is configured as an EAB-compliant UE. The HPLMN stored in the USIM card of UE5 is PLMN1, EHPLMN is PLMN2, and the preferred PLMN is PLMN3. The PLMN of cell 3 is PLMN3, and UE5 belongs to Category B at this time.
[0123] The UE5 needs to initiate a service, and the UE5 needs to determine whether to allow access to the network to initiate a service request based on the EAB parameters or ACB parameters broadcast by the cell 3 (transmitted through system messages). At this time, the system message of cell 3 contains EAB parameters; UE5 uses EAB parameters to implement access decision. If the decision result is not barred, UE5 needs to implement access decision based on ACB parameters. Random access can be initiated only when the entry decision is successful, and an RRC connection request is sent to the network side when the random access is successful;...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com