DDoS filtering method based on SDN network architecture
A filtering method and network architecture technology, applied in the field of network security, can solve problems such as network security issues, and achieve the effect of running colleges and universities, avoiding traffic data loss, and reducing burden
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
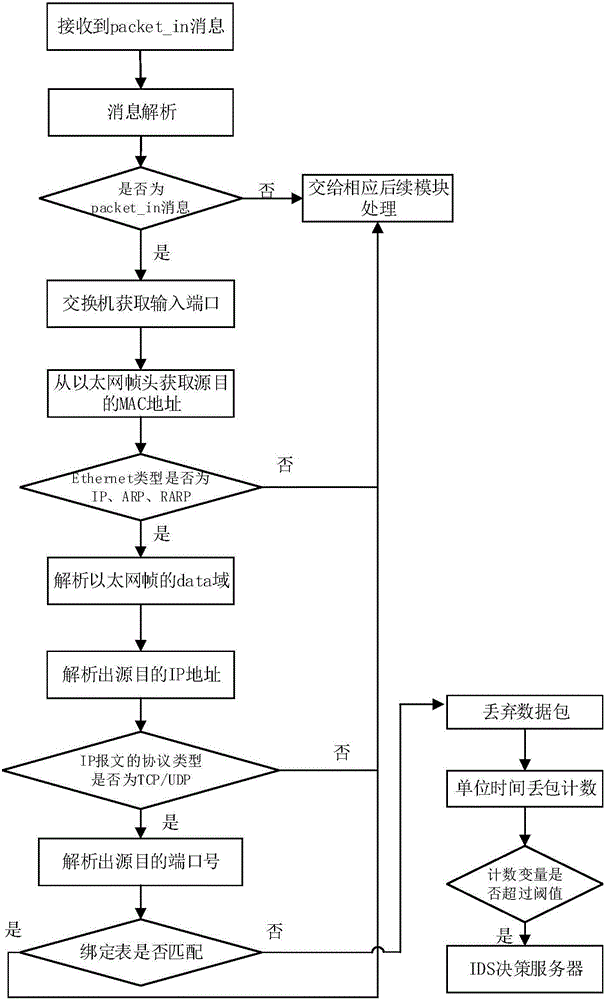
[0035] figure 1 A structural block diagram of the SDN network architecture of the present invention is shown.
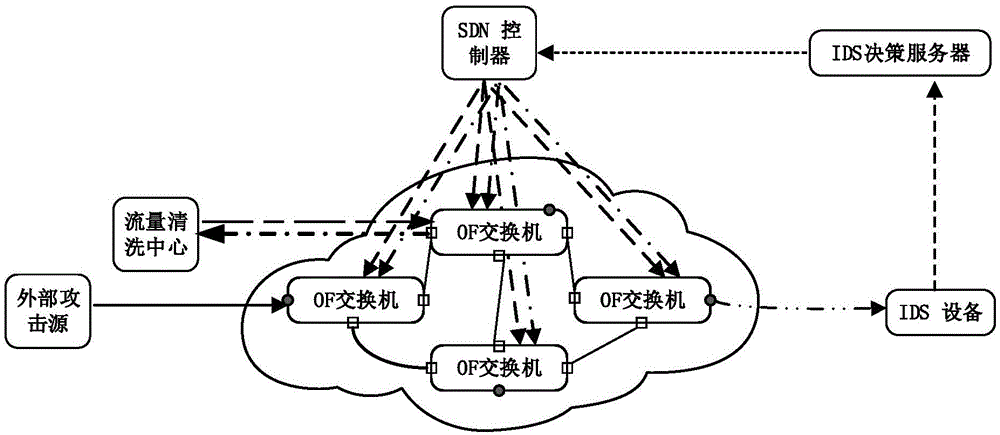
[0036] Such as figure 1 As shown, the SDN network architecture of the present invention includes: an SDN controller, an IDS decision server, an IDS device (i.e. an intrusion detection device) and a traffic cleaning center; The channel is reported to the IDS decision server; the IDS decision server formulates a processing strategy corresponding to the message with DDoS attack characteristics according to the reported information, and then the message is shielded by the SDN controller or the OF The traffic on the access port of the switch is redirected to the traffic cleaning center for filtering; at the same time, the current SDN link status information is collected through the SDN controller to provide the corresponding packet sending path.
[0037] Among them, the characteristics of DDoS attack are defined as: spoofing of link layer and Internet layer addresses, a...
Embodiment 2
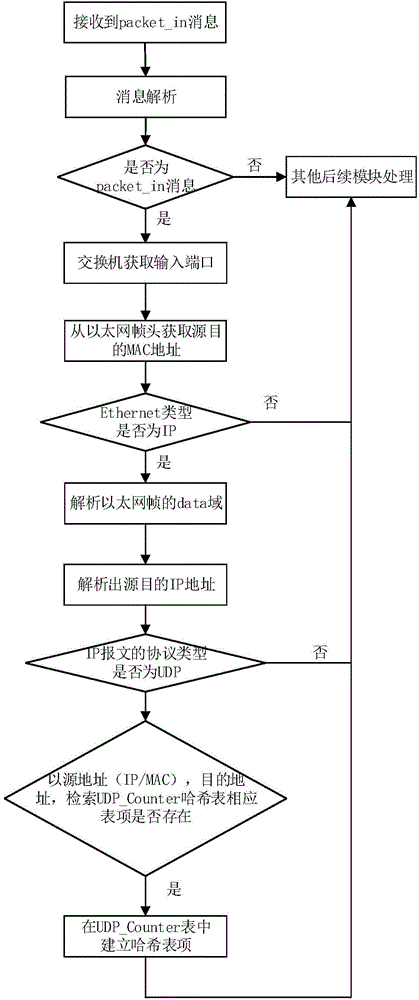
[0125] A DDOS filtering method based on the SDN network architecture based on Embodiment 1, through detection and centralized processing, effectively reduces the workload of the SDN controller, improves detection efficiency and data transmission rate, and collects SDN link status information to avoid traffic loss when a link fails.
[0126] The DDOS filtering method based on the SDN network architecture of the present invention includes the following steps: step S100, network initialization; step S200, distributed DDoS threat monitoring and / or collecting SDN link status information; and step S300, threat processing and / or determination Data distribution path.
[0127] Further, the devices involved in network initialization in the step S100 include: SDN controller, IDS decision server and IDS equipment; the steps of network initialization are as follows: Step S101, the IDS decision server and IDS equipment establish a dedicated SSL channel; S102, the SDN controller builds a ne...
Embodiment 3
[0153] The SDN framework of the present invention can define SDNQA (SDN Communication Quality Assurance Strategy), that is, an SDN communication quality assurance strategy.
[0154]The test environment and test contents of the SDN framework of the present invention are as follows:
[0155] Based on the OpenFlow 1.3 protocol, the communication between the Floodlight SDN controller, OF switch, IDS device and IDS decision server equipped with DDoS threat filtering and communication quality assurance components is tested.
[0156] Test whether the IDS device can monitor abnormal attack traffic in the network in real time, and report to the IDS decision server through the SSL channel.
[0157] Test whether the IDS decision server can formulate a strategy to deal with the corresponding attack threat based on the information reported by the IDS device, and issue it through the northbound interface of the SDN controller.
[0158] Test whether the SDN controller can generate and deliv...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com