Data security verification method and device
A security verification and data security technology, applied in security devices, secure communication devices, digital data authentication, etc., can solve the problems of high hardware cost, easy password or biometric identification to be cracked or invalidated, etc., to ensure uniqueness, Convenient and easy to carry equipment resources, enhance the effect of anti-cracking possibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
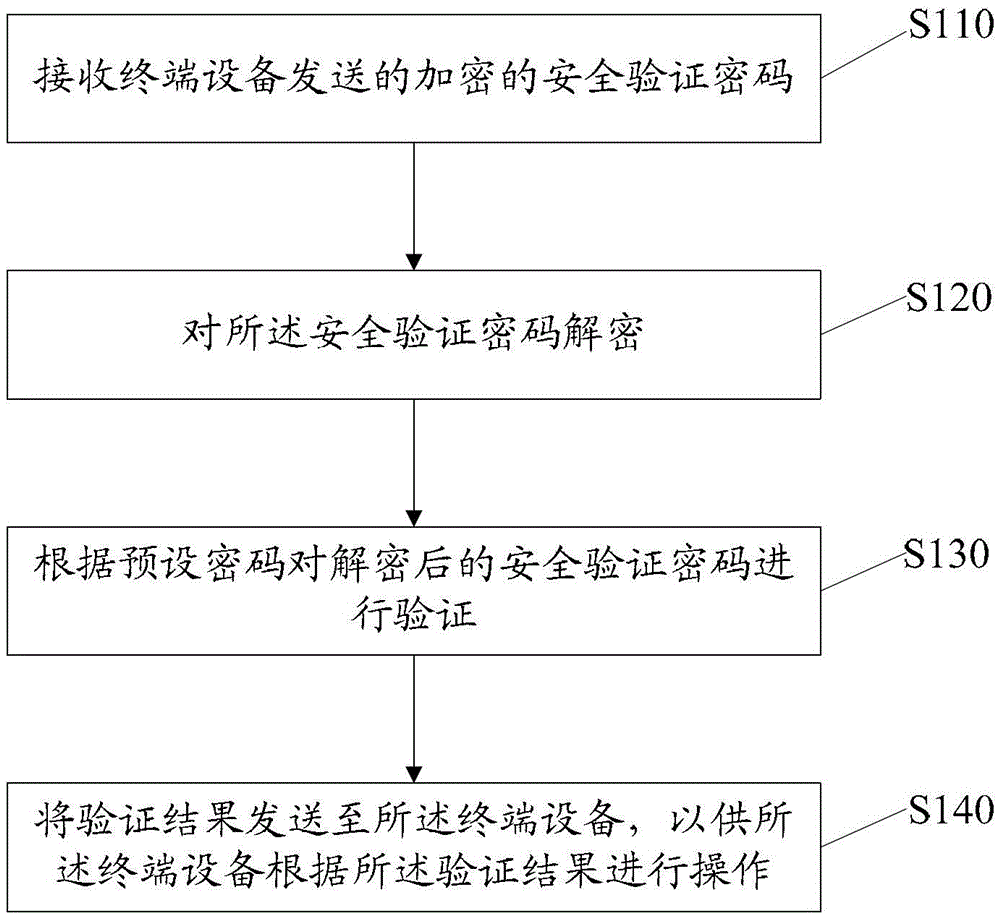
[0026] figure 1 It is a flow chart of a data security verification method provided by the present invention. The method can be realized by software and used for security binding verification between the mobile terminal and the terminal equipment, for example, running through a mobile phone. Such as figure 1 As shown, the method includes:
[0027] Step S110: Receive the encrypted security verification password sent by the terminal device. Wherein, the terminal device encrypts the security verification password input by the user with the International Mobile Equipment Identity (IMEI: International Mobile Equipment Identity) of the mobile terminal, so as to ensure the uniqueness of the security verification.
[0028] Step S120: Decrypt the security verification password. Wherein, the mobile terminal uses the private key to decrypt the encrypted security verification password. The private key is a password generated by combining the mobile terminal's International Mobile Equi...
Embodiment 2
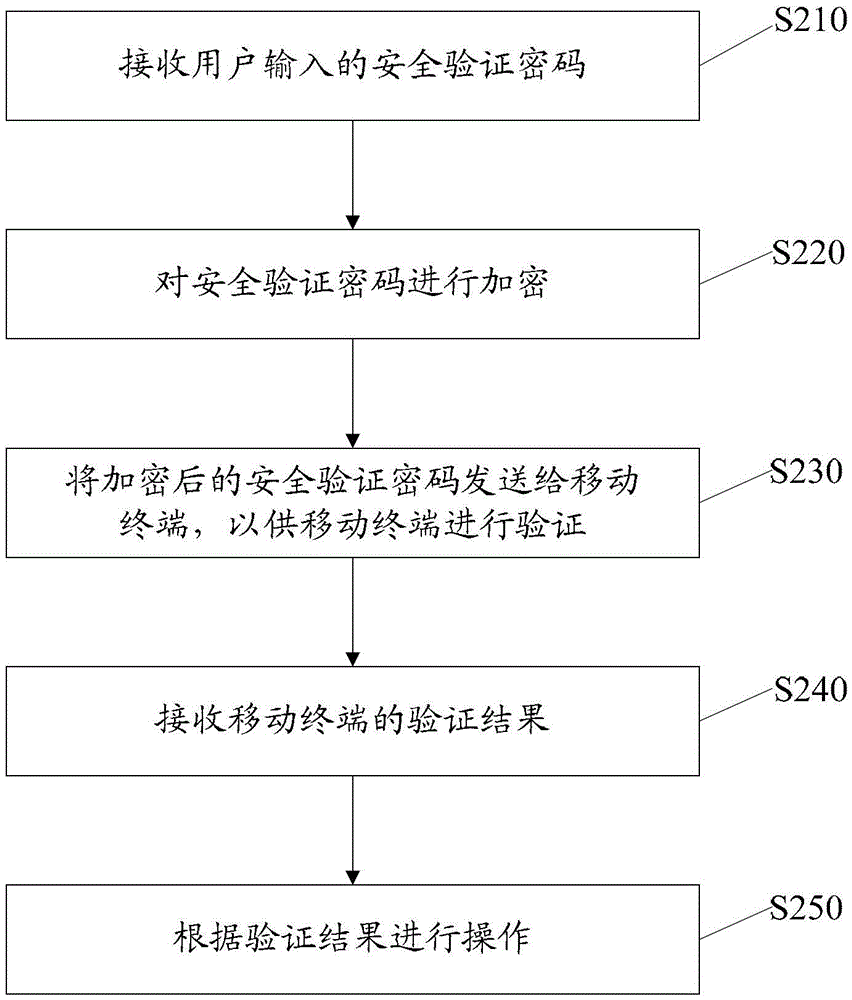
[0033] figure 2 It is a flowchart of another data security verification method provided by the present invention. The method can be realized by software and used for security binding verification between the mobile terminal and the terminal equipment, for example, running by a computer to realize the security verification of entering the computer operating system. Such as figure 1 As shown, the method includes:
[0034] Step S210: Receive the security verification password input by the user. Before this step, the screen lock function structure can be called to lock the screen and prompt the user to input the correct security verification password. Wherein, the lock screen mechanism can be implemented through the SendMessage interface of the API of the windows operating system of the terminal device, so that the system message mechanism will not be intercepted.
[0035] Step S220: Encrypt the security verification password. The terminal device uses the mobile terminal IME...
Embodiment 3
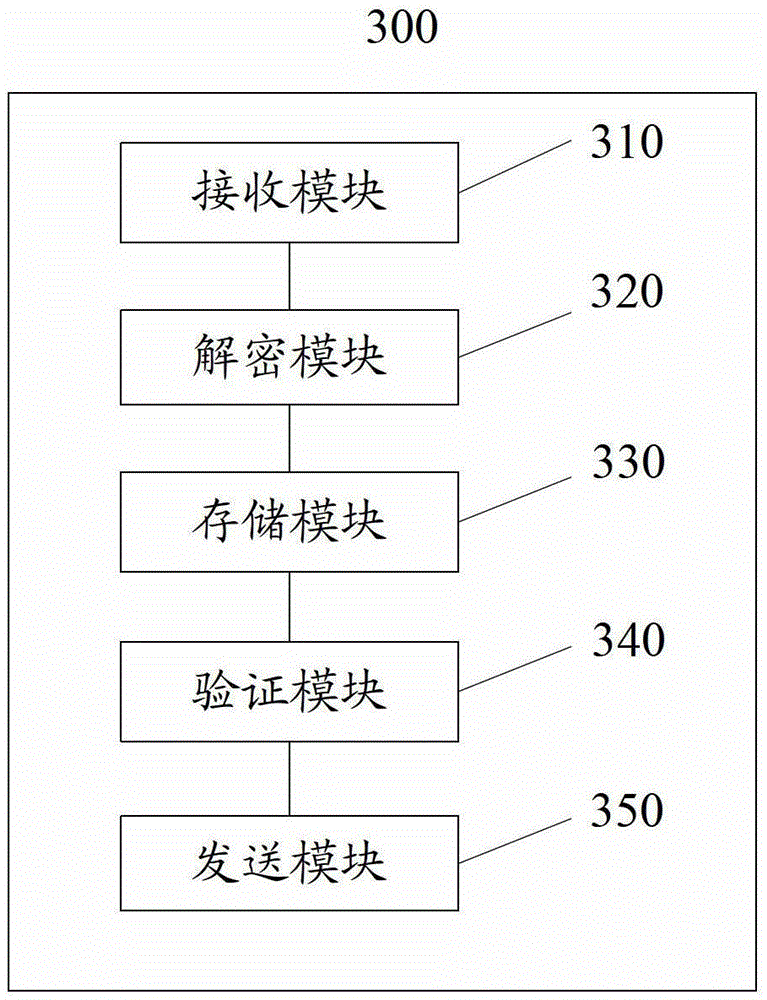
[0042] image 3 It is a structural schematic diagram of a data security verification device provided by the present invention. The device is a mobile terminal, such as a mobile phone, and is used for security binding verification with terminal equipment. like image 3 As shown, the data security verification device 300 includes:
[0043] The receiving module 310 is configured to receive the encrypted security verification password sent by the terminal device;
[0044] A decryption module 320, configured to decrypt the security verification password;
[0045] The verification module 340 verifies the decrypted security verification password according to the preset password; and
[0046] The sending module 350 is configured to send the verification result to the terminal device, so that the terminal device can operate according to the verification result.
[0047] Wherein, the terminal device encrypts the security verification password input by the user with the Internationa...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com