Method, device and system for identity authentication
An identity authentication and authentication request technology, applied in the field of identity authentication, can solve problems such as malicious attacks, user inconvenience, inconvenience, etc., to ensure security, facilitate popularization, and achieve simple and convenient effects
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Aiming at the problems existing in the prior art, the present invention proposes an identity authentication scheme, which can more conveniently and reliably realize authentication of user identity by an authentication server of a mobile online business hall.
[0050] In order to make the technical solution of the present invention clearer and clearer, the solution of the present invention will be further described in detail below with reference to the accompanying drawings and examples.
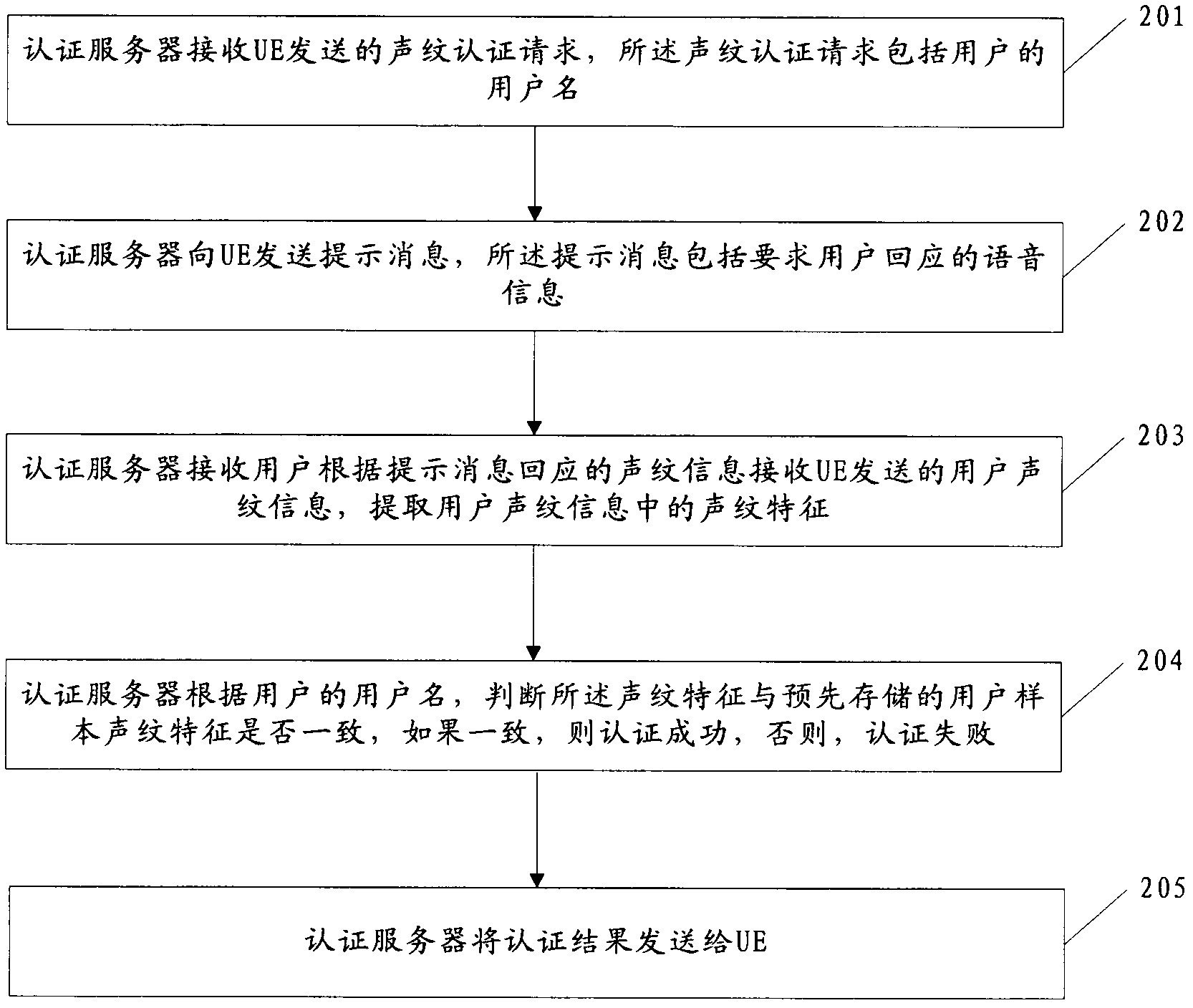
[0051] figure 2 It is an identity authentication flow chart of the first embodiment of the identity authentication method of the present invention. In this embodiment, after receiving the voiceprint authentication request sent by the user terminal UE, the authentication server of the mobile online business hall randomly generates voice information requiring the user to respond, sends the voice information requiring the user to respond to the UE, and prompts The user responds to the v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com