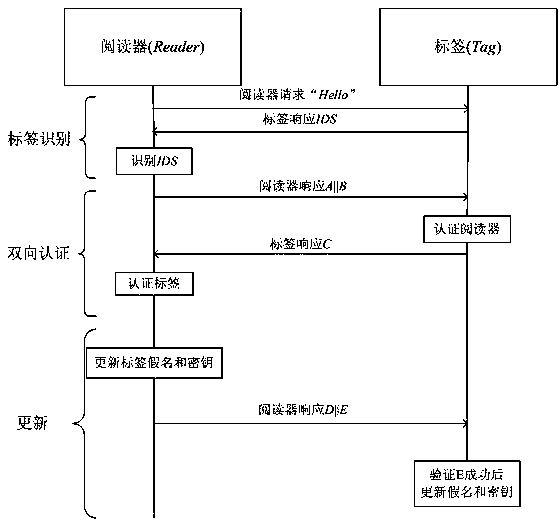
A kind of rfid two-way authentication protocol method
A two-way authentication and protocol technology, which is used in collaborative devices, user identity/authority verification, instruments, etc., can solve problems such as weak authentication and data integrity, large storage space for labels, and no forward security. Achieve strong authentication and data integrity, ensure freshness, and ensure forward security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0032] The present invention and its advantages will be further described below in conjunction with the accompanying drawings and its embodiments.
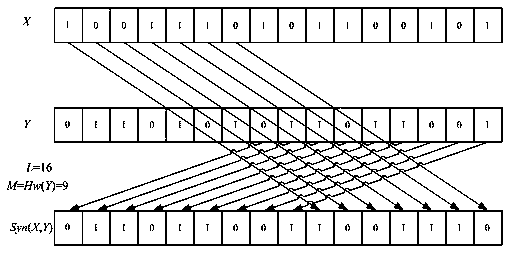
[0033]In order to be suitable for low-cost labels, the present invention newly defines the word synthesis operation Syn(X,Y): Syn(X,Y) is a new array of L bits formed by combining the last M bits of the array Y and the first L-M bits of X. Wherein X, Y are two binary arrays required for the word synthesis operation, , , ;Where M is set as: M=Hw(Y), also can be M=L-Hw(Y); or M=Hw(X), can also be M=L-Hw(X); or M= Hd(X,Y) can also be M=L-Hd(X,Y); Hw(X) is the Hamming weight of X, Hw(Y) is the Hamming weight of Y, Hd(X,Y) is The Hamming distance between X and Y.
[0034] For example, take L=16, set X=1001110101100101, Y=0110101011011001, set M=Hw(Y)=9, then get Syn(X,Y)=0110110011001110 according to the above word synthesis operation, the specific operation process is as attached figure 1 shown. This operation can be realized...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com