Open flow meter security enhancement method and device
An open-flow and secure technology, applied in transmission systems, electrical components, etc., can solve the problems of large differences in security execution units, difficult to achieve centralized control and management, and difficult to achieve interoperability, etc., to defend against zero-day attacks and mitigate distributed Effects of Denial of Service Attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0059] In order to make the object, technical solution and advantages of the present invention clearer, the present invention will be further described in detail by citing the following embodiments and referring to the accompanying drawings.
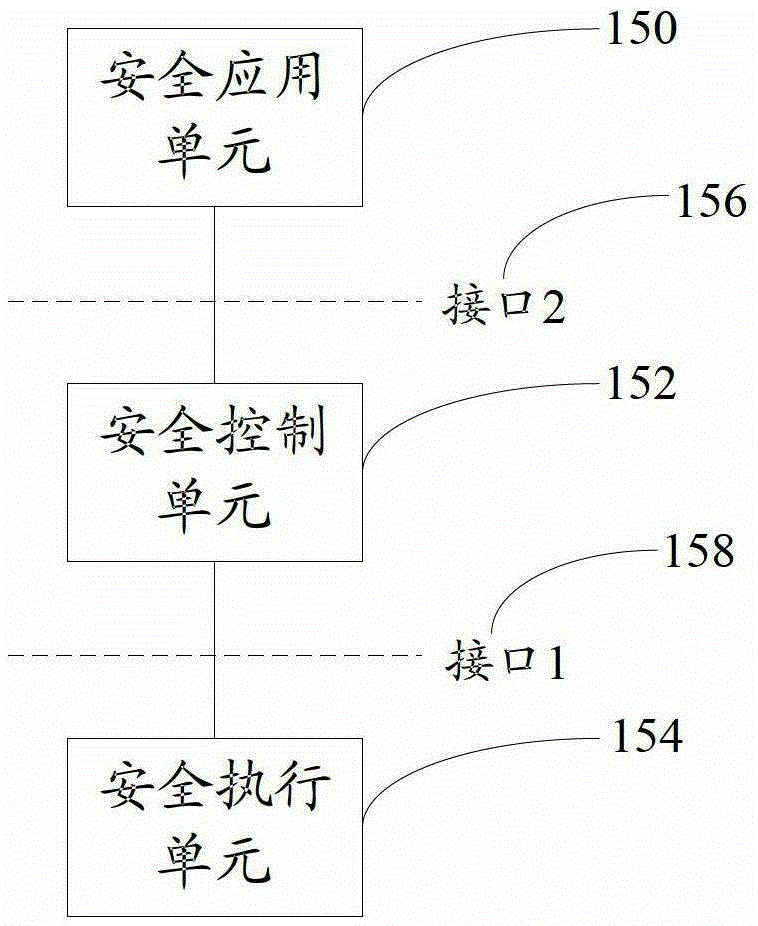
[0060] figure 2 A schematic diagram of the composition and structure of the open flow table security enhancement device in the embodiment of the present invention, as shown in figure 2 As shown, the open flow table security enhancement device in the embodiment of the present invention includes a security application unit 150, a security control unit 152 and a security execution unit 154, wherein:
[0061] A security application unit 150, configured to provide security applications for various security services, and security policies, security protocols, and feature libraries corresponding to the various security services;
[0062] The security control unit 152 is configured to analyze the security policy of the security service, gener...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com