Cloud data safe auditing method based on multi-Agent
A data and database technology, applied in the direction of data exchange network, digital transmission system, electrical components, etc., can solve the problems of unable to send logs in a centralized manner, large bandwidth, denial of service attacks, etc., and achieve the effect of supporting data privacy protection and flexible event analysis
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
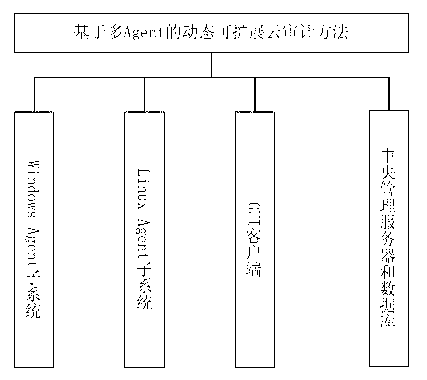
[0041] The present invention is based on a multi-Agent dynamically scalable cloud data security audit method, which mainly completes data protection verification and related audit work, including functions such as remote data verification, data privacy protection, log audit and data batch audit.
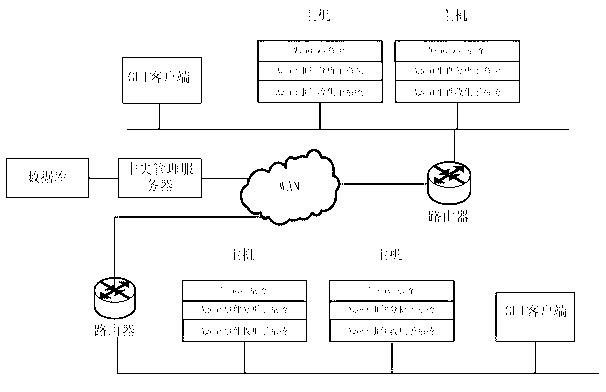
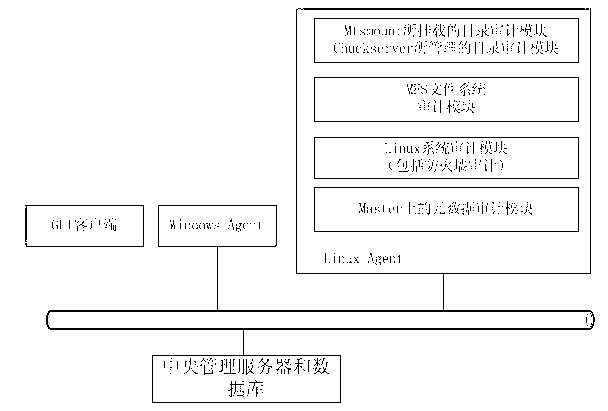
[0042] Such as figure 1As shown, the audit system environment in which the audit method of the present invention operates includes three parts: a host, a GUI client and a central management server. The host part can be a Linux Agent system or a Windows Agent system, which can be a physical host or a virtual machine. Agent event collection subsystems and Agent event analysis subsystems are deployed on each host, and these subsystems run auditing as background processes in the monitored system The main purpose of information collection and analysis is to collect security-related event information on the host, and transmit the data analysis and processing to the central manager server. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com