Method and system for protecting data based on iris identification
An iris recognition and iris technology, applied in the field of information security, can solve problems such as slow data reading speed, fragile data, and insufficient security, and achieve the effects of protecting security, solving data security, and fast data security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 1 example
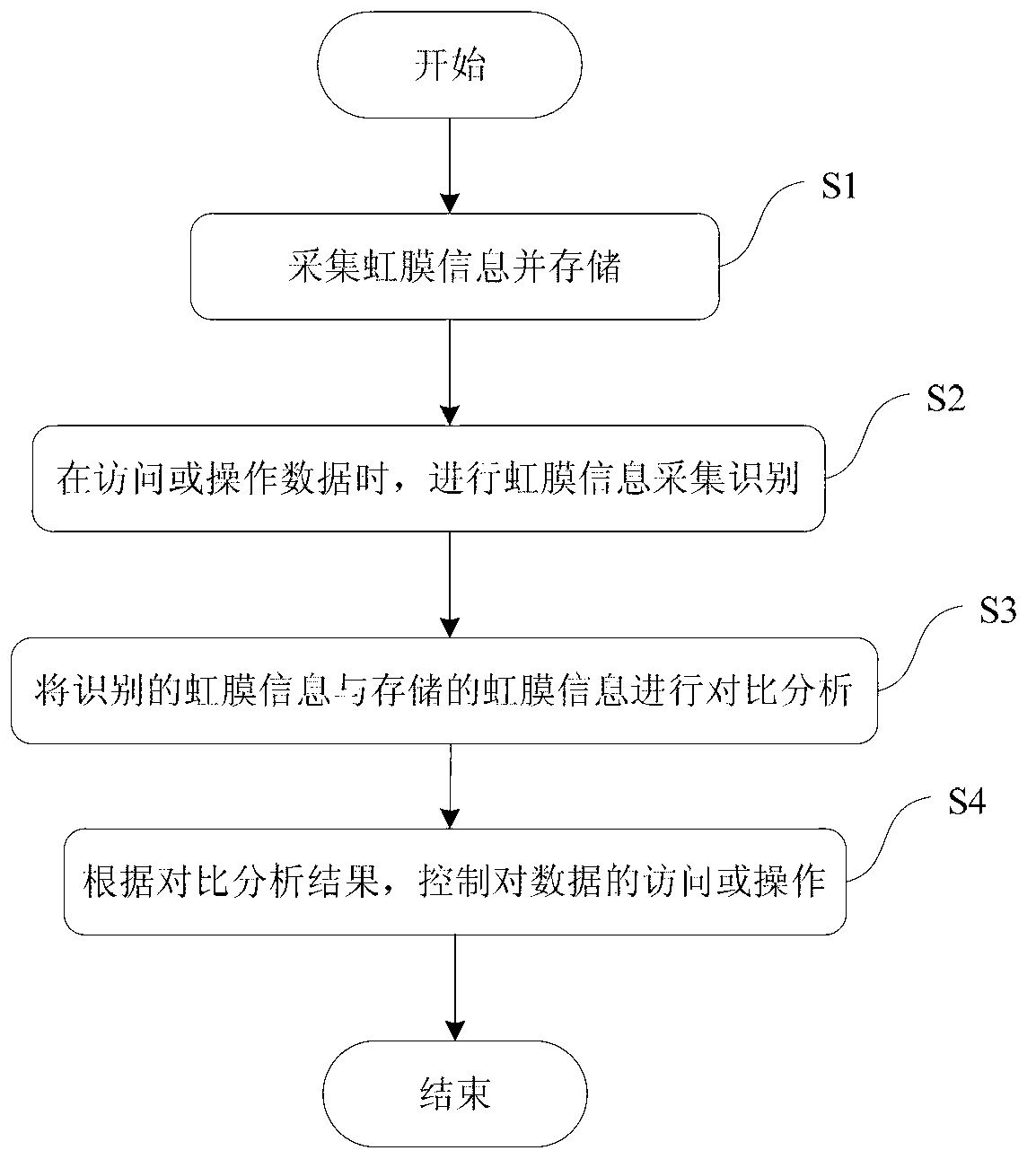
[0043] see figure 1 , which is a schematic flowchart of a method for protecting data based on iris recognition in the present invention. Such as figure 1 As shown, the present embodiment provides a method for protecting data based on iris recognition, and the method at least includes the following steps:
[0044] S1, collecting iris information and storing the collected iris information.
[0045] S2, when accessing or operating data, perform iris letter collection and identification.
[0046] S3, comparing and analyzing the identified iris information with the stored iris information.
[0047] S4, according to the comparative analysis results, control the access or operation to the data.
[0048] Steps S1 to S4 will be described in detail below.
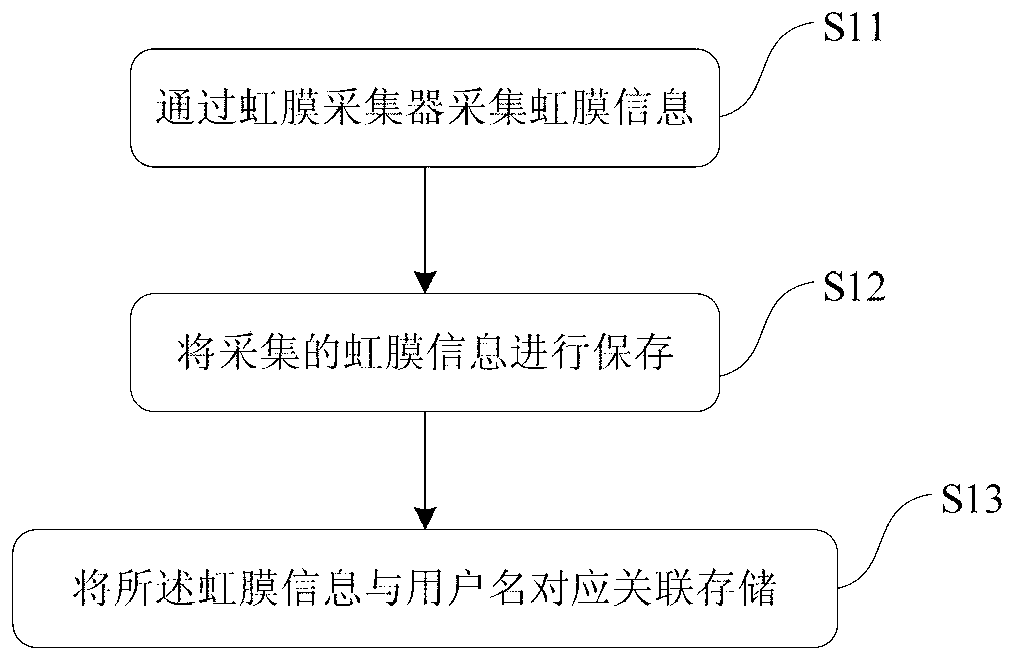
[0049] [Step S1] Collect iris information and store the collected iris information.
[0050] The iris of the human eye is as unique as the fingerprint of the finger. It is impossible to surgically change the characteristics of th...
no. 2 example
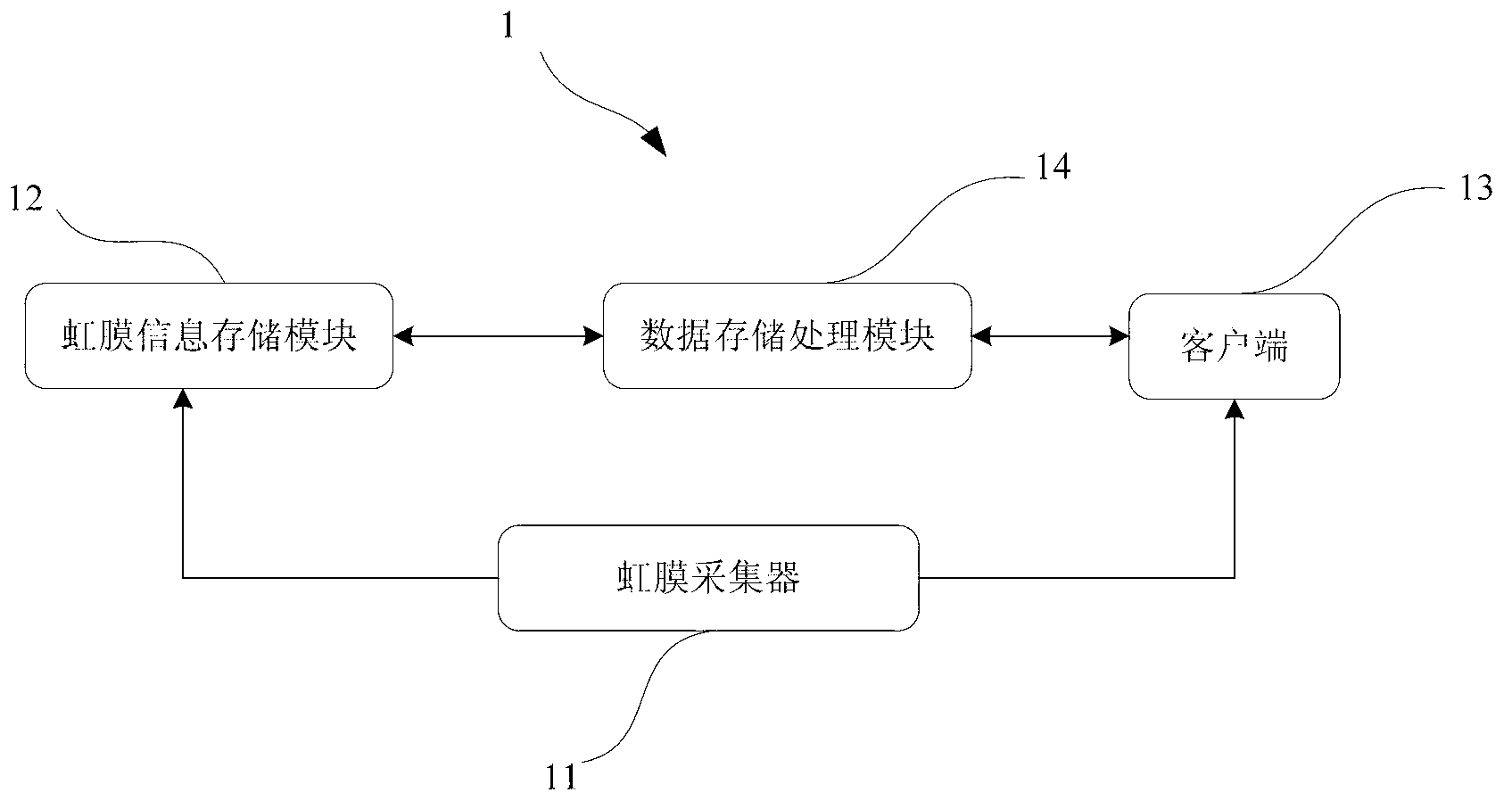
[0071] see Figure 3 to Figure 4 , which is a schematic structural diagram of a system for protecting data based on iris recognition and a preferred structural diagram of the present invention. This embodiment is to realize the method in the first embodiment, such as image 3 As shown, the present embodiment provides a system for protecting data based on iris recognition, and the system 1 for protecting data includes: an iris collector 11, an iris information storage module 12, a client 13, and a data storage and processing module 14 .
[0072] The iris collector 11 collects and identifies iris information. In this embodiment, after the iris is collected by the iris collector 11, the iris collector 11 recognizes the collected iris, and the iris recognition is to convert the visual feature of the iris into a 512-byte Iris Code (iris code), This iris code is stored for later identification. The collection and identification of irises are disclosed in the prior art, and will ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com