Operation and maintenance safety management method based on fingerprint identification
A technology of fingerprint identification and operation and maintenance security, which is applied in the field of IT operation and maintenance to achieve the effect of improving security, ensuring confidentiality and reducing security crises
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0018] All features disclosed in this specification, or steps in all methods or processes disclosed, may be combined in any manner, except for mutually exclusive features and / or steps.
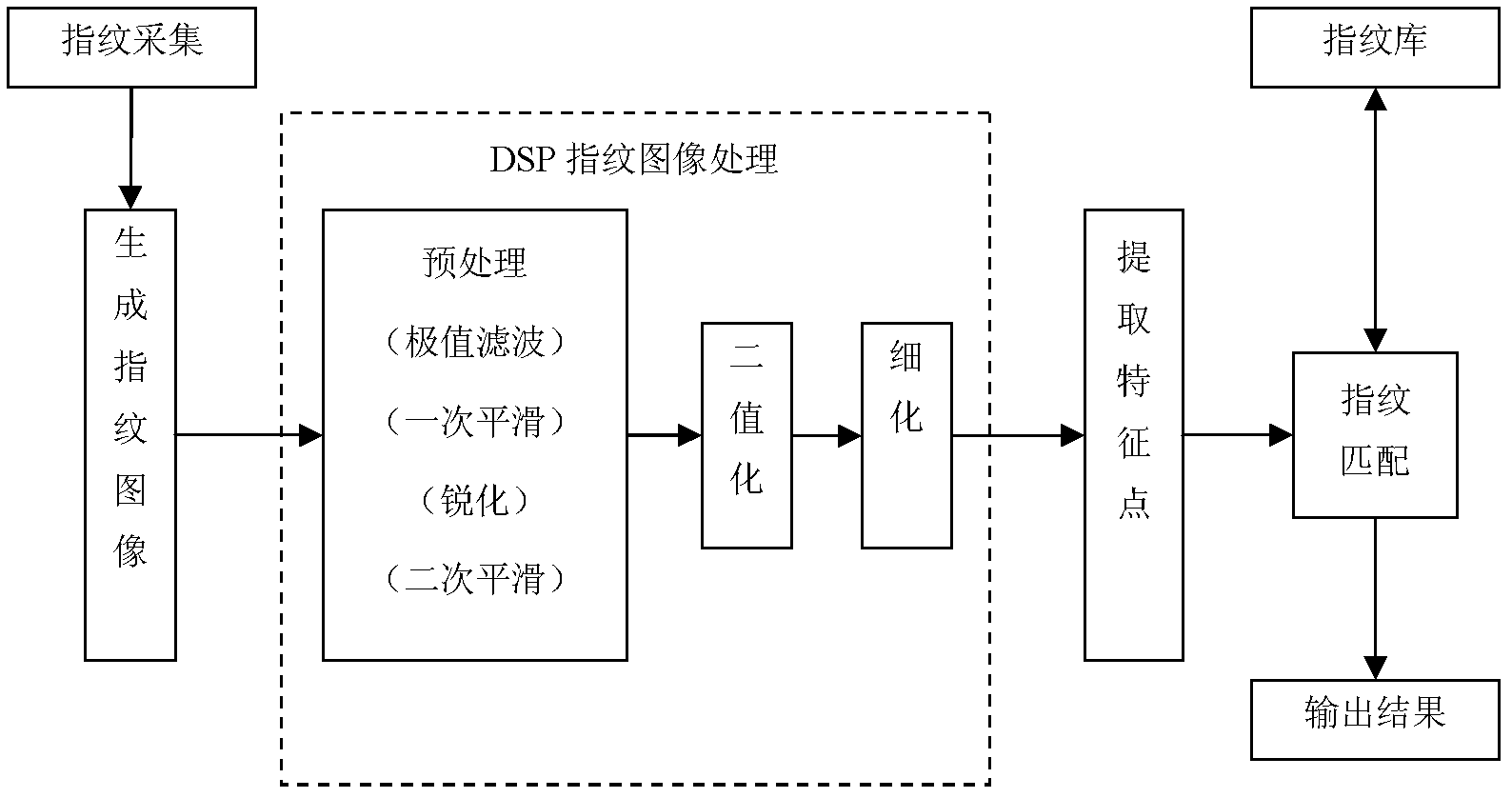
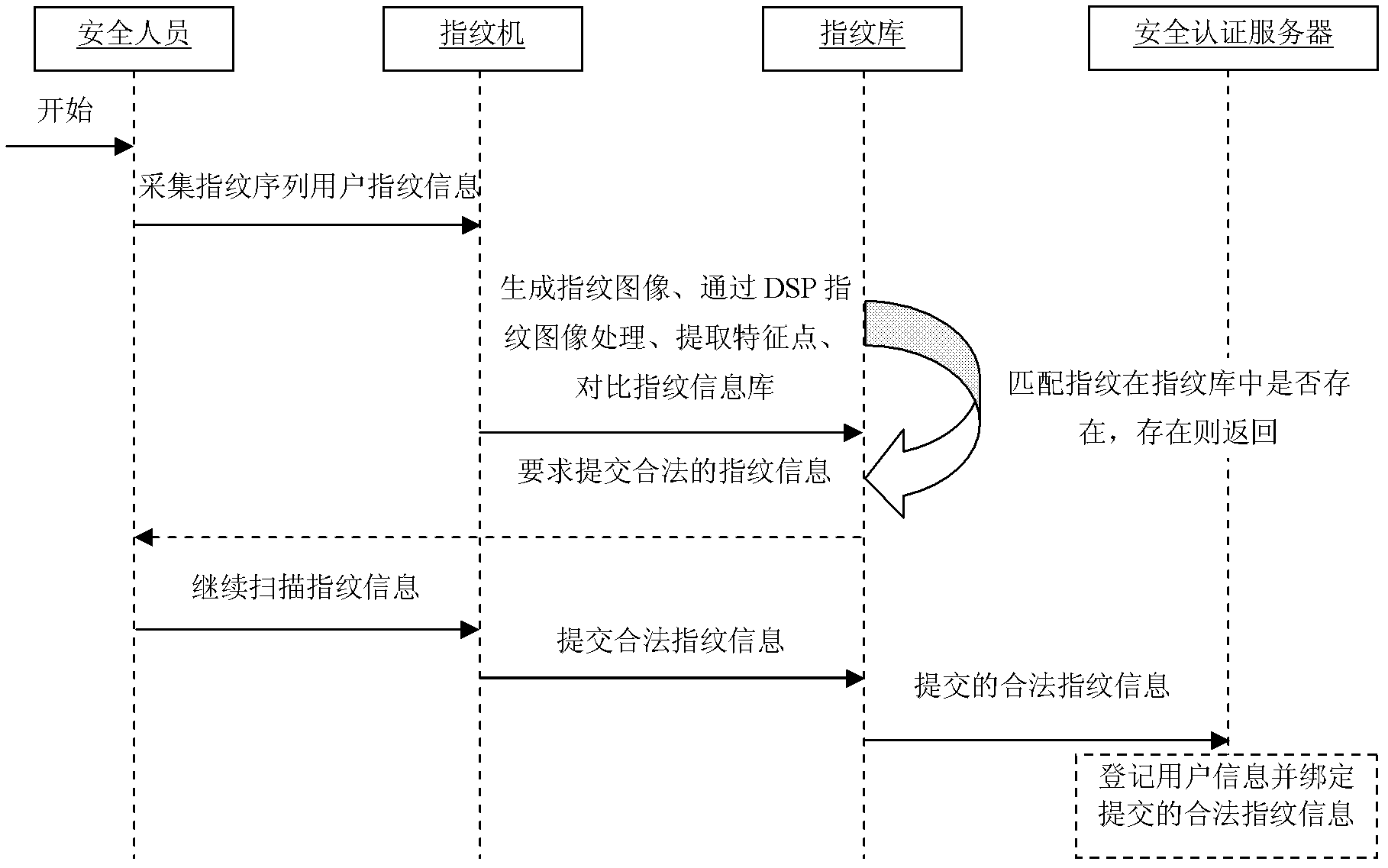
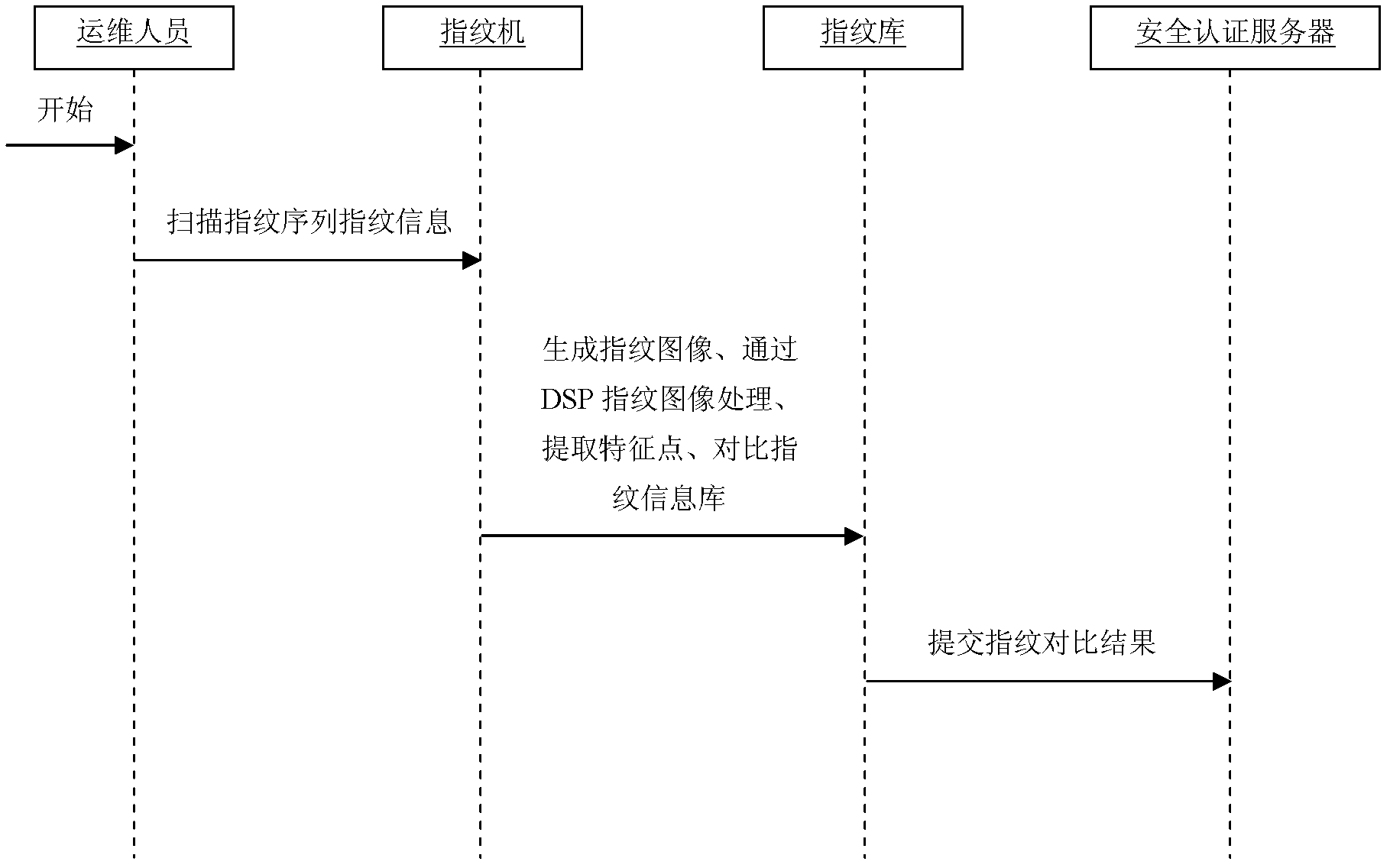
[0019] A fingerprint identification-based operation and maintenance security management method, the characteristic steps of which include: 1) a fingerprint identification machine collects user fingerprint information and saves it in a fingerprint information database; 2) submits user fingerprint information to a security authentication server and registers user basic information to bind 3) Before logging into the operation and maintenance management system, the user first scans the fingerprint information to the fingerprint identification machine; 4) The fingerprint identification machine compares the fingerprint information scanned in step 3) with the fingerprints in the fingerprint information database one by one, Identification; 5) Send the comparison result to the security authentication se...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com